One of the many great reasons to use Apple Maps is to find fun food options, chill cafes, enlightening museums, cute gift shops, and other interesting businesses that you might otherwise overlook, as well as must-see places of interest. But after a while, you might forget about some of these hidden gems. With iOS 15, it will no longer be an issue.

Having thousands of photos and videos in your Photos gallery can make it difficult to find the best ones, but your iPhone does make it a bit easier. Memories, which have been around since iOS 10, automatically group your photos and videos into mini-movies by location, date, or person. It's a fun feature that does the work for you, and it's getting better with the release of iOS 15.

Sound Recognition was introduced with iOS 14, and the accessibility feature uses on-device intelligence to detect 13 different sounds and then notify you whenever it hears one. Apple increases that number to 15 with the addition of two more detectable sounds in iOS 15 that it should have included from the get-go.

When you first open Safari after updating your iPhone to iOS 15, you might be a bit surprised by the design change. Apple attempted to make browsing the web on its smartphones more natural and cohesive, but it may leave you wondering just how to actually navigate your tabs.
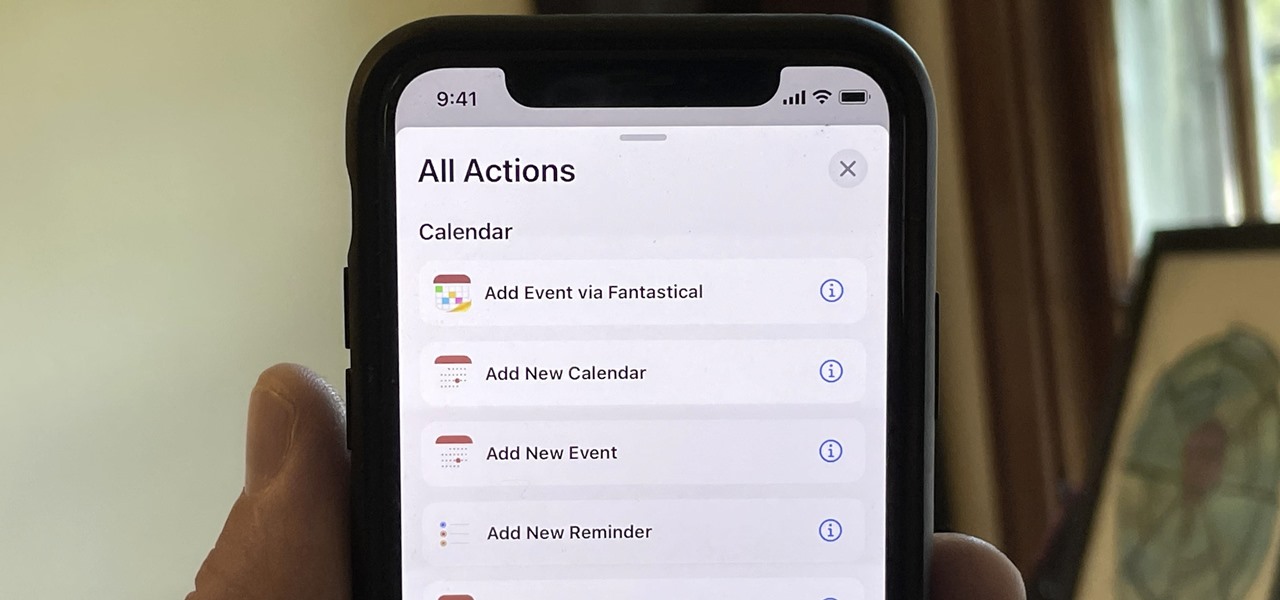
One thing you couldn't do in the Shortcuts app when building a shortcut was browsing the entire list of available actions for all of the apps and services on your iPhone. That all changes in iOS 15.

Apple's exclusive chat services, iMessage and FaceTime, force many of us to stay locked into iOS, iPadOS, and macOS to communicate with other Apple users, so chatting with Android-using friends means SMS texts, third-party messaging apps, and third-party video chat services. However, Apple is breaking boundaries with iOS 15 so that we can FaceTime with Android, Linux, and Windows users.

Your iPhone's search bar has so many great uses. For example, you can quickly find apps on your device, browse different Safari results to find the site that's right for your question, and even search across different iOS apps like Messages, Mail, Notes, and Photos. With iOS 15, Apple has introduced the fastest way yet to start searching with Spotlight on iPhone.

Whether it becomes mandatory or not to show your COVID-19 vaccination card at events, restaurants, bars, hotels, airports, and other public places, it's a good idea to digitize the paper card on your smartphone so that it's always with you. It's also wise to give yourself quick, convenient access to it, so you're not holding up lines while trying to locate the file, and there are a few ways to do that on your iPhone.

Apple released the eighth iOS 14.5 public beta on Tuesday, April 13. The update (build number 18E5199a) comes three hours after Apple seeded developers 14.5 beta 8, so we know that it contains little-to-no surface-level features or changes. Any changes, at this time, appear to be under the hood.

Did you know that you could learn all the fundamentals of web development for less than $35? Set yourself up for your new coding career in 2021 with The Ultimate 2021 Web Developer & Designer Super Bundle, which is on sale for just $34.99 right now — a huge 98% off the regular price of $1,886.

Android's status bar is ever-present. It sits at the top of almost every screen in every app, making it the most prominent part of your Pixel's theme. So it only makes sense that Google would give you a way to change the icons it uses.

Attacks against databases have become one of the most popular and lucrative activities for hackers recently. New data breaches seem to be popping up every week, but even with all of that attention, databases continue to be a prime target. All of these attacks have to start somewhere, and we'll be exploring a variety of methods to gather information on PostgreSQL databases with Metasploit.

TWRP is the premiere custom recovery for Android because of how many devices it supports and how simple it is to use. But installing it in the first place hasn't always been the easiest thing to do — until now. With the help of a Magisk module, you can finally use one Android device to flash TWRP on another.

File permissions can get tricky on Linux and can be a valuable avenue of attack during privilege escalation if things aren't configured correctly. SUID binaries can often be an easy path to root, but sifting through all of the defaults can be a massive waste of time. Luckily, there's a simple script that can sort things out for us.

Without admin privileges, installing additional software, or modifying the Windows 10 firewall, an attacker can alter a router and perform a variety of exploits. It's accomplished by forwarding requests from Kali through a backdoored Windows computer to the router gateway with simple SSH tunnels.

Smartphones are inherently bad for privacy. You've basically got a tracking device in your pocket, pinging off cell towers and locking onto GPS satellites. All the while, tracking cookies, advertising IDs, and usage stats follow you around the internet.

After facing reports of financial troubles over the past month, Magic Leap came out swinging this week with a big push for the enterprise segment of AR, including a repackaged Magic Leap 1, a suite of enterprise apps, and updates to Lumin OS and its supporting development ecosystem. Oh, and its AR headset managed to win a starring role in the marketing juggernaut for the forthcoming Star Wars movie.

TWRP won't be ready for the Pixel 4 and 4 XL until months after release. But since you can already root with Magisk and tinker with the OS, you might find yourself in a situation where your phone won't boot, yet you don't have a custom recovery installed to fix it. Luckily, there's still a way around this.

Spam calls are one of the most annoying things to happen in the world of smartphones for more than one reason. Not only are they bothersome, but they can also be dangerous to people who don't know any better. Google has come up with a crafty solution known as "Call Screen" to let the Google Assistant handle the call for you while you listen in on the caller like a stealth ninja.

The Galaxy Note 10+ is the pinnacle of Android hardware. You won't find many phones with a better combination of specs and design. But you may not love the software. Even with One UI on board, some users still want a more "stock" feel.

The idea of a world without passwords used to be a pipe dream. But as we inch closer to making that a reality, we have services now that securely store all of our passwords under a single master password. It's a convenient way to keep our accounts safe and sound without having to remember all of their credentials. And there's no reason to be afraid — I'll explain why.

One of the most common web application vulnerabilities is LFI, which allows unauthorized access to sensitive files on the server. Such a common weakness is often safeguarded against, and low-hanging fruit can be defended quite easily. But there are always creative ways to get around these defenses, and we'll be looking at two methods to beat the system and successfully pull off LFI.

The idea of squeezing your phone might have sounded a bit out there when it was new, but it's now a hallmark feature on Pixel devices. As useful as it is for summoning the Google Assistant, however, it certainly would be nice to be able pick and choose what action is triggered by squeezing the phone. Well, now you can.

When researching a person using open source intelligence, the goal is to find clues that tie information about a target into a bigger picture. Screen names are perfect for this because they are unique and link data together, as people often reuse them in accounts across the internet. With Sherlock, we can instantly hunt down social media accounts created with a unique screen name on many online platforms simultaneously.

Fireworks are the best part about the Fourth of July and other celebrations, but they can easily cause accidental injuries. It's both safer and more fun to set them off remotely, so we'll hack some standard fireworks with nichrome wire, a relay, and an Arduino to ignite remotely over Wi-Fi using any smartphone or computer.

The Pixel 3a runs smoothly out of the box already, but installing a custom kernel can supercharge your experience even more. From fine-tuned CPU tweaks for boosting performance or battery life to adjusting the display colors for your screen how you want, ElementalX kernel can provide you with a ton of new features you didn't know you were missing.

MouseJack vulnerabilities were disclosed over three years ago. Some wireless keyboard manufacturers have since issued firmware updates, but millions (if not billions) of keyboards remain unpatched worldwide, either because they can't be updated or because the manufacturer never bothered to issue one.

If you record yourself for a vlog or story post using your selfie camera, it can be challenging to stay on message. You might worry too much about the way you look or sound to focus on what you want to say. Using a script can help, but looking away from the camera to read is unprofessional, even on social platforms like Instagram. What you need is a teleprompter, and there are apps for that.

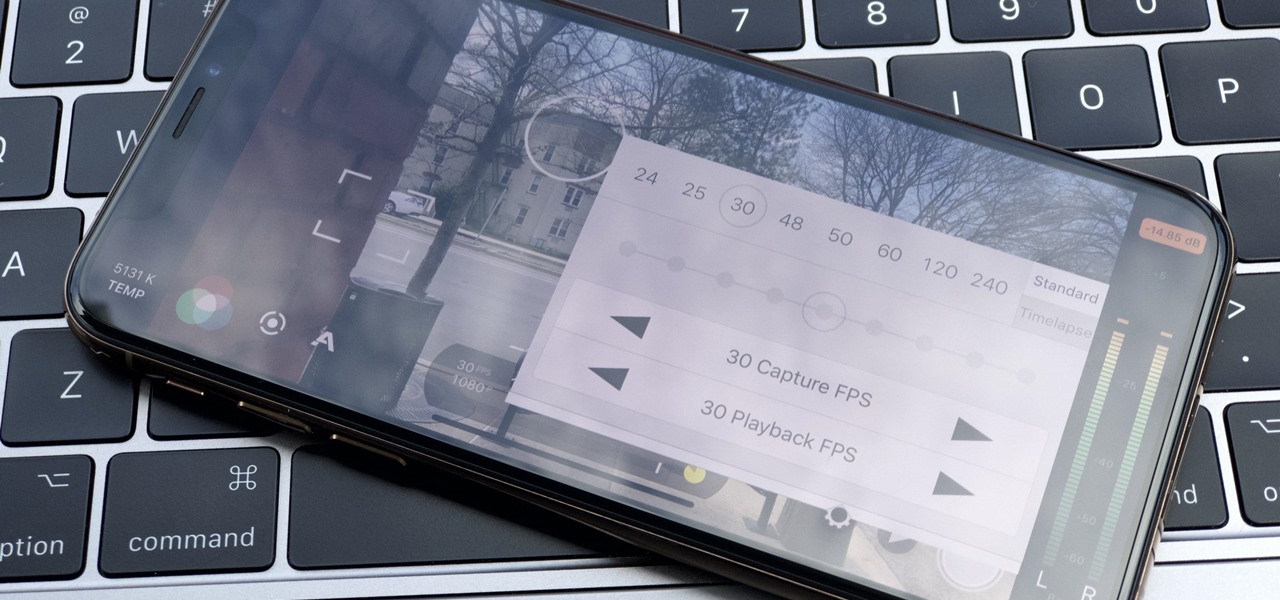
The days of bad smartphone videos are long gone. Your iPhone or Android phone is a capable video recorder, even offering different frame rate options in the native camera settings. Filmic Pro makes things a little simpler, however, and adds additional controls you wouldn't find on your device alone.

A lot of people still trust their web browsers to remember every online account password for them. If you're one of those users, you need to adopt a more secure way of managing passwords, because browser-stored passwords are hacker gold mines. With a USB Rubber Ducky and physical access to your computer, they can have a screenshot of all your credentials in their inbox in less than 60 seconds.

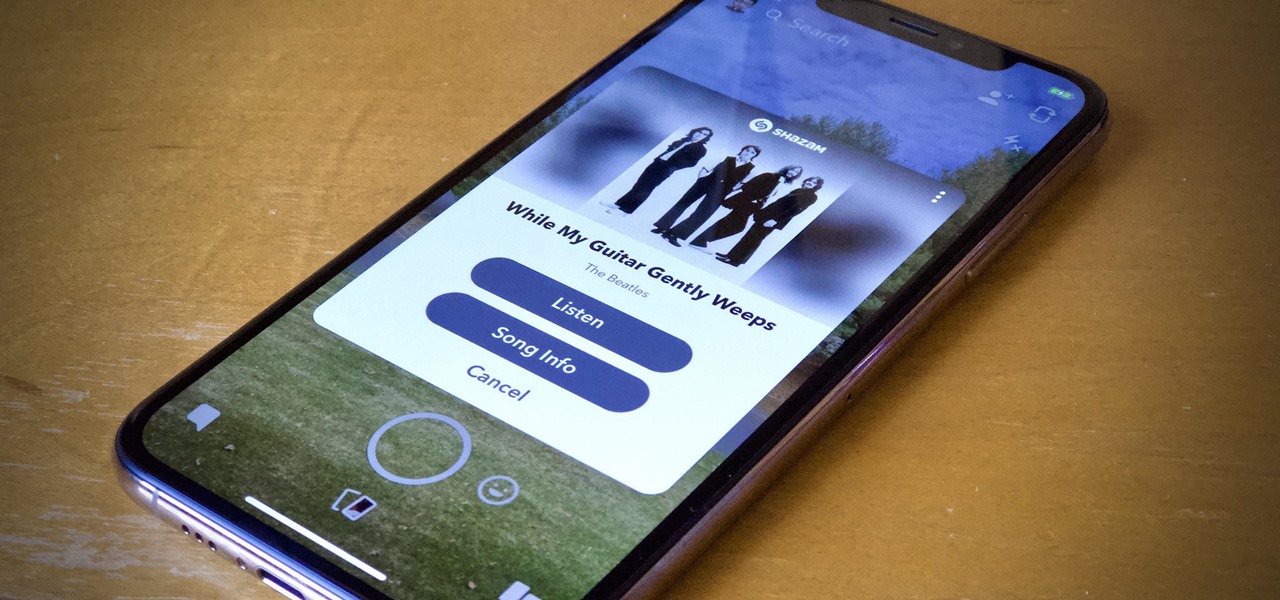
Say you're sending a snap to a friend at a restaurant, bar, store, what have you, but you're curious about the song that's playing in the background. You could leave the app to Shazam it, or you could ask screen-hogging Siri or Google Assistant what the track is, but why not just have Snapchat do the work for you? With its built-in scanner, you can discover a song without ever leaving the app.

With a simple social engineering trick, sudo passwords can be captured in seconds without the target's knowledge. The passwords can then be saved to a file or exfiltrated to another computer on the network.

When flashing files through TWRP, ADB, or Fastboot, there's a slight chance for things to go wrong. Whether it's user error related or something else entirely, it's always good to have a backup plan. In most cases, you'll be dealing with a semi-brick or soft-brick, which can usually be solved by wiping the data of the device using TWRP. However, it can be more severe than that in some cases.

These days, it's easy to cut the cord. Thanks to a new crop of streaming TV apps, you can get the same service offered by a traditional cable subscription at a fraction of the price. After some extensive testing, we believe we've found the absolute best apps for cord cutting.

Before you can dive into customizing your OnePlus 6T, you must take the initial step of unlocking the bootloader to gain the ability to install TWRP, Magisk, custom ROMs, and other mods.

By now, you've probably already seen Andy Serkis and his performance capture demo for Magic Leap. And sure, marrying motion capture acting and augmented reality sounds compelling, but how does it really work as an experience?

Like an overbearing mother, Apple will constantly nag you through annoying red bubble alerts about iOS updates that are ready to install. Fortunately, you don't have to take this issue lying down, as there are ways to prevent your iPhone from receiving OTA updates and their corresponding prompts, regardless of whether your device is jailbroken or not.

In a surprise twist, Apple released iOS 12 public beta 8 to software testers on Thursday, Aug. 23, right alongside iOS 12 dev beta 10. The release comes as a bit of a shock, as the company released iOS 12 public beta 7 just three days earlier. The official build of iOS 12 now feels closer every day.

You can feel it in your bones. You may die if you don't get this phone. There's just one problem — the price. Suddenly, you come across what seems like manna from heaven. That very device, at a deeply discounted rate, can be yours.

Wi-Fi tools keep getting more and more accessible to beginners, and the LAZY script is a framework of serious penetration tools that can be explored easily from within it. This powerful and simple tool can be used for everything from installing new add-ons to grabbing a WPA handshake in a matter of seconds. Plus, it's easy to install, set up, and utilize.