Pay attention to this knitting demonstration video and learn how to do the e wrap cast on. This is not a good knitting cast-on for long lengths because it is not possible to control the tension well when knitting the first row, resulting in a loopy, uneven edge.
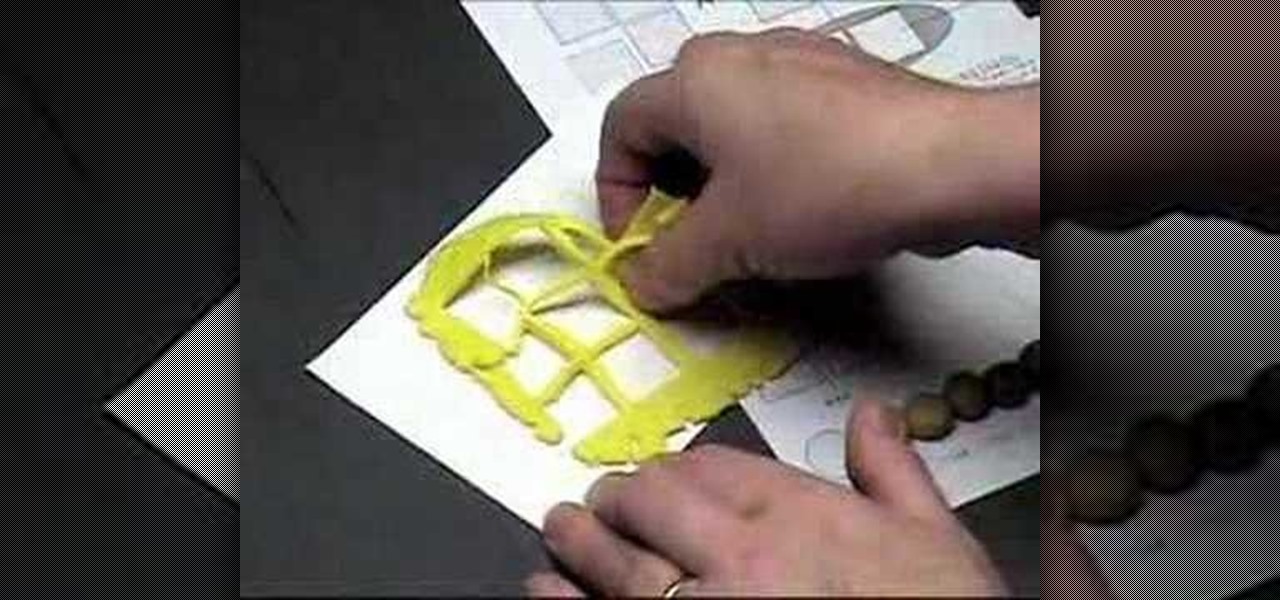
Color scales are important to learning the subtle changes and variations in colors that result from mixing. Polymer clay is an excellent medium to create these color scales, and the beads don't need to remain prototypes of colors, but can be used in jewelry. Watch this video crafting tutorial and learn how to make a color scale out of polymer clay beads.
In this video tutorial, Chris Pels will show how events are handled in master and individual content pages. Even though the end result of a master and individual content page is a single ASP.NET page rendered in the user's browser the event handling in each type of page is handled separately. If a control is located in the master page the corresponding event handler is located in the master page by default. The same is true for controls in the content page. See two approaches to having the ev...
In this ASP.Net video tutorial, Chris Pels will show how to use nested master pages to create individual master pages that represent different standard content layouts for a web site. First, see how several major commercial web sites use a standard set of content layouts. Next, see how to nest a master page within another master page, and use the design time support in Visual Studio 2008. Then, learn the considerations for establishing a “page architecture” which represents the major types of...

Ever here of the "overworked" defender" chess move? Of course you have, but that doesn't mean you know how to pull it off. See how to do it, right here. A chess piece is overworked when it has more than one defensive job (guarding pieces or squares) to do. Typically, the overworked piece is exploited by capturing one of the pieces it's defending or occupying a square it's defending. This forces it to leave one of its defensive jobs usually resulting in material loss or checkmate.

The Windsor knot, also (wrongly) known as the "Double-Windsor" (a non-existent enormous 16-move knot), is the most well known knot in the world. The Windsor is a large, symmetrical, self-releasing triangular knot. The tie was named by Americans in the 1920-30's after the Duke of Windsor. The Duke was known for his fondness of large triangular tie knots, but didn't in fact invent this particular knot. His secret was a specially tailored tie with an extra thickness of material.

Trigger point massage is a good technique to bring immediate relief to conditions like frozen shoulder, stiff neck, tennis elbow and headaches. Trigger points form whenever a muscle or joint is stressed beyond its capacity to recover. They are usually believed to be the result of an accumulation of toxic waste around a nerve ending. Active trigger points will create pain and discomfort.

Pythagoras was a smart man, so smart that his mathematical theory is named after him and still used today, more than 2,000 years later: the Pythagorean theorem. It implies that the square of the hypotenuse of a right triangle is equal to the sum of the squares of the other two sides. The Pythagorean theorem is a cornerstone of geometry. Here’s how to use it.

Throughout this video, The Cupcake Special, with Realizing Nuala, you listen to the song "Happy" as you watch a young woman demonstrate the correct and incorrect methods of baking and icing cupcakes. She begins the video by baking several dozen chocolate cupcakes in small paper cups. Then moves onto beating the icing, starting with orange, and then chocolate, and continues on making several other colors. Amidst the creation of the icing, you are shown other decorative features made for the cu...

With Samsung's One UI version of Android, it's easier than ever to take a screenshot and quickly edit the captured image. However, the downside to that convenience has manifested itself in an overlay ribbon that can also get in the way.

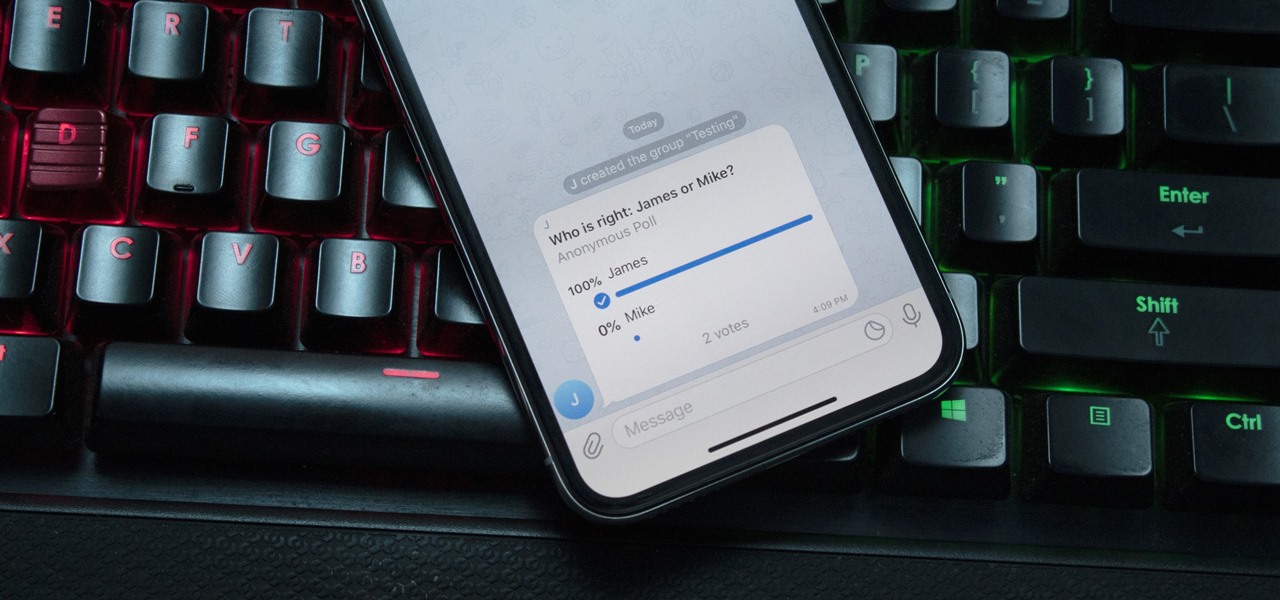
With group chats, arguments tend to devolve from a dispute between two people to a giant debate amongst all members. But before things get out of control, Telegram has a feature that can help.

Just days ago, Georgio Armani canceled his live show in Milan and opted to stream it instead due to coronavirus concerns. Now, at the start of Paris Fashion Week — shadowed by similar worries — Burberry has launched an augmented reality tool that lets you view the latest high fashion from the comfort of your home.

Web application firewalls are one of the strongest defenses a web app has, but they can be vulnerable if the firewall version used is known to an attacker. Understanding which firewall a target is using can be the first step to a hacker discovering how to get past it — and what defenses are in place on a target. And the tools Wafw00f and Nmap make fingerprinting firewalls easy.

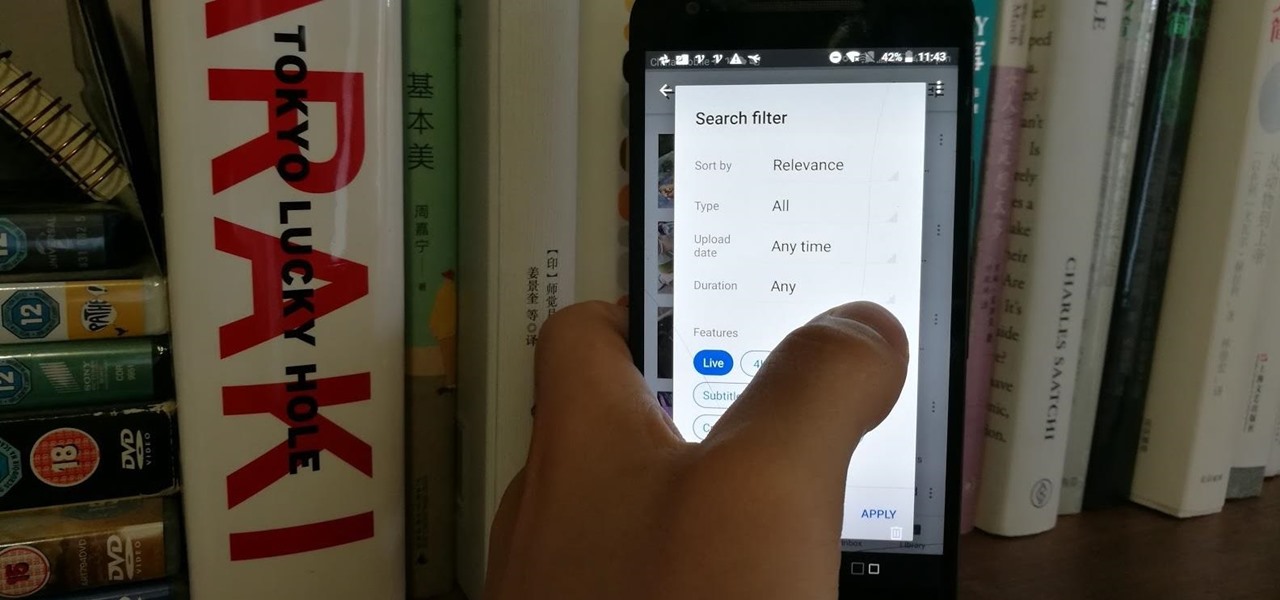
Have you tried searching for 4K HDR videos on YouTube, only to get 1080p videos just because the uploader used "4k" or "HDR" in the description? Or have you tried looking for a video about something that just happened, except YouTube's algorithm surfaces established videos first by default, so all the results you get are older than a month? Well, there's a better way.

There's something seriously wrong with Apple's new Shortcuts app, and it's severely limiting the number of shortcuts users can install on their iPhones.

Reconnaissance is the phase of an attack where a red team or hacker designs a strategy based on the information they can learn about the target, as well as what the available attack surface looks like. These scans can take time to discover relationships, but Raccoon OSINT scanner coordinates multiple automated scans to produce invasively detailed reports on a target with a single command.

Like an overbearing mother, Apple will constantly nag you through annoying red bubble alerts about iOS updates that are ready to install. Fortunately, you don't have to take this issue lying down, as there are ways to prevent your iPhone from receiving OTA updates and their corresponding prompts, regardless of whether your device is jailbroken or not.

In our last ARKit tutorial, we learned how to measure the sizes of horizontal planes. It was a helpful entryway into the arena of determining spatial relationships with real world spaces versus virtual objects and experiences.

Ever notice how some augmented reality apps can pin specific 3D objects on the ground? Many AR games and apps can accurately plant various 3D characters and objects on the ground in such a way that, when we look down upon them, the objects appear to be entirely pinned to the ground in the real world. If we move our smartphone around and come back to those spots, they're still there.

HTC is entering the augmented reality market through the back door by giving developers access to the stereo front-facing cameras on the Vive and Vive Pro VR headsets.

Apple's iPhone X now has the power to turn anyone into a Japanese anime character, thanks to a new app that harnesses the device's TrueDepth camera.

A development duo has concocted an iPhone app that displays related tweets based on objects recognized by the device's camera.

When we are building programs that communicate over a network, how can we keep our data private? The last thing we want is some other lousy hacker sniffing our packets, so how do we stop them? The easy answer: encryption. However, this is a very wide-ranging answer. Today we're going to look specifically at how to encrypt data in Python with dynamically generated encryption keys using what is known as the Diffie-Hellman key exchange.

Thanks to augmented reality, fashion companies can let customers try on cosmetics, clothes, more cosmetics, and sunglasses from the comfort of their homes and through the non-judgmental eyes of their smartphone camera.

The creative possibilities are part of what makes Apple's ARKit so exciting. We've seen new camera effects, painting, and new ways to tell stories through ARKit. Now, the app developer studio "Orb" has created an app to let you create scenes with 3D objects of your choosing.

People love sex. They don't love talking about the possible repercussions of sex. And with dating apps such as Tinder, Grindr, and Bumble paving new ways for strangers to talk and have casual hookups, people need to be able to more comfortably have a conversation about sexual health and protection. Luckily, now there's an app for that.

Findings from a mouse study suggest that the Zika virus infection may have serious reproductive consequences for men.

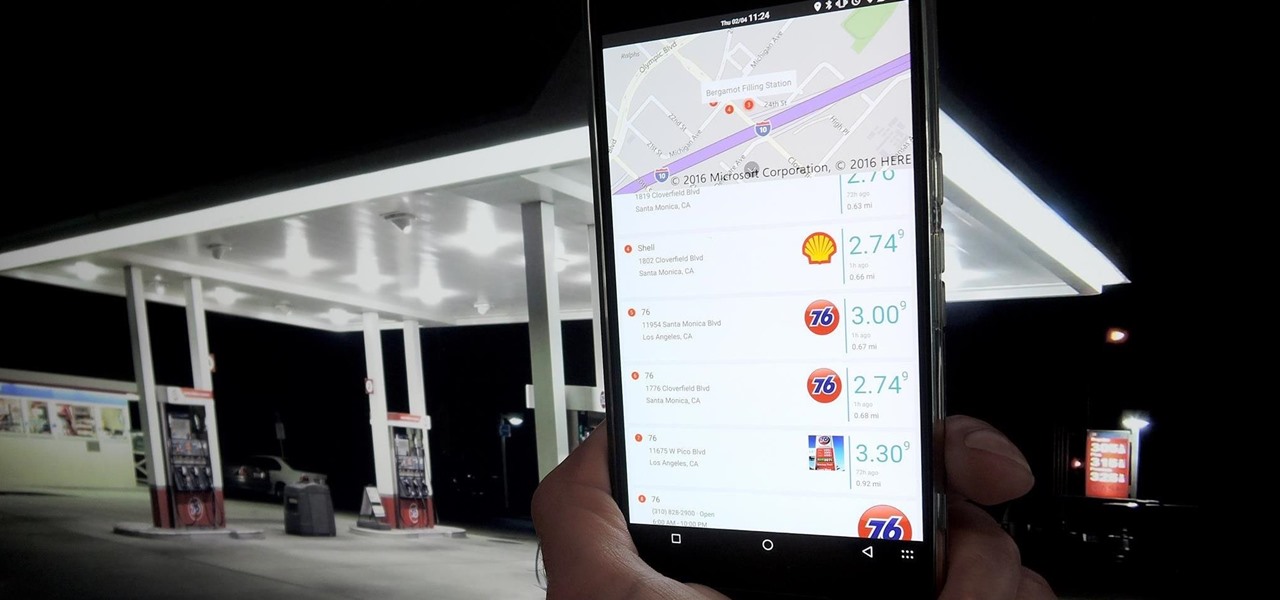
Google Maps, once considered superior to Apple Maps, has contributed to a terrible mistake for one woman. A group of demolition workers in Texas were using the service to find a worksite, and to the dismay of homeowner Lindsay Diaz, Google was entirely inaccurate.

Microsoft is working hard to make Bing a good alternative to Google for more than just looking up images of the "human anatomy" that Google and a lot of other search engines filter out of their results.

In the last iteration of how to train your python, we covered the concept of control flow and covered the booleans associated with it. Today, we'll be putting those to use as we discuss how to use if, else, and how to make conditional statements. So, Let's get started!

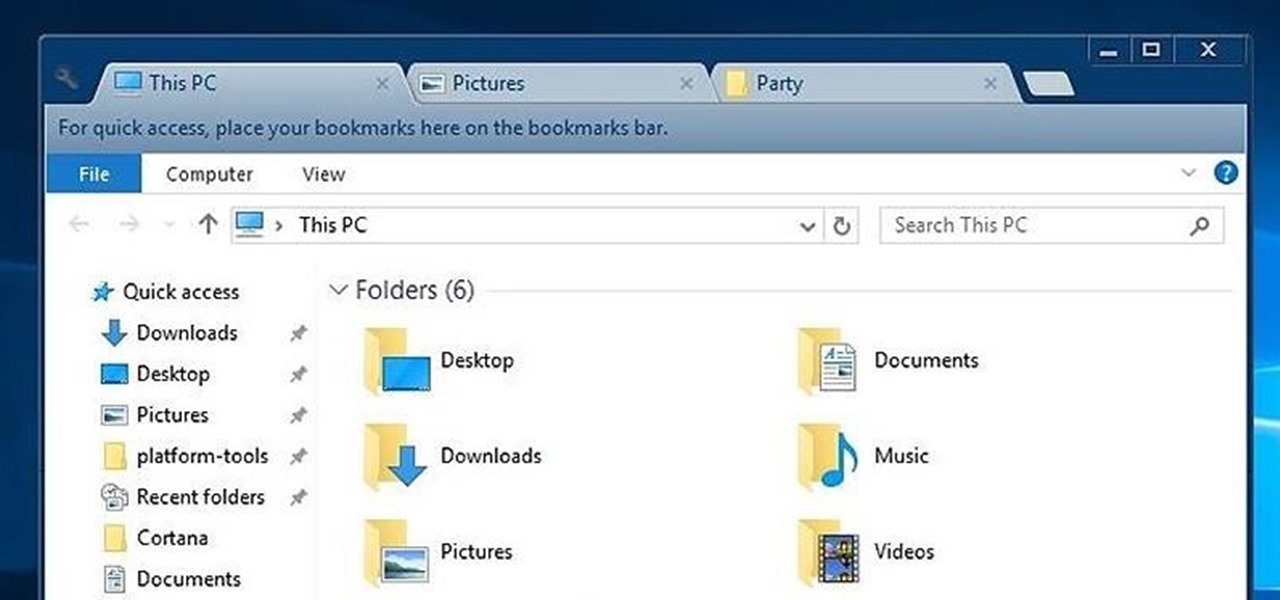
While Windows 10's new File Explorer is just as, if not more, useful as it was in previous iterations of Windows, it could definitely still be better. Two features that would greatly improve File Explorer are tabbed results and a customizable user interface, similar to how they are in Google Chrome.

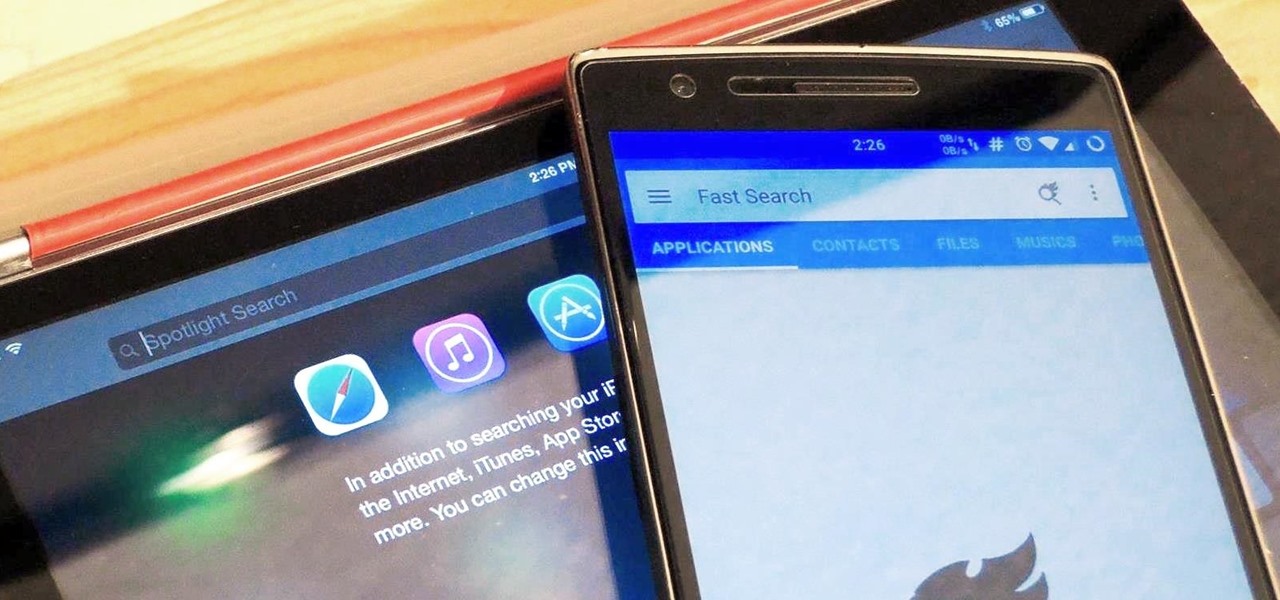
Google Now is great for looking up movie times or finding your parking spot, but if you need to track down a file you downloaded, you're relegated to using a file explorer and, depending on your organizational skills, this can either be extremely easy or a huge pain in the ass. Unfortunately I land in the latter category, which is why I started using Fast Search by developer Mohamad Amin.

As you might know, there are a multitude of tools used to discover internal IP addresses. Many of these tools use ARP, address resolution protocol, in order to find live internal hosts. If we could write a script using this protocol, we would be able to scan for hosts on a given network. This is where scapy and python come in, scapy has modules we can import into python, enabling us to construct some tools of our own, which is exactly what we'll be doing here.

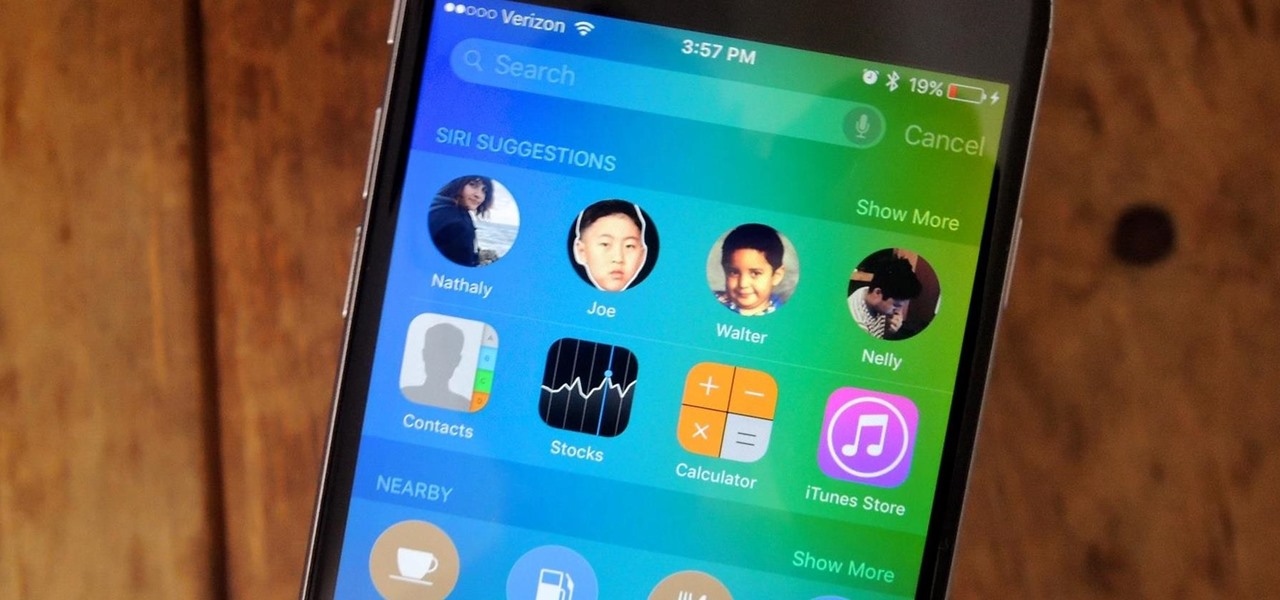
Apple certainly took a page from Google Now with its new "Proactive" search page in iOS 9. Located to the left of the home screen, the page provides quick access to contacts you've recently corresponded with, suggested applications, nearby places, and news articles based off of your Safari activity.

Most cooks know they should stir pasta a few times while it's cooking, for obvious reasons: as the noodles cook, they release a glue-like starch that makes them stick to one another. Stirring prevents them from clumping together in an unwieldy, inedible mass. Now Mark Bittman in The New York Times discusses a great technique from Italy that helps you produce a plate of tender, toothsome pasta evenly coated in rich sauce every time, but it involves stirring the pasta at the end of its cooking ...

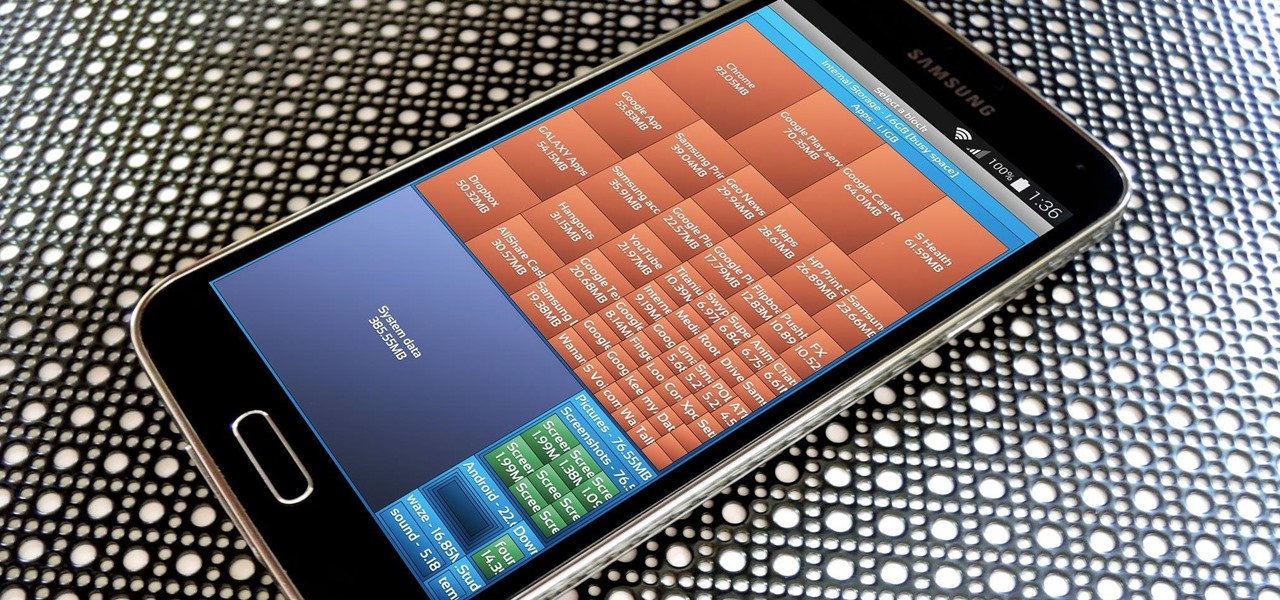
The more we use our smartphones, the more storage space becomes occupied—it's an inescapable fact. But as the data accumulates and chokes off our storage, it can become difficult to identify exactly which files are occupying the most space.

We're a little citrus-obsessed, and with good reason: lemons, limes, oranges, grapefruit: Mother Nature really packed those babies with flavor, from peel (which you can zest without special tools) to juice. Now executive chef Amanda Freitag of Empire Diner has come up with a way to make those lemons and limes give up even more flavor by applying a lot of heat.

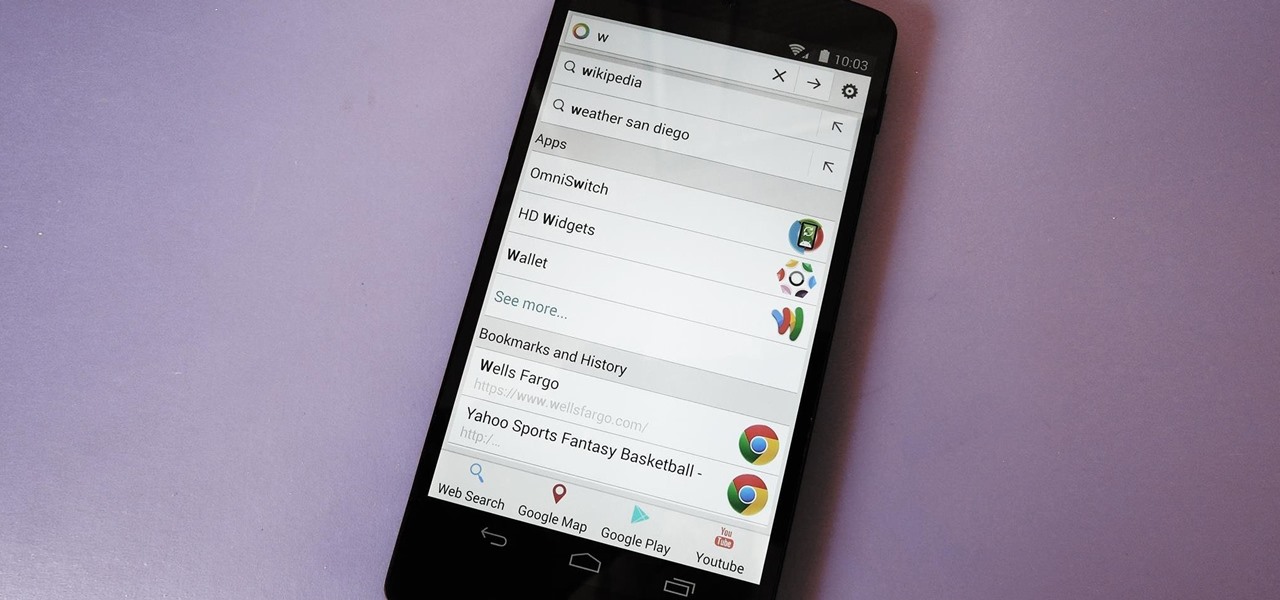
Let's be real, browser histories are virtually useless. Trying to find something you passed up a week ago is like, pardon the cliché, finding a needle in a haystack.

Merely fidgeting and shivering can burn calories, but now you can add trembling in fear to the list too. Just pop in a good horror movie and turn down the lights to burn off up to 200 calories. What would you rather do? Walk for over 30 minutes or watch a 90-minute scarefest?

Prior to the release of Android 4.0, most devices had a dedicated search button. This functionality allowed you to search Google from your home screen and app-specific content from within any app. Eventually, though, this dedicated search button was ditched in favor of an icon in the action bar of apps, and a search bar on the home screen.