If you have trouble deciding on just one cover photo for your Facebook profile, this new app is perfect for you. It's called InstaCover and it lets you create your own cover out of Instagram photos. They can be your own photos or you can choose from all of the public photos by other Instagram users. All you need is a Facebook account.

We've featured unusual pinhole cameras before, but nothing at this grandiose scale. Presenting the world's largest mobile pinhole camera, the Cameratruck, creation of photographer Shaun Irving. The Cameratruck can take pictures approximately 3,000 times the size of a 35mm!

To Mario enthusiasts everywhere: Mario mania has been lovingly expressed all over the web for some time now (including How-To). The most recent accomplishment brings together two classic favorites: Mario plus LEGOs.

Korean artist Osang Gwon creates more than just alluring paper-made girls. Gwon has moved past traditional papercraft, taking volumes of photographs of his subjects and constructing sculptural forms from the carefully arranged 2D images. Gwon shows in galleries, and has done commissioned projects for both Fendi and Nike.

This technique was popularized on Japanese television and has since been widely imitated and posted everywhere. The original concept was shown on a primetime Japanese variety show. Many others produced (plagiarized) their own tutorials for the web. Even Martha made one.

Need a way to prove your strength? Only superheroes have the power to tear metal, right? Wrong! Even the weakest nerds can shred metal with science on their side. Ripping through metal is easier than it sounds.

In case anybody's been under a Beyoncé-proof rock for the last month, the (internet) world is forever changed by the Single Ladies... and in many ways, me.

Surf the web, regardless of the weather or where you are. Your LG Rumor cell phone comes internet capable and ready. Watch this video cell phone tutorial and learn how to use an internet browser on an LG Rumor. Use the web on an LG Rumor cell phone.

For the holiday season, a great knitting project is a snowflake design. It's perfect for handmade Christmas gifts. You can knit just one, or a row of them, or use them as full pattern on a sweater or blanket—or whatever project you choose.

Have you ever wanted to make your own Minecraft server on Windows? This tutorial will teach you how, without having to download Hamachi.

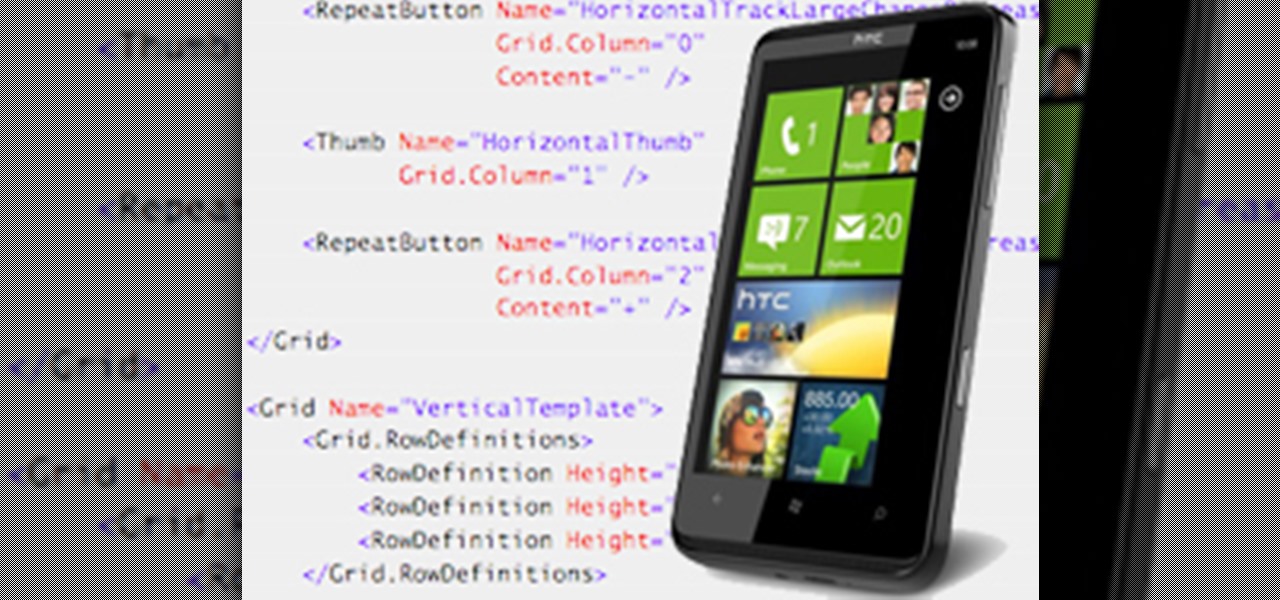
Microsoft's new mobile operating system is officially out on the market, and programmers are hard at work developing new mobile apps for Windows Phone 7 devices. But there's a lot going on in this new platform, which means there's a whole lot to be learned, and the only man in the world with a Windows tattoo is here to help— Charles Petzold.

Hello everyone, This is my first tutorial posted on WonderHowTo and as a starter I wanted to show you how to make a nice curtain in GIMP, the free Photoshop alternative. Even though GIMP does not have all the features of his expensive brother, you can still do some cool designs or photo manipulation.

This is one of the many great features of Windows 7 and If you don't have windows 7 I would definitely recommend it. This feature allows you to have multiple background images and windows change them to however often you choose.

Ingredients: White multi-purpose glue (do not use washable glue)

Are there web sites at work or school in which you would like access but they are blocked by the administrator? Use the command prompt in Windows XP to access blocked web sites. Access web sites blocked by your administrator.

In this tutorial you will learn how to create glossy web icons in Illustrator CS2. Very often you will be able to download royalty-free icons from the Internet, but the problem is they are not customized to fit in with your existing web site's design. So creating your own icons is always a good way if you have the time to do it. Make sure to hit "play tutorial" in the top left corner of the video to start the video. There is no sound, so you'll need to watch the pop-up directions. Create glos...

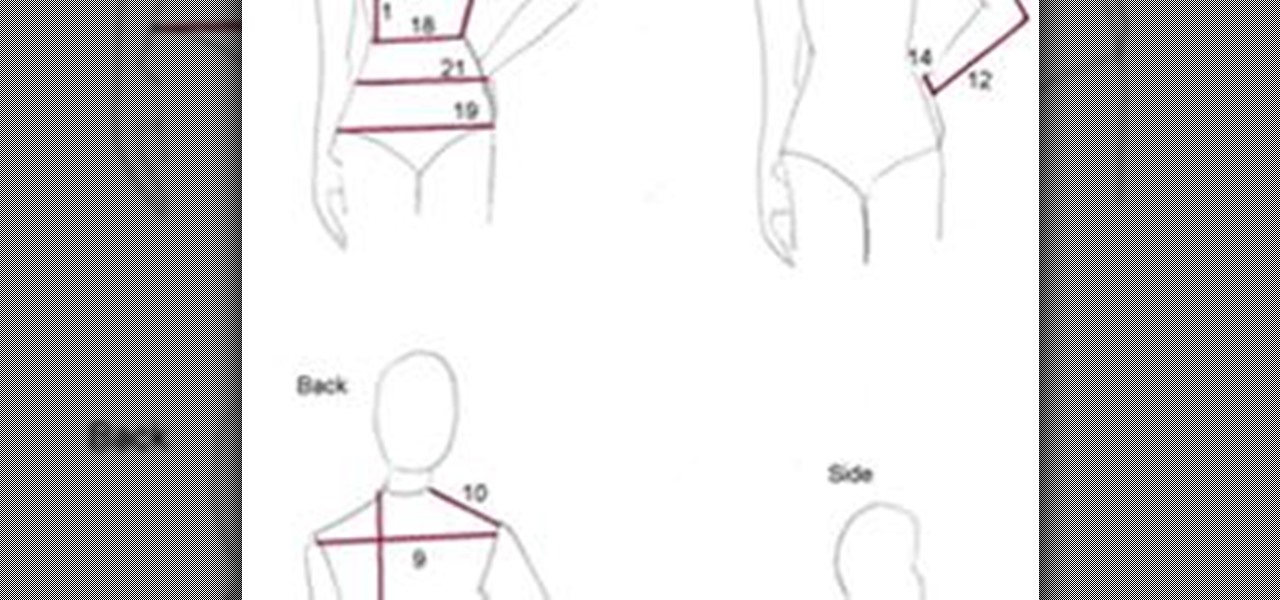
These measurments should be taken and recorded before drawing up you clothing design pattern. Wear the bra and panties you will be wearing with the final garment. Another option, especially if you are going to be selling a series of the garments, is to follow a size chart. While sizing is not very standardized in the clothing industry, I like the charts on the Burdastyle website which are in both inches and centimeters. When measuring, the tape measure should be neither too tight nor too loos...

Ink & Paint was originally intended to provide a place for the sharing of graffiti and street art related news and the spreading of the street art culture. However in recent months I have noticed a distinct lack of "lowbrow" art in the WHT community. Don't get me wrong though, I'm a HUGE nerd. I love null byte, I love the Minecraft world, and all the tech posts that are becoming increasingly more common. It's awesome. However the nerd in me and the artist in me both want to see more comics, s...

You want to put out a live web server, but you don't want to be owned in the process. An expert eye for security is not needed if you take a few basic steps in locking down the hatches. Most successful attacks today are not the complex, time-consuming tasks you might think, but simple lapses in policy that a hacker can take advantage of to compromise your server.

In the first part of this series, we learned about darknets, as well as how they came about. But these patches of forgotten Internet are not the oasis of free information you might think. Despite being hidden—or just harder to come across—these networks are no more safe then anywhere else on the 'clear' Internet. The nature of networking and routing means your location is always known in server logs. It only takes one phone call to your ISP with your IP address to obtain both your physical ad...

As we all know, security is a big thing here in Null Byte. We've talked quite a bit about ways to encrypt traffic and become anonymous on the internet, some of which entail using proxies, VPNs, and SSH tunnels. We've also talked about preference using SSL pages in practice for safe logins. These are all great protocols and tools, but aren't without their flaws and inconveniences.

JavaScript is the language of the internet. It is what allows us to create dynamic, interesting webpages that are fast, web-based applications and so much more. The primary use of JavaScript is to write functions that are embedded in or included from HTML pages and that interact with the Document Object Model (DOM) of the page. This is the magic that allows all of what we see to happen, and for our browser to be manipulated.

Welcome to another Community Byte announcement! In the past two sessions, we have coded an IRC bot in Python capable of issuing commands. Since it can issue commands and most of you are new to programming, that project will stay idle for a while. Other commands such as voice and half-op can be easily hacked in via common sense, even if you weren't there for that session.

In this Null Byte, I'm going to teach you about Null Byte Injections. Null Bytes are an older exploit. It works by injecting a "Null Character" into a URL to alter string termination and get information or undesirable output (which is desirable for the malicious user).

Like the recent XSS 0day exploit found in the Mac and Windows versions of Skype, a similar one has been found in the Skype app for iPhone. The vulnerability allows an attacker to send a message that contains malicious JavaScript code in the "Name" parameter. This code can steal your phonebook, crash the app, and potentially do a lot worse. The URI scheme is improperly identified for the web-kit browser. Instead of going to a blank browser page, it defaults to "file://". The code could steal a...

Big news from the world of game development engines. For several years, Unity3D has been the free 3D game development engine of choice for aspiring and indie game designers around the world. While it isn't as powerful as Unreal Engine 3 or CryEngine, it's free and much easier to use. Now, according to an announcement made by Unity yesterday, Unity 3D is about to unleash a huge weapon that neither of those other engines can claim: Flash compatibility.

If you're like me, you don't do a lot of web browsing anymore. I subscribe to my favorite blogs' feeds and read them via Google Reader. It's one of my favorite Google products, for a lot of reasons. I can keep up with most of my web activities in one tab, and follow along with my favorite blogs, Flickr photos, and Twitter. I can share instantly with people who follow me, and see what other people have shared with me. I hope that Google+ will integrate well with Google Reader, because it alrea...

Mozilla is scheduled to release their updated Firefox browser on Tuesday, bringing the popular web browser up to version 6. Lately, the Mozilla team has been releasing newer versions of Firefox without a slew of new features, focusing on fixing bugs and getting the improved product out as quickly as possible, in order to compete more rapidly with other browsers like Google Chrome.

Google+ Hangouts are proving to be a proficient platform for teaching and communicating in real time with others. If you're someone who creates instructional content online, you may want to consider using the platform for your next project.

Video games are the most prevalent type of interactive media, but certainly not the only one. The interactive music video for the song "3 Dreams of Black" by supergroup ROME and digital artist Chris Milk utilizes the latest web design technology, video game influenced art and interactivity, and large crowd-sourced elements to form a compelling work of art. ROME is composed of producer extraordinaire Danger Mouse, Italian film composer Daniele Luppi, Norah Jones, and Jack White. Their recent e...

The Free Art and Technology Lab (F.A.T.) has provided three different energetic and passionate methods for voicing support for Ai Weiwei, the famous Chinese artist and activist who has been detained without known reason by the Chinese government since March 31st.

At Google I/O this morning, Google finally announced the launch of its much awaited Google Music service. It's currently in invite-only beta mode, but they claim it will open up to the masses soon enough. To start syncing your music library with Google's Cloud now, you need make sure you're signed into your Google Account, then click here for a personal invite. It's currently free for a limited, undisclosed amount time.

Warning If you don't trust that these steps are safe or that they won't work, than have your computer/laptop backed up so you can restore it if necessary.

Does your network begin to crawl right around the time your sinister-looking next-door neighbors get home from work? Do you harbor suspicions that one or more of them may be stealing your Wi-Fi? It's easy to find out. And equally easy to give freeloaders the boot. In the guide below, we'll show you how to secure your wireless connection in three easy steps.

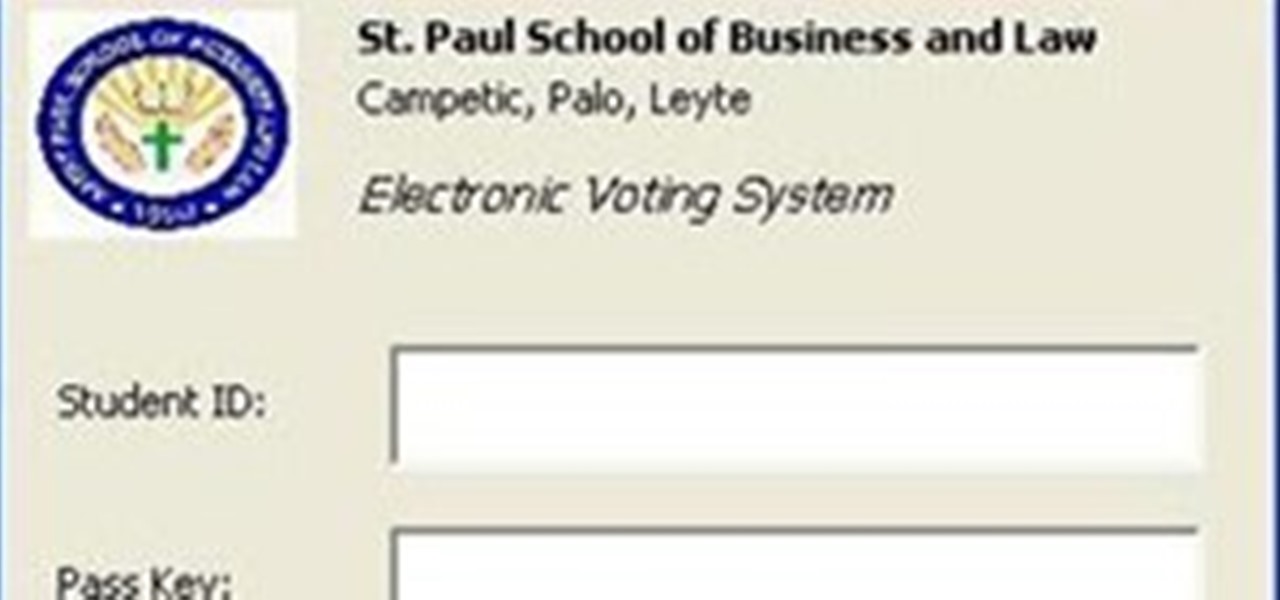
Tomorrow is another day of election (PSG). I have to wake up early to set up the computers on both computer rooms. The election process is computerized, making the counting of votes the responsibility of the computer. What makes this year's election special is that for the first time in 3 years (correct me if I'm wrong), there are competing parties. The result is something to look forward to especially for me who contributed in the creation of the system.

Flash video. It's what all smartphone users have been waiting for. Why has it taken sooo long? And why is Apple still resistant?

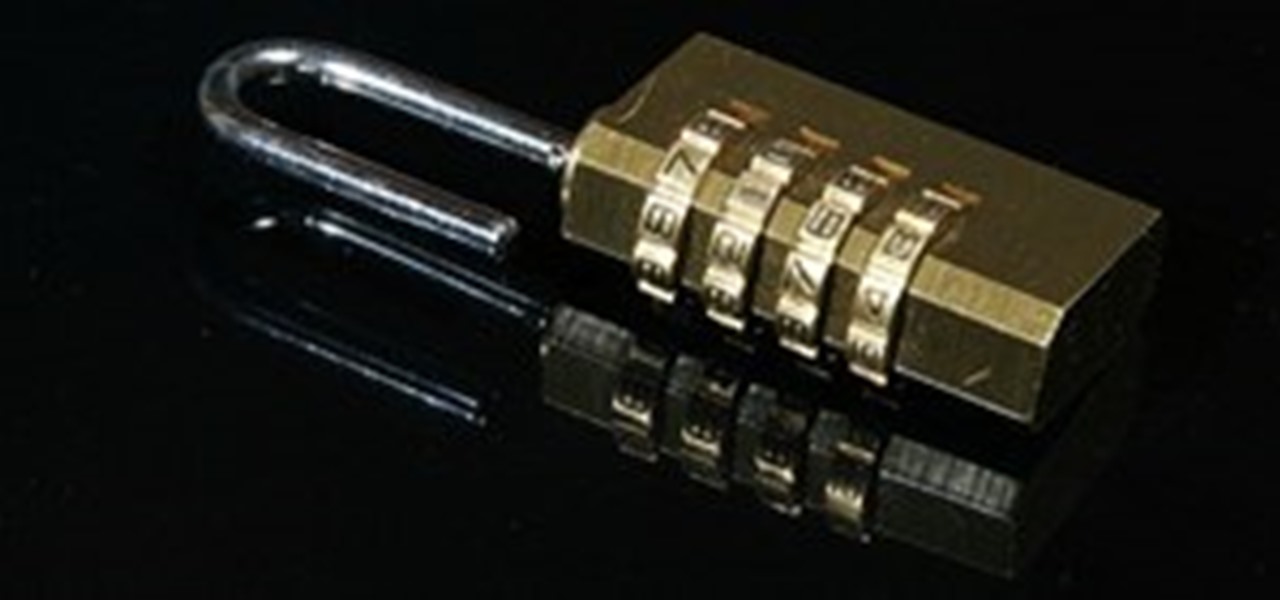
Lifehacker posts an article on the art of cracking weak passwords, courtesy of Internet standards expert, CEO of web company iFusion Labs, and blogger John Pozadzides. Pozadzides certainly knows a thing or two about password logic. (Note: this information is not intended to hack into accounts, but rather to protect you from using weak passwords).

This step by step tutorial teaches you how to apply gothic spider web eye makeup. This is a cool look for Halloween or a costume party. Watch this makeup how to video and you will be able to create a gothic spiderweb eye look. Apply gothic spider web eye makeup for Halloween.

This video will show you how to bypass those pesky home or school web filters Bypass school or home web filters.

This video will show you how to create a simple and quick web photo gallery in Adobe Photoshop. Create a web photo gallery using Photoshop CS3.