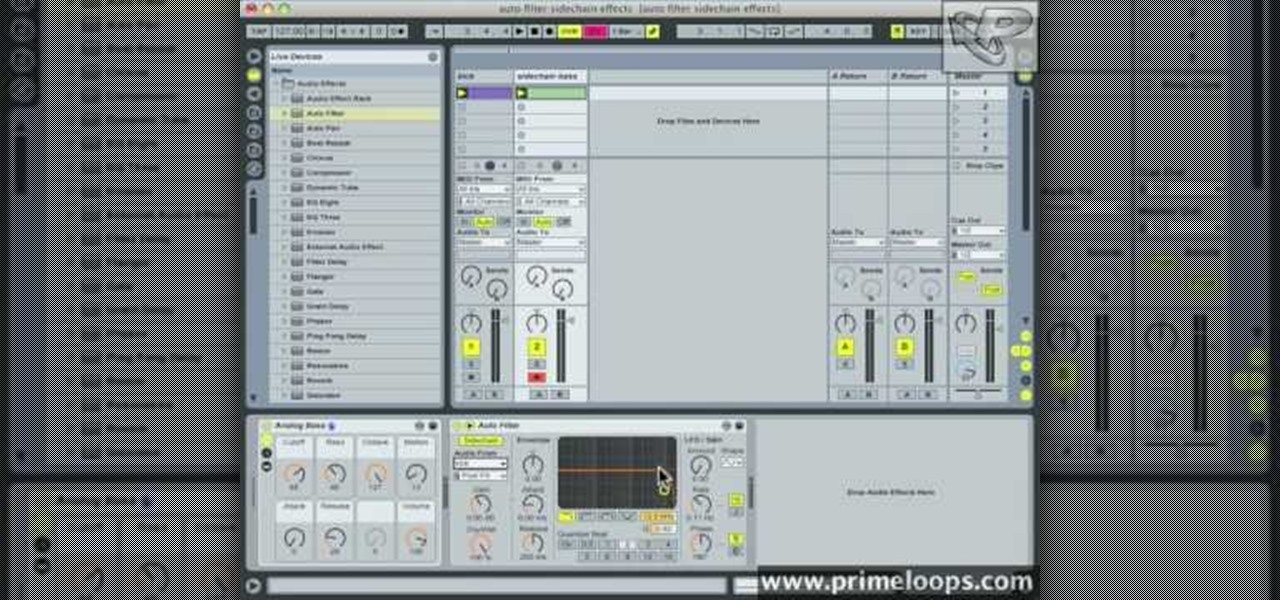
Open your program to a new live set. By using three keys (in Ableton Live), Command (Ctrl), Shift and t, you can create a short cut. Create two new midi tracks making one for (side chain) bass and one for (side chain) kick. To rename a track choose the two keys Command (Ctrl) and r. Next, you can load up the presets, located on the side bar list, one a bass, and, then a basic kick drum by opening up impulse, electronics and Tremor 1994. Now create a couple of patterns. To do this go an empty ...

Create a hand bag using a plastic bag with this video tutorial. We really have to do something with these plastic bags, it spoils nature so dramatically.
A Membership Provider allows a web application to store and retrieve membership data for a user, and the standard ASP.NET Membership Provider uses pre-defined SQL Server tables. In this video tutorial, Chris Pels shows how to create a custom membership provider that uses custom SQL Server tables separate from the pre-defined tables used by the standard provider. The principles covered in the video will apply to creating custom membership providers using other databases such as Access or Oracl...

How to Build a Basic BirdhouseMaybe you were outside in your back yard and you noticed that it seemed a little lonely and empty. Our maybe you have young kids that love to experience wild life in their own back yard. Whatever reason you have for searching out this article, you have decided to build your very own basic bird house. I recently built a deck in my back and had alot of scrap 1x6 decking boards left over. Instead of letting all that good material go to waste, I decided to build a co...

TCP/IP Client / Server Application Hello! Today's blog post will be about coding a very rudimentary Client and Server application duo, which will communicate by using TCP Sockets.

Welcome to Minecraft World! Check out our advanced tutorials and come play on our free server.

Despite a round of updates to Pokémon GO that patched and eliminated location spoofing, the game still has a difficult time dealing with the most hardcore cheaters. Like weeds on a grassy lawn, third-party bot makers still remain the biggest thorn in Niantic's side and continue to thrive despite the developer's best efforts to root them out. While the latest updates have blocked users from running modded versions of the game, like Pokemon GO++, that feature built-in joysticks to move your pla...

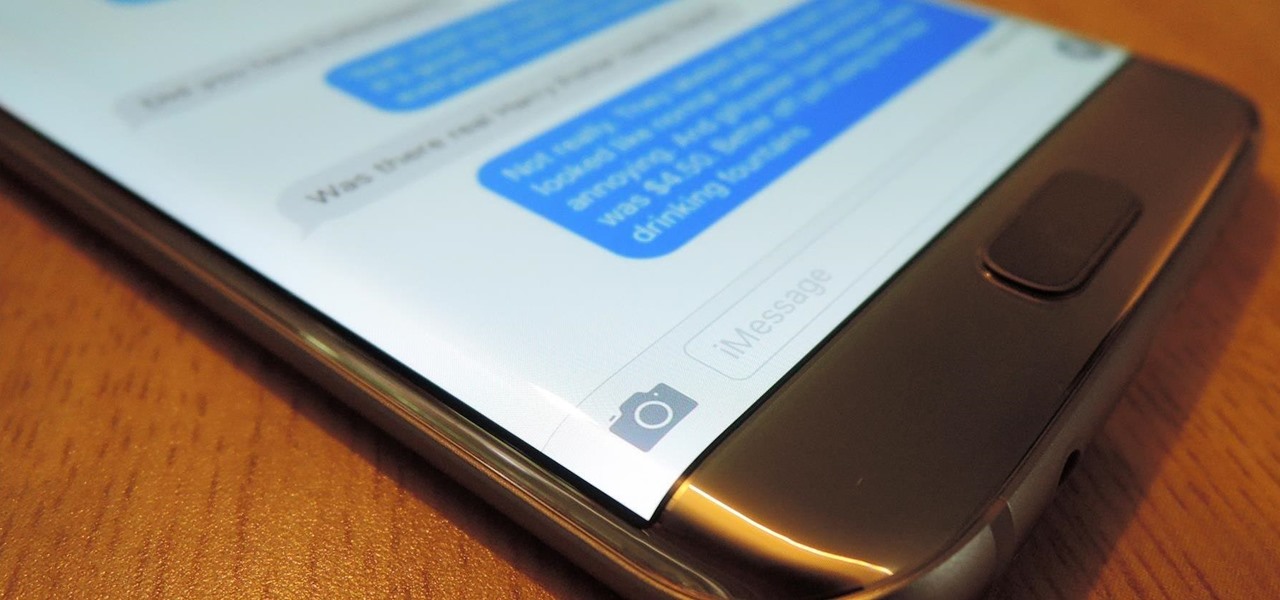
Android phones may soon be able to send and receive iMessages thanks to a new open-source app called PieMessage.

Hello ladies and gentlemen, PySec here coming at you with another informative(hopefully) article for you all. In the last tutorial, we finally finished our discussion about IP Addressing and I intentionally didn't mention a really important concept with which IP Addressing wouldn't be feasible without it. What I'm talking about is how our network device gets the IP Address in order to communicate with other devices on the network/Internet. There are many different ways for that to be accompli...

Today I will show you how to make a metasploit exploit really quickly. This tutorial is mainly applied to stack based buffer overflows and seh buffer overflows exploits .There is a simple way for rop exploits too but I will dedicate a special tutorial on this subject.

Hey guys, today I bring you the fabulous BronzeSMP Server series! I hope you guys will enjoy this video as much as I enjoyed making it!

Still working on mega project builds. This one is going into my own PVP server which (will) contain 4 theme'd biomes inside of a 155m sphere - inside of a 255 meter containment sphere inside a 1000m+ void. The outer sphere acts as both artificial sunlight and a drop-death height of 50m. 4 more outer panels to go (water and lava) and it's ready for interior work and redstone - including command-block powered proximity traps that don't have any triggers marking them as well as hidden walls that...

A good cutting board is almost as important as the utensils you use on it. The wrong type can cause your blades to dull faster, and certain materials hold onto juices (and therefore bacteria) from food. You can wash a plastic board with just about anything, but what about wood?

For over 20 years, a tiny but mighty tool has been used by hackers for a wide range of activities. Although well known in hacking circles, Netcat is virtually unknown outside. It's so simple, powerful, and useful that many people within the IT community refer to it as the "Swiss Army knife of hacking tools." We'll look at the capabilities of Netcat and how the aspiring hacker can use it.

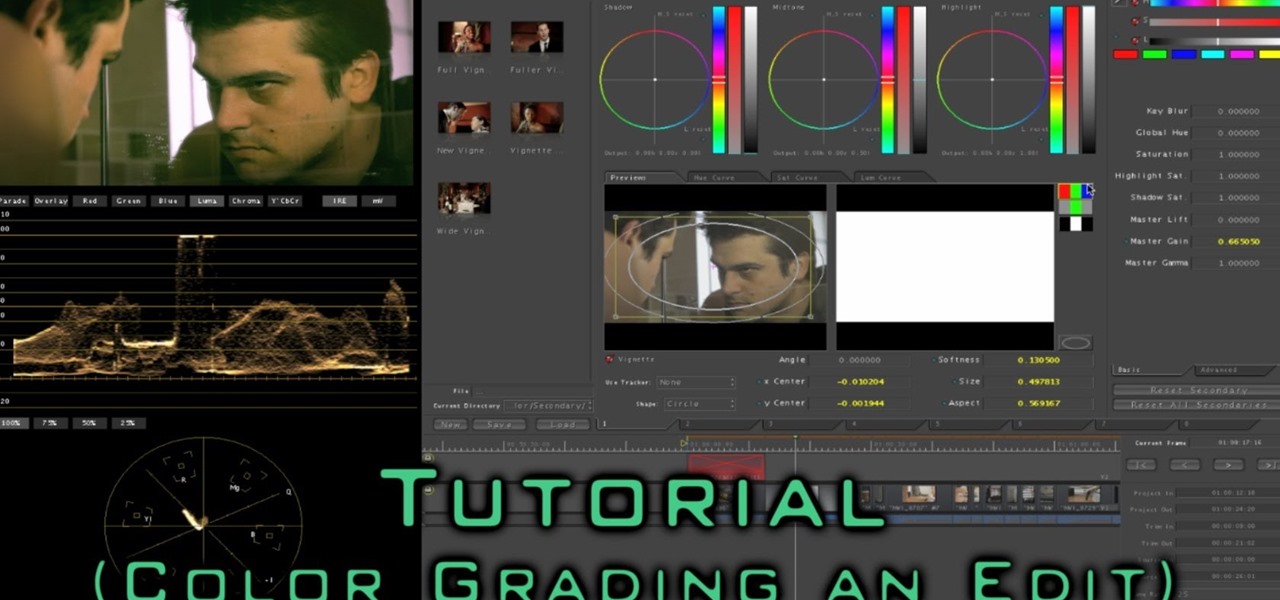
Hey Everybody, I have uploaded a new video tutorial on: How to Color Correct / Color Grade an entire sequence using Final Cut Pro 7 and Apple's Color.

Steam is an online platform that lets you download and play over 2,000 video games, from first-person shooters to RPGs, as well as a pretty long list of indie games. You can play on your PC, Mac, mobile device, or even your television, and it has a community of over 40 million gamers. Prices are different depending on the type of game and how new/popular it is, but they're generally about the same as what you'd pay for an Xbox or PlayStation version. They also have a decent list of free games...

In this tutorial, we learn how to make an adorable Barbie princess birthday cake. First, get 3 (8") round cakes and trim the dome off 2 cakes. Now, cut a small circle in the center of each cake, big enough to fit a Barbie body through. Now, spread icing along the inside of each of the cakes, using a big dollop on each cake. Place the cakes on top of each other then apply a thin layer of frosting to the entire cake. Place the cake in the freezer, then place a final coat of frosting onto the ca...

A CNC router machine is probably the most useful tool a hobbyist can own, but the price for a CNC machine on the market is way more than the average hobbyist is willing to spend. You can build your own CNC with very basic tools, little knowledge of machinery, mechanics, or electronics, but be warned, these machines are inherently dangerous, so wear the proper protection and use common sense. At the very least, read the instructions and precautions on every tool you use.

This video is a walkthrough for the final level in Braid, called Hesitance. You're so close to finding your Princess! In this world, you can use your ring to slow down time while you solve all the puzzles to collected your pieces.

Check out this video and learn how to get the most out of your characters in Final Fantasy XIII. Each character has a different focus when it comes to fighting. In this clip, you will get a quick overview of what each character is good at so you know how to best level them up as you go through the game. Follow along and keep track of your team's strengths and weaknesses so you can dominate FFXII.

This video tutorial will show you how to create a hair look like Rikku from Final Fantasy part 3. This hairstyle is totally perfect for Cosplay, or if you are daring - everyday wear!

This video is a demonstration of the proper way to cut up a cabbage. Large vegetables like cabbage can be hard to cut up because they are so big and tend to move around on the cutting surface. The first thing to do is to create a flat surface, so make it safer to cut. Cut the whole cabbage in half holding the end of the core on top. Cut the core out of each half in a big V shape. Cut it in half again to make quarters. Take the cabbage apart so that you can flatten it out and cut thin slices f...

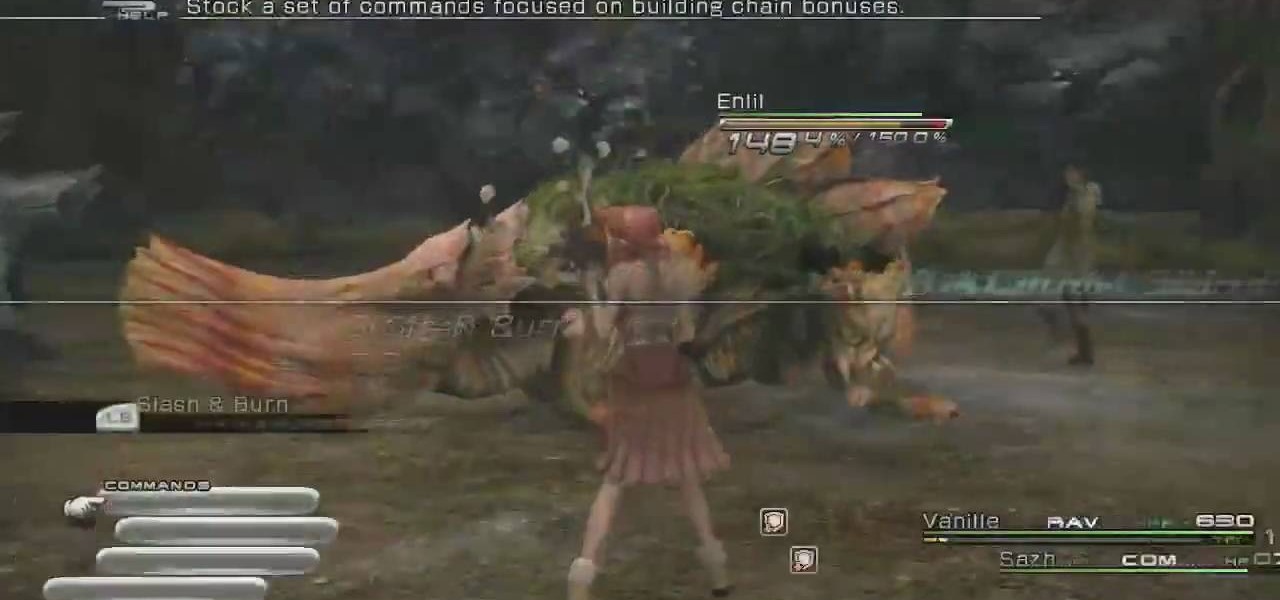
In this how to video, you will learn how to defeat Enki and Enlil in Final Fantasy XIII. You will need Final Fantasy XIII in order to do this. One of them is weak against water, and the other is weak against lightning. Cast deep protect on your guys first. If you want to fight them both at the same time, use slash and burn. Try to keep your health over 50 percent. Also, watch out for the bellow cast. Keep Vanille as a medic so that your health does not go down too far. If you fight them both ...

Scraping cuts in woodturning are used to smooth wooden items cut with other tools, and to shape items that are difficult to shape with gouges. Learn about various scraping cuts from a woodturning expert in this free crafts video series.

Ready to put an end to this "mad world?" This video shows you a simple way of defeating Pale Horse, the final boss in Gears of War.

Here's a quick and dirty little series on the very basics of non-linear editing. If you're not using FCP, don't worry, every non-linear editing software package functions in more or less the same way.

Larry Jordan demonstrates the basics of audio repair using Apple's Final Cut Pro including raising soft recordings without distortion. This is a great tutorial for beginners. Repair audio in Apple Soundtrack Pro.

Minecraft 1.8 has introduced Enderman to tons of blocky servers all over the world. If you're looking for ways to fight against Enderman or just avoid Enderman all together, take a look at this walkthrough on how to do both. Be sure to grab an Ender Pearl so that you can half their attack range!

Most recipes usually don't call for whole vegetables, which means that if you're learning to cook, you'll eventually have to learn how to cut vegetables.

Find which airlines Google is providing free Wi-Fi on this holiday season, fix shutter lag on digital cameras, wipe your hard drive for free, improve your Wi-Fi router performance, adjust your television and monitor for accuracy, choose the best 1080p projector, use a single server that can handle OS X, Windows & Linux simultaneously, and use the best audio encoding system for Windows Media Center and Zune.

In order to cut into a fresh pineapple, you will need a sharp knife and a cutting board.

Finally, the professionals are weighing in on how to create fake wounds! This video features a makeup artist from the BBC demonstrating how to make a really realistic fake cut on the hand of an actor using theatrical makeup. The plastic pieces from a CD jewel case that resemble broken glass really set this cut apart from the other fake cuts on the site, along with the professionalism of the presenter.

Cutting fruits can be difficult if you don't know how to do it. Not only that, but it can result in you wasting precious fruit that you could have easily eaten. So in this tutorial, you'll find out how to cut a pineapple using a simple and easy method. It's a fruit that looks hard to cut, but in reality is quite simple. Enjoy!

Everybody has a drawer full of awkward oversized t-shirts in their bedroom, right? Turn those bulky tees into cute 80's style cut up tops! In this four part video, Kandee gets crafty and turns those tops inside out and upside down! Make halters, off the shoulder sweats and other styles along with Kandee.

We know what you're thinking: You have two left hands and even cutting in a straight line is a monumental feat. But trust us, even butterfingers can cut their bangs professionally. In fact, if you tend to cut slightly slanted or jaggedy then your bangs will look even better!

XAMPP is a free install program you can use to turn your computer into a web server. This video also has a installation guide for XAMPP

Final Fantasy XV, the latest release in the long-running Final Fantasy franchise, has been a massive success, shipping around 6 million copies worldwide in less than two months. Final Fantasy XV: A New Empire is a mobile game based off this popular console iteration, and has surfaced in New Zealand for download.

When I tried to set up an eviltwin for a MitM-constelation in kali 2.0, I couldn't provide internet to the victim. The origin was the brctl bridging. I have read many tutorials but all of them where explained in backtrack and older versions of kali. So i was searching for a solution without using brctl and this solution will be explained now. This will just work on unencrypted wireless-environments.

Welcome back, my fledgling hackers! Sometimes, for a variety of reasons, we can only get a command shell on our target system. For instance, with Metasploit, it's not always possible to get the all powerful Meterpreter on our target system. In other cases, we may be able to connect to a command shell via Netcat or Cryptcat.

Welcome back, my hackers apprentices! To own a network and retrieve the key data, we only need to find ONE weak link in the network. It makes little sense to beat our heads against heavily fortified systems like the file and database server when we can take advantage of the biggest weak link of all—humans.