When I left off on our last hack, we had hacked into the ubiquitous Windows Server 2003 server by adding ourselves as a user to that system so that we can return undetected at any time. The problem with this approach is that a sysadmin who is on their toes will note that a new user has been added and will begin to take preventative action.

Welcome back, hacker novitiates! In the next few hacks, we will be breaking into Windows servers. In this installment, we will learn to add ourselves as a user to a Windows 2003 server. Of course, when we have added ourselves as a user, we can come back any time and simply log into our account without having to hack into the system and risk detection.
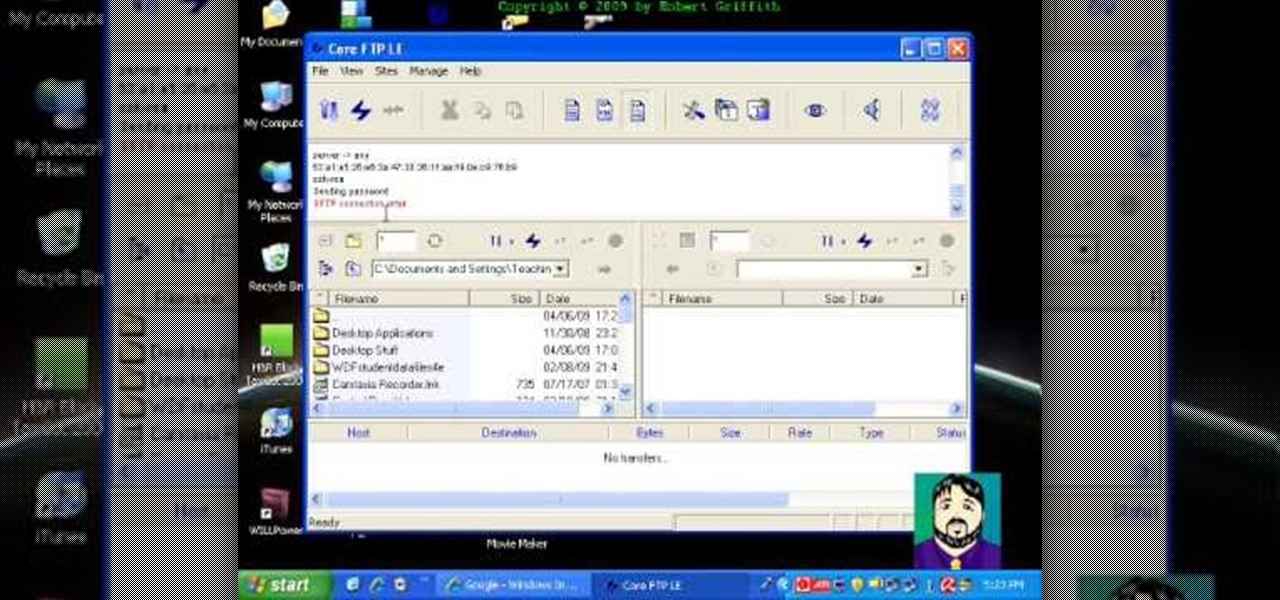
Select an FTP client that allows you to connect to the webserver. Download a free Core FTP Le software. Install the program. Use the site manager to name the internet site. Create a host/url, a user name, password and a connection. Connect to the web server. Create an index file to make files viewable. Open the Core FTP LE software. Drag files from the desktop (left side of the dialog box) to the internet server (right side of the dialog box.)

In this video presenter Dominic shows you how to use a Jig Saw correctly. Dominic suggests that if you are going to make a tight turn then you should use a skinnier blade in order to avoid banging up the wood or breaking the jig saw blade. He adds that you should be patient and try not to go too fast. With the jig saw you first have to drill a hole in the wood and then put the jig saw through as the blade is flexible and cannot be pushed through by itself. He suggests trimming off the first p...

So you beat the final boss in Final Fantasy VII and it seemed way too easy considering the amount of time you've invested into this epic game. There are two additional hidden bosses in the US version of Final Fantasy VII: Emerald and Ruby Weapon, both of which are substantially more powerful than the final boss. In order to even contend with the game's hidden bosses, your characters will need to be maxed out. Take a look at this instructional video and learn how to max out your party's streng...

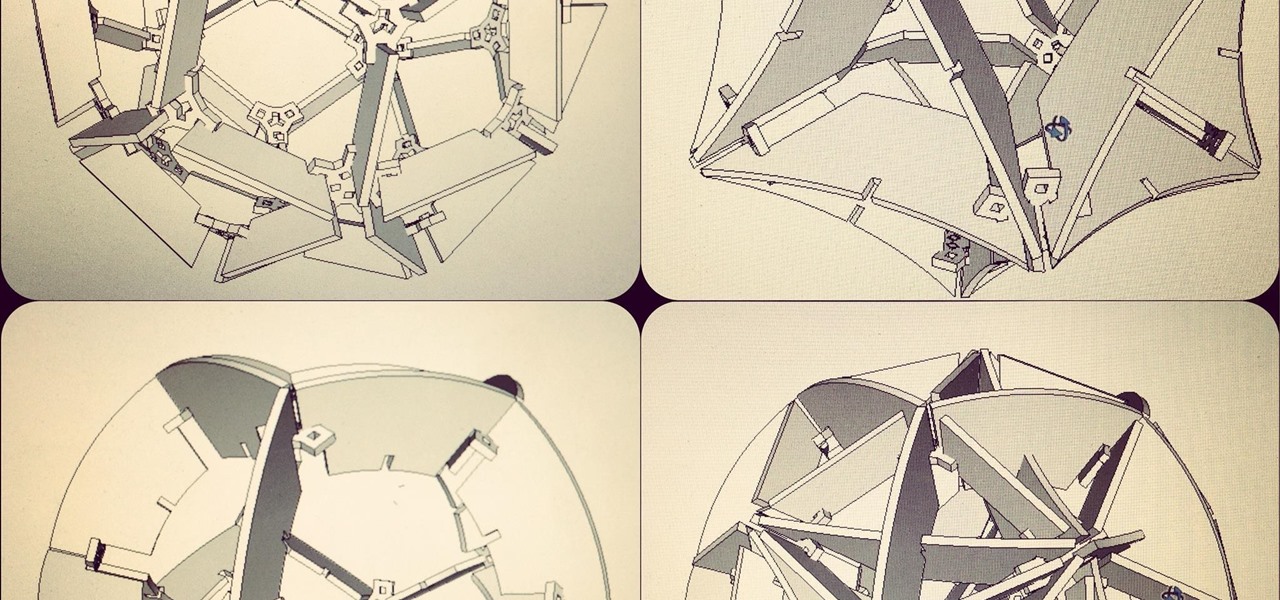
These drawings were made with Google SketchUp. There is a dodecahedral model, icosahedral model, and a third I don't know the name of, made of rhombic faces obtained by connecting vertices of the other two. The final image is all three models together. I'll use a ShopBot CNC router to cut out the pieces this week.

SQL Server Reporting Services allows you to design and deploy nicely formatted and interactive reports representative of your data. Suitable for print or online distribution, these reports and it allows you to get professional results very quickly. This video demonstrates how to set up Reporting Services and the Business Intelligence Development Studio to build reports using the wizards and design. Use SQL Server Reporting Services.

This video helps you to understand the differences between programming languages like PHP and Java Script. See how to understand and be able to use server and client based programming languages. This is VERY important to know before you start developing websites. Understand server-side vs. client-side programming.

Does a bob haircut remind you of flappers from the 1920's? Originally, the hairstyle (as worn by flappers) was meant to be an androgynous cut, boyish in length and style.

This video is a demonstration of how to cut up a T-shirt, inspired by 80's rock band fashions. Use a regular white T-shirt and start by cutting a deep scoop neck out of it, starting about an inch outside the neckband. Turn the shirt over and fold it in half Snip horizontal lines down half of the shirt all the way down. Then stretch out the thin strips. Cut the other side of the shirt the same way. Cut the sleeves off completely so it's more like a tank top. Wear the shirt over another tank to...

How to prepare bok choy for Chinese food

This is a video that demonstrates how to cut up a pineapple for a healthy snack. She places the pineapple on it's side and then cuts one end off and then the other. She then stands the pineapple up and cuts around until all the outer part of the pineapple is gone. She slices down the side of the pineapple in strips, turning it after each strip is removed. She then cuts the pineapple in half. She then cuts it again and removes the core, doing that to both of the larger pieces of pineapple. She...

Want to play your video collection on any media extender, console or AppleTV? Step one is to get your movies off of the DVDs and onto your hard drive! If you're like most people you probably have a huge library of DVDs that you've bought and collected over the years. Unfortunately, it's an inconvenient format if you want to playback all that content anywhere around the house. So, learn how to rip and encode that stack of DVDs into a format that you can play on your Windows Media Extender, set...

This tutorial covers the ABC's of getting started in Web Development. Mike Lively shows you how to get a server, a free HTML editor, and free FTP Software.

Nearly every connection to the internet is dependent on the Domain Name System. DNS, as it's more commonly called, translates domain names like gadgethacks.com into IP addresses, which is what network devices use to route data. The problem with DNS servers is that they don't have your privacy in mind.

If you have friends who aren't privacy-conscious, you've surely heard the old "What do I have to hide?" excuse. Despite the fact that billions of people are using the internet each day, many of them don't know the dangers that can find them. And many don't know the tools to combat them.

With a simple social engineering trick, sudo passwords can be captured in seconds without the target's knowledge. The passwords can then be saved to a file or exfiltrated to another computer on the network.

Welcome back, my greenhorn hackers! A few years back, Microsoft implicitly recognized the superiority of the Linux terminal over the GUI-based operating system by developing PowerShell. Since Windows 7, every Windows operating system has had PowerShell installed by default, and they even made PowerShell capable of running Linux commands on Windows!

Macs are generally highly power efficient due to, in part, the optimized sleeping schedule with OS X. Yet in certain scenarios, you might not want your Mac to go to sleep: downloading a huge file, reading a book, reviewing a spreadsheet, analyzing some content on the screen... the list goes on. To resolve this, you can go to System Preferences and mess with the settings, but this can be an annoying process if you need to do it often.

Hello fellow Nullbytiens, today we will be talking about IRC again (if you haven't read OTW's post about head over there now)and more specifically about using 1 nickname with multiple devices or IRC clients.

I saw many people asking for a Tutorial about writing their own Remote Administration Tool, so I now introduce you in a basic kind of RAT. This program is not for real use, but for learning how you could write this kind of tool. It will be basicly coded and not very refined. I used Python 3, so you have to install it if you want to use this program unchanged. Also this RAT is for Windows and almost all features won't work under Linux.
Hello Strangers, This is my first article for null-byte and its about staying anonymous on the Internet. But the question is why would you want to stay anonymous online?

Welcome back, my budding hackers! With this article, I am initiating a new series that so many of you have been asking for: Hacking Web Applications.

Welcome back, my fledgling hackers! A short while ago, I did a tutorial on conducting passive OS fingerprinting with p0f. As you remember, p0f is different from other operating system fingerprinting tools as it does not send any packets to the target, instead it simply takes packets off the wire and examines them to determine the operating system that sent them.

Whether you've been fully converted or just want a little Apple with your Android, adding your iCloud email to your Galaxy Note 3 is a fairly simple task. Usually, Apple and Android don't play nice, but your iCloud address can be added to your stock email app just like any other email account.

Issue 287 of the Nanoc the Obliviator level of the game Comic Jumper on the Xbox 360, is the final section of the medieval setting of the game, similar to Thor and other. In this video you will get a complete walkthrough of the final section of Nanoc the Obliviator and also all of its achievements.

In this tutorial, we learn how to make an Android doll at home. First, print out the Android logo from the internet, making it large enough to make a doll. Now, cut out the print out with scissors cutting out the different sections individually. Next, place the cut outs onto a piece of green felt, then pin it down so it doesn't shift around. Now, cut around the paper so you get the same pattern. After this, cut out all the other parts, making two of the shapes so you have a top and a bottom. ...

Brian demonstrates a simple method of cutting a pineapple in this entertaining video. He starts reviewing some pineapple research. Pineapples are named after pinecones! Brian also discusses the concerns of eating pineapple for people with certain health conditions. First twist and pull off the flower top of the pineapple. Then cut off the top and bottom of the pineapple so that they are both flat surfaces. Then cut off the skin of the pineapple, retaining as much of the flesh as possible. Use...

The 190 Helix cut is a pretty cool false cut that you can do with cards. When you cut the cards, the queen of hearts-which was there at the beginning-is somehow still on top after the cards seem to have been sufficiently cut. What you need to do is separate about ten cards from the top with your finger. Lock that in the opposite hand between the forefinger and thumb. Now put your ring finger down and flip the cards back. Do this and continue to rotate the stacks of cards so that the small pil...

Learn how to dice any kind of onion or shallot. First cut the ends off of the onion, being sure to remove only a little bit of the root end. This is so the onion stays together when chopping. Make vertical cuts in the onion starting from the opposite end of the core. Then make horizontal cuts only cutting 3/4 of the way through. Then cut across to dice the onion.

In Boca Al Lupo: The end is almost here. This is the last mission you will need to complete. Talk to Mario and he'll send you on your final mission, to assassinate Rodrigo Boriga in the Vatican in Rome. The mission is more linear than any other you've done up to this point, and it requires much stealthiness. But at first, it requires you break into the Vatican. Climb the wall to the west and use the beams sticking out from the wall to jump to a hanging platform to the south.

Machinima.com holds your hand through the 5th and final Prince of Persia Walkthru.

Woodturning uses skew and gouges to create designs in wood on a lathe. Learn about making cuts with these tools from a woodturning expert in this free crafts video series.

Saving the world an be costly and in Final Fantasy VII, a part of leveling up is to get the funds you need to buy weapons, potions, and materia in your quest to defeat the villain Sephiroth. In this now classic Final Fantasy game, selling mastered materia can be extremely lucrative, particularly All materia. Take a look at this instructional video and learn how to get quick gil by defeating rare Magic Pots in a specific area of the game.

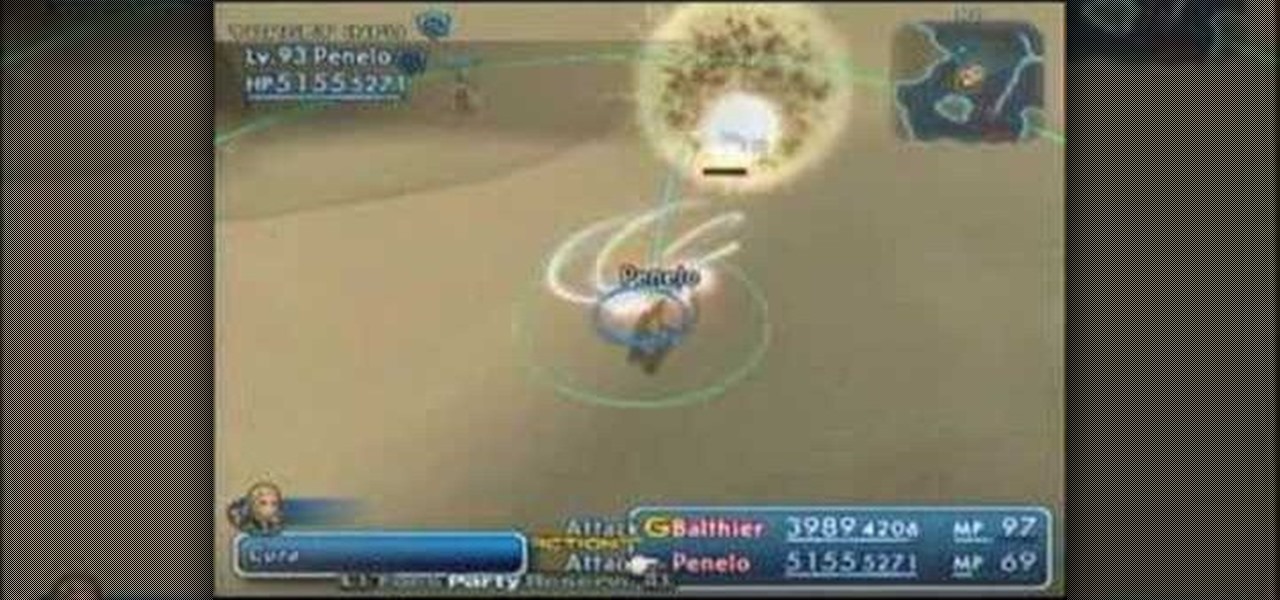
Like the previous Final Fantasy games, the latest installment Final Fantasy XII on the Playstation 2 has hidden bosses to test the mettle of hardcore RPG gamers. The Gnoma Entite is a hidden boss you can find in the Midfault area of the Damasca Wasteland following a sandstorm. Take a look at this instructional video that shows you how to take on this boss even with characters with weak equipment and abilities.

This video playthrough shows the final cutscene and the easiest way to beat the final mission against the mob in GTA: Vice City.

How to Make the Internet Faster in Windows 7 Go to Control Panel.

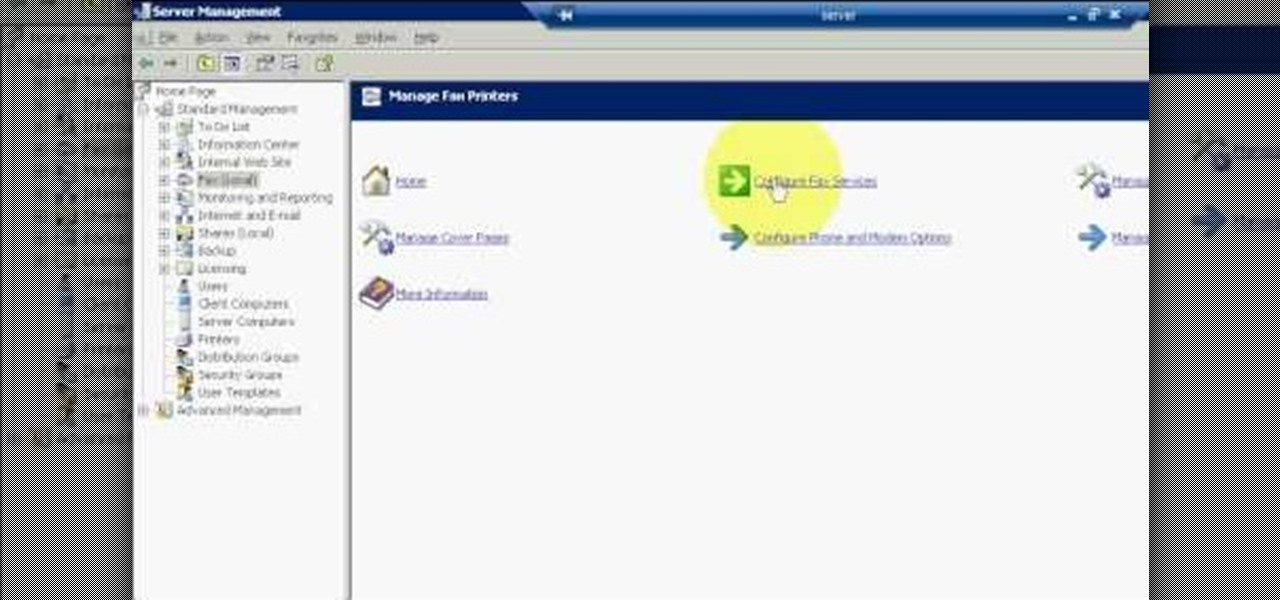
The first step to create a fax using Outlook 2003 and 2003 server. Using add/remove windows component make sure your fax equipment is properly installed. Under the start menu select the printers and fax option and select the share option. Then under administrator tools/users/new/users/fax to enter your password to turn our fax information transfer on. You must now select fax user and select advanced settings and double check to make sure the fax is able to see the object it needs to send the ...