In this Food video tutorial you will learn how to clean and cut a leek for cooking. This is really very easy and simple to do and takes very little time. A leek has a green part at one end, then the white part and the roots at the other end. Never cut the root otherwise, you will not be able to hold it together. Cut off the dark green part. You can use it for stock or soups. Then you got to clean the leek. Holding the root end, make a long slit with the knife, turn it a quarter and make anoth...

Do you ever want you hair to appear short, but feel that cutting it is the only way? Well YouTips4U has found a unique and creative strategy to making your hair appear short without even having to cut it! It's a simple process and all you need is a ribbon of your choice. YouTips4U shows you a few different basic styles and tips you can use to make your hair look short and beautiful. So if you are looking for a short new look for your hair without the cut, this is the video for you.

This video describes how to skin a pheasant to prepare it for cooking and get the most out of the meat. The presenter starts by making a cut longways along the breast bone of the pheasant. Once you make the small incision you can peel the skin and feathers off of the pheasant. The presenter indicates that the main areas of meat are the breast area and the thighs. Next is cutting along the bones into the chest cavity and separating the collar bone. Instead of "gutting" the pheasant, the presen...

Home improvement expert Danny Lipford teaches how to cut drywall around outlets Just watch the video tutorial to see how to cut drywall around electrical outlets.

To make a support halter top shirt, you will need: Pattern for a basic bodice

Plastic bags on their own aren't quite strong enough to hold anything too heavy (at least not for an extended period of time), but when broken down into "plarn" - plastic yarn - they can be woven into some very sturdy fabric.

John White discusses how to propagate houseplants. You will need a potting mix called a “soilless” mix, which contains only vermiculite, perlite and peat moss. In addition you will need a sharp knife, a pruner and a weeding hormone to help induce root growth on the cuttings.

Vicky Taylor from The Crafts Channel teaches us how to transform an old pair of jeans to a trendy denim mini skirt. Get a pair of denim jeans and cut the front side from the end of the zipper downwards to the crotch. Do the same at the back making sure that it is at the same length on the front. Measure the length of the skirt you wanted. Cut it off and make sure they are the same length. Overlap the flaps created at the front and stitch them together. There will be a triangular open part at ...

Cooking With Dog shows you how to make hamburg steak that's delicious. - Finely dice an onion

This week's recipe is a Secret Ingredient team favorite. Not only is it a brilliant use for leftover bread, it's a lively salad of peppery arugula tossed in roasted tomato vinaigrette, topped with toasted goat cheese and generously garnished with Whole Catch™ Wild Caught Crab. Summer salads don't get much better than this!

This is a 3 part series produced by modo community member Paul Hartsuyker. The series was created in response to a challenge presented to the modo community to model a complex folded die cut package. Follow along with this modo tutorial and learn how to create advanced package designs like this die cut package. Create a complex folded die cut package in modo 203 - Part 1 of 3.

Learn how to make your very own Japanese Yamaha paper craft motorcycle YZR-M1! These easy-to-follow instructional paper craft video clips explain everything from basic paper craft techniques and how to make major parts of the realistic paper crafts, right up to the final assembly of your Yamaha motorcycle YZR-M1. These paper craft videos are full of useful tips for efficient construction and superb finish! Watch it, and you'll want to make a realistic paper craft motorcycle yourself!

When you're out and about in the dangerous world of Wi-Fi, it's hard for the average computer user to stay protected, or even know what being protected entails. Little do most people know, Windows 7 has a built-in security that few people take advantage of: a VPN (Virtual Private Network) server and client.

If you have an iPhone or an iPod Touch then you probably think that the only places you can listen to your MP3 files are on your laptop, your i-gadget of choice, and your car. But in reality anything that you can groove to on your iPhone or iPod Touch can be listened to - and transferred to - your PlayStation 3.

In this video, we learn how to pull a compilation of computer pranks on a friend. The first trip is a mouse prank where you will open up the control panel and find the mouse settings. From here, you can switch the buttons from left to right and change the speeds of the mouse. Next, you can do network pranks by running cmd.exe as administrator. Then, go and see who is on the network and type in "msg /server:(ip address) and message". You can also do a ghost typing prank, which you will create ...

You hunt and you hunt, but you can never find the right pillows to go with you couch. Even your reupholstered chair needs a little pillow love, but it seems impossible to find the right color and design to make a perfect match. That's when you know it's up to you save the day. Why settle for simple decor when you can make your own chic throw pillow to match any room?

Your iPhone may be great, but like any other mobile device, it might be wasting more battery power than it needs to. If you want to learn how to conserve your battery life, there's plenty of precautions you can perform. So what all can you do? Best Buy has answers. The Best Buy Mobile team explains how simple it is to maximize the battery life of your Apple iPhone. You can put it in standby mode, reduce screen brightness, and turn off Location Services when you're not using them.

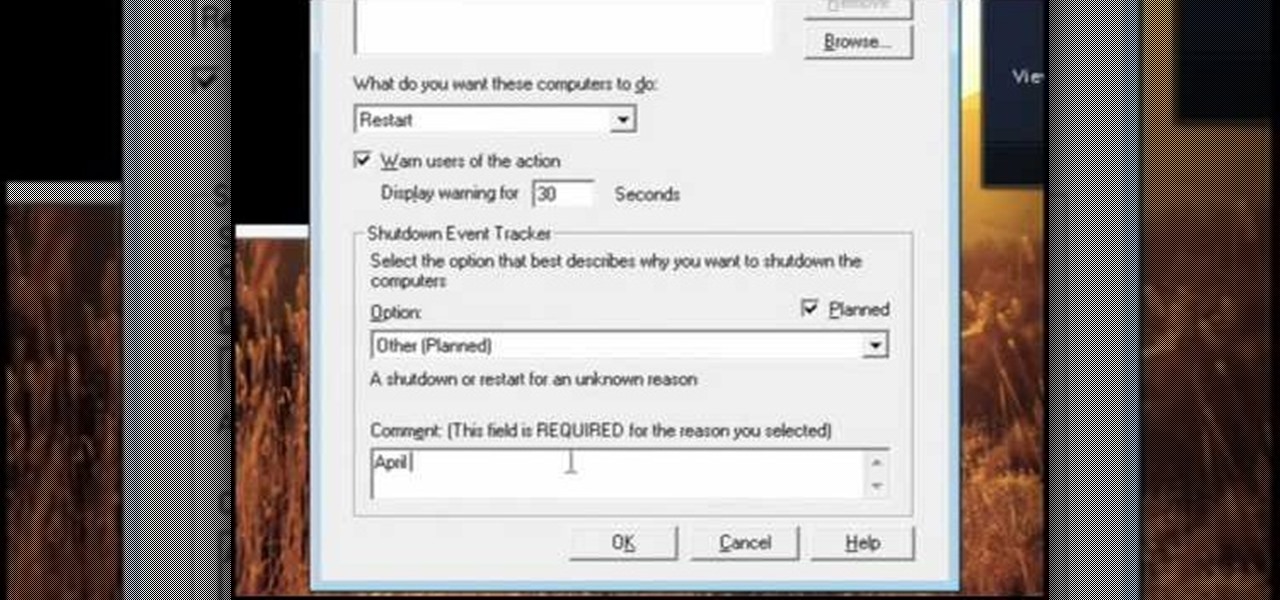
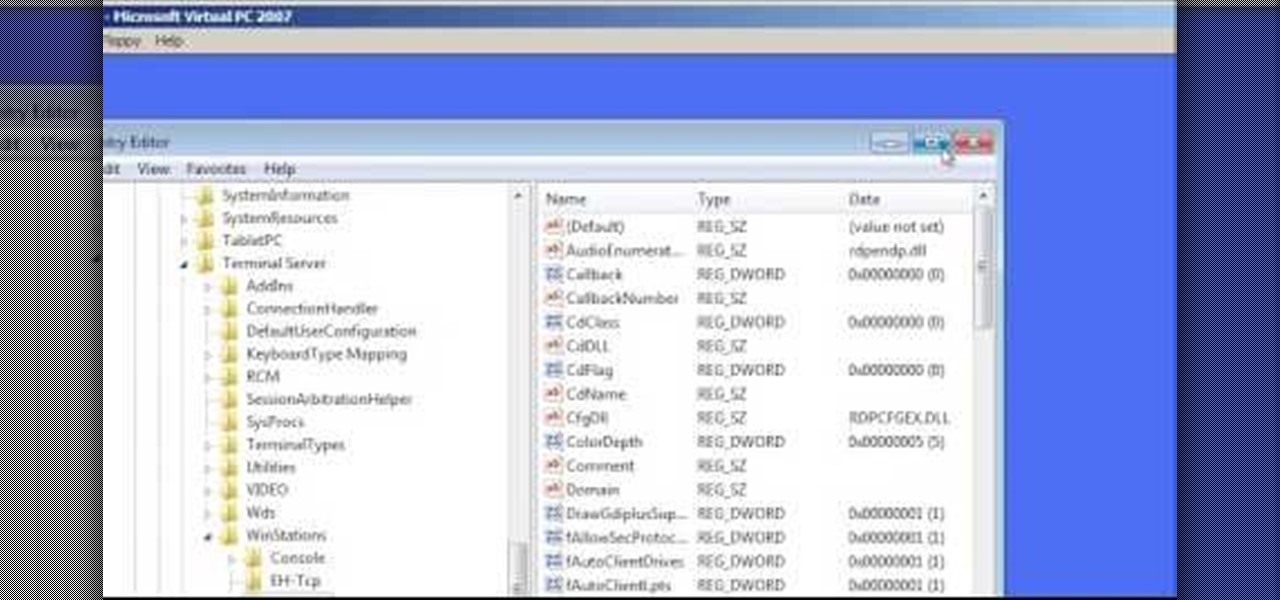
In this Computers & Programming video tutorial you will learn how to change the default Windows Remote Desktop port. It is actually a registry hack. You can check the IP address of our machine by typing ipconfig into the cmd prompt. For hacking into a machine, you should have created a user for the machine and allowed remote desktop to that user. Open up the remote desktop and type in the IP address and it will ask for a login. To hack the registry, click start and type in ‘regedit’ . now go ...

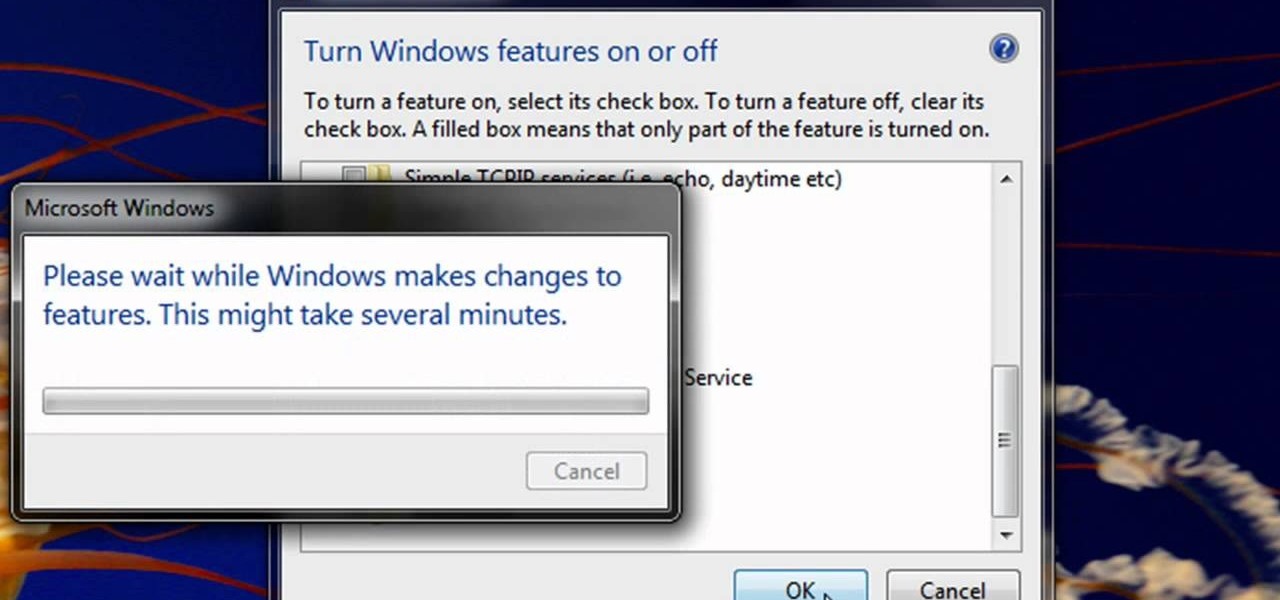
Enabling Telnet in Windows Vista is a little bit more difficult than its predecessors but it still can be done. This video will demonstrate exactly how to enable Telnet in Windows 7 and Vista.

You don't need to be an expert designer to make your own clothes, only the patience to work step by step. This video will show you how to follow a sewing pattern.

VNC stands for Virtual Network Computing. It is remote control software which allows you to view and fully interact with one computer desktop (the "VNC server") using a simple program (the "VNC viewer") on another computer desktop anywhere on the Internet. The two computers don't even have to be the same type, so for example you can use VNC to view a Windows Vista desktop at the office on a Linux or Mac computer at home. For ultimate simplicity, there is even a Java viewer, so that any deskto...

In this tutorial, Mike Lively of Northern Kentucky University gets you started in getting the Adobe Air Content Management System up and going.

This new episode of Full Disclosure shows you how to use a SSH Tunnel to secure your data when you are on an untrusted LAN (ex. Coffee Shop, School's network, or Defcon). Furthermore, you can use the SSH Tunnel to bypass the LAN's internet filters. The SSH tunnel protocol works by encapsulates your data into an encrypted payload and transmitting it to the SSH Server which is setup on a trusted LAN.

For Infinity Exists Full Disclosure's first Website Hacking episode, we demonstrate how to exploit a security vulnerability occurring in a website's database to extract password hashes. Sql (Structured Query Language) is a computer language designed for the retrieval and management of data in a system's database. The Attack, known as Sql Injection, manipulates Sql statements before they are sent to the Sql Server, allowing the Attacker to create, change, or retrieve data stored in the database.

Internet Relay Chat, or IRC, is one of the most popular chat protocols on the internet. The technology can be connected to the Tor network to create an anonymous and secure chatroom — without the use of public IP addresses.

If you maintain a digital library of your favorite movies, Plex is the perfect solution for bridging the gap between your computer and your mobile device. All you have to do is install the server program on your Mac or PC and point it to the folder where you store your movies, then you can use the Plex app for Android or iOS to watch the movies on your phone or tablet.

Supercell's highly anticipated Brawl Stars has soft launched in Canada, with gamers worldwide salivating at the prospect of a full debut around the corner. Unbeknownst to many, this game can be played on your iPhone right now, regardless of where you live.

Who said sports need parity to be fun? For the third year in a row, the Cleveland Cavaliers are facing off against the Golden State Warriors on the NBA's biggest stage, and basketball fans everywhere couldn't be more excited.

New Android versions have always been released on a fairly regular schedule—in late Fall, Google debuts a new Nexus device, while simultaneously publishing the next iteration of the world's leading mobile operating system. But things are different this year, as we now have numerous indications that Android Nougat could be released as early as August or September.

NMAP is an essential tool in any hacker's arsenal. Originally written by Gordon Lyon aka Fydor, it's used to locate hosts and services and create a map of the network. NMAP has always been an incredibly powerful tool, but with it's newest release, which dropped mid-November of last year, they've really out done themselves.

In this cardmaking tutorial I make a gorgeous card using cut out decoupage from a sheet of 12x12inch paper from Anna Griffins range of fabulous papers. I finish off the card with the matching leaves and paper curls. This looks like a time consuming card but apart from the cutting out of the flowers, it is quite quick & easy and all from 1 sheet of paper. Step 1: Items Used

Hello fellow Null-Byters! This is my first post so please be respectful and constructed criticism is much appreciated. I am no professional, however I believe that it is important to understand technologies before you go poking at them and trying to break them, I therefore decided to make this series. In this "tutorial" we are going to setup a web server with php and mysql. I will be doing this with a raspberry pi because a pi is quite versatile.

A lot of people think that TOR services are unhackable because they are on a "secure environment", but the truth is that those services are exactly the same that run on any normal server, and can be hacked with the same tools (metasploit,hydra,sqlmap...), the only thing you have to do is launch a transparent proxy that pass all your packets through the TOR network to the hidden service.

Welcome back, curious hackers! In today's tutorial, we will be diving deep into the manipulation of Google Operators, commonly referred to as "Google Dorks" in order to access Surveillance Cameras and other control panels.

If you're a Mac user with an Android phone, some apps on your computer aren't very useful, such as Messages, which is meant to work and sync with iOS devices. But now, thanks to MDRS, LLC, using the Messages app on your Mac with an Android phone is now possible and easily achievable. Plus, we've got 50 promo codes to give away for a free year of service!

Some nights, I'm a lazy cook and only want to chop one clove of garlic for my immediate needs instead of prepping a giant batch and freezing it the way I normally do. The only problem is if I'm already feeling that lazy, I really don't feel like dirtying a whole cutting board. However, I still want my garlic to be finely minced so it suffuses my dish with its wonderful, one-of-a-kind flavor.

Making a cool leather wallet is easy. Just get yourself some scrap strips of leather ant you are good to go. No special tool required. You can see full process of making this simple wallet in the video.

It's really amazing how much you can do with root access on an Android device. From various themes to porting exclusive funtionality from other devices, the power of Superuser privileges is truly awesome.

Too little counter space has been the biggest annoyance in every kitchen of every apartment I've ever rented. They've all been either super small or awkwardly shaped, which means choosing between appliances and prep space. You either live with it or learn to adjust.