Welcome back, my nascent Hackers! In my last blog, we looked at a passive way to gather information necessary for a hack. The advantage of using passive recon is that it's totally undetectable, meaning that the target never knows you're scouting them and you leave no tracks. The disadvantage, of course, is that it's limited to only some websites and not entirely reliable.

It's known that during the Thirty Years' War that took place in Europe between 1618 and 1648, soldiers used Swedish fire torches (also called Canadian candles) for heating, lighting, and cooking meals.

All of my hacks up to this point have been operating system hacks. In other words, we have exploited a vulnerability usually in an operating system service (SMB, RPC, etc.) that all allow us to install a command shell or other code in the target system.

Let's face it—if you care about anyone around you, then you brush your teeth. Brushing is an excellent way to not only prevent tooth decay, but to keep people from running away from you with their noses pinched.

For some reason, there's only ever one person in a group of friends that has a cooler. Every time there is a hangout or BBQ, that friend is called and has to lug his expensive, huge plastic cooler around for everyone. Not really fair, is it?

Get rid of your water-wasting sprinkler system— but not entirely! Keep your landscape and garden maintained by converting those sprinklers into eco- and pocket-friendly drip irrigation. In this how-to video, Paula Mohadjer from the Cascade Water Alliance explains how you can easily convert your sprinklers into a drip irrigation system.

DJ Matt shows you the basics of how to cut men's hair. You start out by making a line on the top of the head. You can then make your first cut, or the straight cut on the back bottom. After that, you then make a "down cut" which creates layers. When you get to the "semi-top of the head" you take a comb and rest it along the hair so it is straight. After the comb is in place just clip the top of the hair that is resting along side of it. When you get to the top continue to take long hair along...

Did you lose your key or forget the combination to you lock? This tutorial is here to help you with tips on how to pick just about any combination or padlock without breaking them. All you need is a few household items and a bit of patience and you will be on your way!

Not enough storage space? No problem! In this tutorial, learn how to recycle an old cereal box into a very cool magazine holder. This video will take you step by step and soon you will be on your way to being both more organized and more eco-friendly!

Here's a great craft project you can do with kids or in a classroom. You can use an apple half to stamp apple shapes onto everything from lunch bags to tote bags. This is an easy and cute project to do for the fall.

If you watch only one tutorial on using the Essentials 2 plug-in for Photoshop Elements, it should be this one. Learn your way around the user interface of Cut it Out as well as how to use Cut it Out for most images. Cut it Out in Essentials makes it really easy to remove objects or colors from a photo without using tedious trace tools in Elements. Use Cut It Out in Essentials for Photoshop Elements.

What to put a cake on can be a dilemma. You can decorate a cake board or purchase a cake turntable. This video will show you how to cover a cake board.

The video describes the making of Paper doll dress up and a Tin Purse to put the dolls inside. You can use the cartridge paper but regular paper should do. She was sticking to the princess themes in this tutorial. The tin comes from provocraft but creative imaginations also offers one. Instead of purchasing a tin you can find a old tin purse maybe once for a over sized set of playing cards. There is a tab feature you can use on the dolls but which children the might come off. She suggests usi...

Brian from thetoyz.com and ProLineRacing.com will show you some painting techniques in this video. He is decorating his Revo truck with a special paint design. Brian is painting tears on various shells of vehicles and he got his design idea from the label of a drink can of Monster beverage. Brian suggests using "liquid" masking to mask the base vehicle and then it will be this "shell" that you draw on, which in this case is a design of tears, tear like in air. Draw some tears on the body's sh...

In this video, you will learn how to make a wallet out of paper. First, you will need a piece of paper, a pen, a straight edge, and something to cut the paper. Place the paper on a flat surface. Fold the paper in half, hamburger style and unfold. Fold the bottom half up to the middle crease. Now fold the top half to the middle crease. Fold this in half again and fold it in half one more time in the hamburger style. Now, unfold the paper. Draw lines where you need to cut the paper. Once this i...

This video demonstrates how to make mini peelable potatoes for a doll house. Make a small potato shape out of polymer clay. Scrape some brown pastel chalk into a dish and roll the potato shape in the dust until it is covered. Bake your potato in the oven according to your polymer clay instructions. When it is baked, cut the potato with a razor blade. Be very careful because it is quite hard to cut and you don't want to cut yourself. Place the cut potatoes into a suitable small dish. Take some...

Peel the onions and cut in half length ways, then slice length ways again so each half is cut into 4 long pieces. Heat the oil in a casserole dish that will also go into the oven, and add the onion.

Make a Christmas Gift Card Holder Materials

Cutting the moon and making the shape perfectly round is simple. Usually we have problems drawing a circle free-hand.

In this Adobe Bridge CS4 tutorial you will learn how to create a web photo gallery. Learn how to use built-in HTML and Flash templates within Bridge CS4 to customize, preview and upload a photo gallery directly to an FTP server. Create a web photo gallery in Bridge CS4.

While SSH is a powerful tool for controlling a computer remotely, not all applications can be run over the command line. Some apps (like Firefox) and hacking tools (like Airgeddon) require opening multiple X windows to function, which can be accomplished by taking advantage of built-in graphical X forwarding for SSH.

Windows 10 passwords stored as NTLM hashes can be dumped and exfiltrated to an attacker's system in seconds. The hashes can be very easily brute-forced and cracked to reveal the passwords in plaintext using a combination of tools, including Mimikatz, ProcDump, John the Ripper, and Hashcat.

Apple's Gatekeeper security software for macOS (Mac OS X) is vulnerable to remote attacks up to version 10.14.5. An attacker that's anywhere in the world can exploit MacBooks and other Mac computers by sharing a single ZIP file.

Information gathering is one of the most important steps in pentesting or hacking, and it can often be more rewarding to run things on the target itself as opposed to just running scripts against it remotely. With an SQL injection, a hacker can compromise a server and, ultimately, upload and run the "unix-privesc-check" script locally in order to further identify possible attack vectors.

Most companies have services like employee login portals, internal-only subdomains, and test servers they would prefer to keep private. Red teams and white hat hackers can find these obscure and often vulnerable services using a tool designed to help protect users from fraudulent certificates.

The new iPhone XS and XS Max have more issues than just their hefty price tags. Customers have only had the phones for a handful of days, but some are already complaining of cellular and Wi-Fi connectivity issues on both models. If your experience is the same on your XS or XS Max, there are steps you can take to get your iPhone reliably back online.

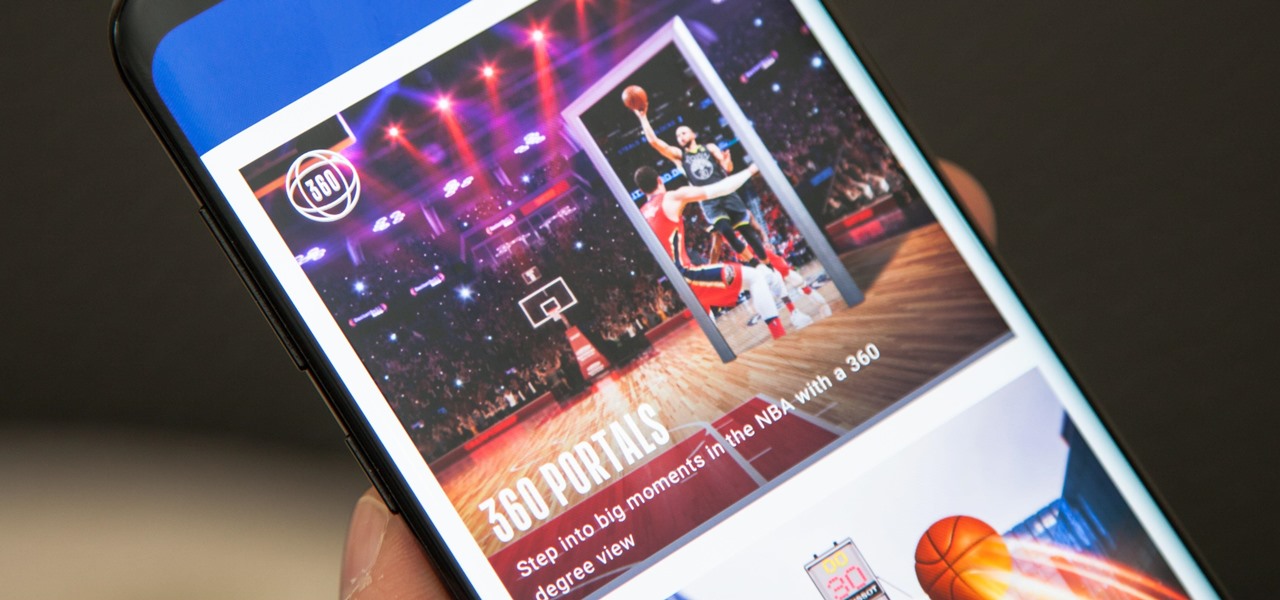
The NBA Finals is underway, and now basketball fans with iPhones and Android devices can get closer to the action for free than they ever could with expensive courtside tickets.

For SQL injection, the next step after performing reconnaissance and gathering information about a database is launching an attack. But something seems off .. in the real world, it's usually not quite as simple as passing in a few fragments of SQL code to an input field and seeing all that glorious data displayed right in the browser. This is when more advanced techniques are needed.

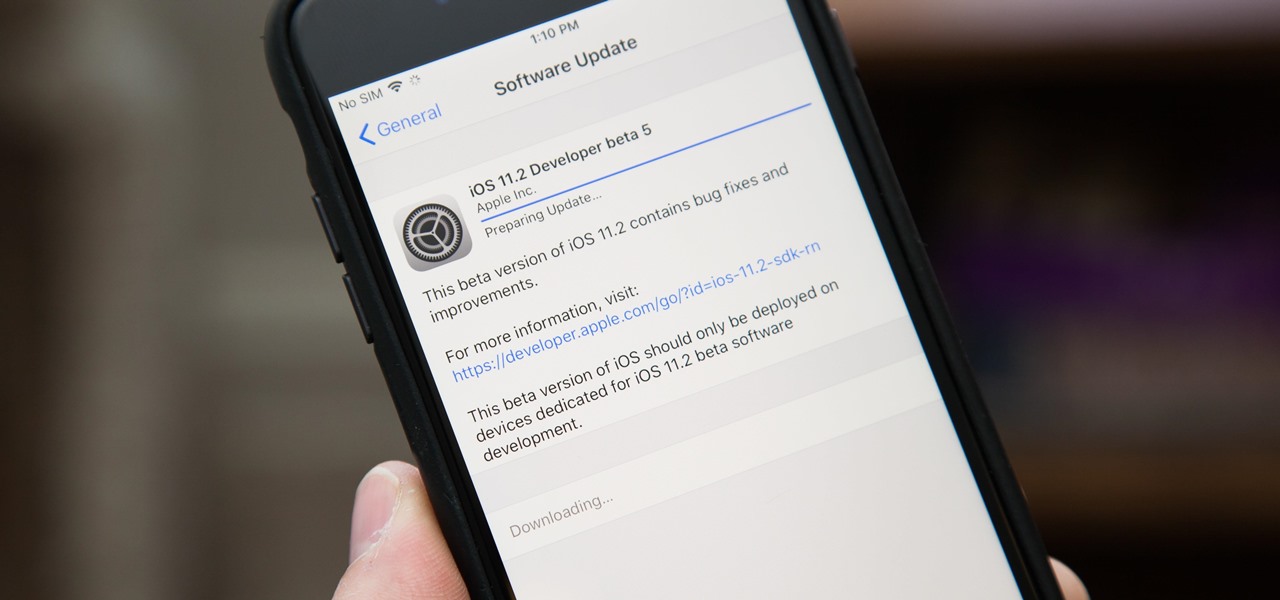
We're getting closer and closer to a final iOS 11.2 release for everyone. Apple just pushed out beta 5 for iOS 11.2 to developers and public testers on Tuesday, Nov. 28, and much like its predecessor from a few weeks ago, there's not much included but bug fixes and security patches.

JavaScript is one of the most common languages used on the web. It can automate and animate website components, manage website content, and carry out many other useful functions from within a webpage. The scripting language also has many functions which can be used for malicious purposes, including stealing a user's cookies containing passwords and other information.

You know Moana's a rock-solid pick for Halloween this year. The question is, how far will you go to become Moana? Are you going to just slap on a cream skirt and a red bandeau? Or do you want to go all out and end up with the finished product like YouTuber Gladzy Kei did?

Telegram routinely boasts about its secure messaging for truly private conversations between two parties. However, default cloud chats in Telegram are only encrypted between client and server, not client and client, which means you have to be a little proactive in making sure your private conversations on Telegram are really private.

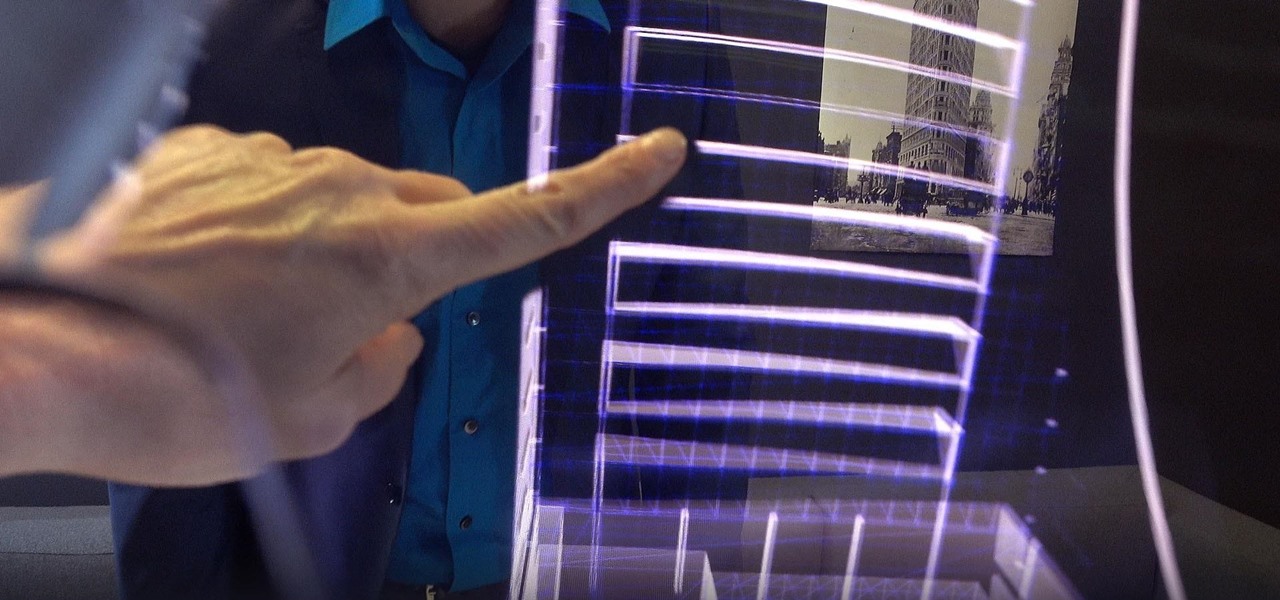
While two augmented reality companies were recently recognized for their innovative technologies, other companies have turned to augmented reality to innovate in their respective fields. Over the past week, use cases have ranged from selling snacks and video games to raising awareness for public health issues.

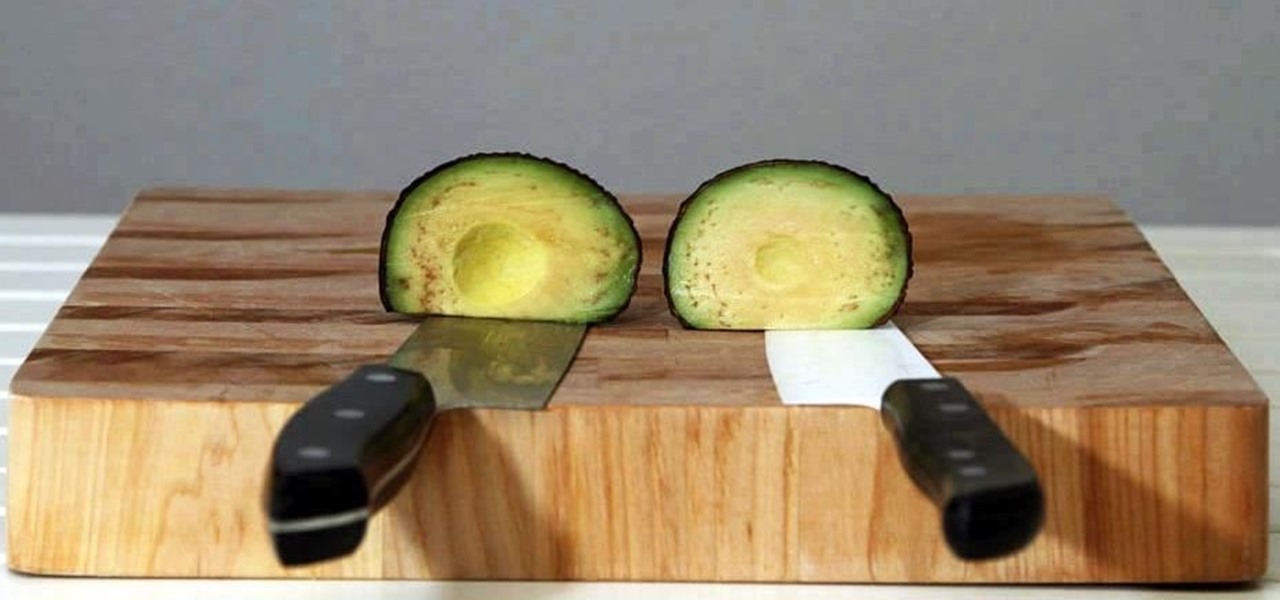
Keeping apples or avocados from browning after being cut is impossible; within minutes of being exposed to air, these fruits (yes, avocado is a fruit) begin to brown. No matter what you try—adding lemon juice, keeping the pits in place, immediately sealing the produce in an airtight bag—brown discoloration always occurs. However, air is not the only reason that foods like apples, avocados, and lettuce brown: it's also due to the knife you're using.

Even though you may love onions, cutting them is probably a completely different story. You've really got to be a pro at slicing and dicing them without getting frustrated, and even then they can still make your cry—literally. But if you don't want to wear a pair of goggles to keep those tears from falling, you have to cut your onions in a very special way.

This video tutorial is on how to make one' favorite superheroes with playdough. This video tutorial is especially for kids and everyone that loves playing with playdough.

Welcome back, my novice hackers! There are SOOOO many ways to hack a system or network, which means you need to think creatively in order to be successful.

Fall is the season of obnoxious food trends. You can't go out to eat or to the grocery store without seeing something pumpkin spice- or candy corn-flavored. Less annoying, but equally prevalent is the butternut squash. For the next several months, we will be pelted with recipes for butternut squash soup, butternut squash risotto, stuffed butternut squash... and the list goes on. Butternut squash is everywhere. But how many people actually know how to prep the stuff?

Prepping fruits and vegetables ahead of time makes putting together the final dish a lot easier, but once you cut them up, they start to turn brown almost instantly. However, thanks to this quick and easy tip from America's Test Kitchen, you can keep them looking fresh for much, much longer.

Panolapse is a simple and easy way to add rotational panning motion to timelapse videos. Video: .