In this video tutorial, Chris Pels will show how to configure an ASP.NET web site to use a specific version of ASP.NET/.NET Framework. First see how to identify what version of the .NET Framework a web site is associated with by viewing the script map in Internet Information Server (IIS). See how a script map is associated with the root in IIS and then with individual web sites. Next learn about the ASP.NET IIS Registration tool (aspnet_regiis.exe) used to configure IIS or an ASP.NET web site...
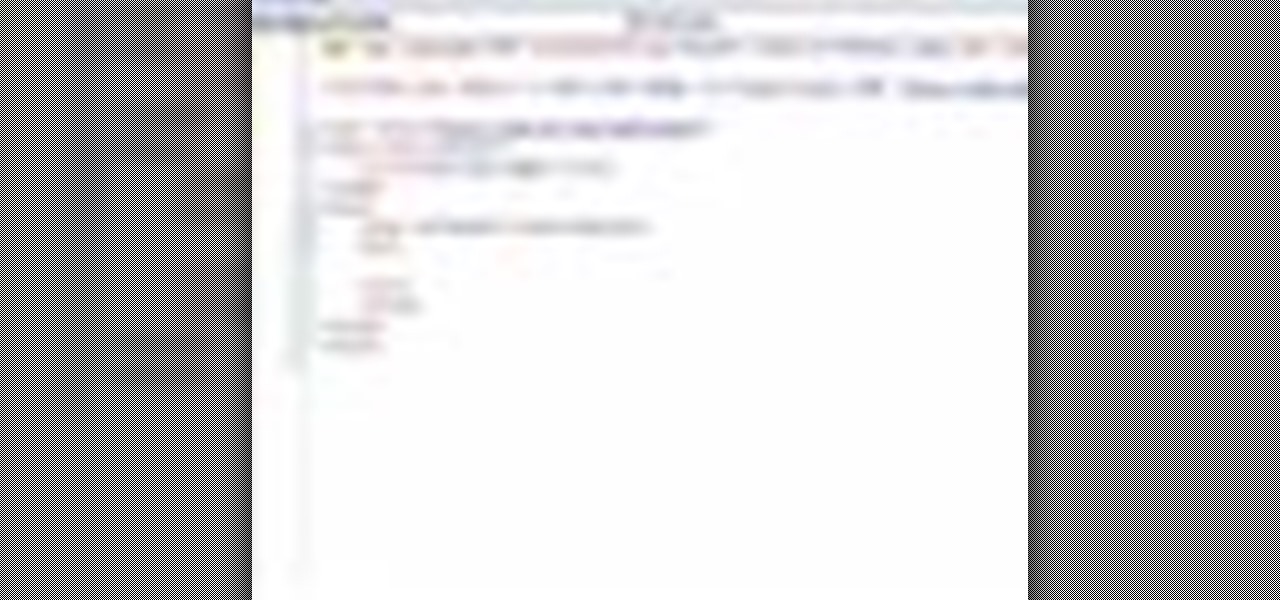
In this video tutorial, Chris Pels will show how information can be passed from one page to another using a query string. First, see how to construct a query string including variable names and values from information on a data entry form. Next, see how to access the query string information when the page is posted including how multiple query string variables are handled. As part of the server side processing of query string information, see how to implement validation for existence of query...
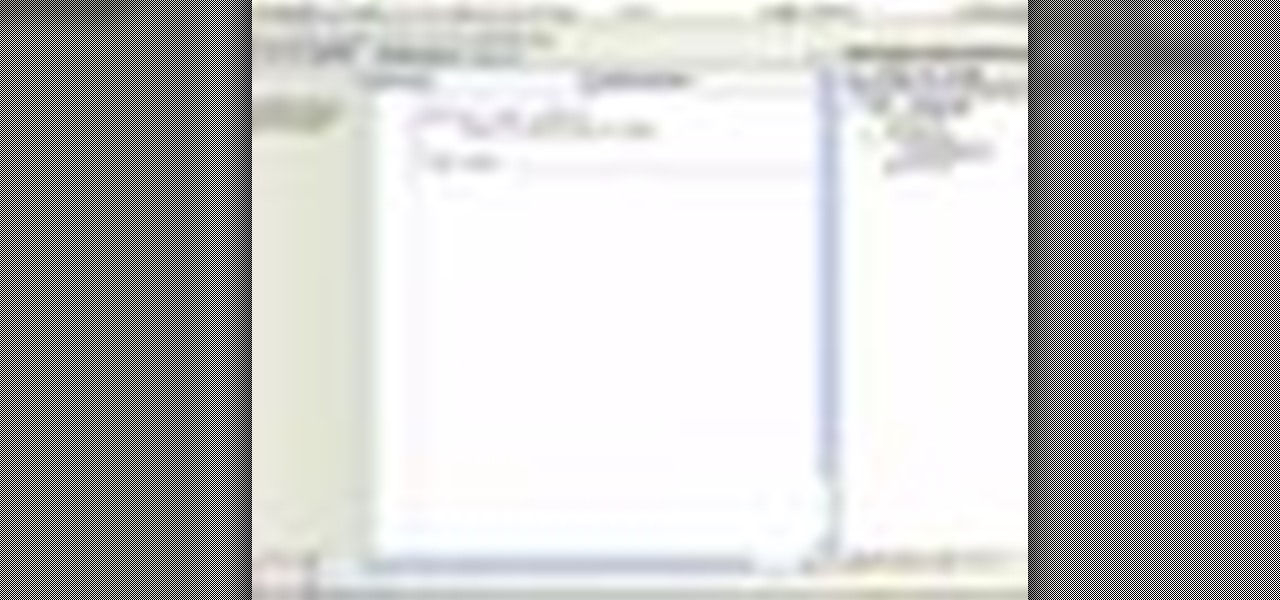
In this video tutorial, Chris Pels shows how to create a Cross Page PostBack in ASP.NET, where a control on a source page raises a PostBack event to a different target page. First, learn how to configure a Button control to PostBack to a different target page. Then, learn how to get information from controls on the source page with the PreviousPage property and the FindControl method. Then, learn how to use public properties on the source page to expose data to the target page, and learn how ...

Be a style standout in this chic, modern bob cut.

Make this nice & easy cut paper flower design.

In this tutorial, we learn where to cut on plants to prune. A plant that has a woody stem can be shortened between the leaves, making sure to cut it towards a node because this is where it will heal most rapidly. If you cut it too close tot he bud it will dry out and healing will not occur. Slope the cut away from the bud so you give the plant a greater chance to heal and you can avoid infection. Pruning often gives you control over how big the plant gets, and you can also control what the si...

Watch this video from This Old House to learn how to make miters. Steps:

Watch this video from This Old House to learn how to make an inside joint for crown molding. Steps:

The Paper Bag Princess is one of the most beloved children's books for girls of all time, and it's heroine is a great role model for young girls everywhere. If you love the book, watch this video to learn how you can make an easy, sexy Paper Bag Princess Halloween costume.

The Fish Contamination Education Collaborative (FCEC) has made this video to reach the public about fish preparation safety, to make su. It's important to prepare fish in a certain way, because some species of fish have contaminants that pose health risks. Those contaminants are stored in the fatty portion of the fish, so by cleaning and cooking the fish in a certain way, you can reduce your exposure to those toxins.

Do you like your guac chunky? Yes? Well, then this video is for you. Learn how to make a super delicious, chunky style, avocado guacamole, perfect for tailgating or a Super Bowl party. Before you actually get to making this chunky guacamole, there's a few tips and tricks to learn, like how to tell if the avocado is ripe enough for your dip, and how to cut it and remove the center.

In this how to video, you will learn how to make creamy asparagus pasta. First, you will need 200 grams of pasta, 3 cloves of garlic, 240 grams of asparagus, a half a cup of white wine, pepper, 2 table spoons of extra virgin oil, 3 sun dried tomatoes, a handful of fresh basil, salt, 2 table spoons of soy cream, and parmesan. First, wash the asparagus and cut the ends off. Now cut the asparagus into pieces. Cut and peel the garlic, tomatoes, and basil. Add the oil into a pan and place the aspa...

This video is about making an origami of a volcano. The video begins with aliMcRose talking about the geographical formations of Japan and then she shows a finished origami. The materials required are one piece of two sided paper and a pair of scissors. Fold the piece of paper in half on one side and make sure the fold is a clear line. Now unfold the paper and fold it on the other side in a similar way.The piece of paper will now have four squares. Now fold these four squares into triangles a...

To start making your tea and toast, roll about a section of white fondant about four inches by six about 1/8th inch thick. Now take a one inch circle cutter and cut out one circle. Now taking a half inch circle cutter, make an impression in the center of the first circle being careful not to go all the way through. Now you have your saucer for your toast. Next, take a one inch square cutter and cut that out of the fondant as well. Cut it in half diagonally and poke tiny little holes with a to...

This tutorial by the Floral Design Institute demonstrates how to create a hand-tied Calla bridal bouquet. The key to creating this bouquet is to make sure your flowers are properly prepared. The flowers should be fully hydrated (in water for at least two hours). Take each flower and mold each stem to to reflect the natural curve of the flower. Lay them side by side so they are lined up in a parallel fashion. Give even pressure on the stem to prevent bends or kinks. Some stems may be straight ...

Kevin demonstrates how to make a paper frog. Take a regular sheet of construction paper. Fold the outer ends towards the center forming a triangle. Fold a crease at the base of the triangle and cut it out. Open the folds and you can observe two creases. Create two X-shaped creases by bending the opposite corners. Hold the triangles on the side of the X and squash it down such that the other two triangles meet. Repeat the process on the other side. This forms a square with a diagonal cut conta...

Minecarts are a lot more complicated than they may seem at first. Between regular rails, powered rails, and detector rails, they all have a lot of quirks that can make them hard to use.

Welcome to Minecraft World! Check out our tutorials, post to the community corkboard, and come play on our free server!
Just a quick post. Xorg is the graphical server that handles the desktop environment you choose for your Linux box. A pretty big flaw was found in Xorg versions 1.11 and later that allows anyone to bypass the screen lock mechanism on xscreensaver, gscreensaver, and many others.

VNC is a great protocol that you can use on Windows and Linux machines to remotely control computers. This is useful if you need to control your computer when away from home, help your grandma check her email, or help a client with a disk cleanup. VNC is secure in the sense that it requires authentication in order to make the connection, but after that, the data is sent over the internet unencrypted. This means that an attacker could sniff your traffic and snoop everything that's going on. Th...

Paying for web hosting isn't ideal in most situations. If you have your own website, hosting it yourself is very acceptable and easy to do, assuming your internet bandwidth permits. Most people want to run a personal site, nothing crazy, so hosting from home on low-bandwidth internet is actually a better solution in most cases.

Today I'll be detailing how to use the two YouTube Video Editors to enhance the quality of your work, as well as going over a simple workaround to save time uploading the variety of clips you'll need to assemble a more complicated piece of filmmaking.

Minecraft World user Xhoes is building an epic "Capture the Flag" arena. While still a work in progress, this epic arena boasts two fortresses with flags, obstacles and objects to hide behind in the battle field, and an underground passageway.

Welcome to Minecraft World! Check out our advanced tutorials and come play on our free server. Long ago some smart folks figured out how to make water, lava, and some blocks do the mob killing for them. More recently, with the addition of redstone, these mechanisms for resource collection have gotten rather complex.

The 1.9 pre-release is out right now, download it here! Notch has also said that the 1.10 release will be coming soon, with even more Adventure-related updates. Enjoy!

Karma is an idea that exists in the Hindu, Buddhist, Jain, and Sikh religions, which simply holds that all actions have consequences. In other words: karma’s not a bitch, but you might be. If so, here’s how to start sending the world good vibrations. Learn how to store up some good karma for yourself.

A CNC router machine is probably the most useful tool a hobbyist can own, but the price for a CNC machine on the market is way more than the average hobbyist is willing to spend. You can build your own CNC with very basic tools, little knowledge of machinery, mechanics, or electronics, but be warned, these machines are inherently dangerous, so wear the proper protection and use common sense. At the very least, read the instructions and precautions on every tool you use.

A pegboard for storage is an essential item in a workshop. Danny Lipford shows you how to install a pegboard in a workshop in this video tutorial.

Avocados are awesome and delicious, especially when you make guacamole out of them. But to take off the skin, chop, and cut it up, preparing an avocado can get tedious. So with this tutorial, I hope that I can provide you with a simple and easy way to peel and cut your avocados in the future.

Dovetails are an extremely old and effective wood joint. There are three types of dovetails, through dovetails (the most popular), half blind dovetails, and sliding dovetails. In this woodworking video tutorial, you will learn how to do a machine cut through dovetail. Cut through dovetails with a machine.

There are countless ways in which a talented and trained programmer and tech pro can earn a lucrative living in an increasingly data-driven age — from writing and creating apps and games to working for a cybersecurity firm or even the federal government.

With an inconspicuous Android phone and USB flash drive, an attacker can compromise a Windows 10 computer in less than 15 seconds. Once a root shell has been established, long-term persistence to the backdoor can be configured with just two simple commands — all while bypassing antivirus software and Windows Defender.

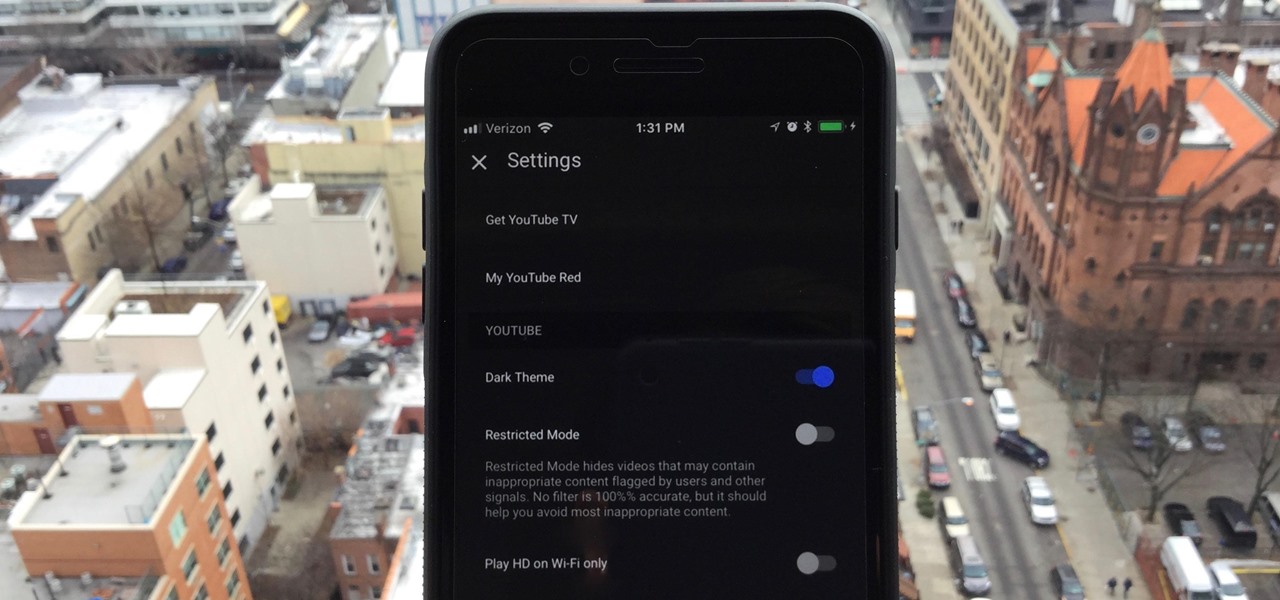
One of the downsides to iOS is the lack of a true dark mode. While Apple has offered a workaround, third-party developers have taken it upon themselves to implement dark themes in their apps. While big names like Twitter and Reddit have led the charge for some time, it appears YouTube is the next app to join the party.

if you're ever wondering what to do on a server, you can ask people to set a challenge for you, or even set a challenge for yourself to create something new.

Hello there Nullbyters, Last tutorial we discussed navigating and setting some options.

Welcome back, my greenhorn hackers! Over the years, I have written many articles here on Null Byte chronicling the many the hacks of the NSA, including the recent hack of the Juniper Networks VPN. (By the way, my speculation in that article has proven to be correct. The NSA did embed a backdoor on those devices.)

Here's a not-so-well-kept secret about the food industry: retailers love to take your money. And one of the ways they do that is by dividing food into smaller sizes and charging more. Have you ever noticed that a container of precut, washed broccoli costs more than a head of broccoli with the same amount of florets and stems?

Welcome back, my greenhorn hackers! Many new hackers come from a Windows background, but seldom, if ever, use its built-in command-line tools. As a hacker, you will often be forced to control the target system using just Windows commands and no GUI.

Not too long ago I showcased ReCam, a free app that lets you schedule recordings and use your Android device as a security or spy camera of sorts. While useful, this app required you to schedule when to record in advance, resulting in you possibly missing the footage you intended to record (assuming your scheduling wasn't as on-point as you wished).

Welcome back, my novice hackers! In this continuing series on Metasploit basics, let's next look at a module that many aspiring hackers find useful—autopwn.