
How To: Dual Boot Mac OS X Mavericks 10.9 & Yosemite 10.10
For those of you who've already gotten Beta Preview or Developer Preview access to Mac OS X 10.10 Yosemite, I highly recommend installing it on a separate partition on your hard drive.


For those of you who've already gotten Beta Preview or Developer Preview access to Mac OS X 10.10 Yosemite, I highly recommend installing it on a separate partition on your hard drive.

LastPass is a password manager that's been around for some time, and has finally made its way over to Android for use with apps, not just websites.

A long time ago, we recommended the Hover Zoom extension for Chrome as an easy way to blow up small image thumbnails without actually have to "click" on the images themselves. Over the past year, there have been reports that Hover Zoom now collects and sells your browsing data to third-party advertisers without your consent.

There's a lot of cool features rumored to be included in next year's HTC One 2 (M8), the follow up to the flagship HTC One smartphone, including a fingerprint scanner, Android 4.4 KitKat, and Sense 6.0, but it's just too far away to get really excited about yet.

One of the most heated topics in the Android community now (and probably forever) is stock Android, with lots of users requesting the ability to use it rather than the manufacturer's skin.
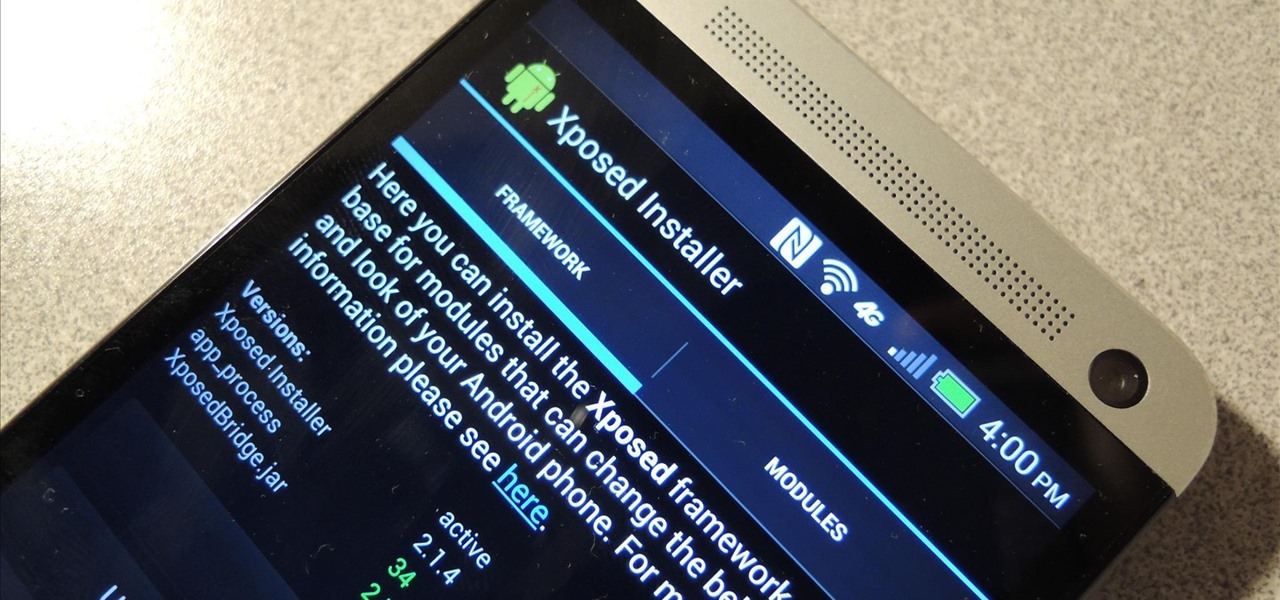
Update: The installation process for Xposed Installer is now dead simple—check out our updated guide!

Welcome back, my fledgling hackers! In one of my recent articles, I showed you how to install BackTrack as a dual boot system on a Windows computer. In this tutorial, I will walk you through BackTrack, giving you a tour of the most salient features for the hacker-to-be.
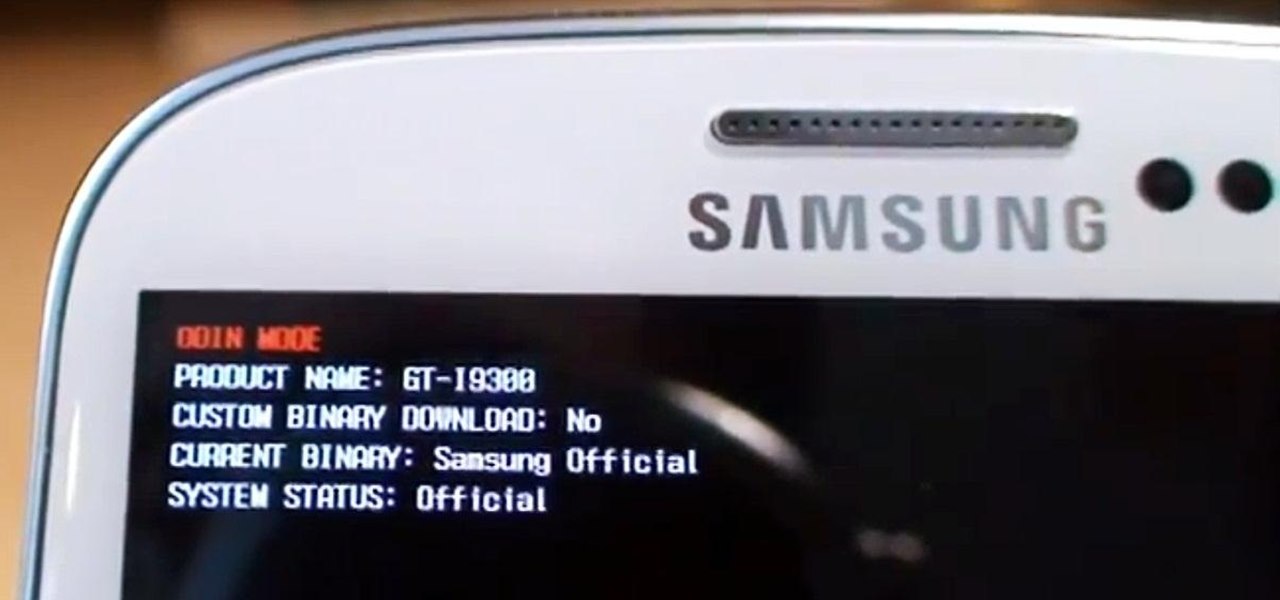
Need root on your Samsung Galaxy S3? Phone not getting the Jelly Bean update? Stuck on the Samsung screen? Phone bricked? Need to restore back to stock? Odin can help!
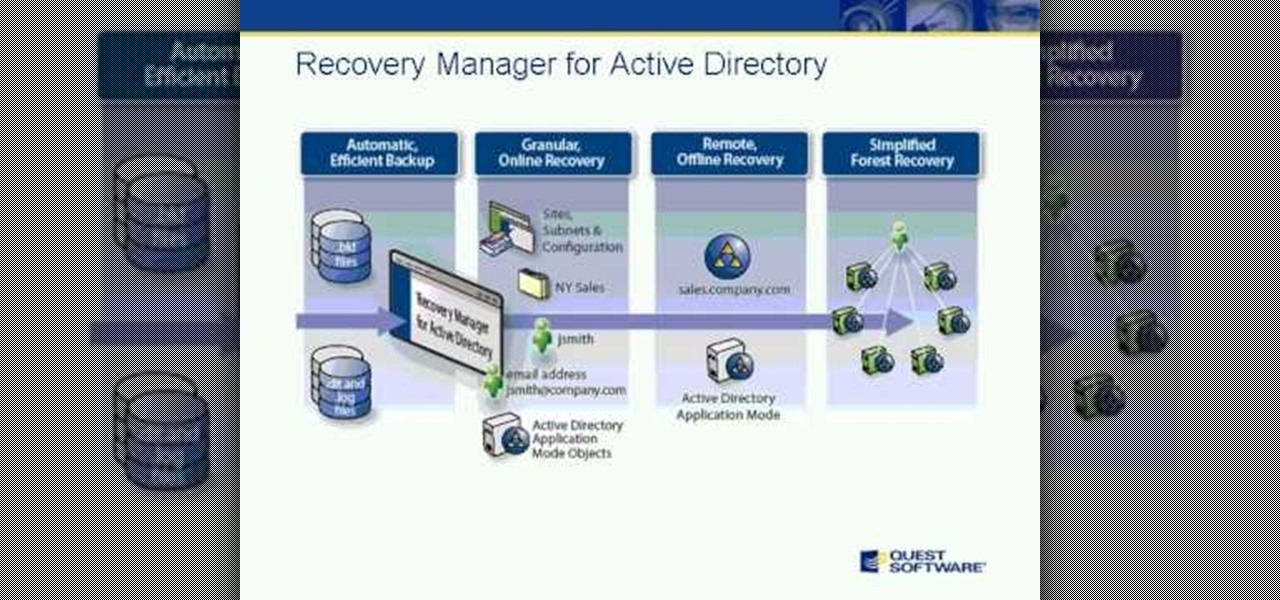
View our webcast to learn about the advantages of using a comprehensive Active Directory recovery solution -- and view a product demo. With Quest Recovery Manager for Active Directory, recovery time can be reduced from hours to minutes!

This video will teach you how to increase your PC's virtual memory. Or in other terms, the Random Access Memory space to be used when doing something with your computer. 1. Press CTRL+ALT+DEL. Go to Performance tab. 2. Check the Commit Charge which is also the amount of virtual memory used. 3. Right-click the My Computer shortcut on your desktop. 4. Go to Advanced tab. 5. On the Performance box, click Settings button. 6. Click the Advanced tab. 7. At Virtual Memory box, click Change button. 8...
On Android, there is a vulnerability that Google doesn't seem to want to fix — anyone can open the Quick Settings panel on your lock screen. GPS, Wi-Fi, and Bluetooth, all toggles accessible in this menu, are vital tools for locating your phone in case it is ever stolen. But thanks to Xposed, you can eliminate this potential risk.

It's nearly impossible not to be at least somewhat familiar with Microsoft Excel. While it's needed for many office jobs and data analysis fields, hackers could also benefit from improving their spreadsheet skills. Many white hats already know some of the essential Excel hacks, such as cracking password-protected spreadsheets, but there's so much more to know from an attack standpoint.

Checkra1n is by far the best way to jailbreak A7- through A11-powered iPhones on iOS 13 and later, but it's not without its downsides. Besides the lack of Windows support, the tool limits your choices to Cydia alone. With a little elbow grease, however, you can easily replace the app with Sileo for a more streamlined jailbreak experience.

One of Android's biggest strengths relative to iOS is how simple it is to sideload apps that aren't on the official app store. Rather than having to sign IPA files or tell your phone you trust a developer every two weeks, you can just enable a setting and be done with it.

It's a good sign for any emerging technology when one of the leaders of an industry adopts it. So when Mastercard, a brand so recognizable that it dropped its name from its logo at CES last year, decides to develop a mobile augmented reality app, the moment is a milestone for the AR industry.

There may be questions from some about the future of Magic Leap, but in Japan, The Force is with the augmented reality startup.

As we predicted this time last year, Magic Leap is finally moving from consumer entertainment hype to making a firm commitment to enterprise customers.

Halloween is barely in the rearview mirror, but Coca-Cola is ready to bypass Thanksgiving altogether to accelerate the arrival of Christmas, and the brand has enlisted augmented reality as an accomplice.

It's been proven that hackers can manipulate your screen with fake taps through specific exploits, so they can potentially hit the "Grant" button when you get a superuser request. This is the last thing you'd want to happen since the malicious app from that point forward has full system privileges. Luckily, using a fingerprint to lock your superuser requests can prevent this.
It's been almost two years since Apple added the TrueDepth depth-sensing camera of the iPhone X for Face ID and Animojis, but now Google is ready to upgrade the front-facing camera on its Pixel series.

Perhaps it's a coincidence that the Vuzix Blade smartglasses look like the sunglasses that a police officer would wear, but a new partnership with an AI software company makes the wearable a perfect fit for law enforcement.

After a rough run of news, smartglasses maker North still has the confidence of investors, as evidenced by its latest round of funding.
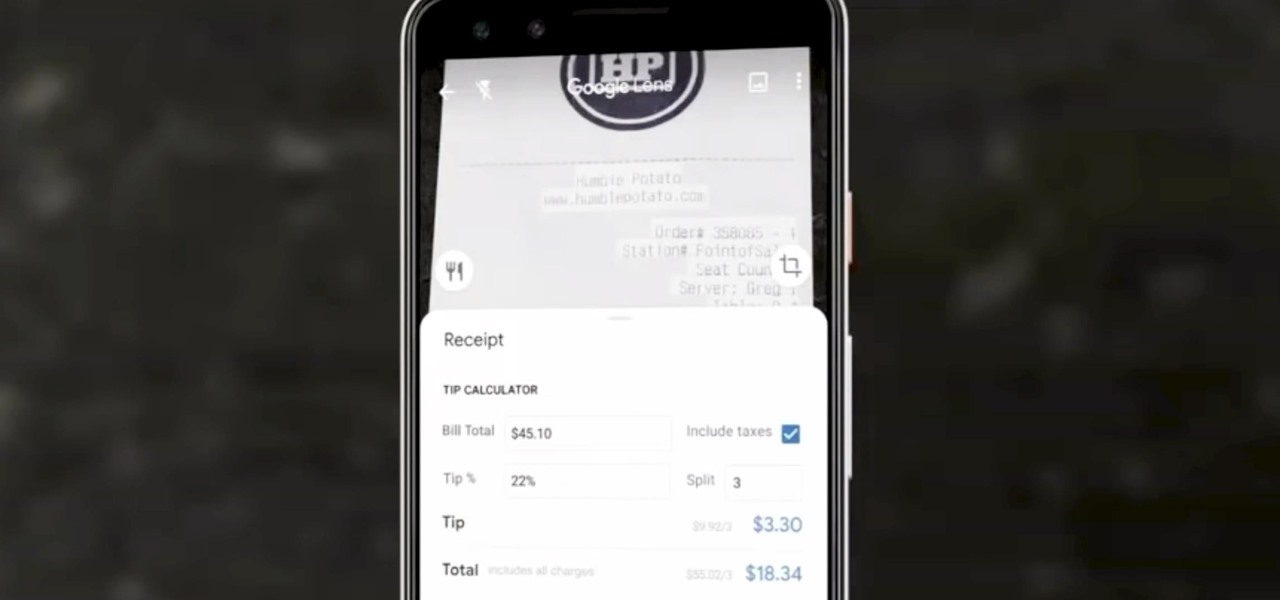
Google Lens can perform many different tasks with your smartphone's camera thanks to advanced machine learning, such as foreign text translations, landmark identification, and business cards to contacts conversion, to name a few. With this year's Google I/O conference, we have another cool Lens feature to look forward to — receipt calculations.
Alongside its official unveiling of the lower-cost Pixel 3a smartphone at Google I/O, Google took the opportunity to extend its early preview of AR walking navigation in Google Maps to all Pixel devices.

The Windows 10 desktop and microphone can be livestreamed without using Remote Desktop Protocol (RDP) software and without opening any ports on the target computer. A hacker with low user privileges can monitor and exfiltrate a target's every move and private conversation in real time no matter where they are. Hackers are watching and listening, and there are few ways to protect yourself.
The Avengers aren't the only shiny new toys available to Pixel handset owners, as the animated stars of the upcoming Pokémon Detective Pikachu movie have arrived in the Google Playground app.

At its F8 developer's conference in 2016, Facebook went on record with a roadmap that called for augmented reality integration into Oculus within 10 years. Now, it appears as though Facebook is accelerating those plans.

Just weeks after revealing plans to port one of its most vital augmented reality products from HoloLens to the smartphone world, Microsoft has finally opened the mobile software floodgates to the public.

Location services provider Mapbox is expanding the reach of its augmented reality development capabilities to include apps for automobiles as well as smartphone navigation.

The actual augmented reality portion of Pokémon GO is about to get even more fun for players. On Tuesday, the company revealed GO Snapshot, an extension of AR+ Mode facilitated by ARKit and ARCore that will enable players to pose Pokémon characters in augmented reality for photo capture.

Simulated training can help soldiers and sailors learn how to use their weapons safely, but simulations can sometimes lack the stressful environment of a real firefight.
Intel's RealSense family of depth tracking cameras has a new addition with a different set of sensory capabilities.
Owners of Google Pixel devices now have a plethora of imaginary friends to play with thanks to the Playground augmented reality app.

Christmas has arrived early for ARCore app developers, as Google just unwrapped a few iterative improvements to the augmented reality toolkit in version 1.6.

Augmented reality and drones already go together like turkey and stuffing, but a new iOS app adds some spice to the combination with a new kind of flight path automation.

On Sunday, Apple CEO Tim Cook (the number one person on our NR30 list) made a rare television appearance to talk about and show off his current obsession: augmented reality.

With HoloLens and its enterprise-focused software offerings, Microsoft continues to make an impression on companies looking to adopt augmented reality, with Toyota Motor Corporation among the latest.

With barely a whisper of augmented reality during the first day of its developer's conference, Samsung came out swinging on day two with the introduction of its version of the AR cloud and a partnership with Wacom that turns Samsung's S-Pen into an augmented reality magic wand.

In the latest example of non-tech companies taking on augmented reality marketing, online travel site Travelocity has added an AR version of its Roaming Gnome mascot to its mobile app.

Adding another arrow to its quiver of augmented reality acquisitions, Apple has reportedly acquired Spektral, a computer vision company with technology for real-time compositing (otherwise know as the "green screen" technique in broadcast TV and film).