Are there any benefits to watching a movie in a holographic mixed reality headset, or should you just stick with your TV? It's not as cut and dried as you might think. While TVs have some advantages, so does the virtual screen of a Microsoft HoloLens.

In a letter dated February 16th, Apple CEO Tim Cook responded to the FBI's demand that Apple create a "backdoor" to bypass the encryption on an iPhone used by one of the perpetrators of last year's terrorist attack in San Bernardino, CA. Cook began the letter by stating that Apple has "no sympathy for terrorists" and has cooperated in giving the FBI all of the information that it has available.

What's up readers? We have ever so slightly touched upon this concept of scope with variables but still don't really know what it means. In this tutorial we will learn the behaviors of variables existing in our programs and within functions.

Windows 10 has so many new features that we couldn't even cover them all with one article. From keyboard shortcuts to revamped search functions and all-new window gestures, Microsoft definitely piled on the fresh functionality in the latest version of their operating system.

Let's say you're flush with Google Opinion Rewards credits, or you just got a Google Play gift card for your birthday. This is a perfect opportunity to remove ads and unlock new features by upgrading some of your free apps to their paid counterparts, or to finally purchase that app you've been lusting after that doesn't offer a free version.

Task Manager got revamped quite a bit in modern versions of Windows. First introduced in Windows NT 4.0, it's become pretty popular among more advanced users. In Windows 10, Task Manager is not just a task manager anymore, it's also a system monitor, startup manager, history viewer, user controller, and the list goes on.

Hello all, this is my first submission to null byte! I noticed something a little strange, particularly that whenever Meterpreter is discussed, it is virtually always in the context of Windows. Granted, the Windows Meterpreter is more powerful than the version that can run on OS X (it has several more commands/options), but I think it is still worth noting how to do it. I've even seen some people mistakenly say that Meterpreter can only be run on Windows, which is not true. Meterpreter can ea...

OneDrive, formerly known as SkyDrive, is a free online storage solution developed by Microsoft. If you're a fan of using cloud-based storage systems, then OneDrive offers you plenty of benefits. It's also heavily integrated into Windows 10, including the new File Explorer, in an effort to make utilizing OneDrive easier for you.

Reddit is one of the internet's greatest sources of funny and interesting videos. Its user base is extremely active, and a system of upvotes and downvotes ensures that the best content always rises to the top.

Android Lollipop still doesn't have a simple way to add a custom lock screen wallpaper, so when I came across Corgi For Feedly from developer Stan Dmitriev, I had to check it out. What sets Corgi apart from other lock screen replacements is that it connects directly to your Feedly account to display top stories from your favorite RSS feeds as your background.

Are you a follower or a leader? No matter how you respond, we all know that leader is a more desirable position to hold. Great leaders typically share a few qualities—confidence, intelligence, and strength, to name a few—but one of the most intriguing is their appearance. With the right facial structure, and some well-rehearsed expressions, you can trick others into thinking you're leader material.

Check it out: you save more dough (ba dum bump) when you order a large pizza than with any other size. Why is this true? NPR reporter Quoctrung Bui's engineer friend pointed out that a medium pizza was twice as big as a small one, yet only cost slightly more.

It's been rumored ever since the 2012 release of the Kindle Fire, and now Amazon's first smartphone is set to debut a little later this year.

Released last year for iOS devices, Frontback is a simple photo-taking and sharing app that not only snaps a picture of what's directly in front of the camera, but also behind it, which is to say, a selfie.

Welcome back, my greenhorn hackers! Although we have focused primarily on technical hacks here, social engineering can sometimes be especially effective. This one requires a bit of technical skill, but not too much. In addition, it's limited by how specific a target you can choose—but it will work.

Editor's Note: The claims by Vani Hari which were originally detailed in the article below about azodicarbonamide were unscientific in nature. This article has been updated to reflect that and provide more scientific context on the issue.

When you think of nail polish, it's probably almost always in the context of a manicure. I mean, that's what it's made for, right? But there are plenty of other things you can use clear or colored nail polish for besides painting your nails.

Welcome back, my neophyte hackers! In today's hack, we're going to have a bit of Halloween fun. Have you ever had a boss who made you miserable with his micro-management and nagging? Maybe you thought he unfairly fired your friend/colleague? Well, now here's your chance to get a bit of revenge and keep him or her off your back!

Every time you Google something or click on an ad in a YouTube video, Google gets paid. They are estimated to make well over $100 million a day, and I honestly think that's low-balling it.

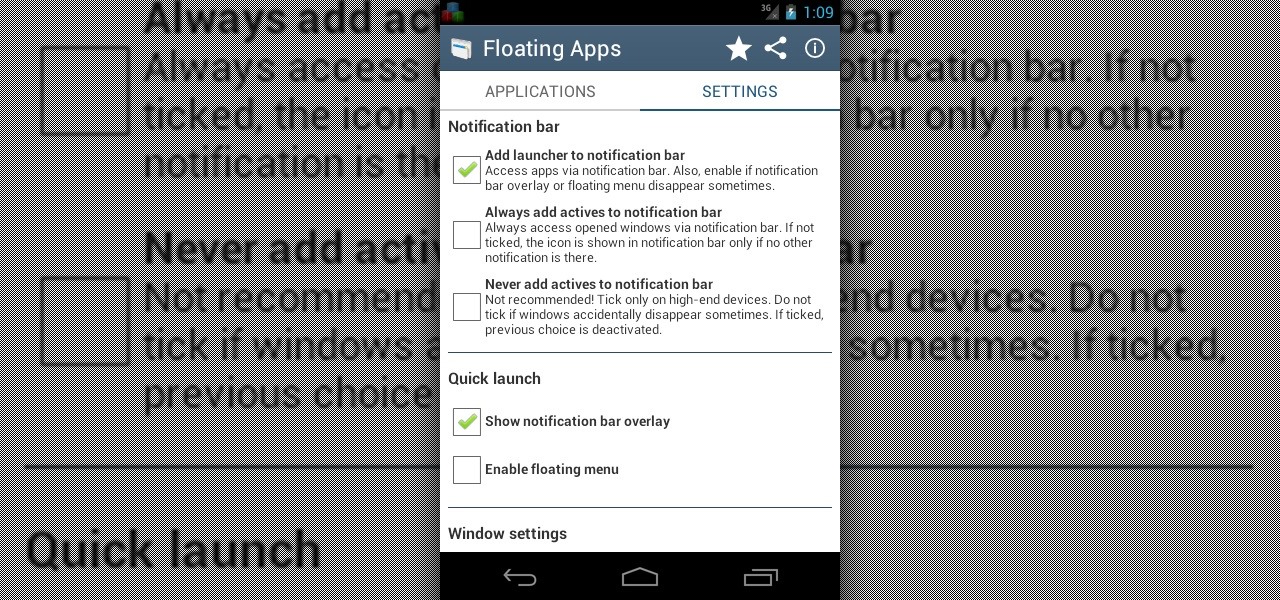
Sometimes, it's very useful to be able to use more than one app on Android phone or tablet. For example, if you want to watch a movie while surfing or if you need calculator, find some contact, write a note, search web or wikipedia for some facts, etc.

For over 20 years, a tiny but mighty tool has been used by hackers for a wide range of activities. Although well known in hacking circles, Netcat is virtually unknown outside. It's so simple, powerful, and useful that many people within the IT community refer to it as the "Swiss Army knife of hacking tools." We'll look at the capabilities of Netcat and how the aspiring hacker can use it.

3D printing has been around for a while, but until recently it was used mostly for prototyping and research. Now, with technological advancements, it seems like everyone is using 3D printers, from crime scene investigators to garage hobbyists and hackers. Below are some of the most innovative uses people have come up with so far.

Last weekend, some unlucky Gmail users inadvertently had their email accounts wiped out. Actually, it was 0.02 percent of all Gmail users—or roughly 40,000 of the 200 million who use the email service, due to an "unexpected bug" which affected copies of the data. Gmail does make backup files of everything, so eventually everyone will reclaim their email history. In fact, as of yesterday, Google has successfully restored all information from their backup tapes and has started returning everyon...

Augmented reality is beginning to leak out into the mainstream world. This is thanks, in part, to ARKit and ARCore. These releases turned the current smartphones owned by millions of Apple and Android users into AR-capable machines. And while there are definitely some awesome use cases for mobile AR, the real future in AR is headworn.

Amy Kline shows us in this arts and crafts series, how to make a hemp beaded necklace. Yes, you’ve seen them around the necks of all of the coolest people in town. Now learn how to make your own with relatively little training or financial outlay. Our expert will show you how to measure the length of your necklace to match your body size, how to anchor the necklace as you’re making it, and two different knotting techniques to create two different designs for your necklace. So the next time yo...

Every year, Apple releases new wallpapers for its iPhone and iPad software updates, and that's exactly what happened with the iOS 18 and iPadOS 18 updates released on Sept. 16. But you don't need iOS 18 or iPadOS 18 to enjoy Apple's new backgrounds — you can download and use them on any device, whether a smartphone, tablet, computer, or something else.

The year 2019 was filled with all the normal peaks and valleys of the tech business cycle, but this year was particularly important in a space as relatively young as the augmented reality industry.

The rise and fall of Meta, the Silicon Valley-based augmented reality startup that looked to challenge the likes of Microsoft's HoloLens, and others, took just six years.

People say that money makes the world go 'round. And it's no different in the world of augmented reality.

Give an 18-month-old a shoe, check back 10 minutes later, and it's a very big maybe he will have it on his foot. But give him your smartphone, and in a mere five minutes, he can take 100 pictures of the carpet, send weird messages, and delete essential apps. Imagine what your child could do if they were able to harness this technical aptitude and put it to good use — and they can, with learning apps.

It's easy to have your password stolen. Important people like executives, government workers, journalists, and activists face sophisticated phishing attacks to compromise their online accounts, often targeting Google account credentials. To reduce this risk, Google created the Advanced Protection Program, which uses U2F security keys to control account access and make stolen passwords worthless.

Social engineering makes headlines because human behavior is often the weakest link of even well-defended targets. Automated social engineering tools can help reclusive hackers touch these techniques, but the study of how to hack human interactions in person is often ignored. Today, we will examine how to use subtle, hard to detect persuasion techniques to compromise a human target.

The world of investment and finance can be labyrinthine in its very nature — and even more complicated in regards to augmented and mixed reality. While these new emergent technologies are teeming with explosive levels of unrealized potential, there's still a big layer of uncertainty in terms of return — but these investors aren't afraid to take the leap.

I love cryptography. It is like a great gigantic puzzle for me to solve. However, it is more important than that. It is also how we keep secrets safe. Not just sorta safe either, but really safe.

In Grant City, crimes has taken over, and there's only one man who can help: Jack Slate. With the help of his trusty sidekick canine, Shadow, maverick cop Jack Slate will help restore Grant City to its previous renowned existence as of one of the world's greatest cultural and financial centers, one criminal at a time. While ridding the city of its filth in Dead to Rights: Retribution, Jack and Shadow uncover a conspiracy that threatens their whole existence. And it's up to you to stop it.

Buying a home is a big step so find out just what is involved when you are ready to bid for the house of your dreams. The whole process can be bit nerve-racking but as long as you stick with it you’ll be a home-owner in no time.

One of the hardest parts of entering the IT and computer science field — other than the difficult material and intense competition — is the time and financial cost of learning everything you'll need. Learning to code isn't just learning one language; you have to learn a variety of languages used for different purposes, and then you have to get experience using them.

For Android 11, Google is doubling down on the handy App Suggestions feature that debuted in Android 10's app drawer by expanding it to the home screen dock.

The results of Microsoft's $480 million contract with the US Army are on display and users continue to test the suped-up version of the HoloLens 2.

Amid the coronavirus chaos, two companies at the forefront of augmented reality technology took starkly different approaches to their upcoming developers conferences, as Facebook has canceled its annual F8 conference and Magic Leap plans to invite a limited number of attendees to its Florida headquarters for LEAP Developer Days.