Squash is a racquet sports game, seemingly similar to tennis, but played on a small indoor court with hollow rubber ball, much small than a tennis ball. Squash is an intense, high impact sport. This squash tutorial demonstrates how to Do a volley to length return of serve for squash.

Squash is a racquet sports game, seemingly similar to tennis, but played on a small indoor court with hollow rubber ball, much small than a tennis ball. Squash is an intense, high impact sport. This squash tutorial demonstrates how to Do a backhand return off a power serve for squash.

Squash is a racquet sports game, seemingly similar to tennis, but played on a small indoor court with hollow rubber ball, much small than a tennis ball. Squash is an intense, high impact sport. This squash tutorial demonstrates how to Retrieve a forehand from the back corner in squash.

Squash is a racquet sports game, seemingly similar to tennis, but played on a small indoor court with hollow rubber ball, much small than a tennis ball. Squash is an intense, high impact sport. This squash tutorial demonstrates backhand return serve options for squash.

Squash is a racquet sports game, seemingly similar to tennis, but played on a small indoor court with hollow rubber ball, much small than a tennis ball. Squash is an intense, high impact sport. This squash tutorial demonstrates a volley boost backhand return of serve for squash.

Squash is a racquet sports game, seemingly similar to tennis, but played on a small indoor court with hollow rubber ball, much small than a tennis ball. Squash is an intense, high impact sport. This squash tutorial demonstrates a backhand return: volley drop off a power serve.

SSH is amazing, and we praise its existence on Null Byte for many reasons. Notably, it allows us to reroute our traffic through encrypted ports on our local host to be sent to its destination when on the go. You can even control your home computers remotely over a secure and encrypted connection. This is handy for a multitude of reasons.

Do you need proxy access, but cannot have it for some reason? The most common perpetrator behind the issue is the network you're trying to access the pages from. Some networks will block websites, then go as far as filtering out all of the web queries for terms like "proxy" because it can get around their filter. Quick web proxies can be used for tons of other things, though.

You might be sitting there thinking that I'm crazy, but the truth is you're only partially right. You can get free text messaging for life, all for a cheap, one-time fee. But, how can that be possible? An exploit in AT&T's prepaid GoPhones is the culprit behind this sweet, oh-so rare opportunity for exploitation. The exploit grants a lifetime of free texting, assuming that the company stays afloat from now until the end of time.

I have to say, the Xbox 360 controller is the best controller ever created. When I first held it back in 2005, I swore that the dudes working at Microsoft came over and took a molding of my hands because of how great it felt. The thing felt like it was born there.

The biggest struggle with flashing DVD drives on Xbox 360s has been the price tag of the probe to extract keys on some drives. The probe and kit is required to extract the DVD key, which is needed to perform a drive repair, flash, or backup of any kind. Who wants to pay big bucks for the "pro" kit and then get added to a huge waiting list behind a million other people looking to buy the same product? We can hack the same thing together at home!

Null Byte is looking for moderators! In today's Null Byte, we're hacking Netflix. As most of you know, Netflix is a subscription service that streams movies and TV shows to your devices over the internet. A common stance amongst my Xbox Live friends is that Netflix isn't worth the cost. The instant movies predominantly consist of old titles, and new movies aren't added often enough.

Here's another Null Byte on hacking our Skyrim game saves. Some of the rarer items in Skyrim are really fun to play with. However, seeing as they are rare, you will probably not see all of the best weapons in the game. Null Byte doesn't take too kindly to games that don't give us the rarest items when we please. Let's beat this game into submission by hacking our game save files via hex editing.

With a lot of Null Byters playing around with Linux because of its excessive use in the hacking world, some of you are bound to run into some trouble with the installation at some point or another. If you make a mistake, or you're intimidated by the wonky-looking installation screen, you may want to just stick with Windows. However, you may notice it can be hard to go back once you've crossed a certain point in the installation. Your Windows installation may be broken or unbootable.

Ever since kernel 2.6.xx in Linux, a lot of the internet kernel modules for wireless interfaces ended up becoming broken when trying to use monitor mode. What happens commonly (to myself included) is a forced channel that your card sits on. No good! For users of airodump and the aircrack-ng software suite, the software has become unusable.

Many users of the virtualization software VirtualBox may have noticed that the USB system has been pretty buggy for quite a long time. I've had my USB randomly duck out on me way too many times to count. This can really be difficult to deal with when you require access to the devices and files from the host system.

Let's face it, CDs and DVDs are a thing of the past. We no longer use them as a storage medium because they are slow, prone to failure in burning, and non-reusable. The future is flash memory. Flash memory is cheap, fast, and efficient. Eventually, flash drives might even replace discs as the preferred prerecorded selling format for movies.

Here's yet another one of those pesky multi-step time sink achievements, but the reward is great. To get the 'Genius' achievement in Batman: Arkham City, you have to rescue all five hostages The Riddler has taken. It should be noted though that you'll need a certain amount of Riddler trophies to activate the hostage rescue missions.

Carol Baldwin-Moody of Wilmington Trust describes the challenges that are present in her line of work as senior vice president and chief risk officer. There is a strong legal backing to every major issue in today’s society. Baldwin-Moody has come across several scenarios that aren’t covered by the dated constitutional law in effect today. In past years, a risk officer was thought to be a management concept that would be useful, but not worth the investment. Lately, a risk officer career has b...

Welcome to Part 3 in my series on protecting your computer from prying eyes (Part 1, Part 2). In today's segment, we will be going over drive encryption using the TrueCrypt program on Windows OS. Drive encryption is a technique that masks your data with a cryptographic function. The encryption header stores the password that you have entered for the archive, which allows the data to be reversed and read from. Encrypted data is safe from anyone who wants to read it, other than people with the ...

Encryped traffic and tunneling is a must when away from home to keep you and your information safe. SSH tunnels can be slow, and are heavily encrypted. VPNs are an all port solution, and proxies are just not what we need in most cases. Then, there is Tor.

Everyone has deleted a file or folder on accident before. Sometimes people even delete stuff on purpose, only to find out that they needed the files after all. If you're experiencing one of these mishaps, don't worry, file recovery is possible in most cases!

OpenVPN is the open-source VPN (Virtual Private Network) client, used over the PPTP (Point to Point Tunneling Protocol). It allows you to connect to a remote network over a secure, encrypted connection and mask your IP addresses over all ports. Since there is only one "hop," the network speeds are barely effected and are far more secure.

Without Japan, video games would not be very fun. Atari's early work was important, but Japanese developers, publishers, and hardware makers were responsible for almost every major advance in video games for the first 25 years of their mainstream existence. In recent years, it has often been said that they have become less relevant than Western developers. In the indie games movement— (our area of greatest interest here at Indie Games Ichiban)—Japan does not have anywhere near the presence th...

What do you do when you desperately need to put a parking garage into the bottom floor of your Victorian apartment building, but the city's Department of Planning says "No". The simple and expensive answer: Create an elaborate secret garage door. If you own a pretty building, it is well within the jurisdiction of the Landmark Commission to inform you that even though you own the piece of property, you cannot remodel it any way you want. Seems un-American. But in San Francisco, specifically th...

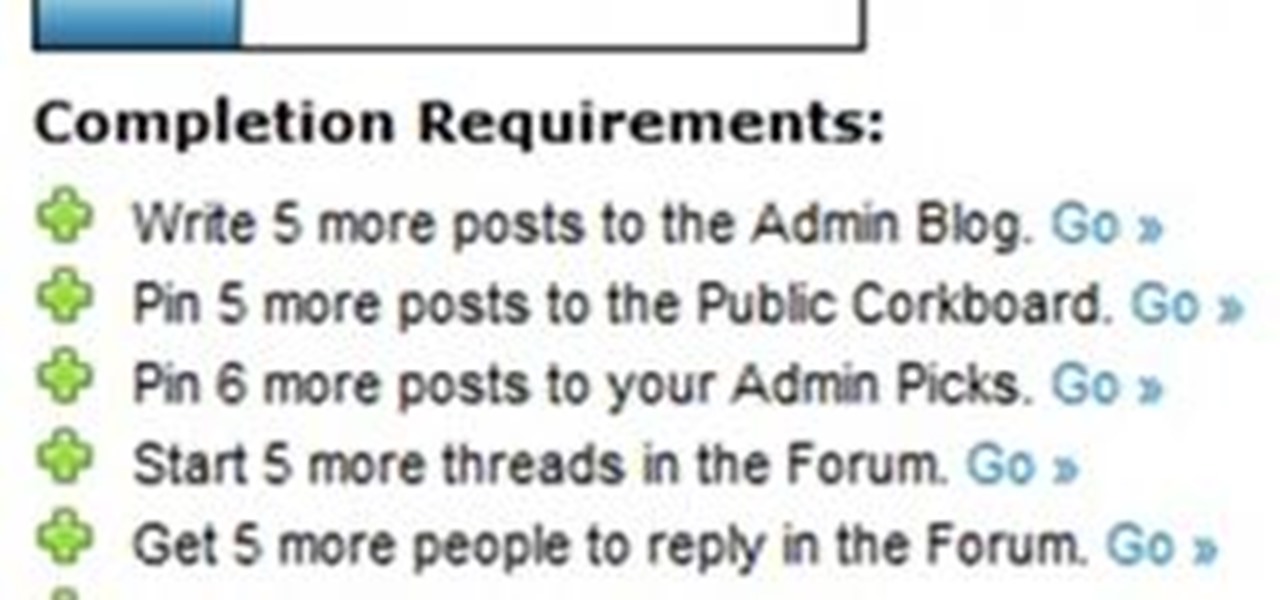
Some update notes that you should take notice to are:Celestian Furniture Yes you read that correctly! Celestian Furniture has come to the Spiral, as well as recipes for furniture from our newest underwater world! Keyboard Shortcuts

Progression, isn't it great? It used to be that video games only rewarded you with game scores. The satisfaction was always at the end, and all that mattered was getting there.

We're set to see the actual debut of Google Daydream on October 4, and it'll hopefully serve as a significant step up from Cardboard—their current virtual reality smartphone platform. If you want to get an early taste, you can set up a development kit—you just need two phones to do it.

If you want to have windows .iso files for various purpose like you want to have windows 7 in virtualbox, then you need an .iso file. There are many methods of creating an .iso from installed windows. But what if microsoft provided all of them( I mean 7,8 &10) free of cost. The only requirement is that you own a product key for the respective Windows edition (and that's also is not a painful task to get).

The latest Android N preview build was released today, April 13th, and included Emoji Unicode 9.0 support, among other things. The highlight is definitely the emojis, and the new designs are intended to look more realistic than the older, blobbier emojis. The update also allows for skin tone variations and adds new emojis like the face palm, selfie, and the juggler, to name just a few. Get These Emojis Right Now

Hello everyone. As many of you know, we've successfully launched the Null Byte Suite for our wonderful community. In addition to the prepackaged tools, there is a dedicated GitHub repository where tools submitted by the community will be pushed to for distribution in the suite. There have only been a couple submissions, and out of them, only one fit the requirements. So, out of anticipation, we've added it to the suite!

Welcome everyone Today i will show you a simple but very useful way to stop your ip leaks . In order to stay anonymous on the web you HAVE to do this.

Take a minute and think about how many times a day you press the home key on your iPhone . . . a lot, right? It is quite literally the most important button on your device. If the home key stops working, you won't be able to multitask or back out of apps to go to your home screen, so preserving its life should be priority, otherwise you're stuck using one of these tips for fixing your home button. Luckily, for 5S users, you can add a tweak that will utilize your touch ID sensor, instead of ha...

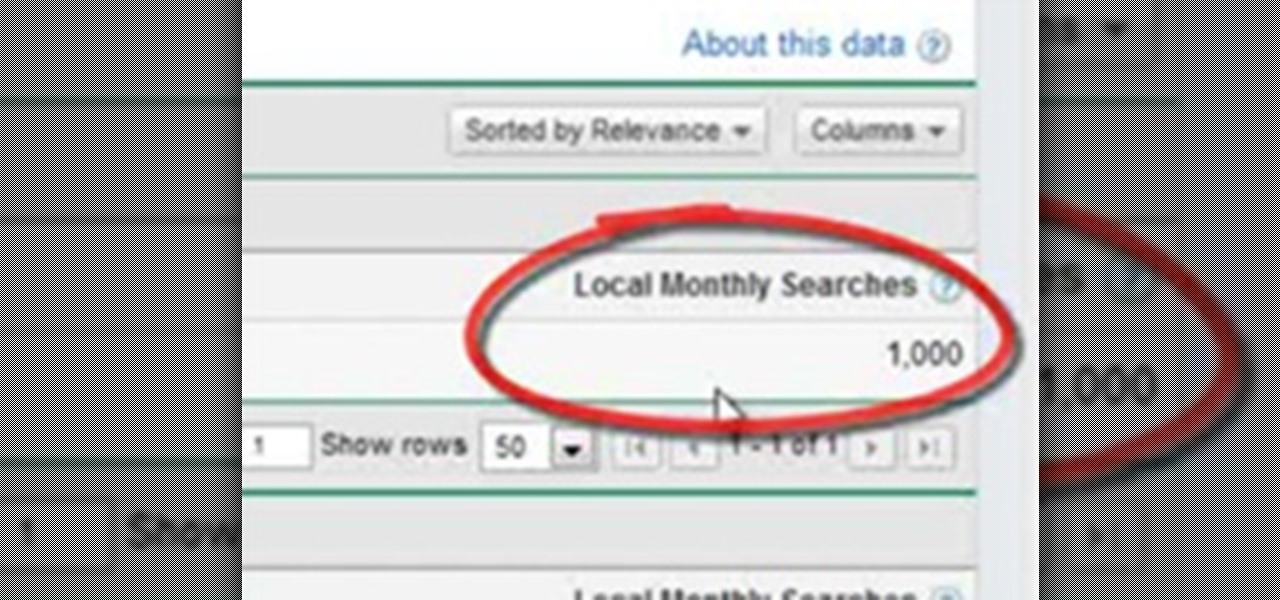
The importance of keyword research is for everyone wanting to create a website. Are you a dog trainer or a golfer? A billiard player or a surfer? Whatever niche you're in or skills you have right now, you can document them and save some for the rainy days. You can create a one-page website or a blog out of it and later on market it to respond to its financial benefits.

Christmas is almost over— all of the presents are unwrapped, all of the prime ribs have been eaten, the whole family's drunk off eggnog— and soon it will be time to forget about Christmas until next year.

Watch this "Grease On Your Hands" video tutorial from the Washington Post to see how to change the engine oil in your car properly.

Today's guide is on creating a password protected folder on Windows 7 without any additional software. Yes, you heard that right. No extra software at all! This guide is intended for beginners. But please note, this method should not be used to store financial or otherwise highly confidential material. It might be a good place to hide a planning document for a family member's birthday party or similar occasion where you need to keep something secret temporarily.

Have you ever wondered how credit card numbers work? I mean, how they really work? How do they come up with the numbers? Credit cards actually follow a very specific pattern. Let's take a look at how they're set up.

Call Your State's Nurse Aide Registries for School Inquiries