Between Renault Truck's testing of the HoloLens in factories and BMW promoting its newest model through Snapchat, the auto industry is hot for augmented reality to improve internal operations and engage consumers.

There are more than 2 billion Android devices active each month, any of which can be hacked with the use of a remote administration tool, more commonly known as a RAT. AhMyth, one of these powerful tools, can help outsiders monitor a device's location, see SMS messages, take camera snapshots, and even record with the microphone without the user knowing.

The last quarter of 2017 brought us some downright excellent smartphones. Between the iPhone X, Pixel 2, and Note 8, consumers have more fantastic options than ever when choosing a new device. It's now the perfect opportunity for Samsung to set the tone for 2018 smartphones with their exceptional S9 and S9+.
When the Super Bowl airs, every other TV network puts on reruns because no one wants to face that juggernaut for ratings. The launch of a new iPhone is the Super Bowl of the tech world, with the launch of the iPhone X being the biggest one yet.

In our previous article, we learned how to take advantage of a feature, Dynamic Data Exchange (DDE), to run malicious code when an MS Word document is opened. Because Microsoft built DDE into all of its Office products as a way to transfer data one time or continuously between applications, we can do the same thing in Excel to create a spreadsheet that runs malicious code when opened. The best part is, it will do so without requiring macros to be enabled.

While other devices are moving away from fingerprint scanners (cough, iPhone X), for many, a fingerprint scanner provides the best balance between security and speed. Typically, the rear fingerprint scanner on the LG V30 is quick and accurate, but every so often the phone will not recognize a registered fingerprint.

For a company who hasn't released a product and has a reputation for being secretive, Magic Leap sure has a tendency to make waves. Over the past few weeks, they've refreshed their website design, released an abstract YouTube video, and announced a partnership with Madefire to offer mixed reality comics on its device whenever it launches. Next, they are gearing up for another round of funding.

Bluetooth Low Energy (BLE) is the de facto wireless protocol choice by many wearables developers, and much of the emerging internet of things (IoT) market. Thanks to it's near ubiquity in modern smartphones, tablets, and computers, BLE represents a large and frequently insecure attack surface. This surface can now be mapped with the use of Blue Hydra.

According to Digi-Capital, investors poured $1.8 billion into augmented and virtual reality companies over the last 12 months, including $300 million in the third quarter. These investments are not made without a means to monetize products and services.

The launch of the latest line of iPhones came and went without major revelations for advanced AR hardware other than the next iteration of processors and cameras.

Outside of early military applications, augmented reality is a relatively new technology. It stands to reason that the next company to make a splash in AR would be a startup, and Techstars wants to help.

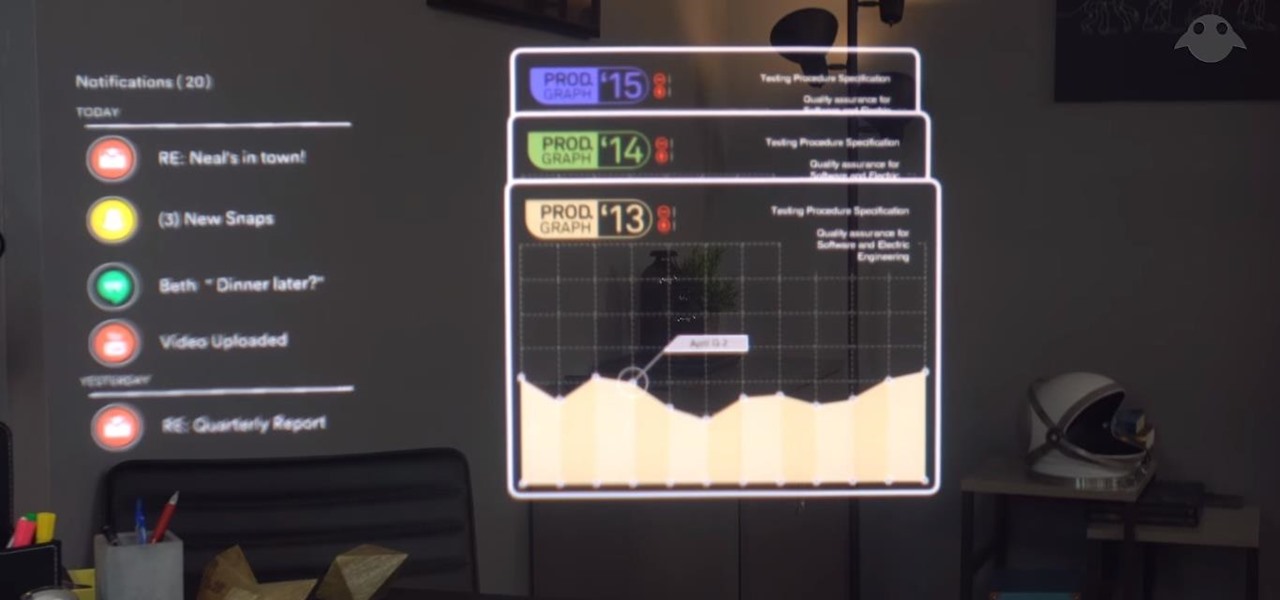
Augmented reality can be used to fascinate and entertain, but it can be applied in the workplace. While companies on the entertainment end received their votes of confidence via funding, two companies working with enterprises demonstrated their worth by teaming up to pursue customers.

Augmented reality sells, but who's buying? Over the past week, two companies made executive hires to capitalize on the growth of augmented reality as a service to sell to other businesses. Meanwhile, two companies joined forces to offer augmented reality tools to headset makers and content providers.

All eyes will be on Tesla CEO and founder Elon Musk tonight to see if he is reveals details about the status of Tesla's challenged Autopilot at tonight's official Model 3 launch party.

RouterSploit is a powerful exploit framework similar to Metasploit, working to quickly identify and exploit common vulnerabilities in routers. And guess what. It can be run on most Android devices.

We continue to field stories underscoring the strong trends of Investment in augmented reality in various sectors. This week, one company strengthens their offerings to the enterprise sector, while two other companies capitalize on the promise presented by augmented reality to consumers – specifically, in gaming.

Natural remedies used through the ages abound, especially in Asian medicine. The willow-leaved justicia plant, found throughout Southeast Asia, has traditionally been used to treat arthritis, but scientists have just discovered it contains an anti-HIVcompound more potent than AZT. AZT was the first drug approved to treat HIV, and is still used in HIV combination therapy today.

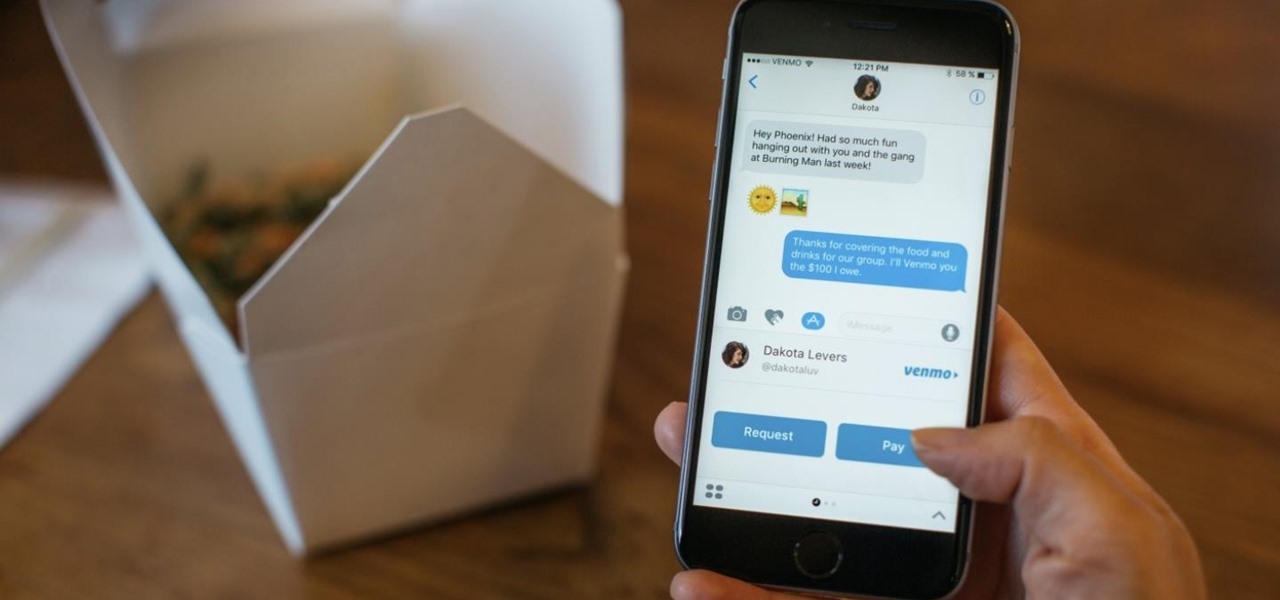
For $0.25 per transaction, PayPal will soon be allowing you to transfer money through their app that will get delivered within seconds rather than days.

Uber's struggles are expected help Lyft get ahead in driverless development as it confirms its third partnership with autonomous tech company nuTonomy today.

Over the past week, we are seeing more companies capitalizing on services leveraging augmented reality. One company secured funding to expand their service, while two other companies grow its own services through acquisition.

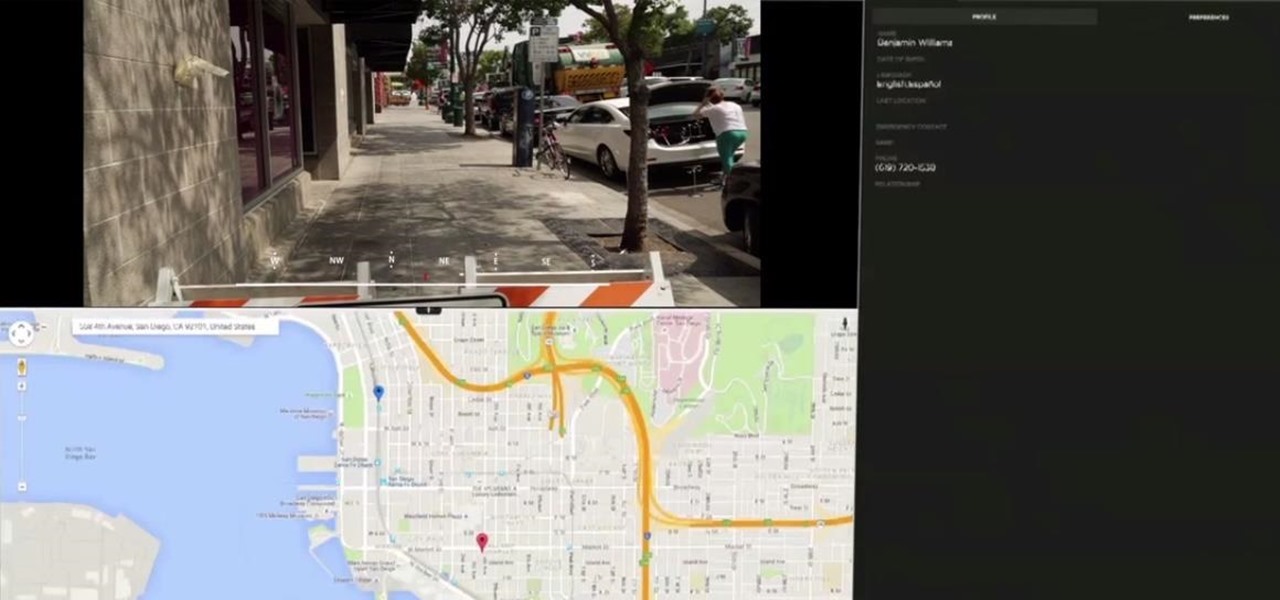
This week's Brief Reality is led by a pair of stories with an eye to the future of the augmented reality industry, first in terms of standards for the industry, then with regards to its future applications in the automotive realm. Finally, one company looks to boost its future sales with an executive hire.

Reports of Zika-related birth defects are coming in at shockingly low rates in Puerto Rico. While that might be something to cheer, one former US government official is saying there could be a nefarious reason for the low numbers.

In a world increasingly regulated by computers, bugs are like real-life cheat codes. They give you the power to break the rules and do good or bad without ever leaving your seat. And government agencies around the world are discovering and stockpiling unreported bugs as cyberweapons to use against anybody they see fit.

At a global security conference in Munich, philanthropist and businessman Bill Gates spoke about the next pandemic and a dire lack of global readiness. Here's how his statement could come true—and how to be ready when it does.

The rate of preterm birth has been increasing in the United States for unknown reasons, causing increased health risks for infants born too soon. But researchers may have found a signal that could help doctors plan ahead for, or even prevent, early birth with a simple swab of the vagina and cervix during pregnancy.

Super Mario Run was released for iOS on December 15, 2016. Even though it debuted as a "free" app, almost all of the playable content was hidden behind a ridiculous $10 unlocking package. Despite coming with such a hefty price tag and receiving a two-star rating on the day of its release for iOS, Android users are still very much interested in giving this game a whirl.

When we talk about augmenting our reality, we often first think about vision instead of our other senses—but there's more to an immersive experience than what you see. One inventor figured out how to utilize sound and touch to create a simple, upgraded version of laser tag that you can play with your smartphone.

Welcome back, my fledgling hackers! Over the years, we have examined multiple ways to own, exploit, or compromise a system. On the other hand, we have not spent a lot of time on denial-of-service (DoS) attacks.

Welcome back, my aspiring hackers! In many of my earlier tutorials, I mentioned the complementary nature of hacking and forensics. Both disciplines, hacking and forensics, benefit from a knowledge of the other. In many cases, both disciplines will use the same tool. In this tutorial, we will use another tool that can be used in either discipline—Sysinternals—a suite of tools developed by Mark Russinovich.

Are you a follower or a leader? No matter how you respond, we all know that leader is a more desirable position to hold. Great leaders typically share a few qualities—confidence, intelligence, and strength, to name a few—but one of the most intriguing is their appearance. With the right facial structure, and some well-rehearsed expressions, you can trick others into thinking you're leader material.

Check it out: you save more dough (ba dum bump) when you order a large pizza than with any other size. Why is this true? NPR reporter Quoctrung Bui's engineer friend pointed out that a medium pizza was twice as big as a small one, yet only cost slightly more.

Update: June 19, 2014 Android 4.4.4 has been released, fixing a small security bug in 4.4.3. The factory images have already been made available to all current-generation Nexus devices, and I've linked them out below. This does not affect the process depicted, you can still use these same steps to bring your device up to date with this latest release.

Welcome back, my greenhorn hackers! Although we have focused primarily on technical hacks here, social engineering can sometimes be especially effective. This one requires a bit of technical skill, but not too much. In addition, it's limited by how specific a target you can choose—but it will work.

One of the biggest problems in data security is authentication of data and its source. How can Alice be certain that the executable in her inbox is from the venerable Bob, and not from the not-so-venerable Oscar? Clearly Alice wants to know because if this file is actually sent to her by Oscar, the file might not be a game, but a trojan that can do anything on her computer such as sift through her email and passwords, upload her honeymoon pictures, or even turn on microphones and webcams. Thi...

Welcome back, my neophyte hackers! In today's hack, we're going to have a bit of Halloween fun. Have you ever had a boss who made you miserable with his micro-management and nagging? Maybe you thought he unfairly fired your friend/colleague? Well, now here's your chance to get a bit of revenge and keep him or her off your back!

Remote Desktop gives you access to your Windows 8 PC or device from wherever you are to run your applications and access your files remotely.

3D printing has been around for a while, but until recently it was used mostly for prototyping and research. Now, with technological advancements, it seems like everyone is using 3D printers, from crime scene investigators to garage hobbyists and hackers. Below are some of the most innovative uses people have come up with so far.

Access your computer's BIOS settings

This video will show you how to disable secure virtual memory in Mac OS X. From the top left of your screen click on the apple icon. Click on system preferences from the pull down menu. Click on the security icon. Click on the image of the closed lock from the bottom left of the window so that you can change make changes.

Get a new perspective on computing with an HP Tablet PC. HP's Tablet PCs are well-equipped personal notebooks, with a significant twist. The display turns around one hundred and eighty degrees, transforming your notebook into a flat tablet touchscreen PC.