WonderHowTo is a how-to website made up of niche communities called Worlds, with topics ranging from Minecraft to science experiments to Scrabble and everything in-between. Check in every Wednesday evening for a roundup of user-run activities and how-to projects from the most popular communities. Users can join and participate in any World they're interested in, as well as start their own community.

You're sitting in front of your grandmother's Windows XP machine that has the worst infection you've ever seen. Safe mode? No dice. Restore points? They're compromised. Even worse, all of the files are hidden and none of the executables will run! This leaves her computer in a bricked state. Without some serious CPR, it will be lost to you. Sure, you could just reinstall the system, but then you might lose all of that valuable data.

When I was attending college, my friends had a phantom thief in their dormitory. Almost every night, a different item of food would go missing, never to be seen again. There was constant speculation as to whom the thief was and how to catch them. Security cameras were deemed too invasive, but none could think of another method of surveillance... until today.

Injection is an attack vector that involves breaking out of a data context and switching into a programming context through the use of special characters. These characters are significant to the interpreter being used, but not needed for the general user input being asked for.

Wouldn't it be nice to just sit at your buddy's house, plug into his network, and see exactly what he's doing? What if it was as easy as that? What makes packet sniffers like Wireshark such potent tools is that a majority of local area networks (LANs) are based on the shared Ethernet notion.

Here at Null Byte, we try to inform and teach the community on ways to navigate the Internet in that special way, as well as staying safe along the trip. That being said, I need some help from all of you! There is a lot of information to cover and I know we have some smart users lurking around. We would love to hear from you.

Last week, we had a great contribution from Christopher Voute, who introduced us all on some of the basic moves in Python. Now, who else will share their knowledge and tackle some of the topics below?

Did you know there is hidden data in your digital pictures? Well, there is, and that data might be a security risk to you. Think back at all of those pictures you're in and are connected with. I'm sure some of those you'd like to distance yourself from. And surely you wouldn't mind checking out the metadata in a few of those images. In this article, we'll be going over how to do just that.

Cryptography is a quintessential part of computer security in the modern world. Whenever you buy something on eBay or log into Facebook, that data is encrypted before it's sent to the server in order to prevent third parties from eavesdropping and stealing your sensitive information.

In my recent Darknet series, I attempted to connect the dots on the Deep Web. I covered the two largest anonymity networks on the Internet today, Tor and I2P. While my initial four articles were meant as an introduction, I ended up receiving a lot of interesting comments and messages asking the technical differences between the two. I'd like to thank all of you for letting me know what was on your minds, as you should always!

Social engineering is described as the clever manipulation of the natural tendency of human trust. All of the passwords, locks, and encryption in the entire world are useless against a good social engineer who can charm or trick you into giving it up.

In the last article, we left off with the Tor network and its hidden services. As I mentioned, Tor is not the only option in the game, and I want to offer a general introduction to I2P.

Are you the expert hacker we're looking for? Do you have a great idea for an article on Null Byte? Do you have a passion to write, and more importantly... teach?

Eventually, we plan on doing some root the box competitions here at Null Byte, but we're still looking for a server to play on. Anyone want to donate one? You won't regret it. Root the box is like 'king of the hill', except you have to hack a server and maintain access. Each server will have numerous known security holes, but until then, let's get back to the regular weekly coding sessions and realistic hacking missions on HackThisSite.

We'd like this to be one of the last HTS mission announcements, at least for now. As soon as Null Byte finds a server to play with (anyone want to donate one?), we are going to start doing root the box competitions, which is like king of the hill, except you have to hack a server and maintain access. Each server will have numerous known security holes. But for now, back to the normal flow of things...

I'm sure we've all heard about MSN and Yahoo! Messenger, right? They can be useful, but the setup can be quite time consuming for those who need to use it just once or twice—and the privacy statements are a real bother. For example, we must provide our real details. You could use Fake Name Generator, but if you get caught, you will have your account suspended. I don't have a law degree, but to my understanding the United States recently passed legislation that gives the authorities the power ...

We're aiming for this to be one of the last HTS mission announcements, at least for now. As soon as Null Byte finds a server to play with, we are going to start doing root the box competitions, which is like king of the hill, except you have to hack a server and maintain access. Each server will have numerous known security holes. But, for now, back to the normal flow of things...

WonderHowTo is made up of niche communities called Worlds. If you've yet to join one (or create your own), get a taste below of what's going on in the community. Check in every Wednesday for a roundup of new activities and projects.

WonderHowTo is made up of niche communities called Worlds. If you've yet to join one (or create your own), get a taste below of what's going on in the community. Check in every Wednesday for a roundup of new activities and projects.

It has been suggested that about 150 million internet users will be affected by today's blackout of Wikipedia in protest of SOPA and PIPA. If you don't know what those are, go here and read up on it, and then take action yourself! After you've contacted your Representatives about these bills, you'll probably still need to get some work done today using Wikipedia's English-language site.

This tutorial will be based on creating a partition in Windows Seven. I have seen so many people attempt to do this themselves without guidance. Ultimately, they end up with a corrupt system. The aim of this tutorial is to make sure you don't corrupt your system.

If you've ever wondered how software pirates can take software and crack it time and time again, even with security in place, this small series is for you. Even with today's most advanced methods of defeating piracy in place, it is still relatively easy to crack almost any program in the world. This is mainly due to computer processes' ability to be completely manipulated by an assembly debugger. Using this, you can completely bypass the registration process by making it skip the application'...

Another Community Byte announcement from Null Byte! The Community Byte projects serve to teach people in a co-operative, hands-on manner. Learning from experience and immersing yourself in a subject is the best way to learn something foreign to you. In our sessions, we have started to both code and complete HTS missions. There is something for everyone here, so make sure you join in on the fun learning experience.

Friday's Community Byte was weird. The intent was to do a HackThisSite mission, but upon time to begin, everyone in there was programming without my assistance, with the help of Sol Gates. This is great! It's really awesome that everyone enjoys programming that much and will make the effort to learn even when I am not present. So, a tip of my hat to Mr. Sol Gates and the rest of you fine people.

Big name individual hackers and hacker groups everywhere in the news are getting caught and thrown in jail. Everytime I see something like this happen, I won't lie, I get a little sad. Then I wonder, how are these guys getting caught? If a group like LulzSec, with all the fame and "1337-ness" can get caught, I think my hacker comrades are doing something wrong.

Welcome to Minecraft World! Check out our advanced tutorials and come play on our free server. Oh, the power of redstone! But, what good is any technology if it can't be harnessed for killing? Here's a redstone build for the mad scientist in each of us.

I have had a lot of people ask me, "How does my neighbor keep getting into my wireless?!". Chances are, these people are all using WEP, a deprecated wireless encryption protocol. Either that, or you are using one weak WPA passphrase.

If you're interested in bypassing Windows and Linux passwords, there is a great tool from the good people at Kryptoslogic. Have you ever forgotten your administrator password? Have you ever bought a used computer with a password on it? Well, Kryptoslogic have created a boot-disc call 'Kon-Boot', which allows you to bypass any Windows 32 or 64 bit OS, as well as Linux passwords. There is both a paid and freeware version available.

Gone are the days when you had to carry a clunky DynaTAC to make phone calls, pocket phone book for you contact list, Sony Discman for your tunes, and wallet for you cash and credit cards. Today, all you need is your smartphone. To be specific, Google's Nexus S 4G on Sprint.

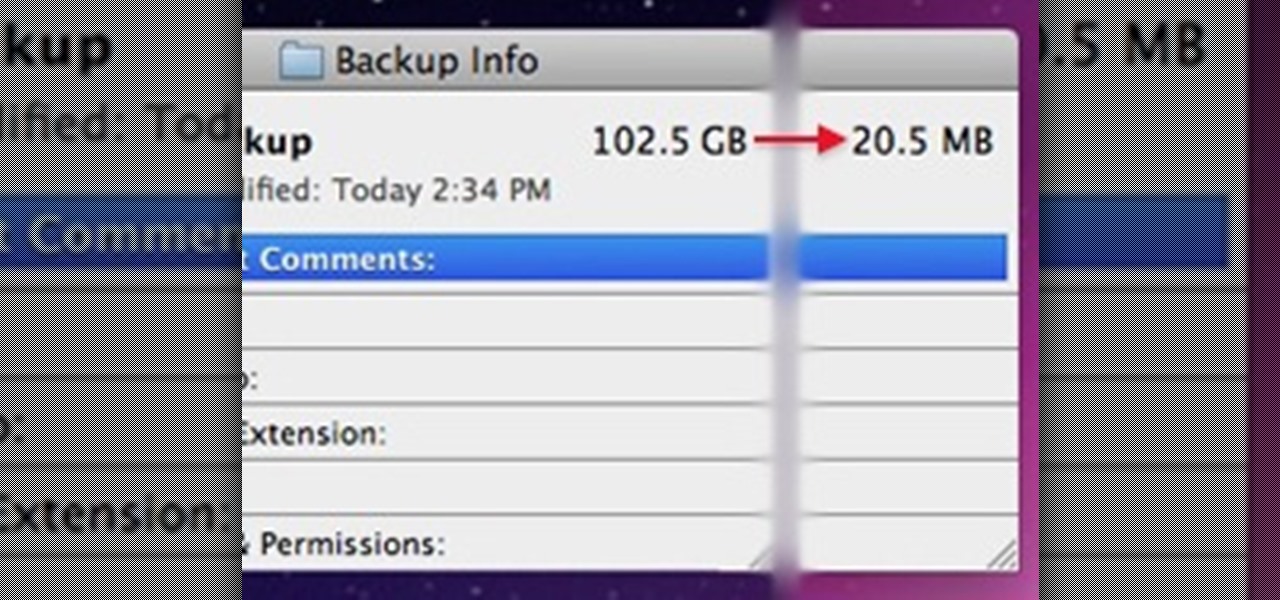
Do you ever wonder if the files you're trashing on your Mac are actually trash? Let's say there are 80 million computer owners running Mac OS. If each user trashes at least 10 files each day, that's 800 million deleted files that cease to exist every 24 hours. If that doesn't sound like a lot to you, a month would equal 24 billion junked files, a year—nearly 1 trillion.
To go Open Source or go proprietary? There is a common conception that open-source is unsafe and insecure and therefore companies should rather go for proprietary solutions. They think that because software is termed "open-source", that the world can see the vulnerabilities of the software and might exploit it, and less informed people tend to think that open-source software can be modified while it is running.

By now, you probably know that your iPhone secretly tracks and stores the locations you've visited in a backup folder on your computer's hard drive. The files are unencrypted, which means anyone with access to your computer or device can retrieve the information, which is downright scary. But Pete Warden and Alasdair Allan are making it fun with their iPhone Tracker application, which lets you map out everywhere you've been with your smartphone.
USE WINDOWS 7 ULTIMATE x64 w/ all the latest updates always OF COURSE AND... USE THE ASTON 2 SHELL REPLACEMENT, MENU, DESKTOP, W/ THEMES...

disguise yourself however you like Go to an airport. have a suitcase full of fake illegal items such as powder (cocaine), crushed leaves (weed), guns, knives and dynamite . make sure it all looks real and also something metal to set off the detector so the search your bags.

Disguise yourself how ever you like. Go to an airport. Have your suitcase full of fake illegal items such as powder (drugs), crushed up leaves (weed), guns and Knives dynamite make sure everything looks as real as possible and also something metal to set off the detector (so they search your bag).

A press release should be about news. It should have a sense of urgency about it and grab the reader’s attention from the outset. A good press release must quickly answer the journalist’s immediate questions:

Over the past couple of weeks, there have been a series of high-profile hacks and leaks. From the rooting of CombinedSystems, to a secret FBI conference call leak, all the way to the distributed denial-of-service (DDoS) attacks on U.S. government sites—with a lot in-between. As governments move to close their long fingers around the free speech that exposes their secrets, this shadowy collective of loose-knit, but like-minded individuals are hell bent on preventing them. Or are they?

If you've read Alex Long's last two articles in this series (Part 1 and Part 2), you know by now that making money rarely is risk free, and generally plays out to be a high risk-high gain/loss scenario. The best way to make money is to have money, so for this article, lets assume a financial backing of about $10,000 dollars. For the sake of simplicity, I'm going to be working with online trading systems in this article. Some stocks are traded on exchanges, where buyers meet sellers and decide...

BioShock is one of the best games of all time. It combines FPS gameplay with RPG storytelling and supports multiple systems better than any other game, that much is for sure. And the setting of its amazing story is a place called Rapture, a high-tech libertarian colony at the bottom of the Atlantic built by Andrew Ryan, a greying industrialist clearly inspired by John Galt and his creator Ayn Rand, the mother of Objectivism and modern American libertarianism in general. Ryan is a Soviet exile...

Anonymity is very important to many internet users. By having your "e-identity" exposed online, you can be stuck with a number of unwanted issues, such as: