How To: Find the smiths in Wizard101
Get the inside scoop on Wizard101 hacks, cheats, tricks, tips, and walkthroughs! Watch this video tutorial to learn how to find the smiths in Wizard101.


Get the inside scoop on Wizard101 hacks, cheats, tricks, tips, and walkthroughs! Watch this video tutorial to learn how to find the smiths in Wizard101.
Check out this informative video tutorial from Apple on how to do more with the Sidebar in the Mac OS X Finder. Learn about the Sidebar devices, the Sidebar shared, the Sidebar places, and the Sidebar search for. Mac OS X. It's what makes a Mac a Mac.
Check out this informative video tutorial from Apple on how to use the basics of the Mac OS X Finder. Learn about the Finder basics, the Sidebar, view buttons, and Quick Look. Mac OS X. It's what makes a Mac a Mac.

The Hairy Bikers explain the best way to cook Noah's Pudding, a milk and rice based dessert. Delicious recipe idea from BBC foodshow 'Hairy Biker's Cook Book'.

In Turkey, near the Syrian border, the Hairy Bikers demonstrate the best way to build and cook the perfect doner kebab. Brilliant recipe clip from BBC food-lovers show 'Hairy Bikers Cook Book'.

CJ Jackson, Director of the Billingsgate Seafood Training School shows how best to fillet a mackerel.

Simon King, one of the Hairy Bikers falls off the dock in Vietnam during filming leaving Dave Myers alone to cook a delicious crispy beef recipe. Great idea for dinner from BBC cooking show 'Hairy Bikers Cook Book'.

The Hairy Bikers demonstrate an easy step-by-step guide to making a traditional Palak Paneer dish in India. Great recipe idea from BBC cookery show 'Hairy Bikers Ride Again'.

Stuck for supper? Try this delicious wheat-free recipe idea from the Hairy Bikers Cook Book - an Indian lentil and rice flour doughnut recipe known as a Vada.

New to the pranking business? Well, this video tutorial ought to start you off good and proper. Here, you will learn how to perform the liquid pen prank. Maybe it's called something different, like water pen prank, but the point is to remove everything from the pen, then fill it with water and return the cap. Wait and watch as someone opens the pen lid to spill water all over their important document.
Need a little help with your math homework? No problem, the Math Centre offers students video tutorials that will provide as a reference guide for self-study. Students get self-study resources targeted to the needs of individual courses, and teachers gain generic mathematics support and study materials for use with students.

Check out this highly educational video for all you veterinarians, or farmers, to see how to do a rectal palpation of a horse (mare) to feel the tract and ovaries for finding the recurring period of sexual receptivity and fertility.

This is an excellent video, by the wonderful Dr Jack Newman, showing a classic cross-cradle hold, and a baby latching well. The important part of this video is what's happening at the mouth/nipple exchange. Learn tips for how to breastfeed a baby properly and comfortably.

This film is about gold. Gold diving. Use of the hookah rig to find gold. Gold flakes, nuggets, and platinum nuggets are shown. Gold and platinum are 15-19 times heavier than other streambed materials and concentrate in low pressure areas and cracks that run across rivers and streams. You look for a crack on the bank, and follow it out until you meet the "gold line" and there you suck it out with your dredge. Gold will be on the outside edge of a river gravel bar, at the head of the bar (larg...

This one's for Party Boy Chris Pontius. He gets to be 'The Stud'. The Stud, dressed in his thong and bowtie, stands facing an unwooded section of "The Wall", constructed from gyprock with vertical 2 by 4 studs placed at 2 foot intervals. Meanwhile, on the other side... "The Foremen" get into their construction gear and take turns attempting to find the stud by punching a hole through the wall... this goes on until the stud is found.

This is a great instructional video on how to find oblique asymptotes of rational functions. Let us take the example f(x)= x square+4x-12 over x-6. Now we have to find the horizontal or oblique asymptotes of this rational function. The higher power here is x square which is at the top and hence we have to find oblique asymptotes of this function.When we divide x square+4x-12 by x-6 we get x=10 and the reminder is 48. Now you can easily write down the final answer. The oblique asymptote for th...

You may not have thought of dorks as powerful, but with the right dorks, you can hack devices just by Googling the password to log in. Because Google is fantastic at indexing everything connected to the internet, it's possible to find files that are exposed accidentally and contain critical information for anyone to see.

Imagine a scenario where you're nowhere near your iPhone, but it's on loud, and you really need to silence it. An alarm may be blaring, notifications could be spitting out sounds left and right, and calls may be ringing. Things can get annoying real quick for whoever's around it. Plus, all that attention makes it easy for someone to find and possibly steal your iPhone. Luckily, you can quiet it down.
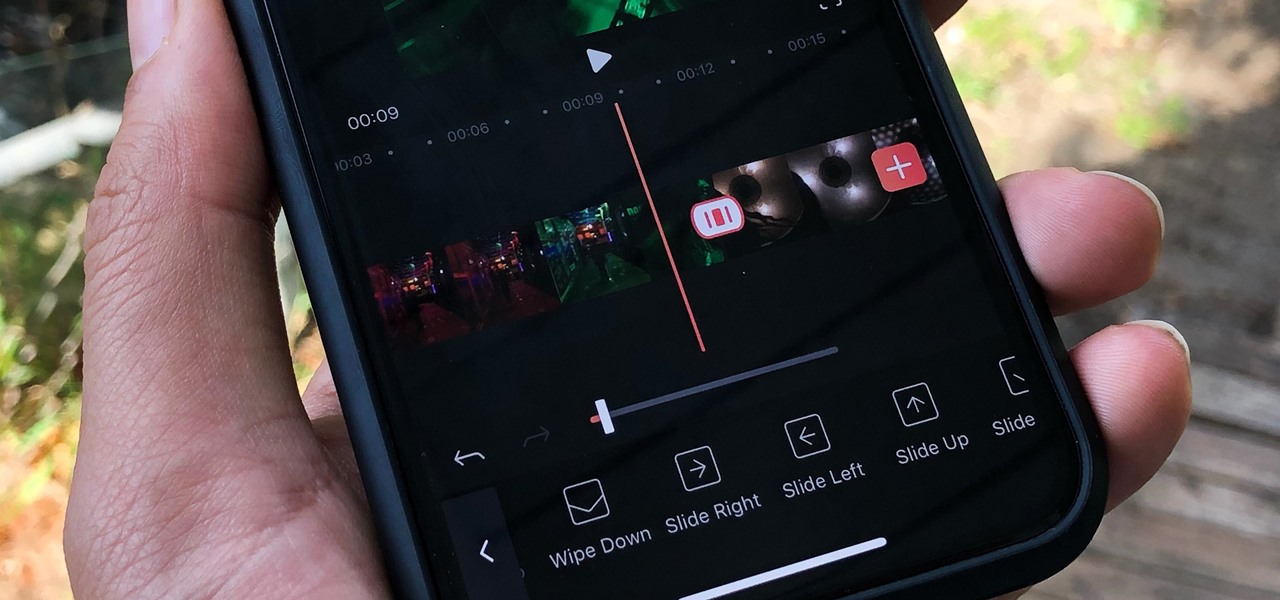
An edited video with lots of different clips needs great transitions to be successful. Transitions support your story and message, and without any, there's always a chance that your audience might lose track of what's going on and when. When editing in Enlight Videoleap for iOS, you can easily add cut, dissolve, iris, wipe, slide, and fade transitions to your video clips with just a few taps.

Your iPhone just went missing, and now you're panicking. You need it for work, to get around, to contact your friends and family, and pretty much everything else in your life. So, what are the chances you might get it back? The odds may be stacked against you unless it's just under a couch cushion, but you can improve your chances of recovering your iPhone by taking certain steps.
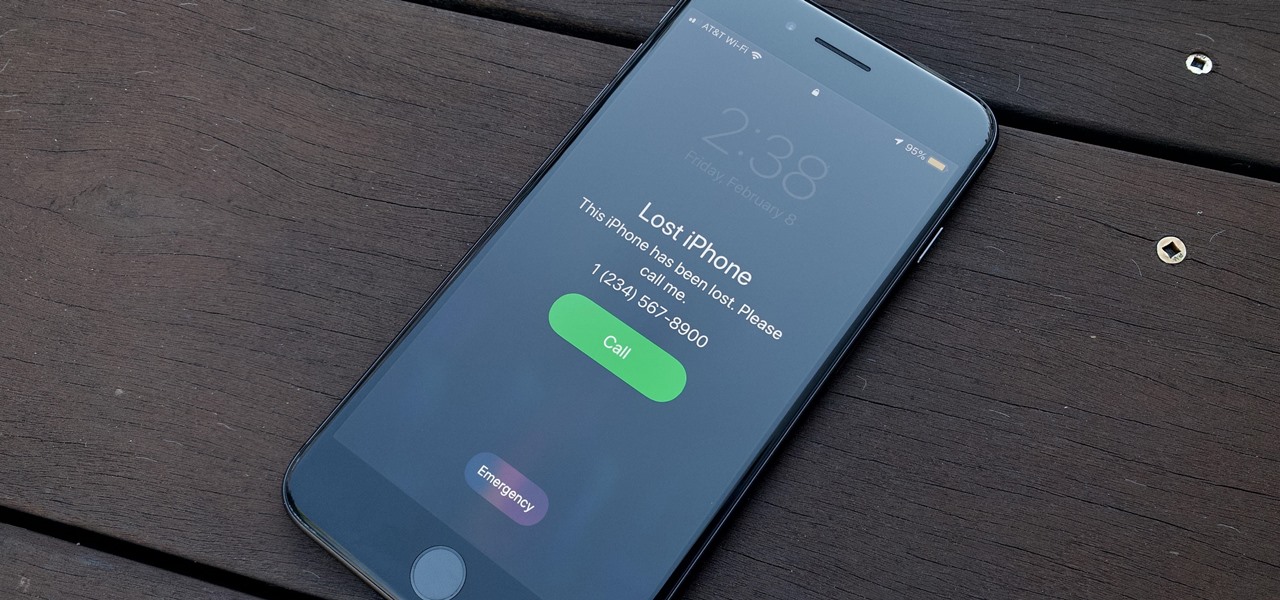
So, you're on the way back from a restaurant and realize you left your iPhone there, but you're late for a meeting and can't go back yet. You may as well kiss that iPhone goodbye, right? Not yet, as long as the right person gets their hands on it first. But that potential do-gooder won't know to contact you, and that's where Find My iPhone's "Lost Mode" comes in handy.

In a surprising twist of expectation management, Magic Leap managed to not only ship but deliver the Magic Leap One I ordered on Wednesday by 4 p.m. PT on the same day.

The Xposed Framework has an official repository for downloading modules which can be easily accessed by searching the Download section in your Xposed Installer app. But not every module is available on the Xposed repo — in fact, many unique and interesting modules are only hosted on third-party servers.

It appears a privacy lawsuit that began five years ago is about to come to an end, and you might get some money out of it.

I've been an Android user almost as long as the operating system has existed, so when I received my first iPhone in April, I felt like I was in a foreign land. Sure, it runs most of the apps I'm used to, and the phone itself feels about the same in my hand as any similarly-sized device, but everything else is just different.

More often than not, when you find an app that offers a particular functionality, there are ten other apps on the Google Play Store that offer virtually the same features. But the reason we choose one app over the alternatives is mainly due to one thing—a preference for the user interface of the app we ultimately install.
Fugu - a simple virus in bash. I once told a friend of mine I'd written a virus in bash and he scoffed - "You can't write a virus in bash!" - he sniggered, like an ignorant idiot.

Welcome Back !! TheGeeks. SQL Injection (SQLI) Part-1


Welcome learners, lets us proceed further with the information we already have. In this post we will explore more about finding hacked accounts online. We will look into how to find juicy info in pastes which are deleted on Pastebin.

This is second post in my series of posts for finding hacked accounts online. Please do read the part 1 of the post at http://null-byte.wonderhowto.com/how-to/find-hacked-accounts-online-part-1-0164611/
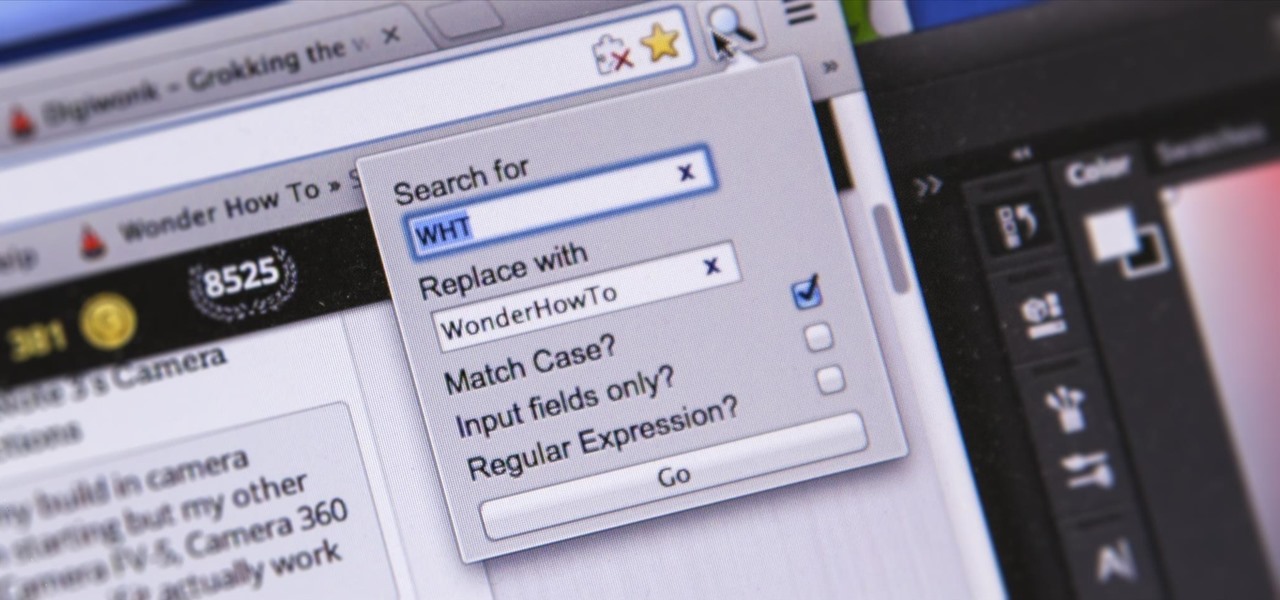
I'm sure you've been there—halfway through typing something out, you realize that one word you've been using more than any other has been misspelled. Perhaps it's a single word, acronym, or line of code that you find yourself typing quite often at work, but this one requires complicated hand gymnastics that you'd simply rather not perform over and over again.
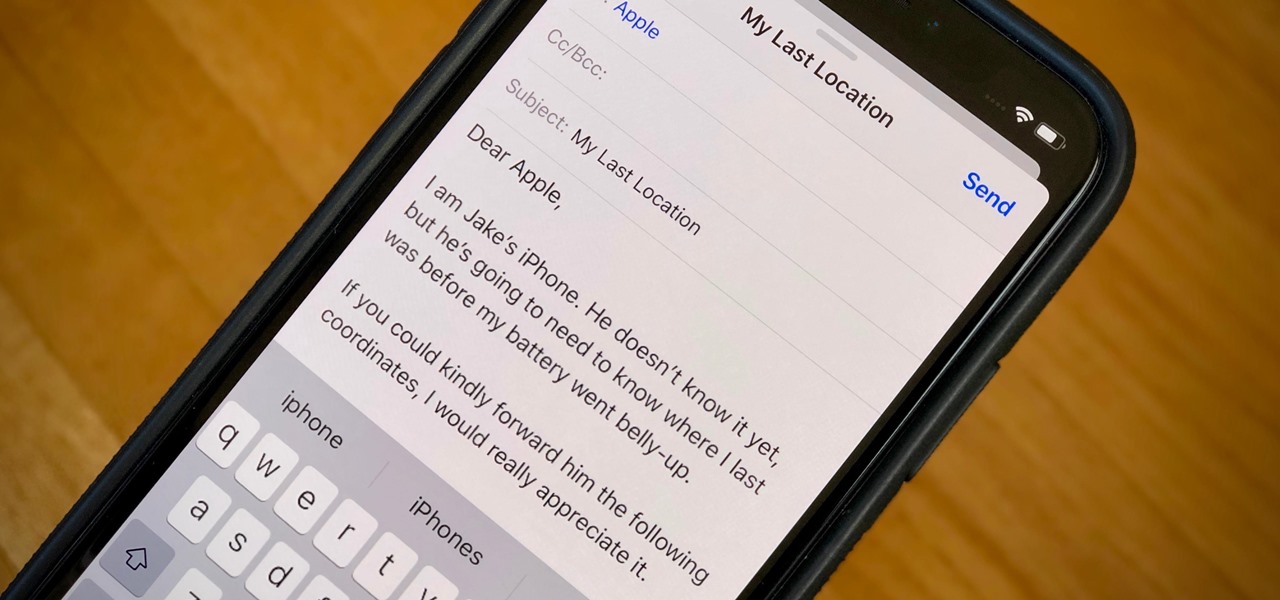
When your iPhone can't be found, Find My iPhone is a true lifesaver. When you use the feature, you can ping your iPhone and even see its current location on a real-time map. But what happens when your iPhone runs out of battery? Find My iPhone can't locate a dead iPhone, can it? You might be surprised to know it can, to a certain degree.

Welcome back, my hacker novitiates! When we are trying to find vulnerabilities in a website to attack, we need a solid web server vulnerability scanner. Internet-facing web apps can open enormous opportunities for us as they are often riven with vulnerabilities and can often offer an entire point to the internal network and resources.

Welcome back, my greenhorn hackers! Sometimes, we don't have a specific target in mind, but rather we are simply looking for vulnerable and easy-to-hack targets anywhere on the planet. Wouldn't be great if we had a search engine like Google that could help us find these targets? Well, we do, and it's called Shodan!

Welcome back, my fledgling hackers! The database is the hacker's "pot-of-gold," as it contains information that is very valuable to both the business and the hacker. In this, the second of my series on hacking databases, we're on the "hunt" for Microsoft's SQL Server. Although far from the most commonly used database (Oracle hold's that title), Microsoft's SQL Server is very often found in small-to-medium sized businesses. Even a few big businesses use it.

Welcome back, my nascent hackers! Earlier, I wrote a guide on finding operating system and application vulnerabilities in Microsoft's own security bulletins/vulnerability database. In this tutorial, I will demonstrate another invaluable resource for finding vulnerabilities and exploits by using the SecurityFocus database.

A car is stolen every 33 seconds in the United States, and from that, the percentage of vehicles recovered in the first day is a whopping 52 percent. Over the next week, that number rises to around 79 percent, but after those initial seven days are up, it's unlikely the vehicle will be found.

Living in Los Angeles has taught me one thing—parking is a luxury. If you are lucky enough to find street parking anywhere near your desired location, do not pass it up thinking you will get an even closer one. It does not exist. Looking for free parking? Get real. You can't even park at a busted meter in Los Angeles, despite state law saying otherwise. Now, finding a good parking spot is not just relevant for Los Angeles, but for other large cities and any other crowded areas, be it a shoppi...

Once you have the skills to bring your ideas to life, the hardest part is coming up with ideas. What do you do when you can't think of something to make? What happens when your well of inspiration runs dry?