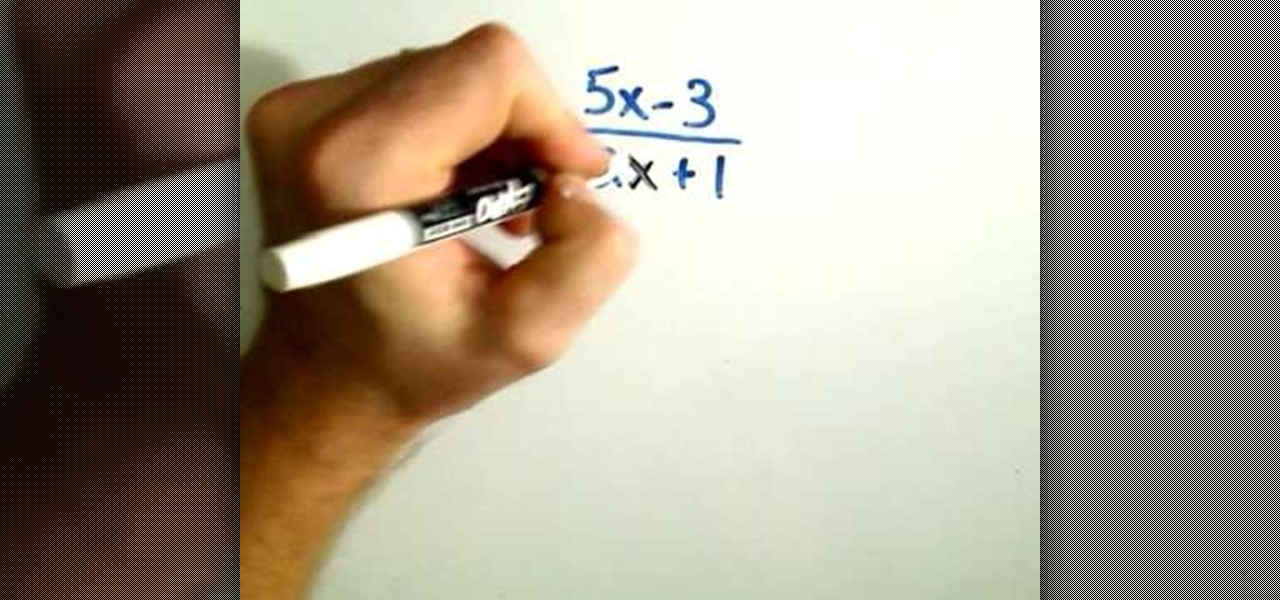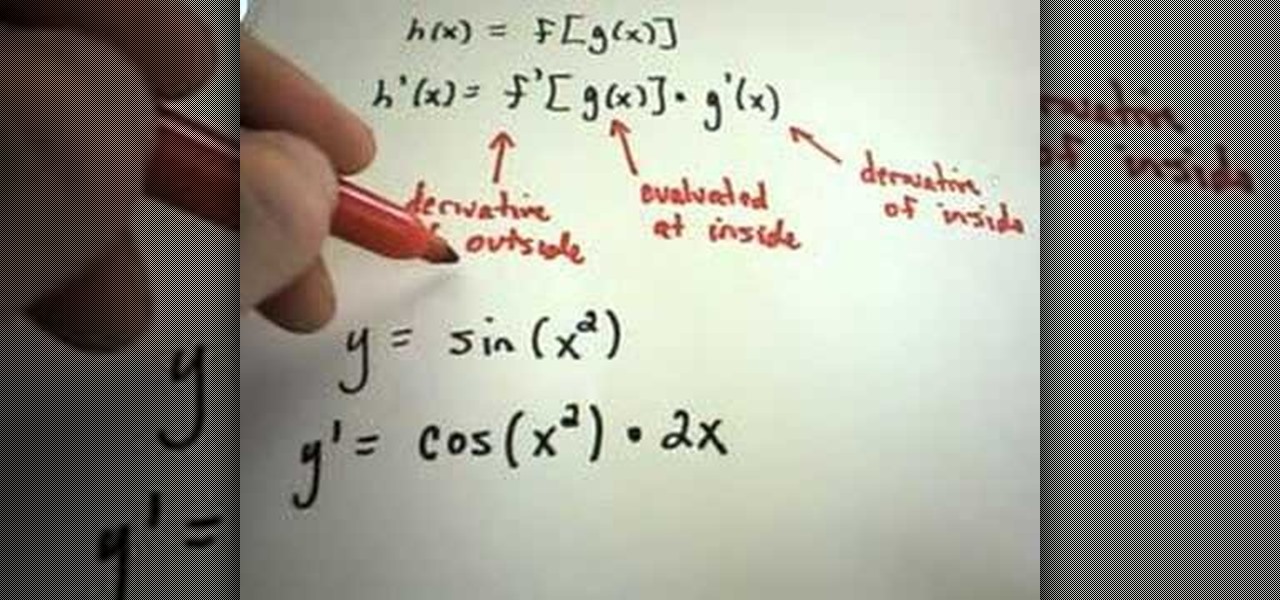Welcome back, my budding hackers! I began this series on Linux basics because several of you have expressed befuddlement at working with BackTrack on Linux. As a hacker, there is no substitute for Linux skills.

More often than not, when you find an app that offers a particular functionality, there are ten other apps on the Google Play Store that offer virtually the same features. But the reason we choose one app over the alternatives is mainly due to one thing—a preference for the user interface of the app we ultimately install.

Welcome back, my fledgling hackers! In this series, I am trying to develop your knowledge of digital forensics, which is valuable whether you're choosing a career in it or just want to know how your hacker activity can be traced. Few professional digital forensic investigators have a hacking background, but the best ones do.
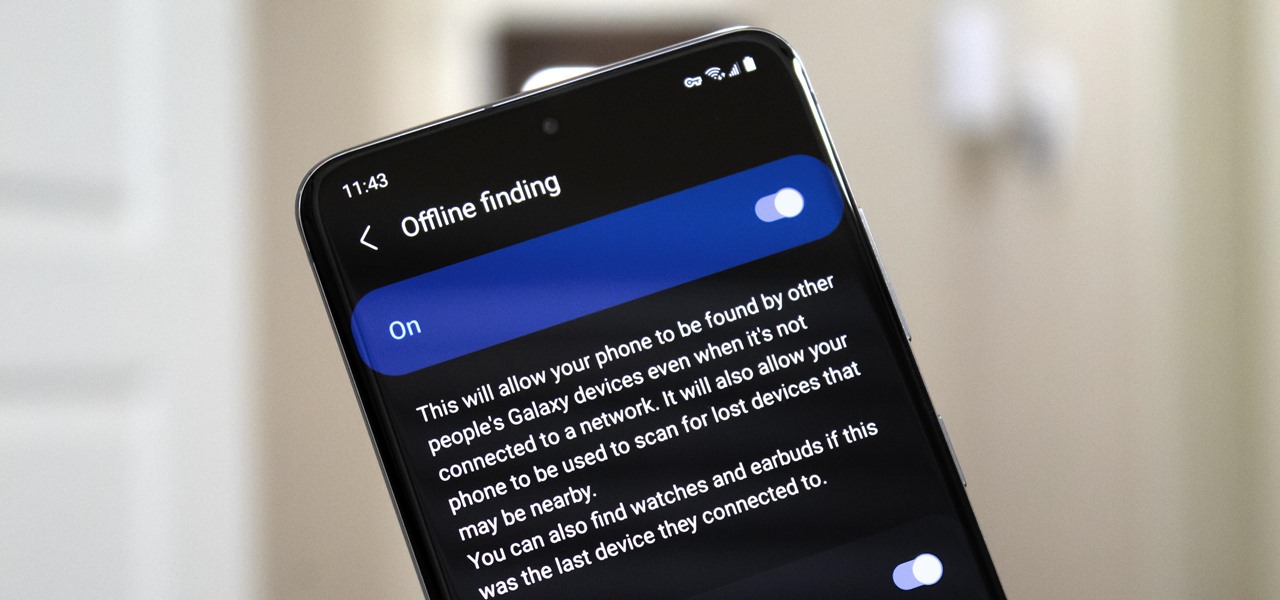
Nowadays, even the dumbest thieves know that the first thing you should do after you steal a phone is turn on airplane mode. Not only does this make it harder for police to track the phone through cell tower triangulation, but it also disables security features the person you stole it from may have implemented — for instance, Samsung's Find My Mobile service.

In a twist in the tumultuous lawsuit between Uber and Waymo, Uber revealed today that they found a document on an employee device, allegedly stolen from Waymo.

This video will talk about how one can make Nemo fish from the movie "Finding Nemo". This video is for all those who are Nemo fans.

Welcome back, my tenderfoot hackers! WordPress-based websites are among the most numerous on this planet (maybe other planets too, but I can't vouch for that). According to WordPress's own website, WordPress powers 23% of the top 10 million websites. That's approximately 2.3 million sites using WordPress!

There's something seriously wrong with Apple's new Shortcuts app, and it's severely limiting the number of shortcuts users can install on their iPhones.

We covered how to upload your library to Google Play Music, but now it's time to delve deeper into the platform. In this article, we'll discuss how to discover new music through a myriad of methods, by using your existing library as a foundation.

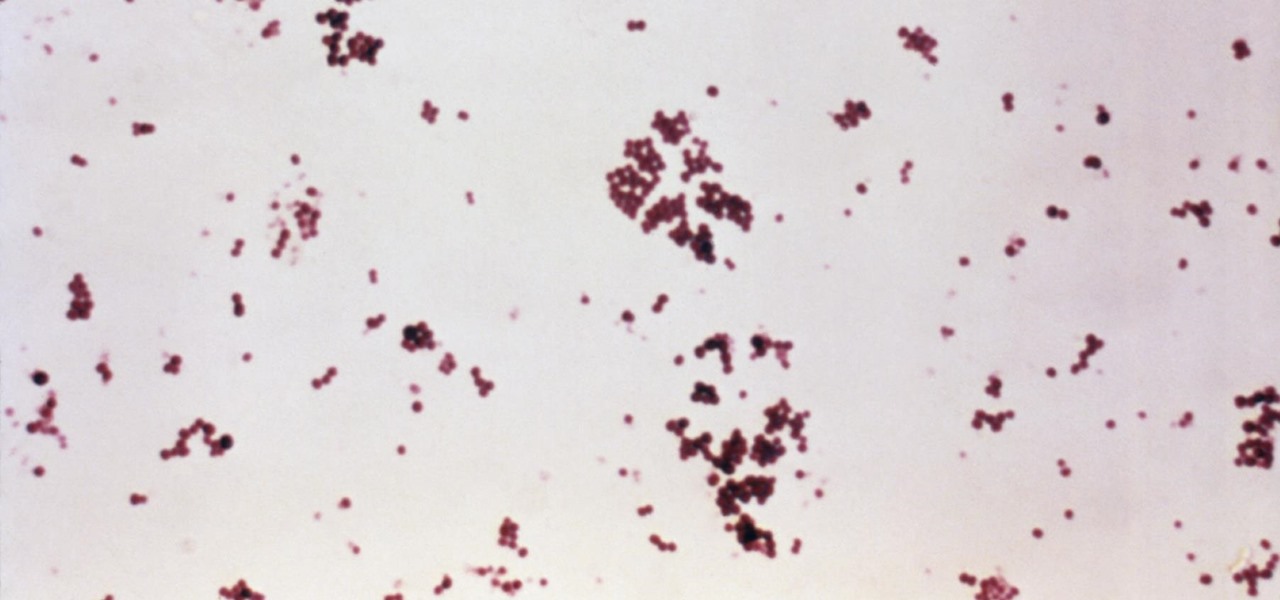
Where in the world did it come from? All of a sudden, one day, someone had an infection with flesh-eating bacteria. It captured headlines and worldwide attention because it was such a severe, strange, uncontrollable, and really disgusting condition.

Welcome back, my greenhorn hackers! Throughout this series on Metasploit, and in most of my hacking tutorials here on Null Byte that use Metasploit (there are many; type "metasploit" into the search bar and you will find dozens), I have focused primarily on just two types of modules: exploits and payloads. Remember, Metasploit has six types of modules:

Welcome back, my nascent hackers! We have spent a lot of time in previous tutorials focused on hacking the ubiquitous Windows systems, but the vast majority of "heavy iron" around the world are Linux or Unix systems. Linux and Unix dominate the world of Internet web servers with over 60% of the market. In addition, Linux and Unix servers are the operating system of choice for major international corporations (including almost all the major banks) throughout the world.

Infections with group A streptococcus, like Streptococcus pyogenes, claim over a half million lives a year globally, with about 163,000 due to invasive strep infections, like flesh-eating necrotizing fasciitis and streptococcal toxic shock syndrome.

If you're looking for an alternative iOS keyboard for your iPhone, look no further than Gboard. The Google-made keyboard is bursting with features like web search, Google Maps, GIFs, and more. Now, Gboard is adding a new feature that'll make it easier to find the perfect emoji.

Sharing your personal information can come up for any number of reasons: you may want to get in touch with a colleague after work or you've been involved in a car accident and need to stay in contact with the other driver. Unfortunately, giving out information can be the key for others to find your social media accounts, such as Instagram, whether you want it to happen or not.

The ride-sharing firm Lyft and Faraday Future, a troubled electric carmaker and potential Tesla competitor, have quietly appointed new top executives, but like the rest of the industry, they struggle to find talent for their driverless programs.

Welcome Back !! TheGeeks. SQL Injection (SQLI) Part-1

You didn't have to attend this year's CES to have gadget envy. There are so many great smartphones, computers, laptops, and other gadgets available in the market that the real challenge becomes choosing the right one to fit your needs and your budget.

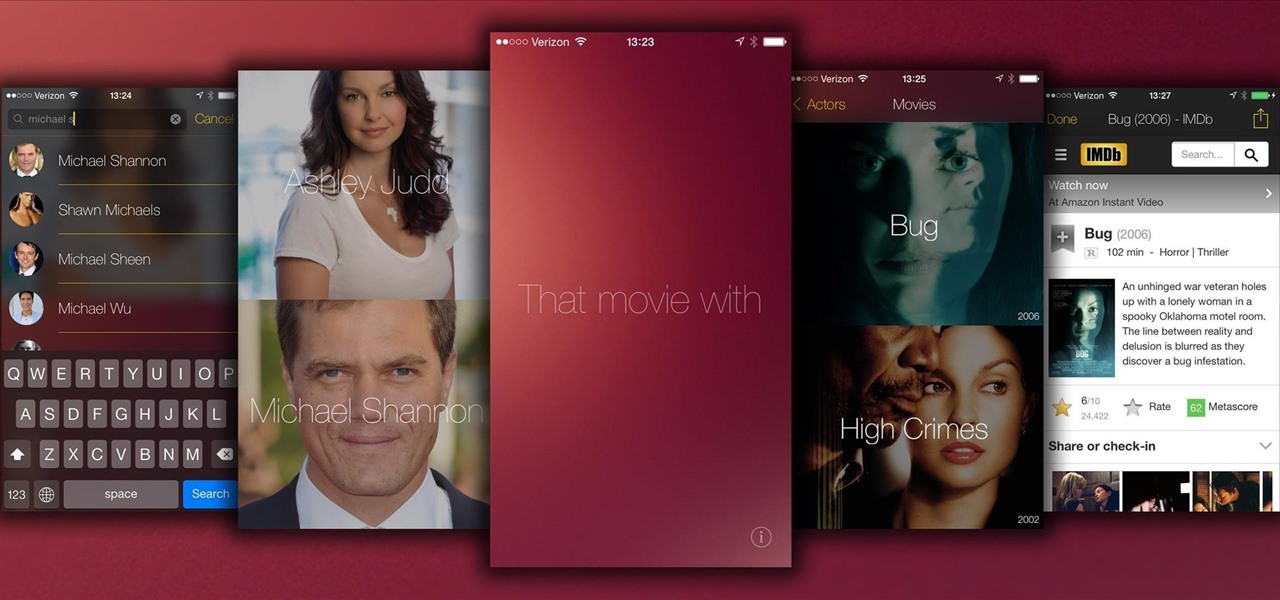
There have been countless times where I'd be racking my brain over the name of a movie I saw, and I don't like giving up. Usually, a few specifics can be remembered, but not enough to come up with a title on my own.

Facial recognition software is being more widely used with every passing day. Your local law enforcement is probably already using it, and it will be even easier for them now that the FBI handed out its own facial recognition software to state authorities. Even the fine folks at Facebook are using this technology. Obviously, this brings up some pretty serious privacy concerns amongst most people, because honestly, who wants to be tracked? Right now, there's not a lot we can do about it being ...

Welcome back, my hacker novitiates! Often, to hack a website, we need to connect to and exploit a particular object within said website. It might be an admin panel or a subdirectory that is vulnerable to attack. The key, of course, is to find these objects, as they may be hidden.

Every year, Black Friday gets a little more insane. People get up at ungodly hours, wait in lines forever, and get into some of the most ridiculous fights you've ever seen. All in the name of saving some cash. Everyone loves saving money, but without a game plan, you could end up missing all the good deals and going home with nothing. Luckily, the Internet is here to take some of the stress out of holiday shopping. With these sites and apps, you can find out about all the best deals before yo...

Hundreds of Windows 10, macOS, and Linux vulnerabilities are disclosed every single week, many of which elude mainstream attention. Most users aren't even aware that newly found exploits and vulnerabilities exist, nor that CVEs can be located by anyone in just a few clicks from a selection of websites online.

Welcome back, my tenderfoot hackers! A short while ago, I started a new series called "How to Spy on Anyone." The idea behind this series is that computer hacking is increasingly being used in espionage and cyber warfare, as well as by private detectives and law enforcement to solve cases. I am trying to demonstrate, in this series, ways that hacking is being used in these professions. For those of you who are training for those careers, I dedicate this series.

If you struggle with deciding which wine you should buy for an intimate dinner, or the type of beer with the highest alcohol content that doesn't taste like tree bark, then check out some of these great alcohol-friendly apps to make better booze decisions.

Creative Commons is awesome—really. If an image, video, or audio file is tagged with a CC license, that means you can use it as long as you give appropriate credit to the owner. For bloggers with no money for pricey stock media, it's a godsend. When you license your own media under CC, you can choose how you want it to be used by others and whether or not it can be used commercially.

When you need to drive somewhere unfamiliar, you probably use Apple Maps to get there if you're an iPhone user. But just getting there isn't enough sometimes. If you pull up to the location, and there's nowhere to park, it doesn't matter that you arrived on time since you'll be late trying to find somewhere to leave your car. That's where Apple's new Maps tool comes in handy.

Imagine a scenario where you're nowhere near your iPhone, but it's on loud, and you really need to silence it. An alarm may be blaring, notifications could be spitting out sounds left and right, and calls may be ringing. Things can get annoying real quick for whoever's around it. Plus, all that attention makes it easy for someone to find and possibly steal your iPhone. Luckily, you can quiet it down.

It's important to know who you're dealing with after hacking your target's MacBook. Getting remote access is simple, but covertly gathering information about the user and their system can be a challenge.

In this two part segment, all of the eBook collectibles locations in Deus Ex: Human Revolution are revealed. Reading all 29 of the books in a single play through of the game allows you to unlock the 'Doctorate' achievement on the Xbox 360--so find those books and get to reading!

Need some help figuring out how to find the inverse of an algebraic function? Learn how with this free video algebra lesson. From Ramanujan to calculus co-creator Gottfried Leibniz, many of the world's best and brightest mathematical minds have belonged to autodidacts. And, thanks to the Internet, it's easier than ever to follow in their footsteps (or just finish your homework or study for that next big test).

In this video the tutor shows how to find the mirror point using a quadratic equation. He says that to graph a parabola you need to find the mirror point symmetrical to the Y-intercept. Now he explains how to find a mirror point using an example with sample values. He begins with saying that the Y-coordinate of the mirror point is same as the Y-coordinate of the Y-intercept. Now you have to find the x coordinate of the mirror point which he shows that it is double the x-coordinate of the vert...

When you're downloading a torrent the speeds that you see are determined by the trackers you're using. In this clip, you'll see how to speed up torrent downloads by finding additional trackers for your torrents. It's easy! So easy, that this video tutorial can present a complete, step-by-step overview of the process in about two and a half minutes. For more information, including detailed, step-by-step instructions, watch this video guide.

This video shows the method to graph a linear function by finding the X and Y intercept. Only two points are needed to graph linear functions. So we find the point on Y axis or the Y intercept and the point on the X axis or the X intercept. We notice that on the Y axis the X coordinate is zero. So, we find the Y intercept by putting x=0 in the given equation and solving for y. In the same way, we find the X intercept by putting y=0 in the given equation and solve for x. We join the two points...

JustMathTutoring This video shows the procedure of finding derivatives using the Chain Rule. The Chain Rule states that the derivative of a composition of functions is the derivative of the outside function evaluated at the inside multiplied by the derivative of the inside. This can be stated as if h(x) = f[g(x)] then h'(x)=f'[g(x)]g'(x). This is explained by two examples. In the first example we find the derivative of the sine of square of 'x'. We take the derivative of sine at square of 'x'...

Gemstone earrings are quick to make at home, not to mention cheaper and more customized. To make gemstone post earrings with snap fit findings, you'll need snap fit post findings, ear clutches, gemstones to match the finding, and bent chain nose pliers will help. Learn how to make gemstone post earrings with snap fit findings by watching this video jewelry-making tutorial.

This video shows students how to add fractions with different denominators. To add different fractions you must be able to find the least common denominator.

The aim of the video is to show how to reduce a fraction by factoring out prime numbers that are common to both the numerator and the denominator. The example shown in the video is 27/21. The number 27 can be achieved by multiplying 3 by 9 and the number 21 is the result of 3 multiplied by 7. The common factor, therefore in both the numerator and the denominator is 3. 3 on the top divided by 3 on the bottom is 1 and so this can be removed without affecting the value of the fraction, leaving 9...

In this economy almost no one world-wide is working up to their potential. If you're in the position of having to apply for a job you're overqualified for and don't want to be rejected because you're too good, watch this video for tips on hiding overqualification and getting the job you need until you can have the one you want.

Hello again my fellow hackers. I've come to give you some hope for hacking. As we know there are a lot of exploits out in the world and there are websites you can find them on.