
News: Apple Planning In-Person AR Wearable Device Launch In Coming Months, Report Says
The Apple rumor drumbeat is getting louder: a wearable augmented reality device is almost certainly coming, very soon.


The Apple rumor drumbeat is getting louder: a wearable augmented reality device is almost certainly coming, very soon.

The Lens Studio creators have published more than 1.5 million AR effects to Snapchat. One of them is Audrey Spencer, who shared her story with us and provided her insights into Lens Studio as a storytelling device. Meanwhile, Snap has added new capabilities to the platform to stoke more creativity from its creators.

Ever since China's Nreal unveiled its Light smartglasses at CES two years ago, an army of look-alikes have emerged from the Asian nation.

The past year has revealed a gaping hole of opportunity in the world of business called virtual meetings. Some existing players like Zoom hopped on that opportunity, while others like Skype seemed stuck on the sidelines, and Google Meet just managed to catch up in time to snag some of the shift in remote work.

It can feel hard to find time for just about anything these days. But if you really sit down and think about it, you likely have a little more free time in your day than you might actually imagine. The average person has about 4.5 hours of total leisure time over the course of a week.
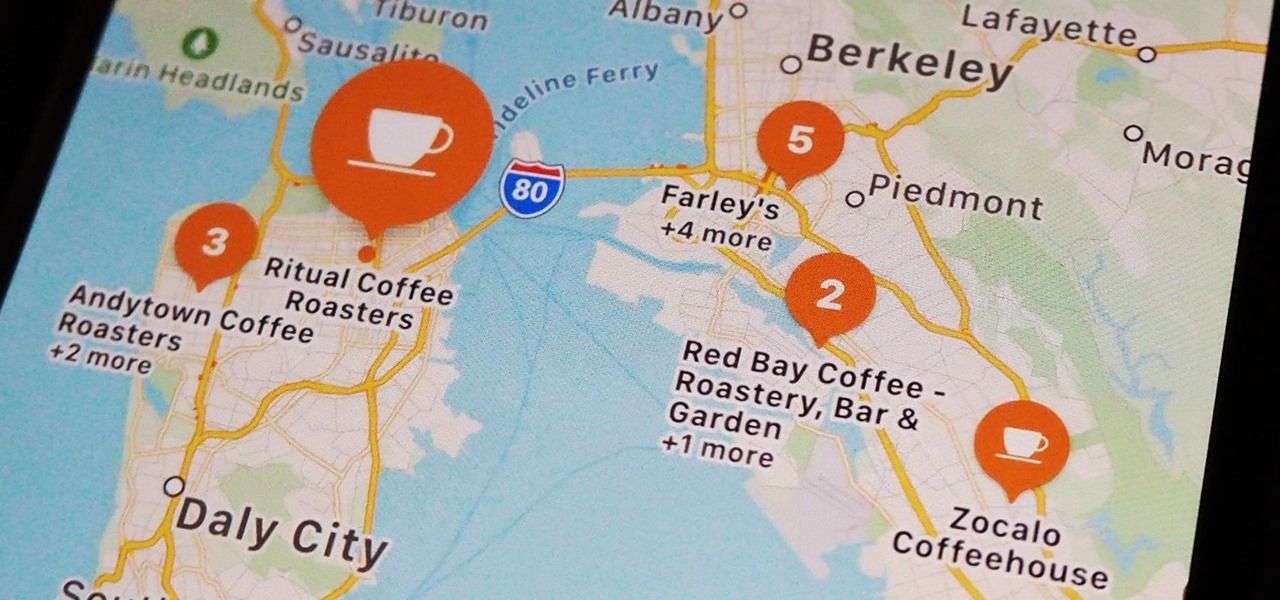
When you're in a new city or even your own neighborhood, you might not know where the best places to visit are. The number of parks, restaurants, shopping centers, and other attractions could be overwhelming, so how do you narrow down your choices? The new iOS 14 update has introduced curated city "Guides" in Apple Maps, created by trusted brands to help you find excellent places to explore.

Working from home is going to be a reality for more people than ever. With Twitter CEO Jack Dorsey announcing that his employees will be working remotely for an extended period of time (and even permanently, in some cases), the workforce is rapidly changing. More companies are certain to follow suit.
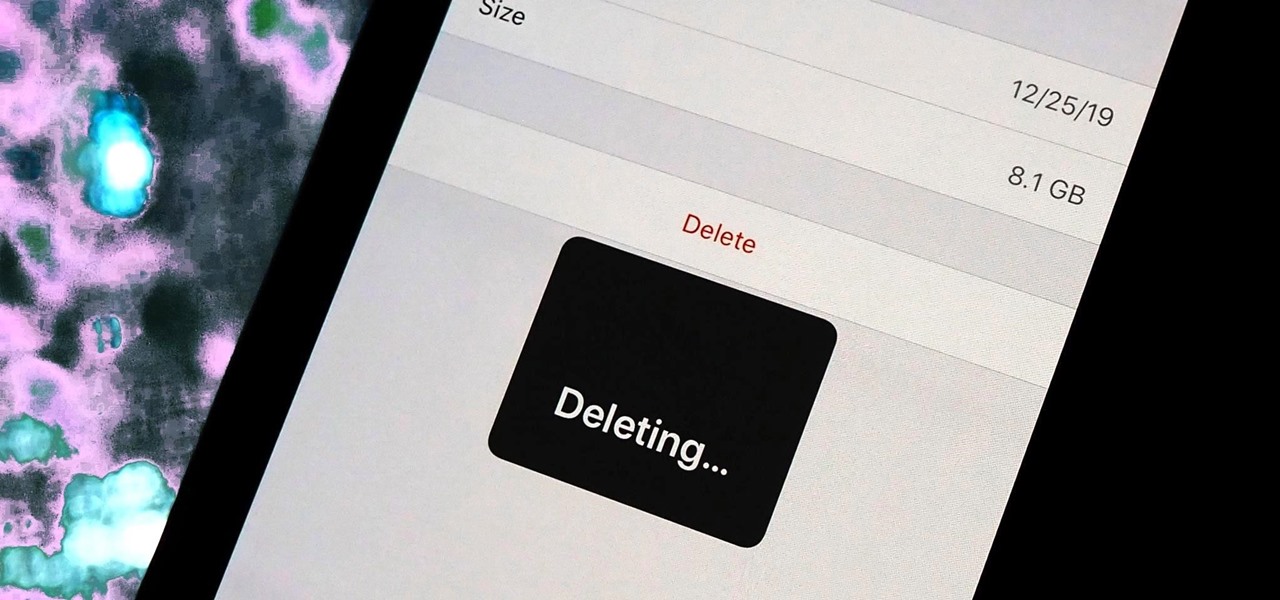
If you use iCloud, you may have experienced alerts such as "Not Enough Storage" and "iCloud Storage Full," especially if you're on the free 5 GB plan. To clear up space on your iCloud account fast, you can delete large files here and there, but trashing one thing, in particular, can clear up gigabytes worth of space instantly.

From booting into Fastboot mode with a single command to installing mods without root access, there's no shortage of reasons to use ADB. The catch, though, you had to be tied to a computer with a USB connection. However, a new feature in Android 11 finally allows you to run ADB commands over Wi-Fi instead of being tethered.

In previous Android versions, you lost about an inch of screen real estate to the status bar and navigation bar. But if you enable Android 10's new navigation gestures on your Samsung Galaxy, you can regain the bottom part — and with the help of ADB, you can reclaim the top portion as well.

If you haven't used a Samsung device in a few years, the Galaxy S20 series will be your first taste of One UI 2, the skin running on top of Android 10. Although One UI is on the heavier side, it has loads of exciting features that go beyond what's offered in stock Android.

With the Galaxy S20, Samsung has officially removed the Bixby button from its flagships. While it was a controversial key, in its later days, it did give us the ability to launch an app or custom action at the press of a button. There's still a way to do something like that, but now, you'll have to use the power button instead.

Amid the coronavirus chaos, two companies at the forefront of augmented reality technology took starkly different approaches to their upcoming developers conferences, as Facebook has canceled its annual F8 conference and Magic Leap plans to invite a limited number of attendees to its Florida headquarters for LEAP Developer Days.

We may or may not see Apple's long-awaited take on AR smartglasses this year, but the company is more than getting its practice swings in with its current wearables business, which hit record revenue in 2019 according to financial results released this week.

Nearly every connection to the internet is dependent on the Domain Name System. DNS, as it's more commonly called, translates domain names like gadgethacks.com into IP addresses, which is what network devices use to route data. The problem with DNS servers is that they don't have your privacy in mind.
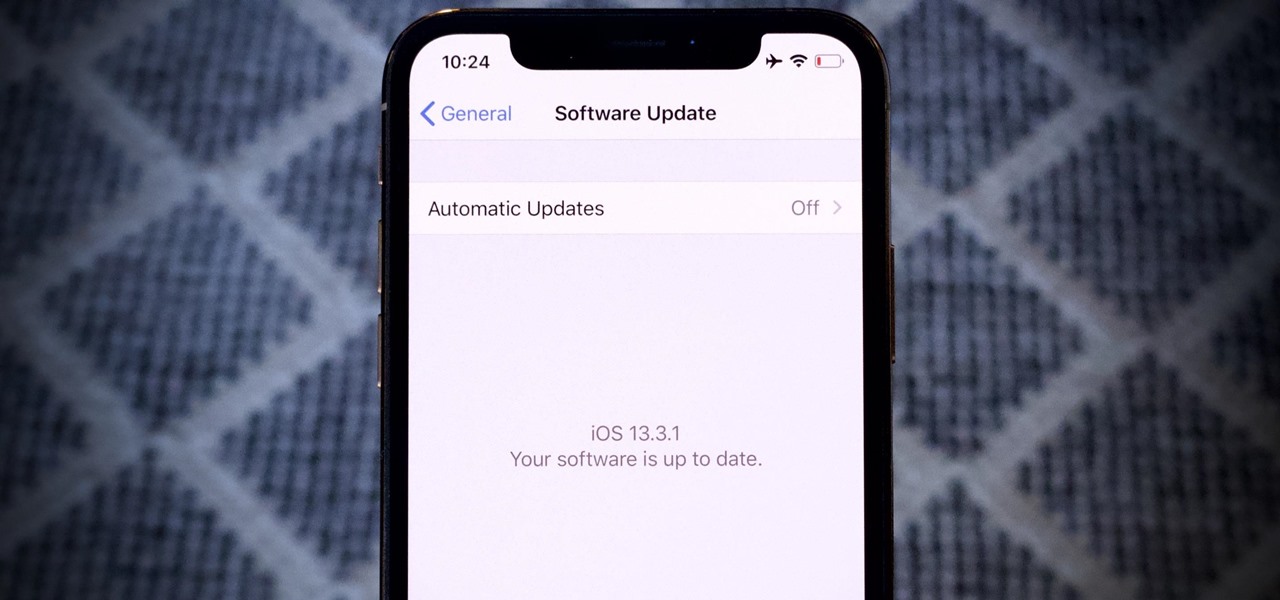
Beta testing on iOS is as Wild West as Apple gets. From feature-filled to featureless releases, there's a high level of unpredictability for what to expect. And not everything is found right away. For instance, last week's developer beta 2 added a new feature that was left undiscovered until three days later. So what has Apple hidden in today's iOS 13.3.1 dev beta 3 update?

While the big names in augmented reality demonstrated the breadth of opportunities in the industry's landscape this week, one new startup showed off what is possible further in the future.

After more than two years of teasing, augmented reality startup Mojo Vision has confirmed that "invisible computing" means what we've suspected all along.

While consumer-grade smartglasses are the holy grail for tech companies, smartglasses maker Vuzix knows where its bread is buttered, and that's in the enterprise segment.

One Instagram creator's augmented reality homage to Disney's deep bench of animated characters has earned him fifteen minutes of fame.
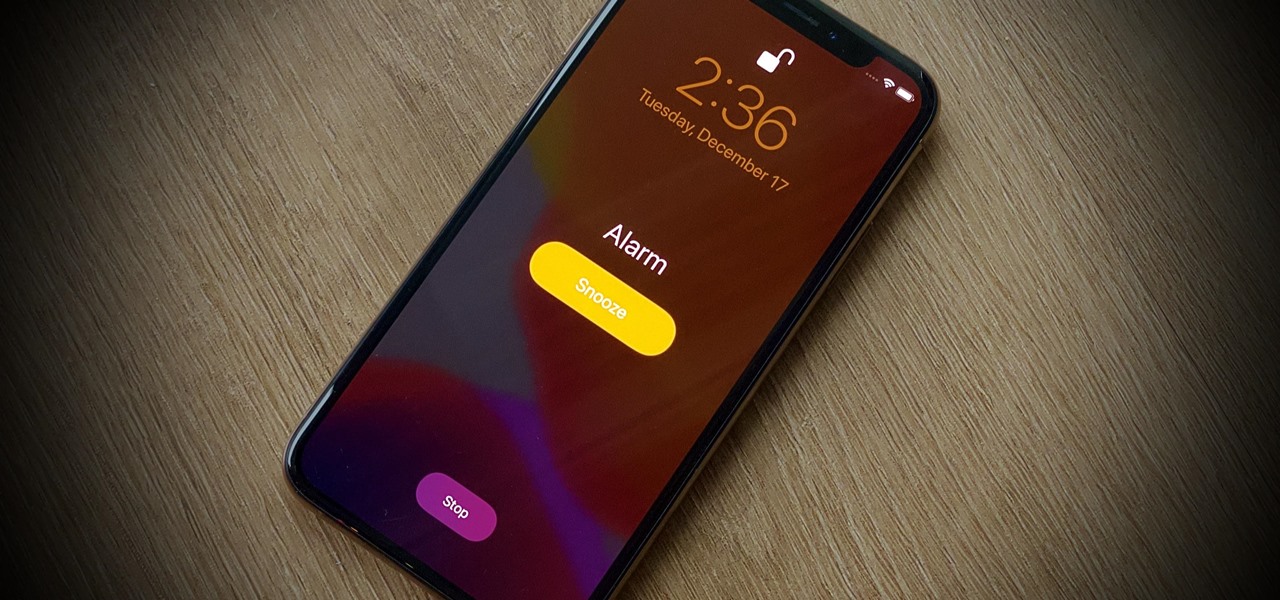
It happens to almost everyone. You wake up one morning, check your phone, and realize your alarm never went off. Now you're late to start the day, and you spend every night onward paranoid it'll happen again. But if you have an iPhone, there are two things you can check to make sure the alarm always goes off on schedule.
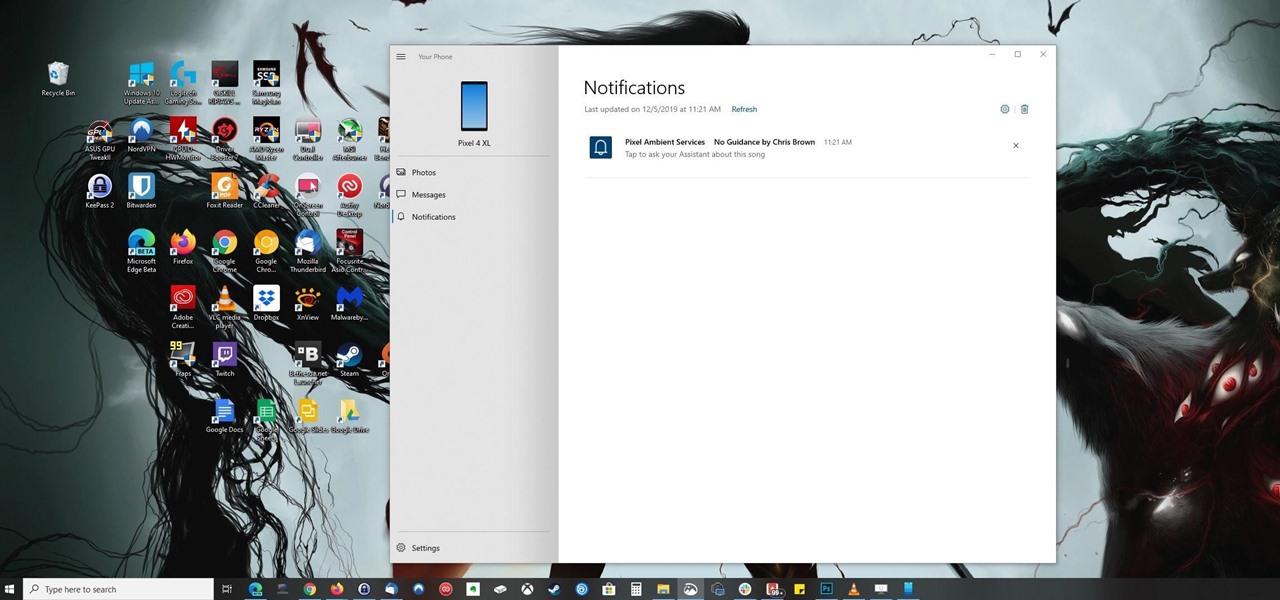
One of the biggest reasons to go with an iPhone over an Android device is Apple's interconnectivity. iPhones, iPads, and macOS devices are all connected in a way that allows seamless transition between devices. Android lacks such a feature by default, but that isn't the end of the story.

Sniffing packets over a network is an easy way for hackers to gather information on a target without needing to do much work. But doing so can be risky if sniffing packets on an untrusted network because a payload within the packets being captured could be executed on your system. To prevent that, Sniffglue sandboxes packet sniffing to provide an extra layer of security.

As the demand for realistic volumetric video for AR experiences begins to grow (along with the available facilities and services for capturing it), researchers at Google have figured out how to improve upon the format.

The week in AR business news started out with a bang with two bombshell reports that cast a shadow on the AR industry as a whole.

Is the augmented reality magic fading down in Plantation, Florida? That's the first question some may be asking following a casual revelation over the weekend that Magic Leap, the maker of the Magic Leap One, has assigned much of its patent portfolio over to JP Morgan Chase as collateral.

Magic Leap's legal battle against Nreal has taken an intriguing turn this week, as Magic Leap set a date to discuss the matter with Nreal. But a new partnership struck by Nreal adds another wrinkle to the duel between the two AR wearable makers.

All those Apple commercials encouraging people to use their iPhones to make their smartphone movies look amazing, but how can you achieve some of the same looks? That's the question many often ask after plunking down over $1,000 for a brand new iPhone, shooting some video, and getting somewhat mediocre results.

With the imminent arrival of the HoloLens 2 expected any day now, Microsoft is preparing new users to take advantage of its software from day one.

I already know what you're thinking: this guide is blasphemy. I am showing you how to turn a Galaxy Note 10 or 10+ into an iPhone 11 Pro Max. And while I'd usually agree with you, hear me out. How can you know you don't like something until you try it? So here is your way of trying out an iPhone using your Galaxy Note 10.

As excitement looms for Apple's annual parade of pomp and circumstance for its latest lineup of iPhones, some hidden hints in an internal build of iOS 13 has Apple enthusiasts salivating for what Cupertino is testing in the AR wearables realm.

Developers and enterprise customers chomping at the bit to get their hands on HoloLens 2 may not have to wait much longer, as Microsoft passed one of the remaining hurdles needed to release their new tech into the wild.

Augmented reality gaming startup Tilt Five is ready to reinvent old school Dungeons & Dragons-style games for the modern age with its augmented reality headset and tabletop game system.

Sports technology company Form is testing the waters for augmented reality wearables with a product aimed at a very specific user group.

The future of smartglasses for consumers seems ever dependent on Apple's entry into the market. Coincidentally, the exit of Apple's long-time design chief Jony Ive has shed some light on that eventual entrance.

While modern browsers are robust and provide a lot of functionality, they can be unlocked to do some pretty spectacular things with browser extensions. For hackers and OSINT researchers, these tools can be used to defeat online tracking, log in to SSH devices, and search the internet for clues during an investigation. These are a list of my top ten favorite browser extensions for hackers — and how to use them.

The photos and videos you take with your iPhone contain bits of information, known as metadata, including the location where they were taken. This metadata makes it easier for Photos to organize your media, but put these photos and videos in the wrong hands and anyone can find out where you live or work. Luckily, iOS 13 makes it easy to wipe the geotag from images and videos before sharing.

In this era of smartphones, we all know very well how easily we can get addicted to our devices. Spending hours each day doing the endless scroll through Facebook and other social media sites just because we feel like we'll miss something if we don't. Both Google and Apple are aware of this and are trying to help control smartphone addition in their own way for Android and iOS.

Metadata contained in images and other files can give away a lot more information than the average user might think. By tricking a target into sending a photo containing GPS coordinates and additional information, a hacker can learn where a mark lives or works simply by extracting the Exif data hidden inside the image file.

During the recent Augmented World Expo (AWE), we had a chance to try out the Lenovo ThinkReality A6 AR headset. Unfortunately, the experience was all downhill from there.