Web application firewalls are one of the strongest defenses a web app has, but they can be vulnerable if the firewall version used is known to an attacker. Understanding which firewall a target is using can be the first step to a hacker discovering how to get past it — and what defenses are in place on a target. And the tools Wafw00f and Nmap make fingerprinting firewalls easy.

Firewall solutions for macOS aren't impervious to attacks. By taking advantage of web browser dependencies already whitelisted by the firewall, an attacker can exfiltrate data or remotely control a MacBook, iMac, Mac mini, or another computer running macOS (previously known as Mac OS X).
Firewall is necessary to protect a computer network from hostile intrusions. You can easily setup your Firewall setting. This video helps you to do it.

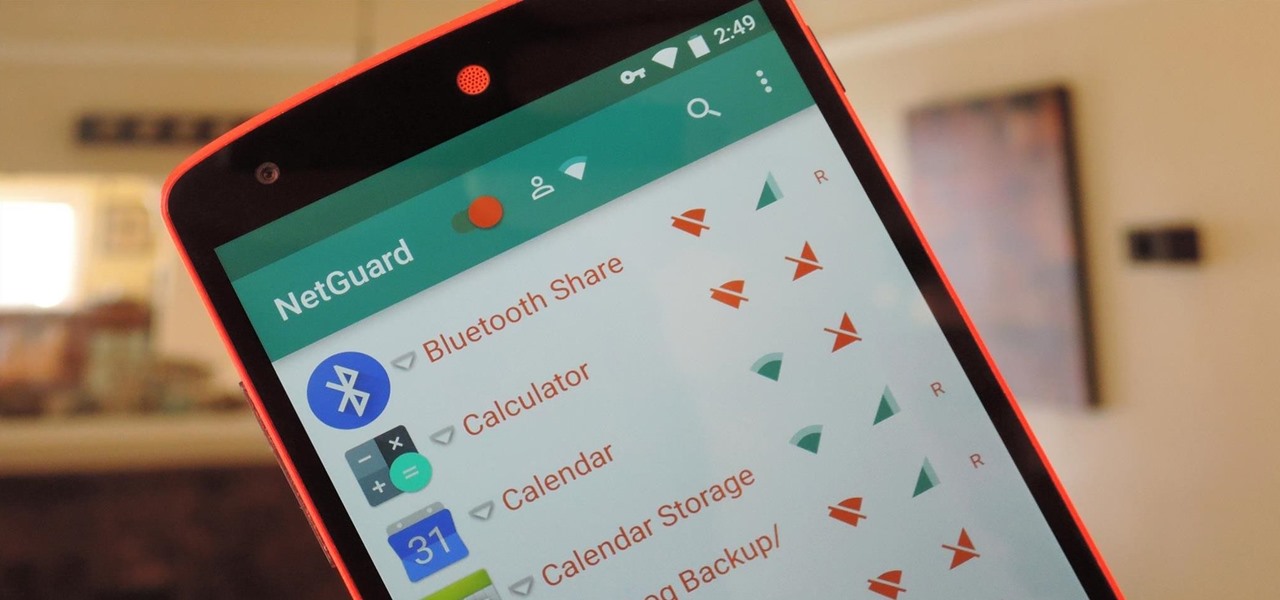
Apps that have no business accessing the internet can share your location, device ID, and other personal information with potentially malicious data snatchers. If you're connected to the internet on your Nexus 7 tablet, you're a potential target for cyber threats.

Identifying security software installed on a MacBook or other Apple computer is important to hackers and penetration testers needing to compromise a device on the network. With man-in-the-middle attacks, packets leaving the Mac will tell us a lot about what kind of antivirus and firewall software is installed.

Local port forwarding is good when you want to use SSH to pivot into a non-routable network. But if you want to access services on a network when you can't configure port-forwarding on a router and don't have VPN access to the network, remote port forwarding is the way to go.

If you exceed your monthly mobile data limit, your cell phone bill can skyrocket pretty quickly. This is why a lot of people vigilantly monitor internet usage and even uninstall apps that use too much background data.

Data can be injected into images quickly without the use of metadata tools. Attackers may use this knowledge to exfiltrate sensitive information from a MacBook by sending the pictures to ordinary file-sharing websites.

Microsoft.com is one of the most extensive domains on the internet with thousands of registered subdomains. Windows 10 will ping these subdomains hundreds of times an hour, making it challenging to firewall and monitor all of the requests made by the operating system. An attacker can use these subdomains to serve payloads to evade network firewalls.

Systm is the Do-It-Yourself show designed for the common geek who wants to quickly and easily learn how to dive into the latest and hottest tech projects. They will help you avoid pitfalls and get your project up and running fast. In this DIY episode, see how to build a firewall from a junk PC to protect networks.

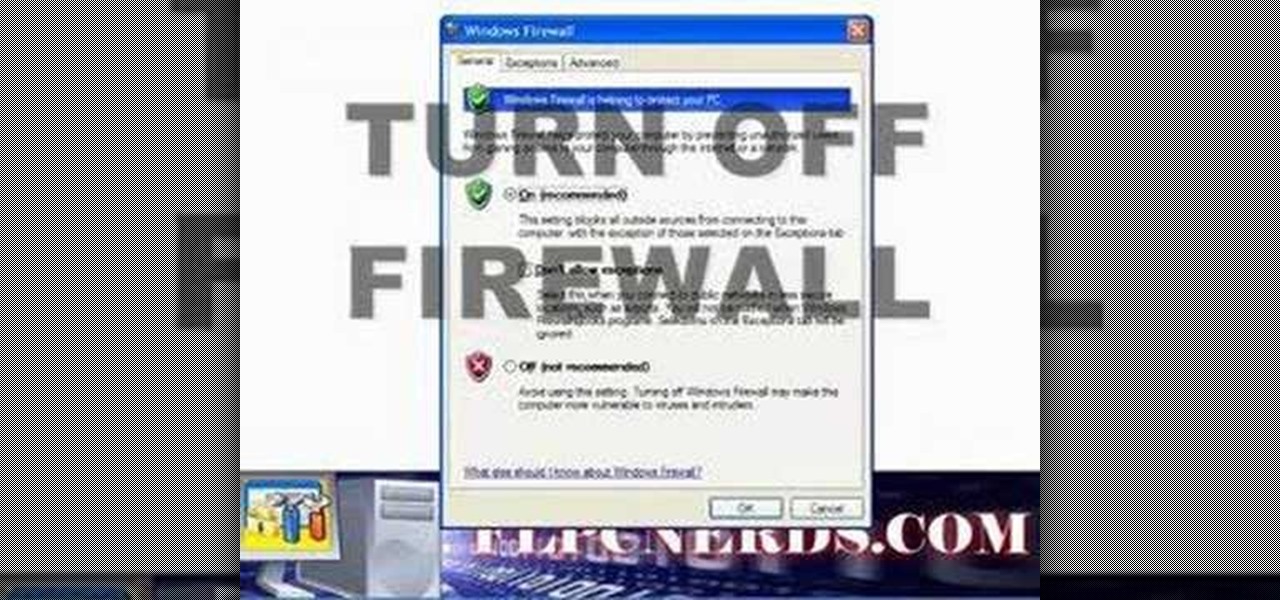
In this how to video, you will learn how to turn off the Windows firewall in Windows XP. This is useful if you would rather use a third party firewall to protect your computer instead. First, go to start menu and click run. Type in firewall.cpl and press okay. The firewall will now open. You will see that the firewall is on. To turn it off, select off. It will say it is not recommended, but if you must turn it off, this is the easiest way to do it. Click okay to complete the process. Your Win...

Hak5 is at it again, with a plethora of somewhat accessible solutions to your technological problems. If you've ever needed to get through your school's firewall, or secure traffic tunneling, or try out applications in a fast, efficient manner? This video has it all and more.

In this video, it demonstrate how to check and configure Windows firewall. In order to check to see if firewall is enable or not. You would click on start which locate bottom left corner of the screen. Then you would click on control panel. On this screen you would see an option for firewall, and click on it. When you click on firewall, it will let you view all the description about firewall configuration. There are also many other option which locate on the left hand side. If you are an adva...

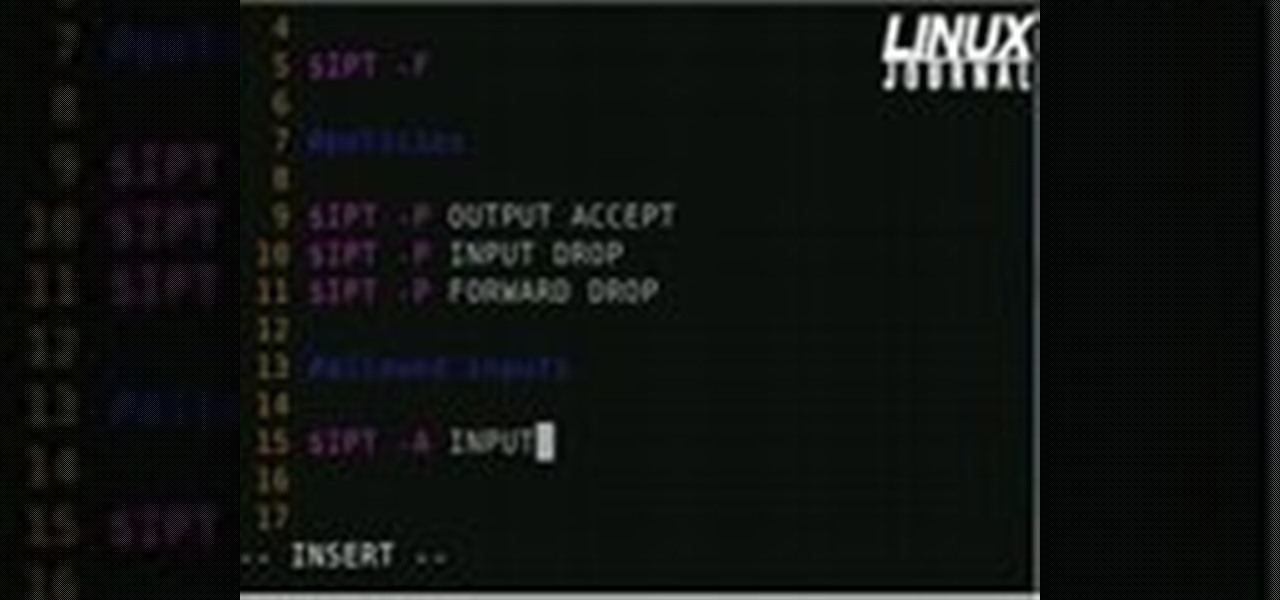
Linux comes with a powerful built-in firewall, although the interface can be a little intimidating. With this multipart GNU/Linux networking video tutorial, you'll master basic and not-so-basic IPTables functionality and create the perfect firewall for your home network. For detailed, step-by-step instructions, watch this Linux how-to.

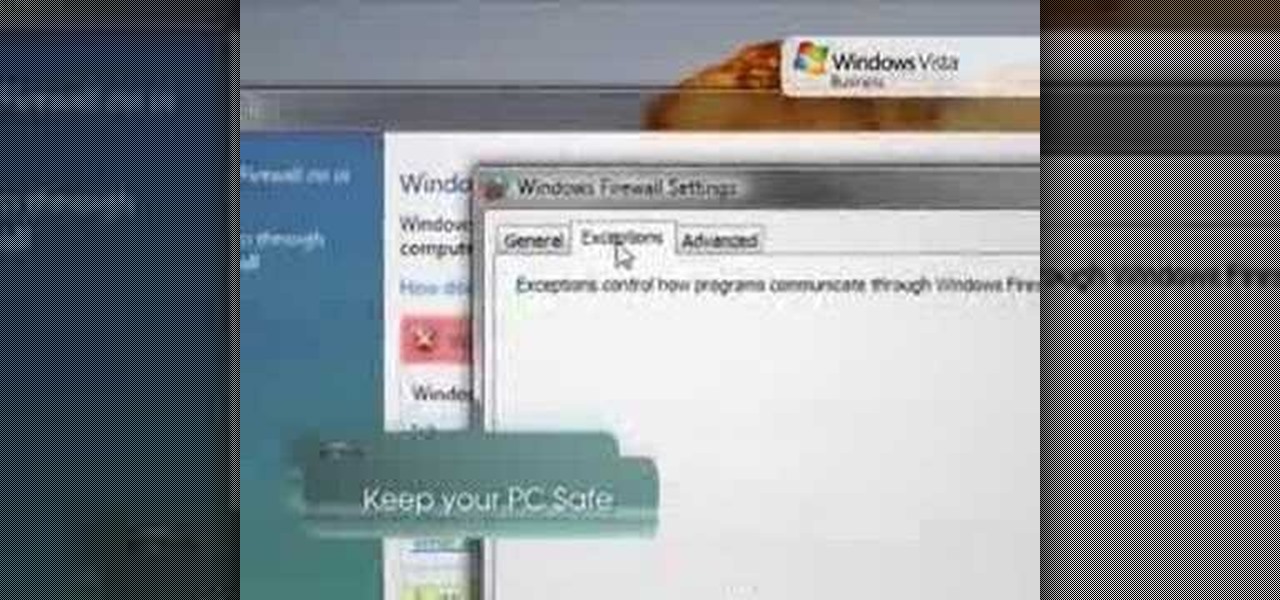
In order to keep your PC safe from annoying or potentially dangerous threats on the Internet, a properly-configured firewall is a crucial item in helping prevent your system from becoming compromised. The Windows Firewall in Windows Vista™ is the first line of defense in helping to keep your computer safe. By preventing your computer from being infected by malware, Windows Firewall is designed to be easy to use and is automatically enabled to protect your computer as soon as Windows starts. T...

Dave Andrews from HelpVids is going to teach you in this video how to configure the Windows XP firewall. To do that, you need to follow these steps: 1. Go to Control Panel and make sure that you are in the classic view.

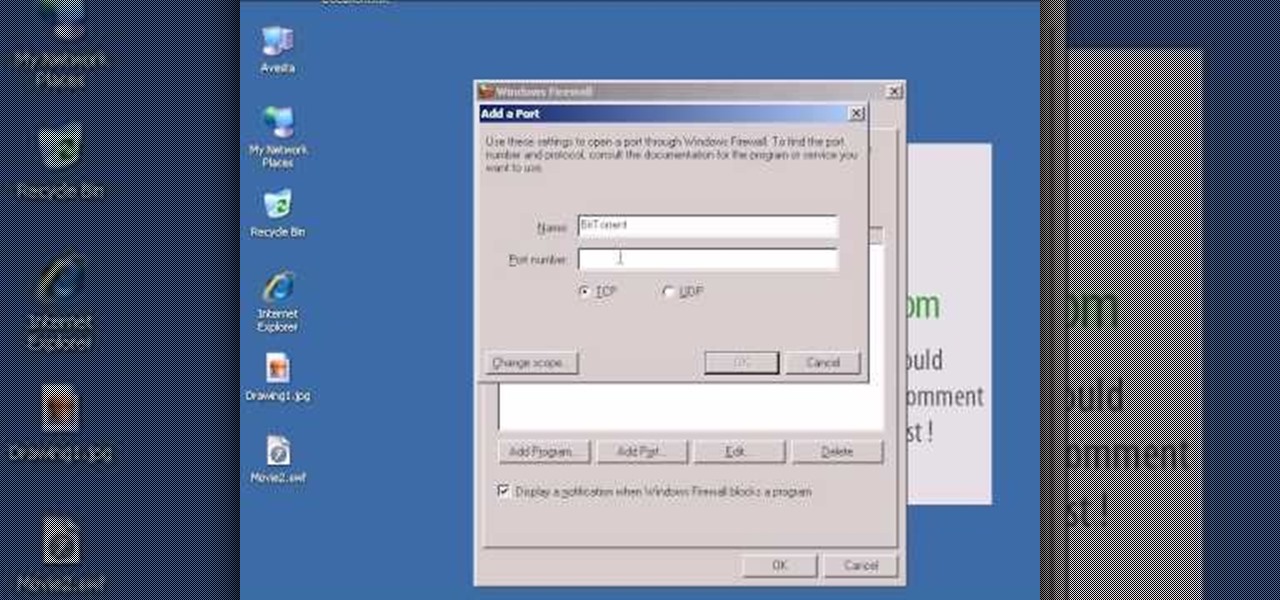
In this video tutorial, viewers learn how to open ports in Windows firewall. Begin by clicking on the Start menu, go to Control Panel and select Windows Firewall. In the Windows Firewall window, click on the Exceptions tab. Here, users are able to add, edit or delete exceptional ports. To add ports, click on Add Ports. Now name the port, input the port number, select the port type and then click on OK when finished. This video will benefit those viewers who use a Windows computer, and would l...

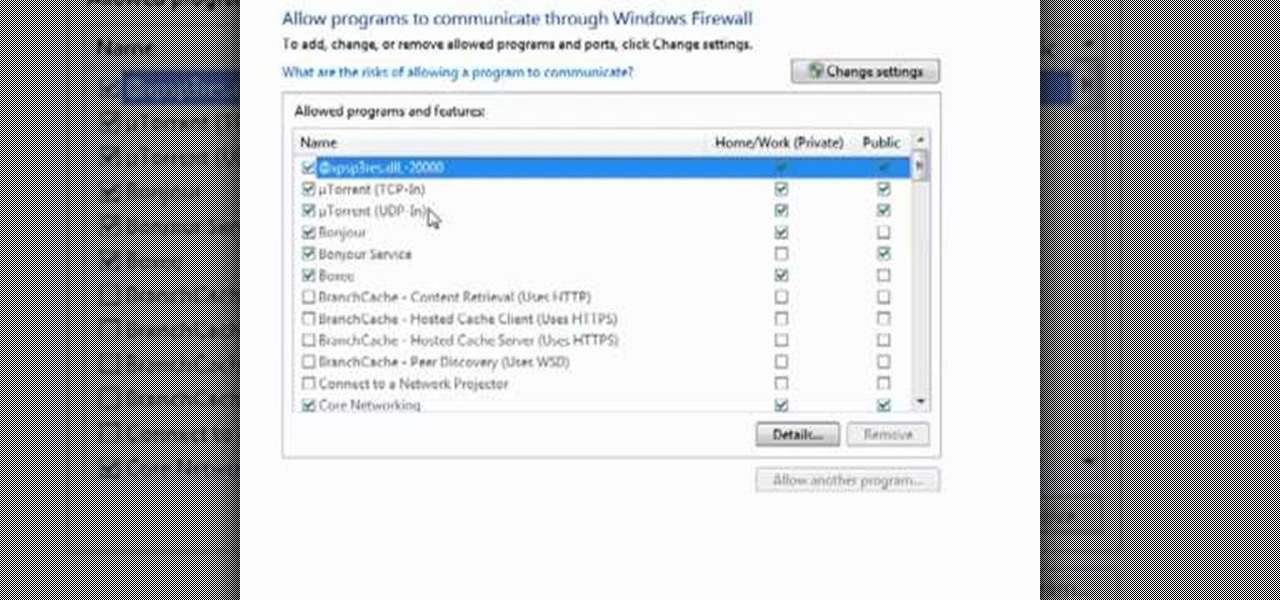
Want to adjust the Windows Firewall to permit µTorrent? This clip will show you how it's done. It's easy! So easy, that this video tutorial can present a complete, step-by-step overview of the process in about two minutes. For more information, including detailed, step-by-step instructions, watch this video guide.

In this video, we learn how to unblock a Facebook firewall at school. First, you will need to try to go to the website you want to go. If you try this and you can't reach the site, go to the top of the bar where you typed the website in at. Once here, you will find where it says "http". Type in an "s" after the "http" so you end with "https" then type in the website that you want to visit. After this, you should be able to go to the website you want to go to without any trouble, just make sur...

Stuck behind a firewall? In this video tutorial, you'll learn how to circumvent a given firewall in five minutes or less by using the tsocks transparent SOCKS proxying library under the Ubuntu Linux distribution. To get started using tsocks, take a look!

In this clip, you'll learn how to enable and use the firewall on a desktop or laptop computer running the MS Windows Vista operating system. For more information, including a complete demonstration of the process and detailed, step-by-step instructions, watch this home-computing how-to.

In this video tutorial, viewers learn how to turn off the system firewall without admin privileges. Begin by clicking on the Start menu and open he Run program. Type in "system.msc" and click OK. Scroll down the Services list and look for Windows Firewall. Double-click on it and under the General tab, click on Stop. Then click Apply and OK. This video will benefit those viewers who use a Windows computer and would like to turn off the firewall, even if they are not running the administrator a...

Check out this computer software tutorial from Dummies.com. This tutorial is made for PCs. Increasing a PC's Windows Vista security is easily done by turning on the Windows firewall and Windows Defender. There's no need to download the firewall or Defender. Protection against spyware and other security risks increases upon enabling these free, built-in Windows solutions. Enable the Windows firewall and Windows Defender.

Have you ever tried check your e-mail for an important project at school? Were you blocked from the site because of the school's firewall? Stop the block by watching this video tutorial. By following its short and simple instructions, you will be able to access that e-mail at school and get that project turned in on time. By watching this video, you will be able to access any site at work or school and bypass any firewall that will try to stop you. Break through a Facebook firewall at school ...

Formerly ipchains, iptables is a script-based firewall that's included with both Mac and Linux operating systems. In my opinion, it's the best firewall in existence. The only downfall is that it's complicated for some people to use due to its script-based nature. But this should be disregarded, as firewalls are nearly the entire security of your computer.

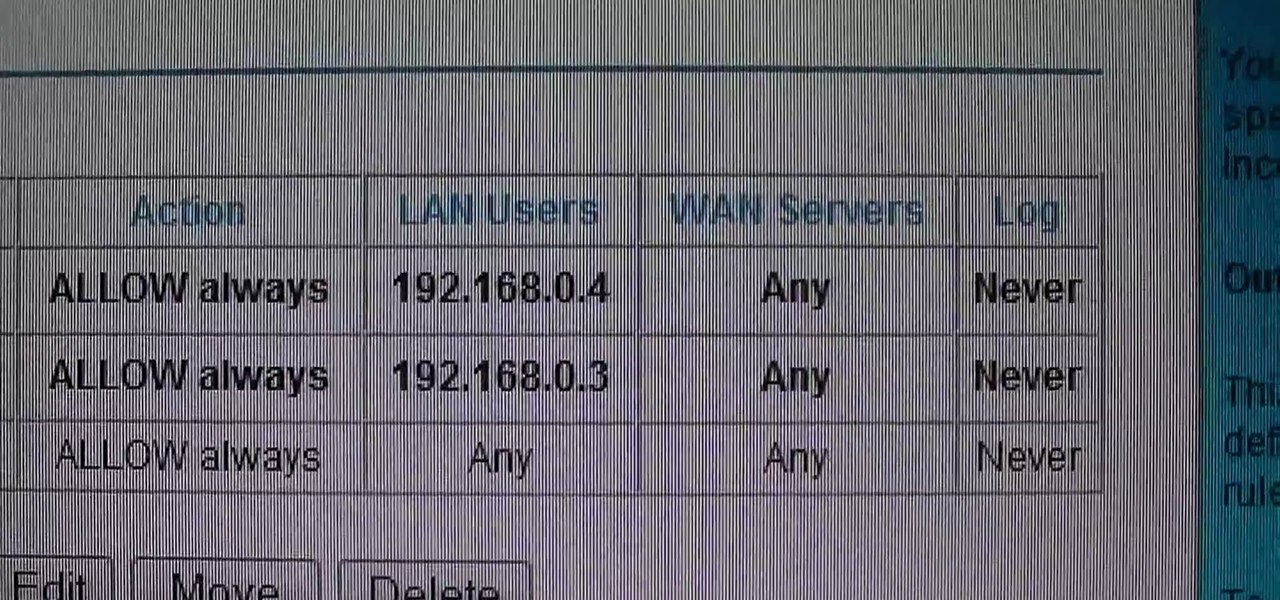
This video shows how to change the NAT type on a PS3. Go to connection settings>network settings>internet connection settings>OK>custom>wired connection>auto detect>manual. Choose an IP address that is different from your router, any other consoles, etc. Click right>automatic>do not use>enable. Press x to save settings, and test your connection. In this example, NAT type is 2. Now go to your PC and open IE. In the address bar, input router IP address, username and password. Go to Firewall Rul...

SSH is a powerful tool with more uses than simply logging into a server. This protocol, which stands for Secure Shell, provides X11 forwarding, port forwarding, secure file transfer, and more. Using SSH port forwarding on a compromised host with access to a restricted network can allow an attacker to access hosts within the restricted network or pivot into the network.

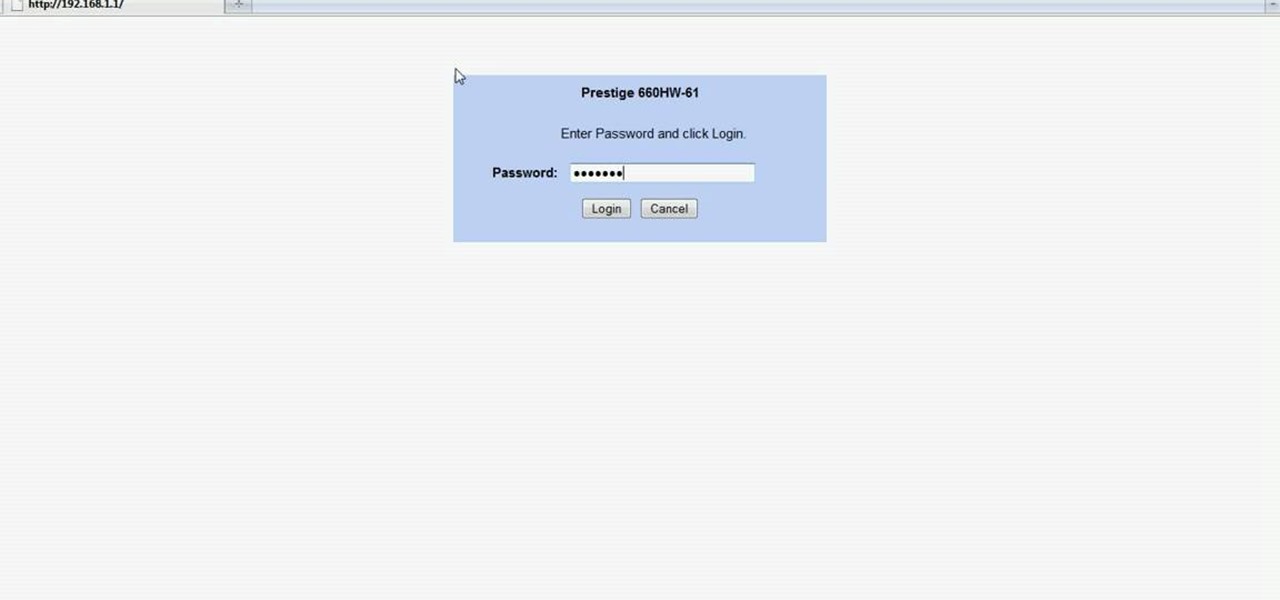
In this Computers & Programming video tutorial you will learn how to easily open your NAT on a ZyXel router. There are three steps involved in doing this. Open your web browser and type in the router IP address which is normally http://192.168.1.1. Then you will get the log in page. The password is either 1234 or admin. It will be written on the packaging of the router. On the next page click on UPNP, then check all three boxes and click 'apply'. Then you click on NAT and set the start and en...

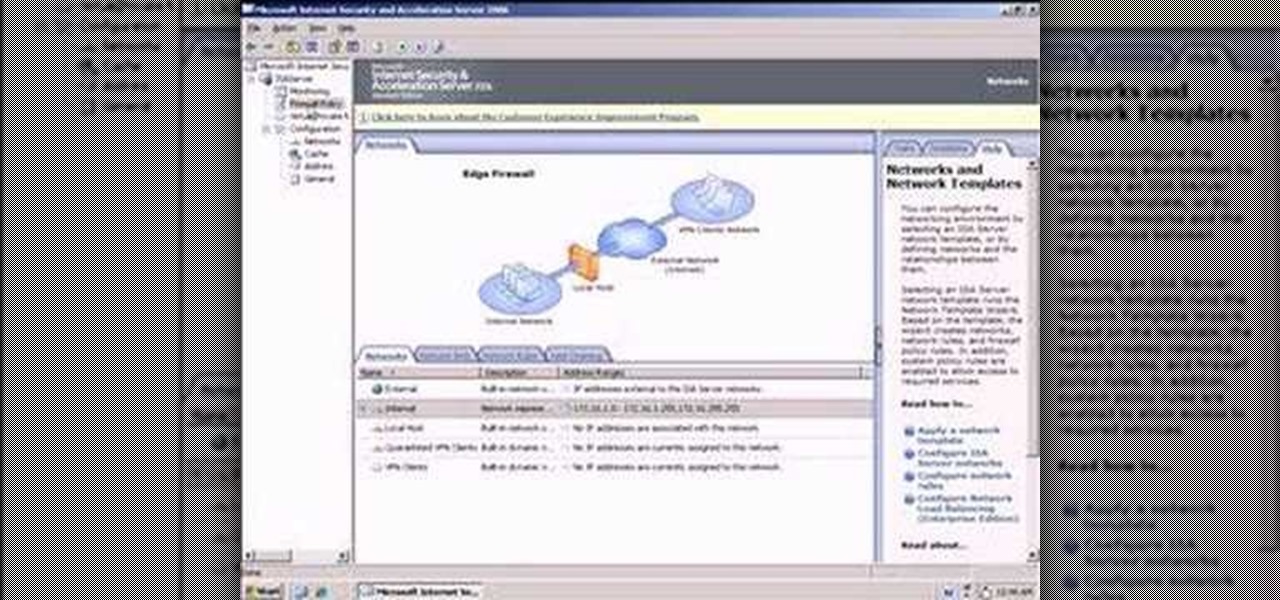
So what exactly is ISA Server? ISA Server, which stands for Internet Security and Acceleration Server, is Microsoft's software-based firewall, proxy, and web caching service/product. Now what does all of that mean? This video helps explain it!

Hello, everyone. Stealth is a large part of any successful hack; if we don't get noticed, we're much less likely to be caught. In these next few articles, we'll be building a shell based on keeping us hidden from a firewall. There are many ways to stay hidden from a firewall, but we'll only be incorporating a couple into our shell. This article will outline and explain these evasion concepts and techniques.

Imagine this scenario: You exploited a system using metasploit and you want to install a backdoor. You have a few options;

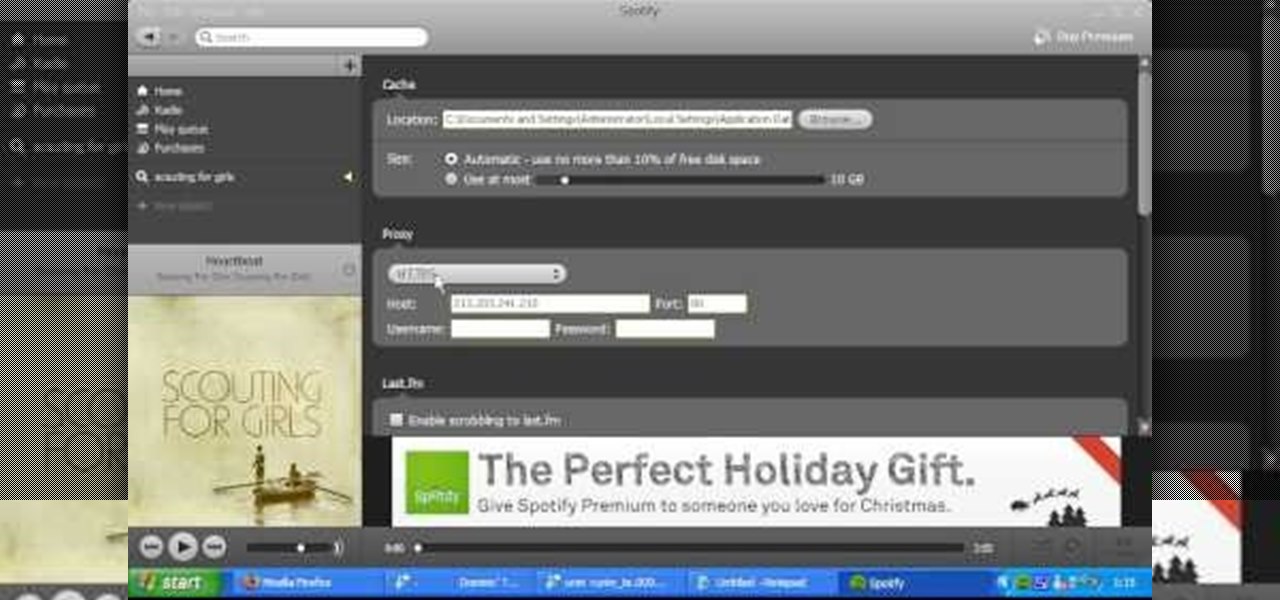
Love free streaming music but hate the annoying ads that come with it? There might just be a solution to that. Use this video to learn how to remove the ads from Spotify. Just follow along and set the Proxy to the following:

At least with a stomach virus you may drop a few pounds; a virtual virus just screws up your computer. Take these precautions to avoid problems. You will need anti-virus software, spyware, a firewall, and a healthy dose of skepticism. You can find free safety software on the internet.

I explain how to view and control your computer from your iPhone/iPod Touch. This works over Edge and Wifi connection, but obviously the better your connection the faster it will go. If you are having problems connecting try going to control panel then security center then turn your firewall off. Also try turning off anything like virus protection.

This video explains how to make your bittorent client download faster. To increase torrent downloads increase your upload capacity to max, enable port forwarding if you have a router hub or firewall that blocks ports, and download torrents with a lot of seeds.

When it comes to antivirus software, you don't want some fly-by-night developer having access to the sensitive data that these apps can scan. Luckily, most of the longest-tenured antivirus companies from the realm of desktop computers offer complete security suites for Android these days.

Welcome back, my fledgling hackers! One of the first issues any hacker has to address is reconnaissance. Before we even begin to hack, we need to know quite a bit about the target systems. We should know their IP address, what ports are open, what services are running, and what operating system the target is using. Only after gathering this information can we begin to plan our attack. Most hackers spend far more time doing reconnaissance than exploiting.

Nmap is more powerful than you know. With a few scripts, we can extend its functionality beyond a simple port scanner and start to identify details about target servers sysadmins don't want us to know.

There are 10 major ways to protect your PC. Disable Autorun, in Windows. Make sure that your system is up to date, by setting automatic updates. Always use a log on for your computer that does not have administrative privileges. Use different passwords, and change your passwords on a regular basis. Don't use simple passwords. Be careful of using links sent to you via email. Never disclose your sensitive information in public forums: e.g. social networks. Encrypt sensitive data on your compute...