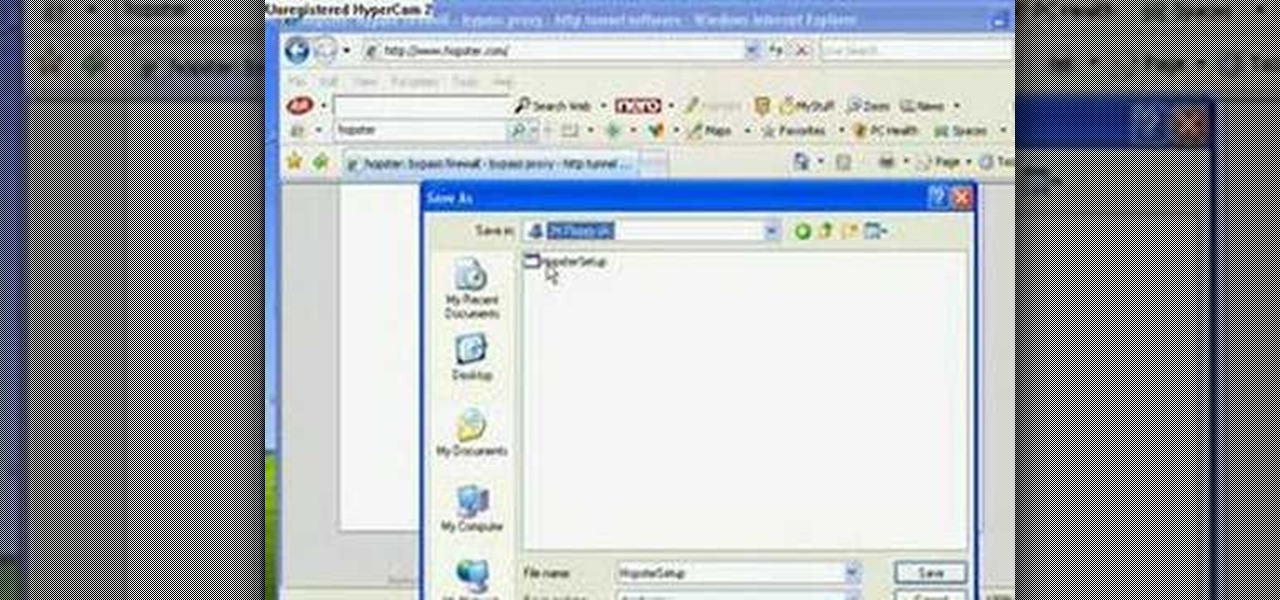
In this video tutorial, viewers learn how to bypass web-sense filter using the software, Hopster. This program allows users to bypass firewall, bypass proxy and HTTP tunnel. To download this program, go to Google and search for the program. Click on the first result and select download. Once the file is downloaded, double-click on it and follow the instructions to install the program. This program runs silently and invisibly so that the administrator won't be able to detect it. This video wil...
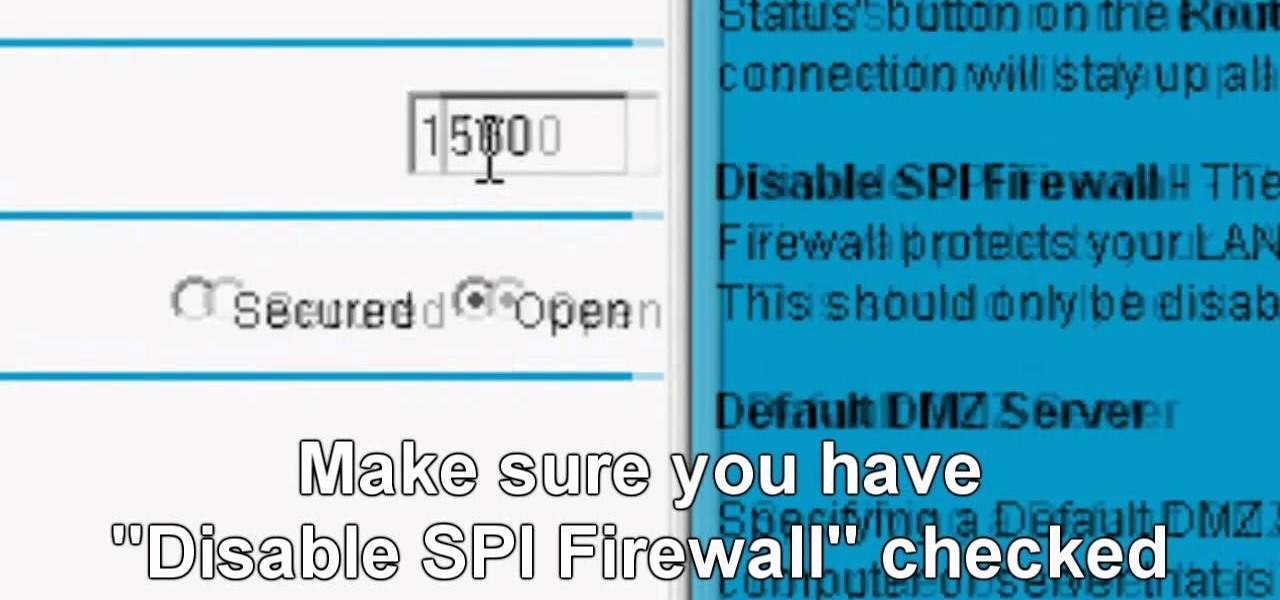
Be warned before hand that by making changes your router settings that you know nothing about can damage your router. Start off by opening your internet browser and then in the address bar either type 192. 168. 1. 1 or www.routerlogin.com. A prompt will come up in which you have to fill in "admin" in the first box and "password" in the second one. Look for the "Advanced" option and under it will be "WAN", click it. Now change your "NAT filtering" to "open". Make sure that "Disable SPI Firewal...

Veronica from Tekzilla teaches you how to monitor network activity on Windows 7. Go to ITSamples and download the Network Activity Indicator program. Install it and run it. This will add a new icon on your system tray. It blinks to reflect incoming and outgoing packets. You can right click to see a more detailed report. You also get statistics and a menu for your network and firewall settings. So to get the popular windows XP type network indicator icon all you need to do is follow the steps ...
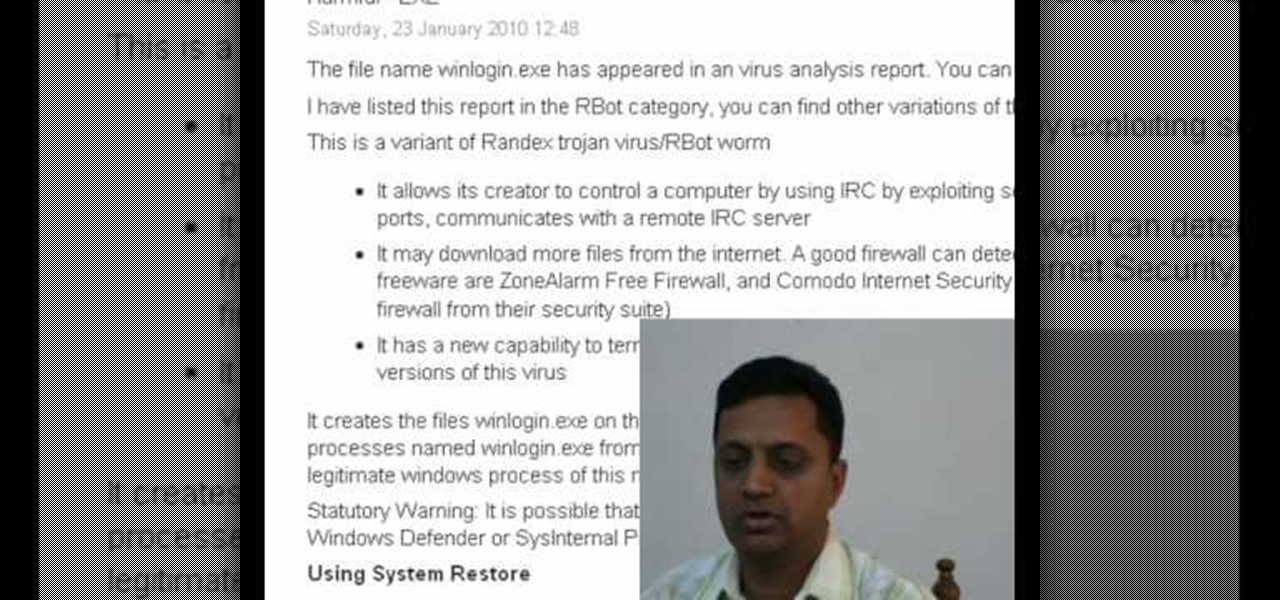
This video shows you how to remove a virus or harmful winlogin.exe file. If you use a good firewall program or a good anti-virus, it will pop-up a window and let you know you have been infected or even block it. If you do not use such things, but you think you know since when you have been infected, you can try to restore your system by using System Restore in Windows XP or Vista. If you do not know the duration of the infection, you can try to manually delete the file when using Windows Safe...

This is a tutorial that shows you how to view and control your computer screen from your iPhone/iPod Touch. But this method is for people who have a jailbroken iPhone/iPod Touch. This works on Edge and Wifi. If you are having problems connecting try going to control panel then security center then turn your firewall off. Also try turning off anything like virus protection.
Follow the steps outlined in this video to learn how to connect to XBox Live using a laptop running Windows XP. The first step is to connect the XBox with the laptop by using an Ethernet cable. When they are connected you have to click on Start and select 'Connect To' and then 'Show all connections'. Select both the Wireless Area connection and the Local area connection icons by highlighting both of them. To do so hold the Ctrl button until they are both highlighted. At this point right click...

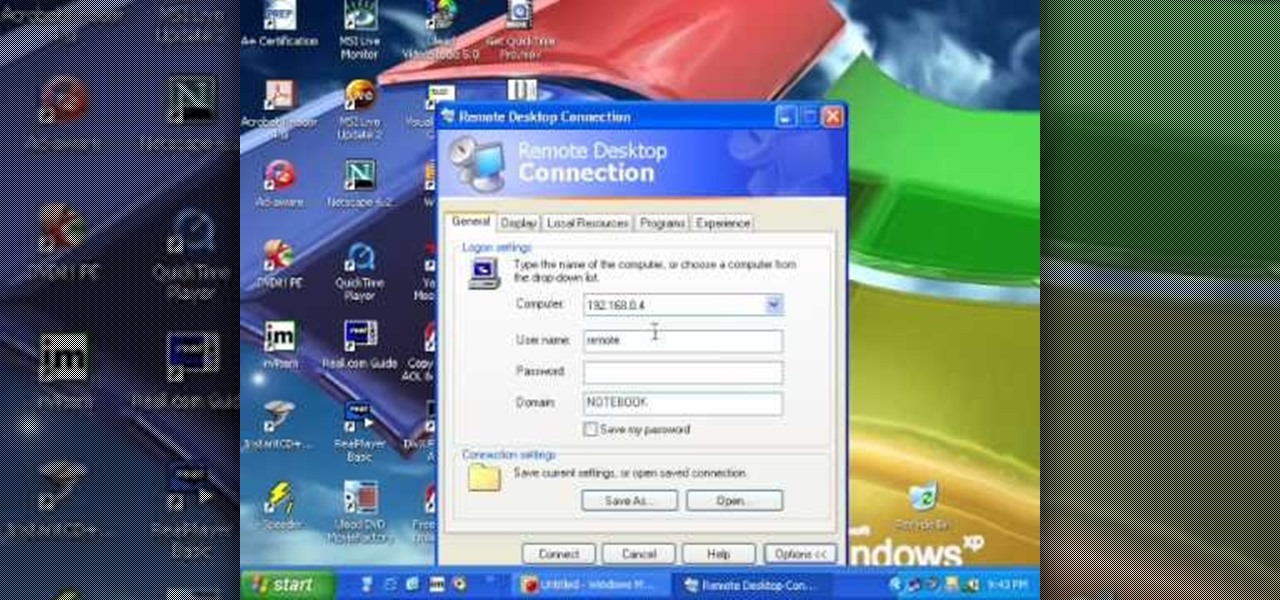
This video from Michael presents how to establish a Remote Desktop connection in Windows XP Professional.This type of connection allows you to access your computer via Internet from any place and manage files, local resources, or perform any other remote activity.To establish Remote Desktop connection click Start button, right click My Computer, from the opened menu select Properties. System Properties window will open. Choose Remote tab. Check Remote Desktop - Allow users to remotely connect...

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to track a USB device.

Determining the antivirus and firewall software installed on a Windows computer is crucial to an attacker preparing to create a targeted stager or payload. With covert deep packet inspection, that information is easily identified.

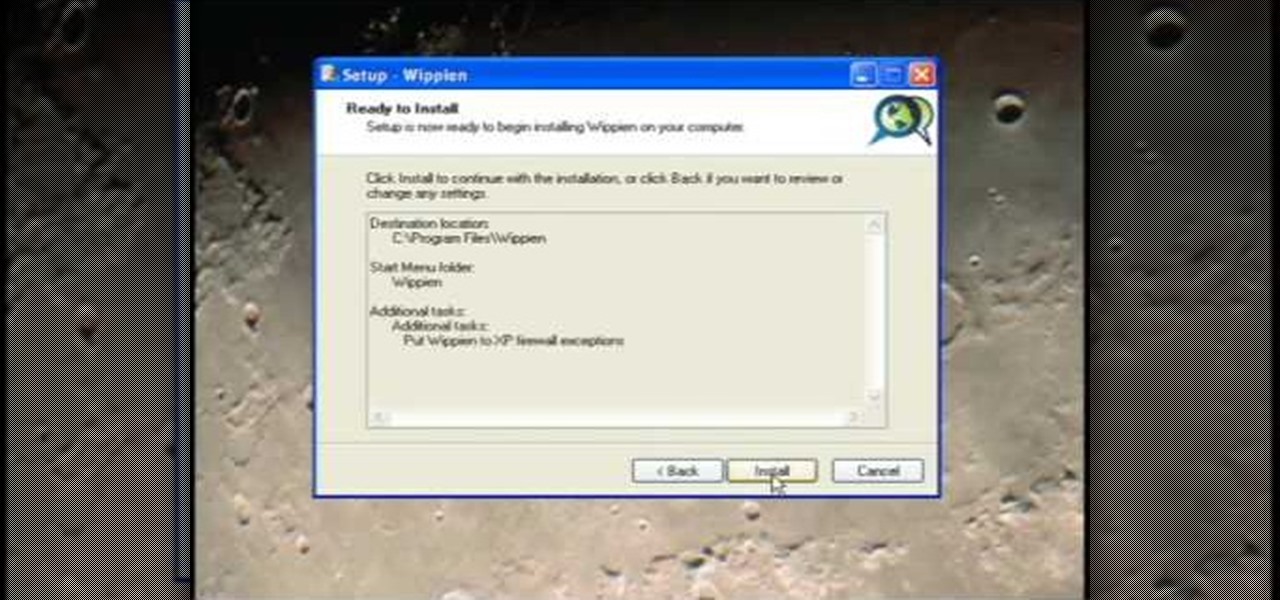
This video tutorial from ruralgeek shows how to set up and use Wippien VPN on Windows XP. First, download Wippien client from here: www.wippien.com.

After installing Ubuntu as your primary OS, you should have protected against USB Rubber Ducky payloads, defended against hard drive forensics, and reduced the overall attack surface against physical strikes. When defending against network-based attacks, you'll want to minimize hardware disclosures, prevent packet sniffers, harden firewall rules, and much more.

Welcome back, my fledgling hackers! Awhile back, I demonstrated one of my favorite little tools, netcat, which enables us to create a connection between any two machines and transfer files or spawn a command shell for "owning" the system. Despite the beauty and elegance of this little tool, it has one major drawback—the transfers between the computers can be detected by security devices such as firewalls and an intrusion detection system (IDS).
Welcome back Hackers\Newbies!

Each day, we read about another security breach somewhere in our digital world. It has become so commonplace that we hardly react anymore. Target, J.P. Morgan, iCloud, Home Depot, and the list goes on and on.

Welcome back, my budding hackers! One of the most time-consuming, but necessary, activities in hacking is reconnaissance. Before we can hack a system, we need to know what operating system it's running, what ports are open, what services are running, and hopefully, what applications are installed and running.

A tutorial showing how to set up a free dynamic DNS address with DynDNS.org and configuring the home router/firewall to forward traffic to your webserver.

The first few minutes after gaining access to a MacBook are critical — but where do we begin? Using tools built into macOS, we can develop an in-depth understanding of running background processes, detect antivirus software, locate sensitive files, and fingerprint other devices on the network. All of this can be done without installing additional software or modifying any files.

Welcome back, everyone. In the previous part of this rapid-fire miniseries, we built the attacker portion of the shell. In this article, we'll just be testing it to see if everything works correctly.

In this tutorial, we learn how to bypass a blocked site on a school computer. You will need a proxy to do this safely. First, go to a proxy site like Proxify. Going through here will prevent the school blocking system from coming up and ruining your fun. If you are blocked, you can use a text file document and run CMD on your computer. This would be the more technological way to do it. Try doing the website first to see if it works, if not, then you can try to change the firewall on the compu...

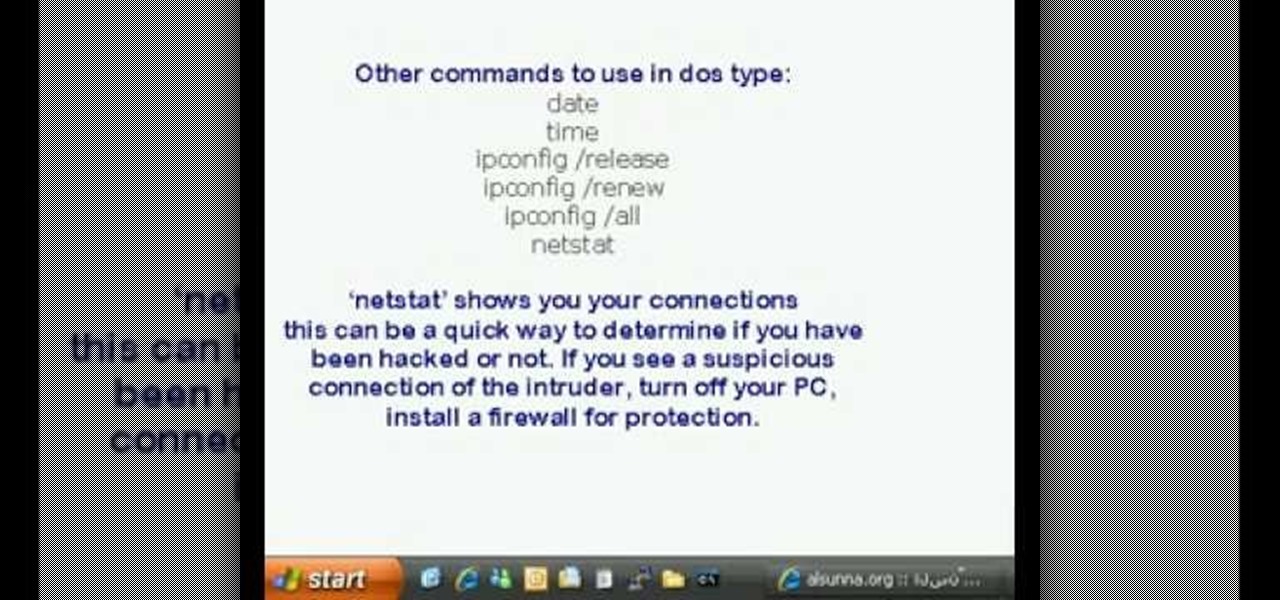
This is a video tutorial in the Computers & Programming category where you are going to learn how to find and ping your IP address. Go to start > run and type in "cmd" to get the DOS window. Here type in "ipconfig" and hit enter. If you are online, your IP address will be displayed. If you are offline, go online and try again. Then in DOS type in "ping yahoo.com". This is to see if you can connect to Yahoo. If you are online, the site will reply 4 times. If you type in "netstat", it shows yo...

In this tutorial, we learn how to connect to Xbox Live using a laptop with Windows Vista. First, connect the Ethernet cable to your computer and to the back of the game console. Next, Click on the start menu, then go to the control panel and view network connections. Next, click on manage network connections. After this, click on your local connection and hold down control until you see your wireless internet. After this, right click on your connection and then go to bridge connections. Next,...

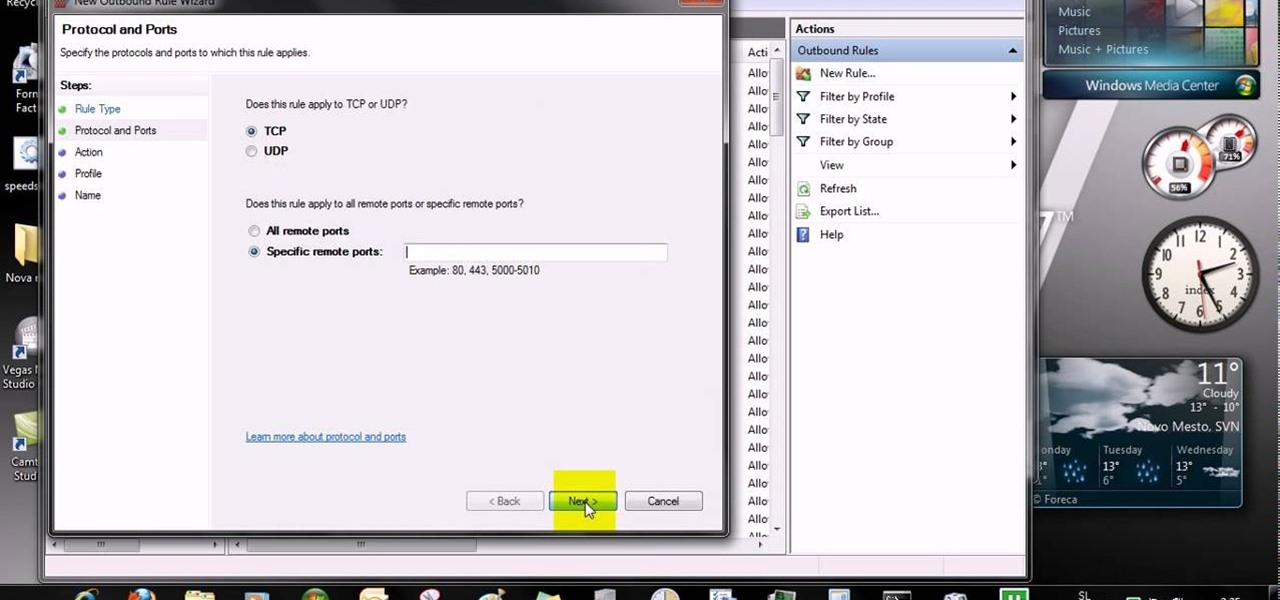
This video tells us the method to open ports in Windows 7. Click on myu icon and go to 'Preferences'. Copy the port number from the resulting window. Go to 'Start', 'Control Panel' and 'System and Security'. Go to 'Windows Firewall' and 'Advanced Settings'. Go to 'Inbound Rules' and 'New Rule'. Click on 'Port' and select 'TCP' and 'Specific Local Port'. Type the port number in the text box. Click 'Next' and 'Allow Connection'. Press 'Next' twice and put the name in the space provided for it. ...

In this video they are teaching about "How to connect XBox 360 to computer for wireless internet". For all this we have to have a laptop or a computer. And it also needs an Ethernet cable. It will be portable both for computer and laptop. Connect the Ethernet cable both to the laptop and XBox. After connecting that switches on the XBox, go to the network connections in laptop and advance the settings there. Switch on the XBox and see if its showing connected. If it does not show just go to th...

Complex shell scripts can be implanted into photo metadata and later used to exploit a MacBook. In addition to obfuscating the true nature of an attack, this technique can be used to evade network firewalls as well as vigilant sysadmins.

Auditing websites and discovering vulnerabilities can be a challenge. With RapidScan and UserLAnd combined, anyone with an unrooted Android phone can start hacking websites with a few simple commands.

With the addition of the OpenSSH client and server in the Windows 10 Fall Creators Update, you no longer have to rely on third-party programs to open an SSH server and connect to a Windows machine. While still a beta feature, this represents a long-overdue update fulfilling a promise made back in 2015.

Welcome back, my novice hackers! Reconnaissance is one of the most important preparatory steps to hacking. As I have emphasized many times before here on Null Byte, you must know the operating system, the ports, the services, the applications, and sometimes even the language of the target to be effective. If you haven't taken the time to gather this info, then you are likely wasting your time.

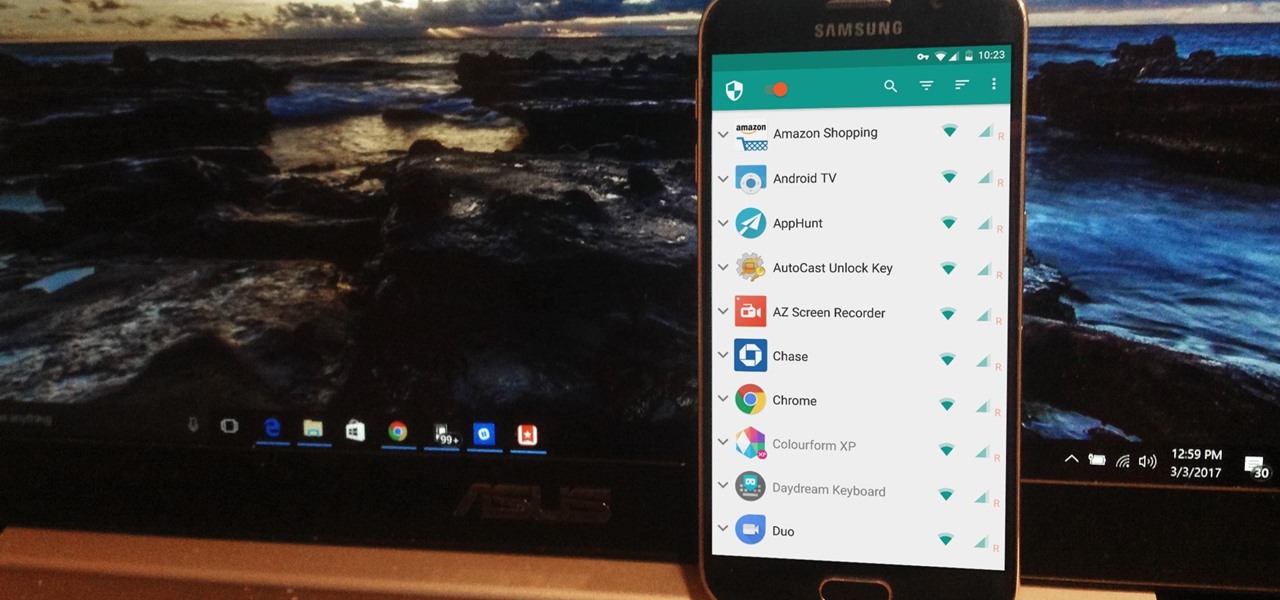
NetGuard is a well-established app known for its highly secure firewall, which blocks unwanted web activity from individual apps that can take up both precious bandwidth and battery life. Not quite as well known, however, is the fact there's a second official version of NetGuard that comes with a hidden ad-blocking feature, which can be activated with just a little tinkering in the app's settings menu.

I have came across a lot of members on the forum that didn't have a clear idea of what port forwarding is and what it does. So...Let's get started...

Keeping your online data and identity private is an uphill battle, but with the anonymity network Tor, you have a pretty decent line of defense from prying eyes.
Hello, Hackers/Viewers! My name is nullf0x, and I have 4 years of experience as a hacker. You might see everyday that one of your friends or acquaintances get a new virus in their computer. You might think, How cool would it be if I made a virus? or How cool would I be if i could remove viruses from others computers for money or free?

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

A hacker with privileged access to a Windows 10 computer can configure it to act as a web proxy, which allows the attacker to target devices and services on the network through the compromised computer. The probes and attacks appear to originate from the Windows 10 computer, making it difficult to detect the attacker's actual location.

Backdooring a powered-off MacBook is easy when a few minutes of physical access is allowed. That attack works well if the hacker also shares a Wi-Fi network with the victim, but this time, I'll show how to remotely establish a connection to the backdoored MacBook as it moves between different Wi-Fi networks.

When I tried to set up an eviltwin for a MitM-constelation in kali 2.0, I couldn't provide internet to the victim. The origin was the brctl bridging. I have read many tutorials but all of them where explained in backtrack and older versions of kali. So i was searching for a solution without using brctl and this solution will be explained now. This will just work on unencrypted wireless-environments.

Welcome back, my greenhorn hackers! Continuing with my Wi-Fi hacking series, this article will focus on creating an invisible rogue access point, which is an access point that's not authorized by the information technology staff and may be a significant security vulnerability for any particular firm.

Post-exploitation information gathering can be a long and drawn-out process, but it is an essential step when trying to pivot or establish advanced persistence. Every hacker should know how to enumerate a target manually, but sometimes it is worth it to automate the process. Metasploit contains post modules that can quickly gather valuable information about a target, saving both time and effort.

Almost every phone comes with biometric security of some sort these days, but the same can't be said of Windows computers. While fingerprint scanners are becoming increasingly common with laptops and desktops, they're nowhere near ubiquitous. Thankfully, your phone's scanner can be used as a sort-of remote authentication point for your PC.

Command injection is a technique used by hackers to execute system commands on a server, usually via a web application or some kind of GUI. This can happen when an application provides some sort of functionality to the user involving the use of system commands. When the input is not properly sanitized, commands not originally intended to be run are allowed to be executed.

Using a keylogger to intercept keys pressed on an infected computer can circumvent encryption used by email and secure chat clients. The collected data can often reveal usernames, passwords, and potentially compromising and private information which hackers abuse for financial gain.