I love eating fish at restaurants—the flesh is flaky and tender; the scent, fresh and sweet. Cooking fish at home is a completely different story, though. Even when I do cook successful fish dishes, it often leaves this (for lack of a better description) fishy smell that permeates everything it touches. Monday's salmon becomes Wednesday's odor. It's enough to deter me from cooking fish, period.

At first glance, caviar doesn't seem overly appealing to the masses; not very many people would be willing to spend upwards of $1,000 on a tiny spoonful of salty sturgeon eggs from the Caspian Sea. Caviar truly is the ultimate symbol of luxury and fine dining.

Granola bars are the perfect snack to have around: they're tasty, not messy, have nutritional value, are filling, and don't go stale quickly.

Avocado is great in guacamole or as slices on a sandwich, but there's so much more you can do with this wonderful fruit (call it a vegetable, that's fine—but it's technically a fruit). While I could eat guac every single day, these are some of my favorite recipes to spice up avocados a bit, from making a guilty snack to a condiment and even dessert!

Cooking on a budget isn't always easy, but there's a silver lining: it can be really fun. Ever since I started supporting myself I've enjoyed going shopping, finding the most affordable items, and learning how to make the most of them. Sure, sometimes I wish I could afford to buy a filet mignon and some morel mushrooms every night, but there's a different kind of enjoyment that comes from being able to turn a few dollars into a gourmet meal. For me, that means starting with cheap meat, and af...

In my opinion, there is nothing in the culinary world as satisfying as cutting into a steak, and seeing that you've cooked it to perfection. Even if you're one of those bizarre people that prefers their steak medium or well done (hey, no judgement... okay, fine, a little bit of judgement), it's culinary heaven when you realize that you achieved the perfect doneness on your steak.

I'm a firm believer that a sandwich is the ultimate food. It's filling, but not heavy; it has carbs, protein, veggies, and sauces; and it's easily customizable. Add that all up and you've got the absolutely perfect lunch.

Given how much use it gets on a daily basis, the power button is always one of the first hardware features to call it quits on an Android phone or tablet. So if your power button is acting up, or you don't want it to, you can extend its lifetime by simply finding ways to use it less.

Poor chickens. Bacon fat is revered (and justifiably so), and duck fat is a staple at most fine grocers. Marbles of fat make a steak divine, and goose fat is the holy grail of fatty goodness. Yet chicken fat is usually thrown away.

Hello readers, and welcome to Null Byte. Before we start, for those of you who may not know me, my name is ghost_; I'm a relatively active member of our community and have been around for a while.

Welcome back, my greenhorn hackers! Before we attempt to exploit any target, it is wise to do proper reconnaissance. Without doing reconnaissance, you will likely be wasting your time and energy as well as risking your freedom. In previous guides, I have demonstrated multiple ways to perform reconnaissance including passive recon with Netcraft, active recon with Nmap or hping3, recon by exploiting DNS or SNMP, and many others.

Ginger root is one of the most underappreciated and versatile spices around. It's simultaneously hot, sweet, and piquant. It's also a pain in the tush to peel, thanks to its thin, fragile skin and the thick, knotty rhizome that contains all the flavor.

A few weeks ago, Bluebox Security uncovered a bug that could potentially effect 99% of Android devices. Bug 8219321, dubbed the Master Key bug, works by allowing applications with modified code to pass Android's signature verification system, thereby bypassing security measures that normally wouldn't allow these apps to be installed.

LEDs have slowly become the standard for DIY lighting projects because they consume less power and last way longer than regular light bulbs do. Light-emitting diodes have no filament, meaning they generate their light solely by the movement of electrons in a semiconductor material.

Hi! All the cake lovers, welcome to my first post in the World of Dessert Recipes. I would like to contribute a recipe for the chocolate cake, called Taraba. The original recipe was made in Bosnia. It is one of my favorite cakes, very sweet, but does not contain fruit.

The next mobile operating system for the iPhone, iOS 6, will be available in fall 2012. The major details and features were released 2 weeks ago a Apple's World Wide Developers Conference (WWDC). While the goal of these yearly OS updates is to move forward with technology, there are a couple of this to watch for. Keep reading to see the good and the not so good. Do Not Disturb

Taco Bell's in the news for umpteenth time, and today the controversy is over their infamous beef taco meat. Gizmodo leaked a picture of Taco Bell's "Taco Meat Filling" and surprise, surprise— it's missing a lot of the "meat" that it claims in its advertisements. Taco Meat Filling Ingredients

If you have no intention of getting personalized engravings on your AirTags, you don't need to shop on the Apple Store unless you have an Apple Card you want to earn Daily Cash with. Best Buy. Target. Adorama. B&H Photo. All of those places will let you preorder AirTags now but so does Amazon, America's second-biggest retailer, a good choice whether you have Amazon Prime or not.

The year 2021 is already promising to yield a number of major shifts in the augmented reality landscape, and Snap is signaling that it has every intention of being an aggressive part of that narrative.

It's no secret that Samsung is working on augmented reality hardware, as the company has been candid about its intentions. However, what we don't know is exactly how many AR projects the company is working on, as patent filings and reports revealed two more over the past week.

Who's ready to let future Facebook augmented reality smartglasses read their brain? Well, ready or not, the tech giant is making progress in the area of brain control interfaces (BCI) by funding research.

All of the the tech industry giants, including Apple, Facebook, and Google, are working on new smartglasses and/or AR headsets, but this week, Google took a major step forward with gesture recognition technology that could make its way into AR wearables, posing a threat to Leap Motion and its hand-tracking controllers.

In the world of technology, there's often a trade-off between convenience and security. The Java Remote Method Invocation is a system where that trade-off is all too real. The ability for a program written in Java to communicate with another program remotely can greatly extend the usability of an app, but it can also open up critical vulnerabilities that allow it to be compromised by an attacker.

Despite a very vocal distaste for Bixby, Samsung continues to push their voice assistant on customers. For many, the button is not only a waste, but placed perfectly for accidental presses. While it appears Samsung has no intention of giving up on Bixby, with the help of an excellent app, you can get rid of it yourself.

Starting Nov. 1, 2018, Google got a lot tougher with Android app developers. New apps being uploaded to the Play Store already had to target Android 8.0 Oreo or higher as of August, but now, every update to existing apps has to do the same. It may seem like a simple rule, but it will have some serious repercussions.

Traditional subdomain enumeration techniques create a lot of noise on the target server and may alert intrusion detection systems to an attacker's intentions. For a stealthier approach, there's a tool with the capability of finding hundreds of subdomains related to the target website without alarming the server administrators.

Google collects an enormous amount of personal data. While some of this data is used for targeted ads, others tidbits of info such as our location are used to improve our mobile experience. While it is natural for us to distrust Google's intentions, by allowing their data collection, we can add new functionality to our favorite apps.

Buying an unlocked phone is usually the correct move. By doing so, you bypass a lot of bloat that carriers put on your phone, and you can also use that phone with another carrier should you decide to switch to a new one. However, a lot of carriers won't give unlocked devices access to their visual voicemail apps. For that, there's Google Voice.

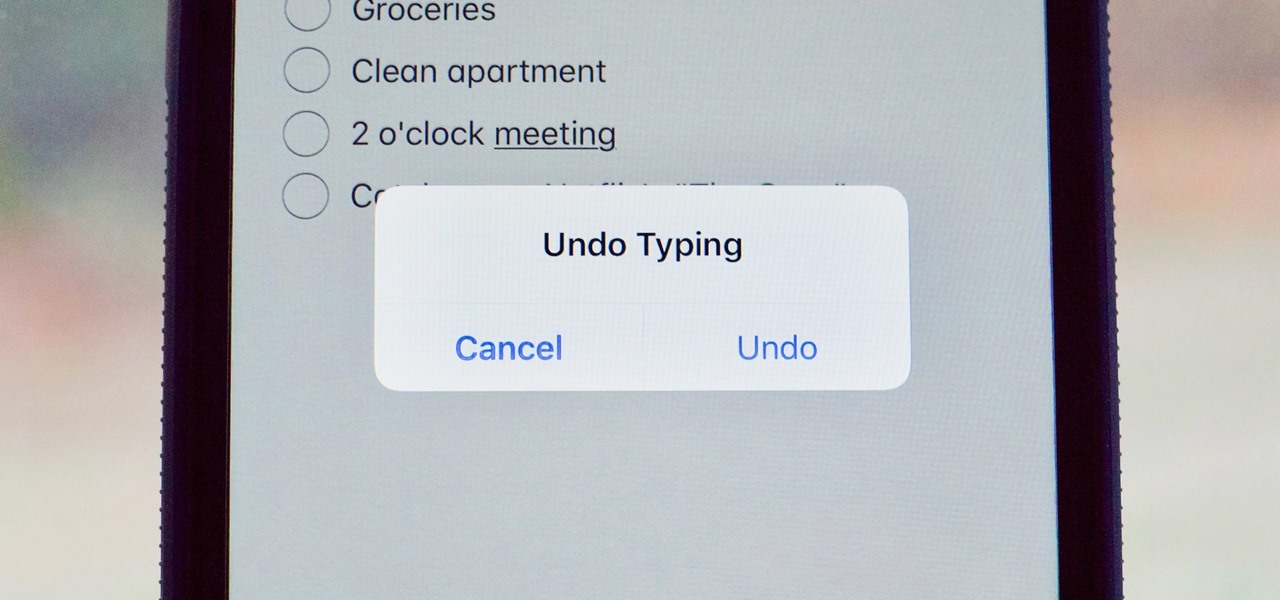
Many of us use the Notes app to jot things down in a hurry. Most of the time, that's no big deal. However, the faster the typing, the higher the chance of error. If you happen to make a typo, or if you accidentally delete that chart you worked so hard on, there's an easy way to undo the changes.

Disengagement report numbers for self-driving car testing in 2016 on public roads in California were just released, and the biggest point we can make about them is that Waymo is very far ahead of their competitors in almost every metric.

before I move on to more exciting areas in this series, I want to also point out some things to protect your information & how to not get DoXed.

Students have been passing notes in class for decades, so what's the big deal about sending a quick text message? Everybody does it, even your teacher was surely guilty of covertly communicating with his or her peers back when they were in high school.

Welcome back, my tenderfoot hackers! A short while ago, I started a new series called "How to Spy on Anyone." The idea behind this series is that computer hacking is increasingly being used in espionage and cyber warfare, as well as by private detectives and law enforcement to solve cases. I am trying to demonstrate, in this series, ways that hacking is being used in these professions. For those of you who are training for those careers, I dedicate this series.

Welcome back, my greenhorn hackers! Sometimes, we don't have a specific target in mind, but rather we are simply looking for vulnerable and easy-to-hack targets anywhere on the planet. Wouldn't be great if we had a search engine like Google that could help us find these targets? Well, we do, and it's called Shodan!

Welcome back, my budding hackers! I've written several listener guides on creating a malicious PDF or malicious Word document that would carry in it a payload with the Meterpreter, or reverse shell enabling you to own the system. One of the hurdles to using these techniques is the antivirus (AV) software on the target system. For instance, if you try to email a malicious PDF or Word doc, it's likely that the victim system will alert the victim that it contains a virus or other malware.

Sometimes, doing the right thing is way more difficult than it should be, like trying to return a lost smartphone. Despite having the best intentions, it's often hard to track down the rightful owner, especially if the device is armed with a passcode. On the other hand, there are plenty of people who see an unattended iPhone or Samsung Galaxy S3 as a chance for profit. In 2011 alone, the number of lost and stolen cell phones in America was worth over 30 billion dollars. That's right, billion....

For those who don't know, LEGO recently came out with a new line called Monster Fighters. This set is about fighting monsters, sure, but it's about fighting classic monsters in a Steampunk universe. Just look at this promotional picture from the LEGO site: That LEGO dude (properly called a minifig) is wearing a vest, pocket watch, bowler hat, and a mean smirk. Not to mention that he has a robotic leg. You won't find the word "steampunk" anywhere in this marketing campaign, but I call Steampun...

With careful wording you can avoid lying and still avoid going to something that you just don’t want to attend. Even without a good excuse you can politely decline without hurting anyone’s feelings or ending up in an embarrassing situation.

Dogs need toys too! Show your dog some love by making him a handmade squeaky toy. You can put an old pair of jeans to use, practice up on those sewing skills and hear the sounds of enjoyment as your dog squeaks to his heart's content.

I was getting kind of sick of ordering delivery pizza (this happens at least 2-3 times a month). It was time to put a spin on gourmet pizza, but I just didn't know what it would be. Without pizza dough or an oven that is capable of creating the perfect pizza crust (I don't have an oven that can go up to a 1000 degrees), I decided I would use potatoes instead. This recipe is elegant enough to serve at a dinner party, but easy enough that you can cook it within 5-15 minutes.