
How To: Calculate variance in a set of data
The video is about how to find the variance of the set of data. They found the variance by using the variance formula. Variance formula was represented by square of S, whereas S is the Standard Deviation.


The video is about how to find the variance of the set of data. They found the variance by using the variance formula. Variance formula was represented by square of S, whereas S is the Standard Deviation.

This experiment is intended to introduce students to hydrated compounds. These compounds have water molecules coordinated in their chemical structures. Examples CuSO4*5H2O, BaCl2*2H2O, and NaC2H3O2*3H2O.

A little-known setting on your iPhone gives you the power to change the color of certain contact names and email addresses when drafting an email. Customizing the color works well for visually separating contacts at a glance, and it can even help you from sending an email to the wrong person.

Pyrit is one of the most powerful WPA/WPA2 cracking tools in a hacker's arsenal, with the ability to benchmark a computer's CPU speeds, analyze capture files for crackable handshakes, and even tap into GPU password-cracking power. To demonstrate how quickly it can hack a WPA/WPA2 password, we'll use it to play a Wi-Fi hacking CTF game anyone can practice for less than $10.

While you might suspect your MacOS computer has been infected with malware, it can be difficult to know for sure. One way to spot malicious programs is to look for suspicious behavior — like programs listening in on our keyboard input or launching themselves every time we boot. Thanks to free MacOS tools called ReiKey and KnockKnock, we can detect suspicious programs to discover keyloggers and other persistent malware lurking on our system.

There are many ways to attack a Wi-Fi network. The type of encryption, manufacturer settings, and the number of clients connected all dictate how easy a target is to attack and what method would work best. Wifite2 is a powerful tool that automates Wi-Fi hacking, allowing you to select targets in range and let the script choose the best strategy for each network.

Getting root is considered the Holy Grail in the world of Linux exploitation. Much like SYSTEM on Windows, the root account provides full administrative access to the operating system. Sometimes even a successful exploit will only give a low-level shell; In that case, a technique called privilege escalation can be used to gain access to more powerful accounts and completely own the system.

Networking is built largely on trust. Most devices do not verify that another device is what it identifies itself to be, so long as it functions as expected. In the case of a man-in-the-middle attack, we can abuse this trust by impersonating a wireless access point, allowing us to intercept and modify network data. This can be dangerous for private data, but also be fun for pranking your friends.

Good day people, today we will examine some basic, for some people well-known attacks, also we will take a look at some advanced attacks.

Greetings all. Before I get into the tutorial, I would like to mention that I am fairly new to Null Byte (been lurking for some time though), and what really appeals to me about this place is its tight, family-like community where everyone is always willing to help each other and the constant search for knowledge that inhabits this subdomain is a driving motivator for me to join in. I'm glad I arrived at the right time. Anyway, wipes tears (not really)...

While password cracking and WPS setup PIN attacks get a lot of attention, social engineering attacks are by far the fastest way of obtaining a Wi-Fi password. One of the most potent Wi-Fi social engineering attacks is Wifiphisher, a tool that blocks the internet until desperate users enter the Wi-Fi password to enable a fake router firmware update.

No one can deny that Bashar Al-Assad’s regime has been responsible for violence. But in failing to equally acknowledge the fact that NATO-backed rebels have also carried out innumerable atrocities is not only dishonest, it represents a deliberate effort by the press to manipulate the narrative of unfolding events in Syria as a one-sided war crime rather than the truth – which is the fact that Syria is in a state of civil war.

What's the best way to celebrate your independence? Alcohol. There's no a soul out there that can't enjoy a few drinks during a nice celebration. So, why not go a step further with some crazy shots? Shots are the quickest and easiest way to get drunk fast. Do it for your country — but don’t overdo it. Mix up a batch of patriotic cocktails for your Independence Day party.

Learn to make a model ship to put in a bottle with this video guide. 1. Take clean plastic bottle with mouth about 5 inches to fit the ship

When it comes to used cars, it’s hard to make lemonade out of a lemon. So don’t get stuck with a piece of junk in the first place.

Learn how to spot a dishonest contractor for home repair. It’s no accident contractors have such a bad reputation – they get more fraud complaints than any other workers! Here’s how to find a reputable one – and skip the scammers.

This Independence Day, make a stunning holiday dessert with fondant, butter cream frosting and royal icing. Decorate a Forth of July cake with an American Flag and fireworks in this free holiday recipe video series.

Downloading third-party screen recording apps can be dangerous. The primary function of these apps is being able to record everything on one's display, so it's easy to see how a malicious developer could exploit this for their own gain. That's why the addition of Android 10's built-in screen recording is so impactful.

Password cracking is a specialty of some hackers, and it's often thought that raw computing power trumps everything else. That is true in some cases, but sometimes it's more about the wordlist. Making a custom, targeted wordlist can cut down cracking time considerably, and Wordlister can help with that.

Privilege escalation is one of the essential skills a hacker can have and often separates the newbies from the pros. With a continually changing landscape and a plethora of exploits out there, it can be a problematic aspect of any attack. Luckily, some tools can help expedite the process. Linux Exploit Suggester is just one of many to help you get root.

So you've managed to get a shell on the target, but you only have measly low-level privileges. Now what? Privilege escalation is a vast field and can be one of the most rewarding yet frustrating phases of an attack. We could go the manual route, but like always, Metasploit makes it easy to perform local privilege escalation and get root with its exploit suggester module.

Starbucks is spicing things up ahead of this holiday season with a little augmented reality joy. This week the company launched its first Instagram filter, called Holijoy, delivered like an early Christmas gift and packing four seasonal lenses.

Correctly identifying the underlying technologies that run on a website gives pentesters a considerable advantage when preparing an attack. Whether you're testing out the defenses of a large corporation or playing the latest CTF, figuring out what technologies a site uses is a crucial pen-tester skill.
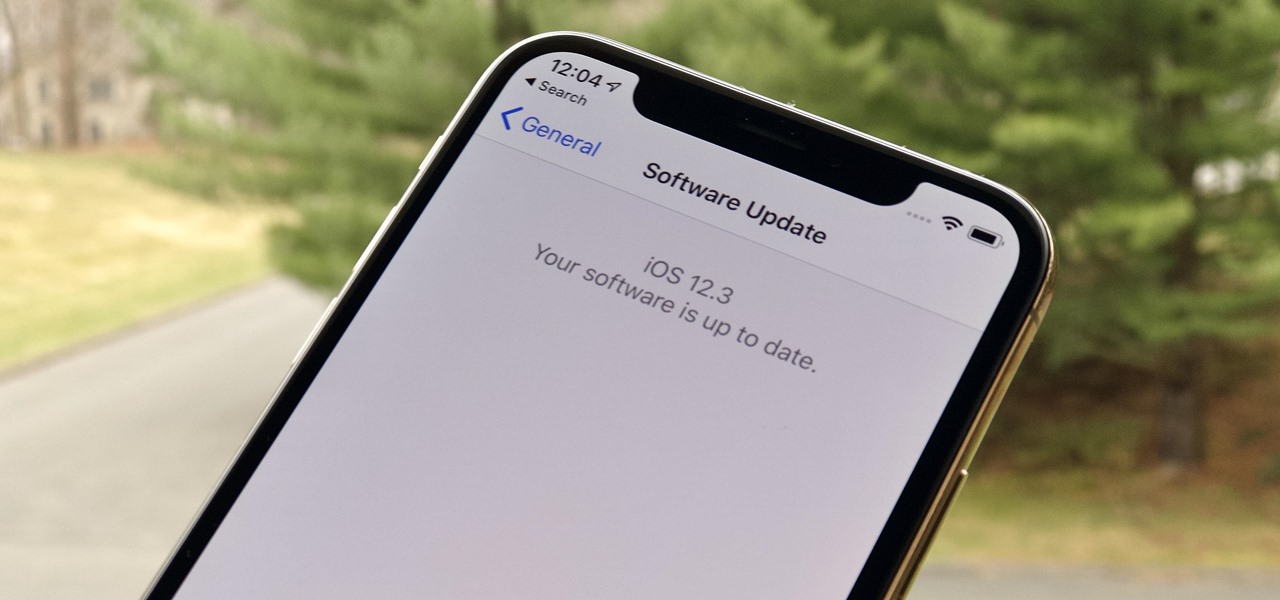
Apple just released the second public beta for iOS 12.3 today, Tuesday, April 9, one day after the release of the iOS 12.3 developer beta 2. This update introduces new Japanese "Date & Time" updates as well as changes to Wallet transactions. Overall, iOS 12.3 includes Apple TV Channels, premium monthly subscriptions with content available directly in the TV app across the Apple ecosystem.
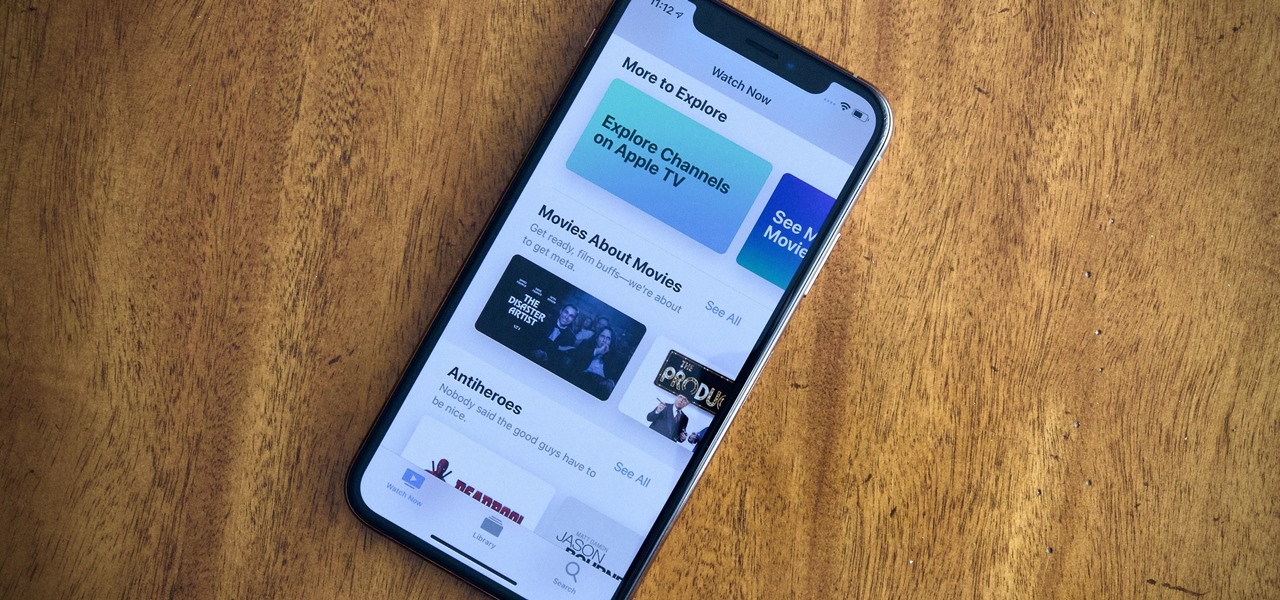
Apple just released iOS 12.3 dev beta 2 today, Monday, April 8, which follows the first iOS 12.3 beta by twelve days. This update introduces new Japanese Date & Time features as well as updates to Wallet transactions. As a whole, iOS 12.3 introduces Apple's previously announced Apple TV Channels, premium monthly subscriptions with content you can watch right in the TV app across Apple products.

Popping a shell is often the main goal of a hacker, and it can be exciting when executed properly, but sometimes they do have their limitations. Metasploit's Meterpreter probably needs no introduction, but this powerful, dynamic payload can offer a leg up over normal shells. To prove it, we'll show how to take a normal command shell and elevate it to a Meterpreter session.
Intel's RealSense family of depth tracking cameras has a new addition with a different set of sensory capabilities.

Things that are supposed to make life easier for developers and users are often easy targets for exploitation by hackers. Like many situations in the tech world, there is usually a trade-off between convenience and security. One such trade-off is found in a system known as Distributed Ruby, which can be compromised easily with Metasploit.

Google subsidiary Owlchemy Labs has cooked up an experimental ARCore mobile app that enables smartphone users to follow along with their VR friends as they play games in a head-mounted display.
Earlier this year, with the Developer Preview, we got a tantalizing glimpse of Google's upcoming Android 9.0 Pie and a whole slew of new features that comes along with it, such as iPhone X-like gestures and improved security features, to name a few. With its announcement at Google I/O, Android Pie just got a lot more accessible.

Next to things like natural disasters and disease, the specter of war is one of the only things that threatens to derail the 21st century's long stretch of technological innovation. Now a new app is using augmented reality to remind us of that by focusing on those most impacted by war — children.
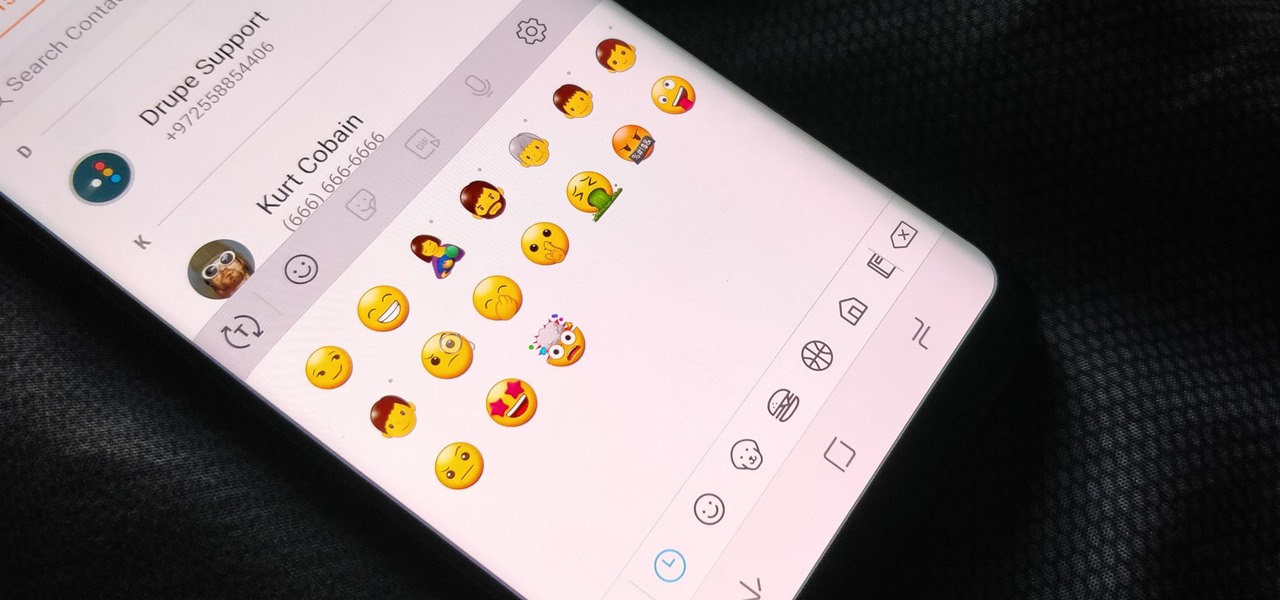
New emojis are coming with the Android Oreo update for Galaxy S8 and S8+. Samsung Experience 9.0 has been updated to Emoji 5.0, adding 239 brand new emojis when you take into account gender and skin tone variants. While there are minor changes across the board, we wanted to focus on the newly created emojis so you'll know what's available to you.

BMW seeks to hire 2,000 engineers for its driverless program ahead of the launch of its iNext Level 3 model in 2021, a source close to the company told Driverless.

A new survey shows that the majority of companies have an interest in using augmented reality, though adoption remains low. Meanwhile, two companies with support roles in the augmented reality industry are seeing positive financial results.

Deleting emails can be a tedious process on the iPhone, especially since the "Trash All" options have been removed ever since iOS 10 first came out. Though likely well-intentioned, this change places an undue burden on all of us iPhone owners who now have to erase emails individually.
Immigration and immigration policy are some of the biggest discussions happening in international and domestic politics right now. From building walls to opening borders, a definitive plan has not been made about how to deal with the large number of people who are fleeing their home countries in hopes of a different life.
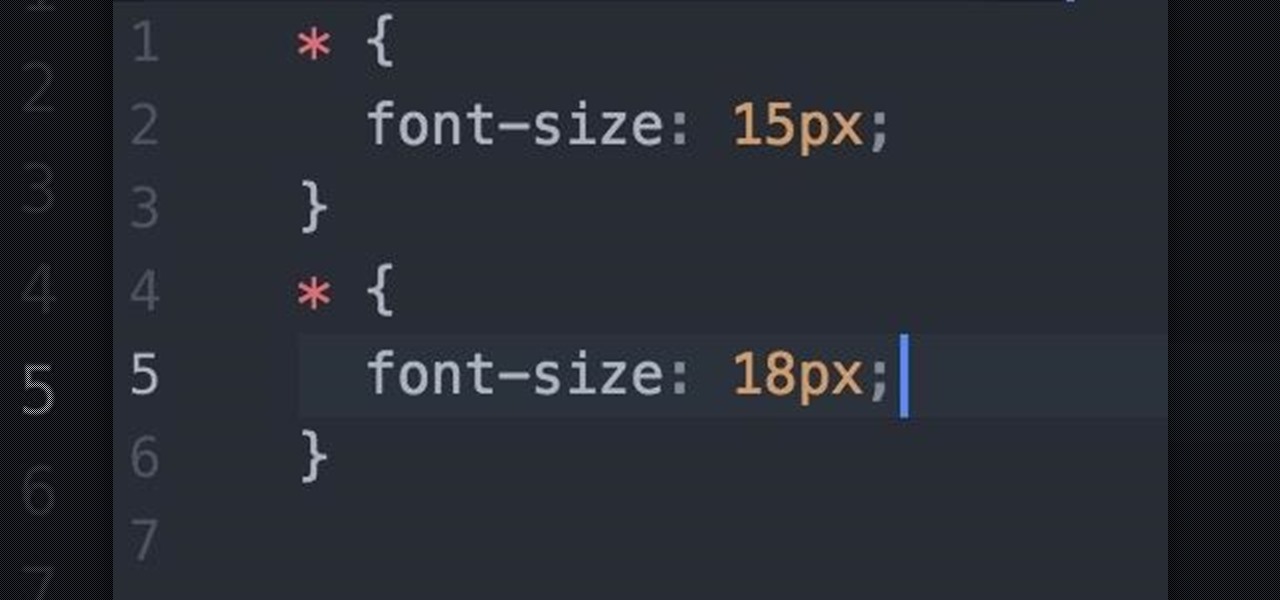
Welcome fellow Null-Byters! I would suggest you watch reading my last tutorial before we begin. In our last adventure, we began making a simple, ugly website. If we want it to make it look good, we should add some styling. But first, we need to understand the basics.
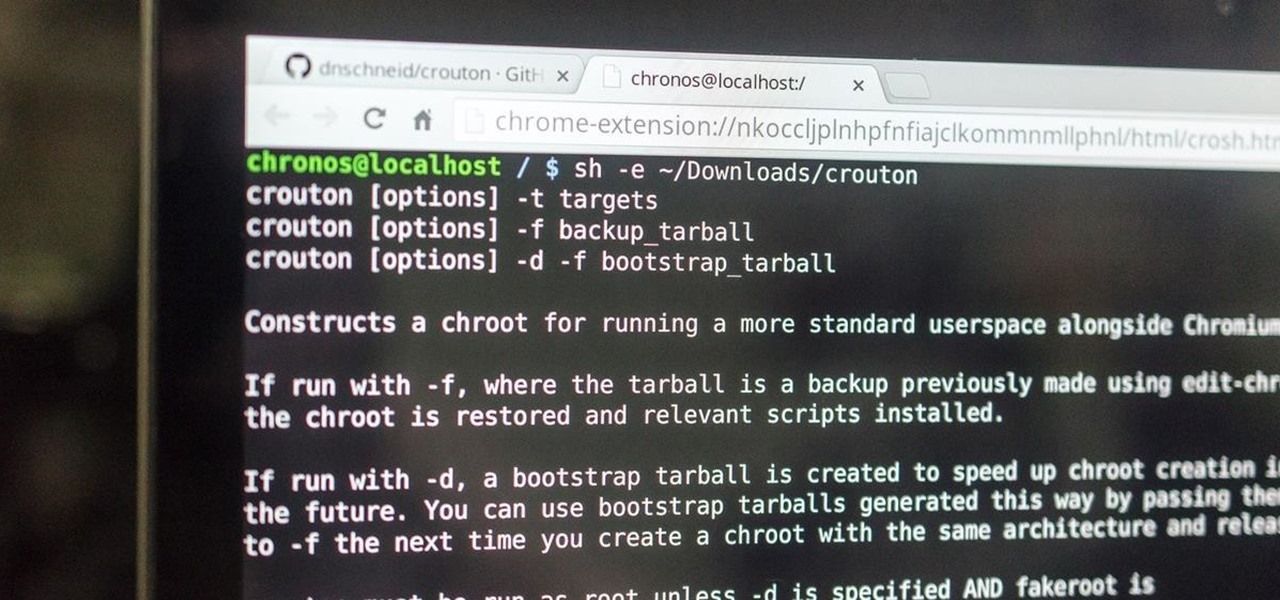
This is my first how-to for this site so feel free to let me know if I can somehow improve! Inspired by the great Jailbroken iDevice and Rooted Android PenTesting tutorials I decided to share how I use my Toshiba Chromebook 2 with Kali Sana.

The horizontal dotted icon in your iPhone's status bar serves as an indicator of your device's network strength. And while it does help provide an approximation of how strong your signal is, swapping it out to display an actual numeric value is a lot more precise and can change up the look of your iPhone (or at least the status bar). The process is quick, painless, and you don't even need to jailbreak your phone.

For many of you, this is common knowledge. But I still regularly see comments posted here and elsewhere asking, "This <AV bypass> doesn't work, because when I upload my payload to VirusTotal...."