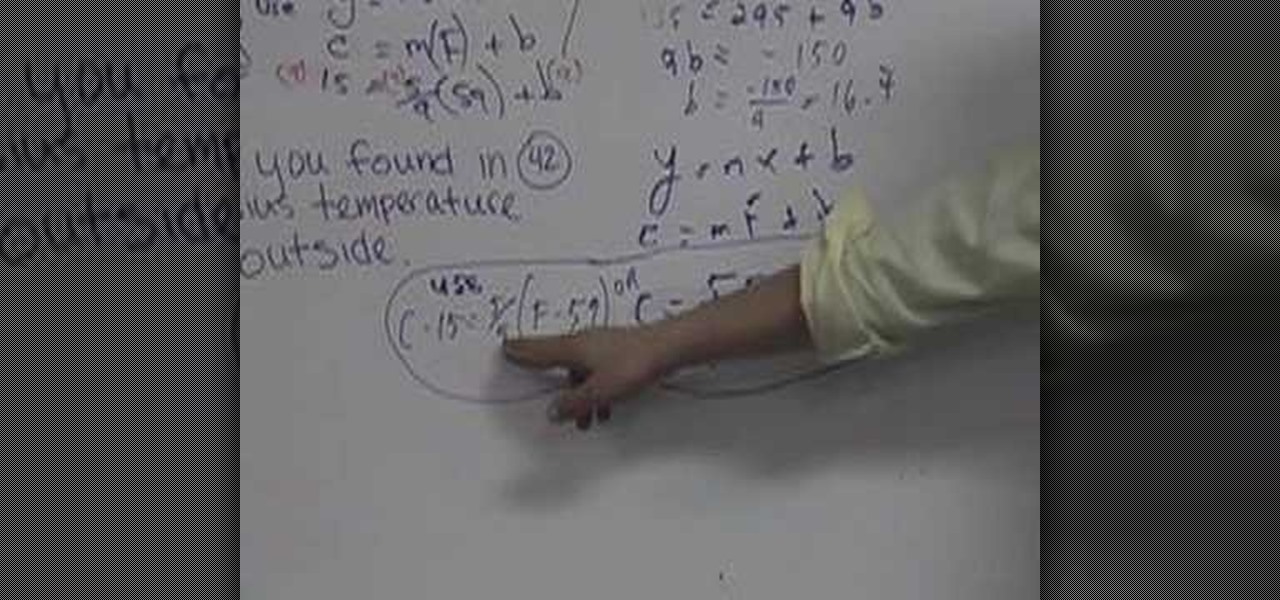Hello, my name is Nicole Valentine and on behalf of Expert Village, I'm here to talk to you about how to coordinate birthday games for a birthday party. Now let's talk about another common game that you can use at a birthday party. And you may recall this game from youth. Paper, rock, scissors. We're going to display this game for you. You ready Robert? Now, let's go over the hand movements. This hand movement represents the paper. Of course it's flat, and it's kind of easy to remember. This ...

In this video series, CGI Animator will teach you how to make a waving flag using the computer program Cinema 4D. Learn all about particles and deformations, planes and cylinders, how to build a leaf, how to run the wind emitter, how to form a flag, and how to integrate all the processes.

In Chinese watercolor paiting, static subjects like cherry blossoms and peach trees never go out of fashion because they represent the teeming life and beauty of nature that most Chinese watercolor artists enjoy representing.

This video shows the method to use differential equations to represent growth. Consider the function y=multiple of C & e raised to kx or Ce^(kx). Differentiating it with respect to x, we get dy/dx=kCe^(kx) or ky. So, the solution of the differential equation dy/dx=ky is Ce^(kx). There are two possibilities in the function y=e^(kx). It can be exponentially growth or decay function. This depends on the value of k. If k is greater than 0 or k>0, we get an exponential growth function. On the othe...

In this video the instructor shows how to choose options on a batch file. In a batch file if you write the command '@ echo off', the person running the batch file cannot see the commands being executed. You can use the 'if' condition to make the program execute either of two commands depending on the condition. While writing the if statements make sure that there is space between the 'if' and the '%' sign. If you write 'shutdown -t 30' command in your batch file, then the batch program when r...

Home improvement expert Danny Lipford helps you figure out a way to get the perfect hole depth when drilling. Watch this video tutorial to see how to make an easy drill bit depth gauge.

To be honest, the Mail app for iPhone had always been somewhat forgettable. It lacked many of the features that made third-party clients like Spark and Edison better, but with iOS 13, the gap between Mail and its competitors is much smaller. Apple updated the layout and added many new features to its native emailing app, and that may be just enough to get you to switch back.

Cross-site scripting is one of the most common vulnerabilities found on the web today, with repercussions of this type of flaw ranging from harmless defacement to sensitive data exposure. Probing for XSS can be tedious and time-consuming for an attacker, but luckily there are tools available to make things a little easier, including Burp Suite, Wfuzz, and XSStrike.

After gaining access to a root account, the next order of business is using that power to do something more significant. If the user passwords on the system can be obtained and cracked, an attacker can use them to pivot to other machines if the login is the same across systems. There are two tried-and-true password cracking tools that can accomplish this: John the Ripper and Hashcat.

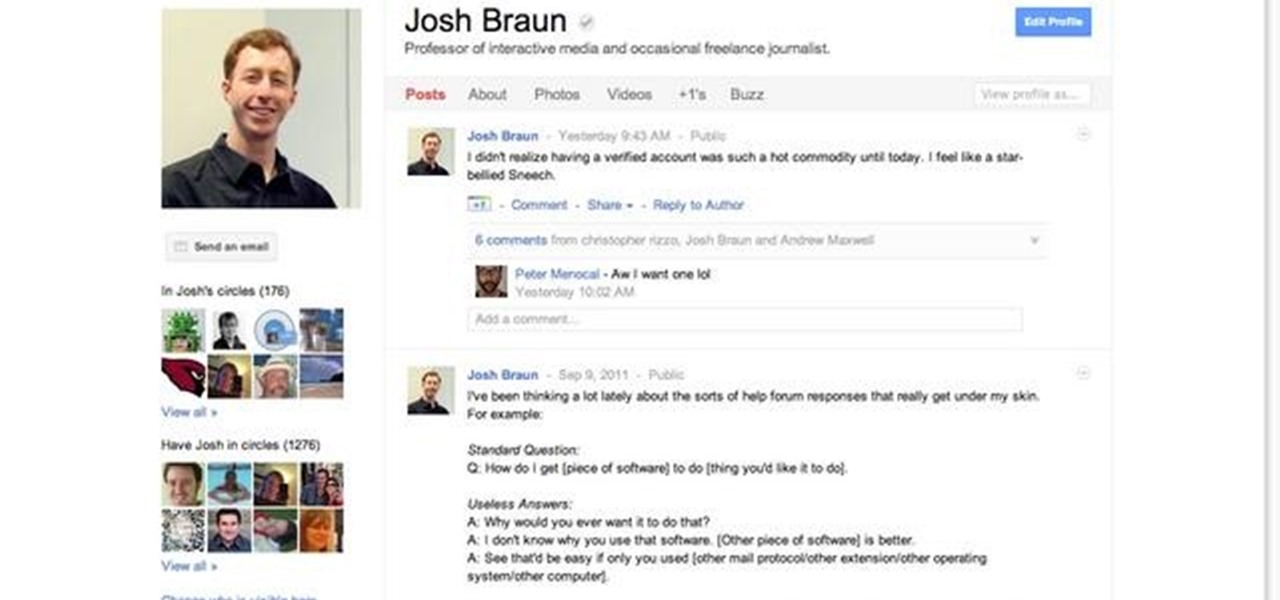
The profile pages on Google+ allow you to represent yourself in unique ways to other Google+ users. If you want to edit the information displayed on your Google+ profile, such as the title that appears under your name or who is visible in your circles.

AirPlay is one of the coolest new features in iOS 4.2, and represents the next step in Apple device networking. It allows you to "throw" content from one iDevice to another, including the iPad, iPhone, and AppleTV. This video will give you a quick primer on how it works.

The Microsoft Kinect represents its attempt to steal the Wii's thunder, and it work pretty dang well. Watch this video for a guide to plugging the Kinect into your XBox 360 and setting up your gaming area so that you'll be able to play it.

Iron Man, and to a lesser extent it's sequel, represent the best of the new comic-book-movie boom and have rejuvenated the popularity of one of Marvel's most interesting characters. Do you want to make a Tony Stark costume, or dress someone you know in one for a film or party? This video will show you how to make one of the coolest and most important parts of the Iron Man ensemble: the repulsor arm ray gun.

This is a video tutorial in the Education category where you are going to learn how to describe chemical formulas. A chemical formula represents the actual number of atoms of each element within a molecule. Different visual representations of molecules include the ball and stick three dimensional model, a line drawing that represents the structure in two dimensional terms, and a shorthand used by organic chemists. If a molecule has 4 green atoms and 2 orange atoms, the ratio of green to orang...

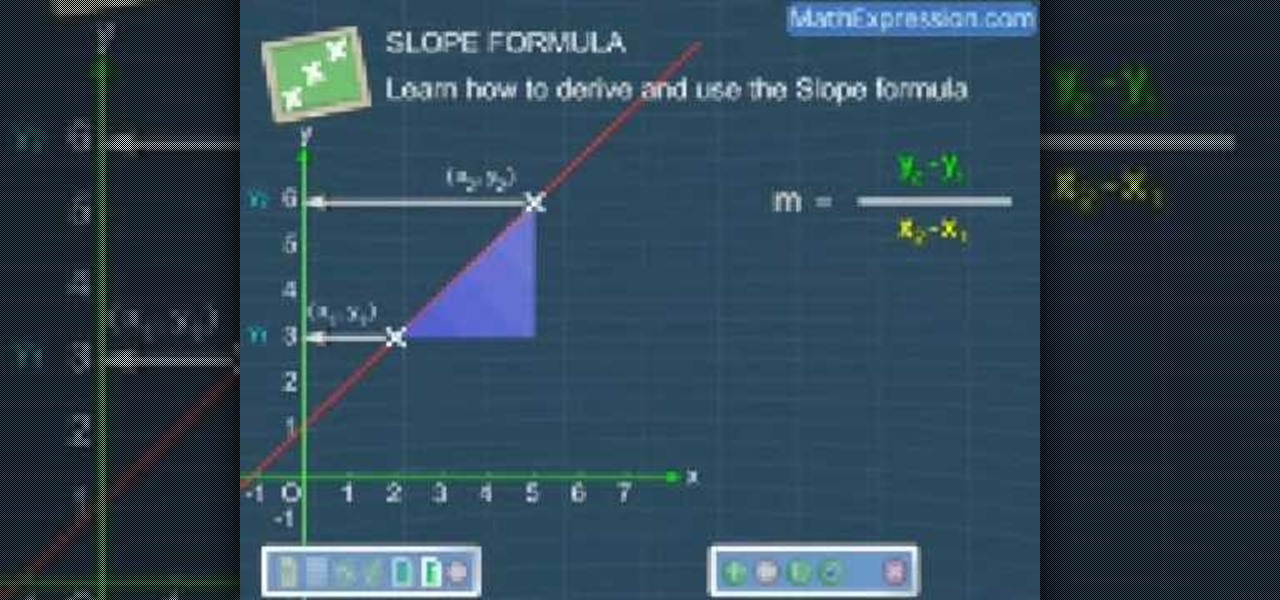
In this video, we learn how to derive and use the slop formula. The slope of a line is equal to change in y divided by the change in x. First, put the first point on the coordinate point. Then, represent the X and Y by X1 and Y1. Then, put the second point on the plane, representing the coordinates with X2 and Y2. Now, with these two points, draw a straight line and derive the formula from here. The change in X will be from X1 to X2. Now, replace that with the change in X and do the same for ...

In this video tutorial, viewers learn how to equip their golf bag in World Golf Tour. Begin by visiting the World Golf Tour website and enter the main menu. Then click on My Settings and select My clubs. Here, users are able to select a club that they want to play with for the next round. The upper blue section represents the clubs that are currently in your bag. The lower section represents all the clubs that you own, sorted by type. When finished editing and customize your club selection, c...

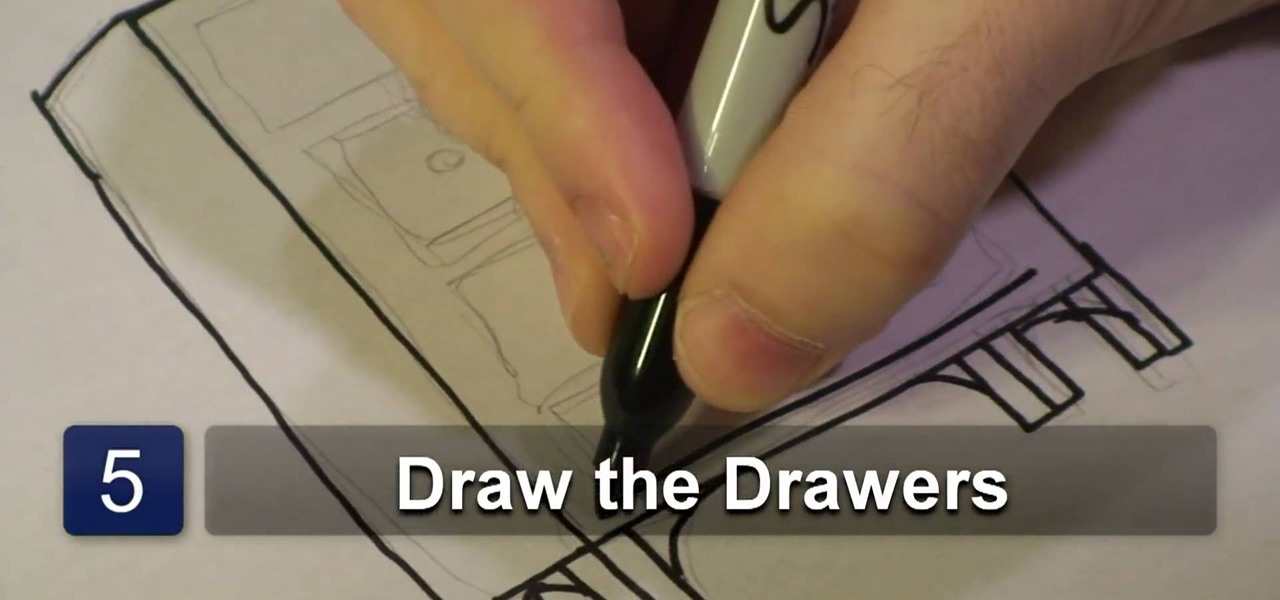
In this video tutorial, viewers learn how to draw a dresser. Begin by drawing a vertical rectangle to represent the font panel. Then add a long rectangle on one side to represent the side panel. Now add 4 pairs of legs under the dresser and add leg supports by drawing an arch between each 2 legs. For the drawers, draw 4 long horizontal rectangles on the front panel and add some doorknobs on each drawer. Finish by adding any extra detail. This video will benefit those viewers who enjoy drawing...

This video illustrates how to draw a fantasy unicorn. Here are the following steps: Step 1: First of all take a sheet of paper and pencil and start drawing the head in a cone shape with the cone having round edge ,this cone represents the head.

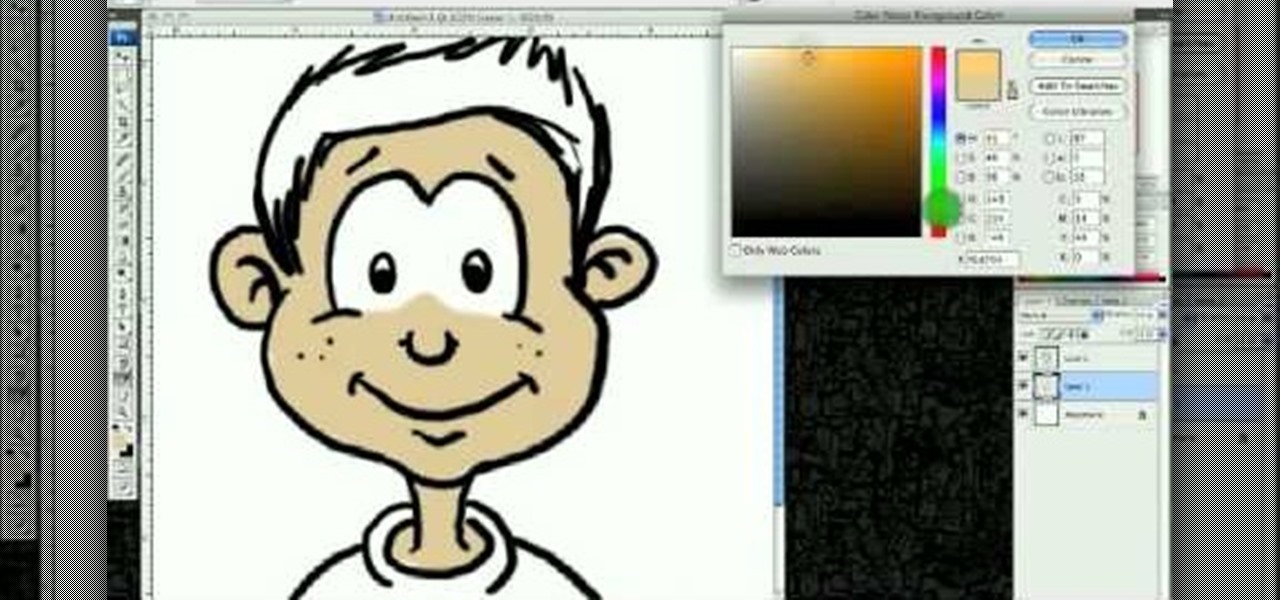
This video illustrates how to draw a cartoon boys face in Adobe Photoshop.Here are the following steps:

This video illustrates how to draw Bowser from Bowser's inside story. Here are the following steps: Step 1: First of all take a sheet of paper and pencil and start drawing the character.

This video illustrate us how to draw manga characters.Here are the following steps:Step 1:Take a sheet of paper and pencilStep 2:Start by drawing a circle ,this will represent the face of the manga. now draw the eyes ,nose lips of the character with sharp lines to represent action on the face.Step 3: Now draw the middle part of the body and it should be in perfect shape.Step 4: Now draw hands of the character with waves on the hands to show masculine look.Step 5: Now draw the feet and legs.St...

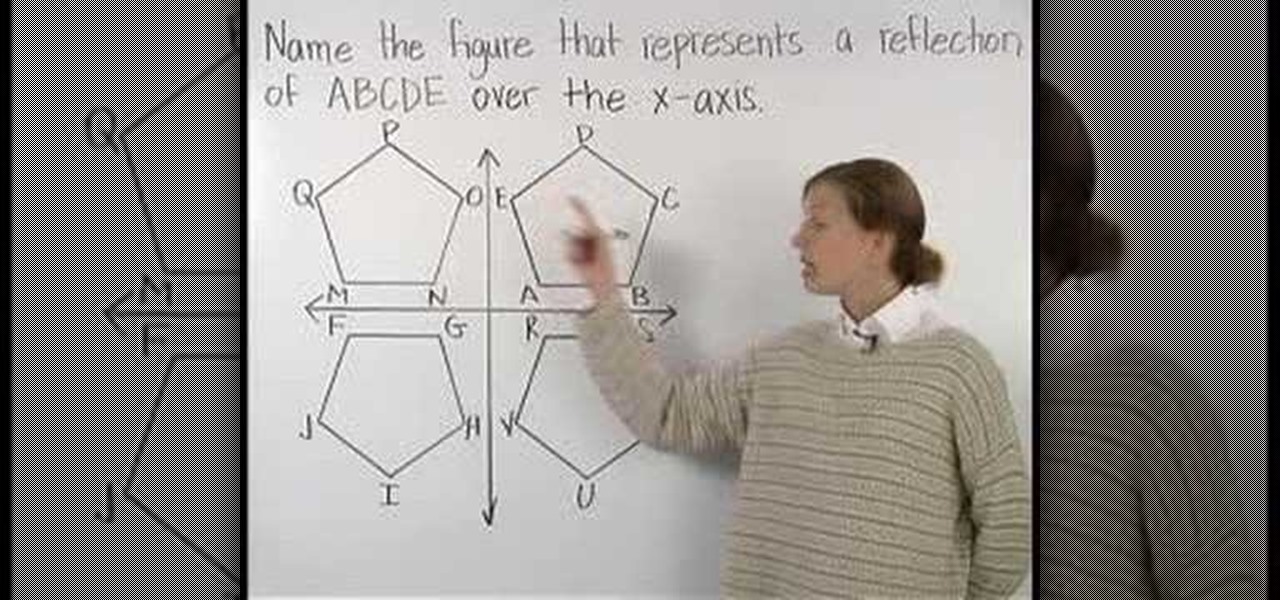
The tutorial is part of a full lesson of pre algebra. This video teaches you what reflection is as a mathematical term. In the beginning of the video, the video maker draws 4 shapes labeled MNOPQ, ABCDE, FGHIJ and RSTUV. The first question in the video asks to "Name the figure that represents a reflection of ABCDE over the X-axis." The woman in the video repeats the question, stating the horizontal line is the X-axis and asks for the reflection image. She puts her hand on ABCDE and flips her ...

In this video the instructor shows how to do temperature conversions using y = m*x + b. Now if Celsius is represented by the variable C and Fahrenheit is represented by the symbol F, you can replace then in the previous equation in place of the variables x and y giving you the equation C = m*F + b. Now to solve for the values of the constants m and b you need to have values of two sample temperatures in both Celsius and Fahrenheit. Take the first sample and substitute in the above equation gi...

Essortment teaches you how to understand guitar tabs. There are six lines that represent a string: E, A, D, G, B and E. Numbers are written on the strings representing fret tabs that tell you where to fret on each string. Also learn how to read a cord which is all the numbers placed at the same time. Numbers on top of each other is a string and lined up means to strum. These are the basics to reading a guitar tab so when you see a tab you are able to play and understand.

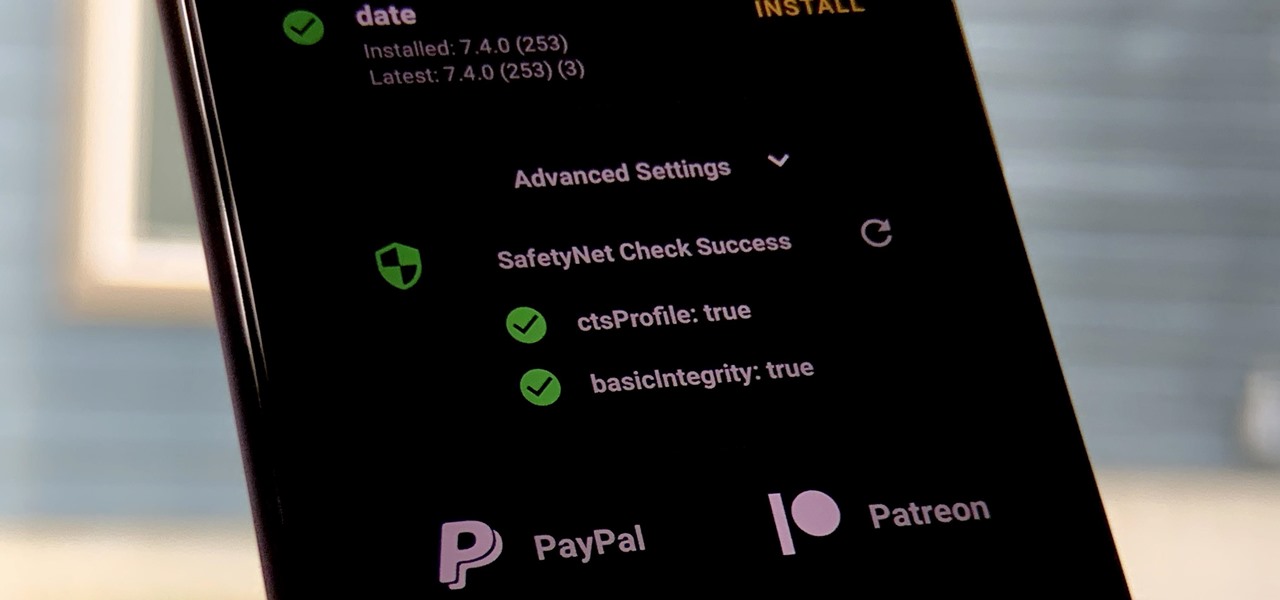
One of the longest-running cat and mouse games in Android has to be that of Google's SafetyNet feature and specific apps that can trip the flag. Many developers have resorted to using Magisk to create their modules since it can systemlessly pass SafetyNet in most cases. However, EdXposed is having some issues passing SafetyNet right now, which affects more than just your mods.

If you've ever needed to prove you have remote access to a device, or simply want a way to convince someone their computer is haunted, SSH can be used to make a device begin to show signs of being possessed.

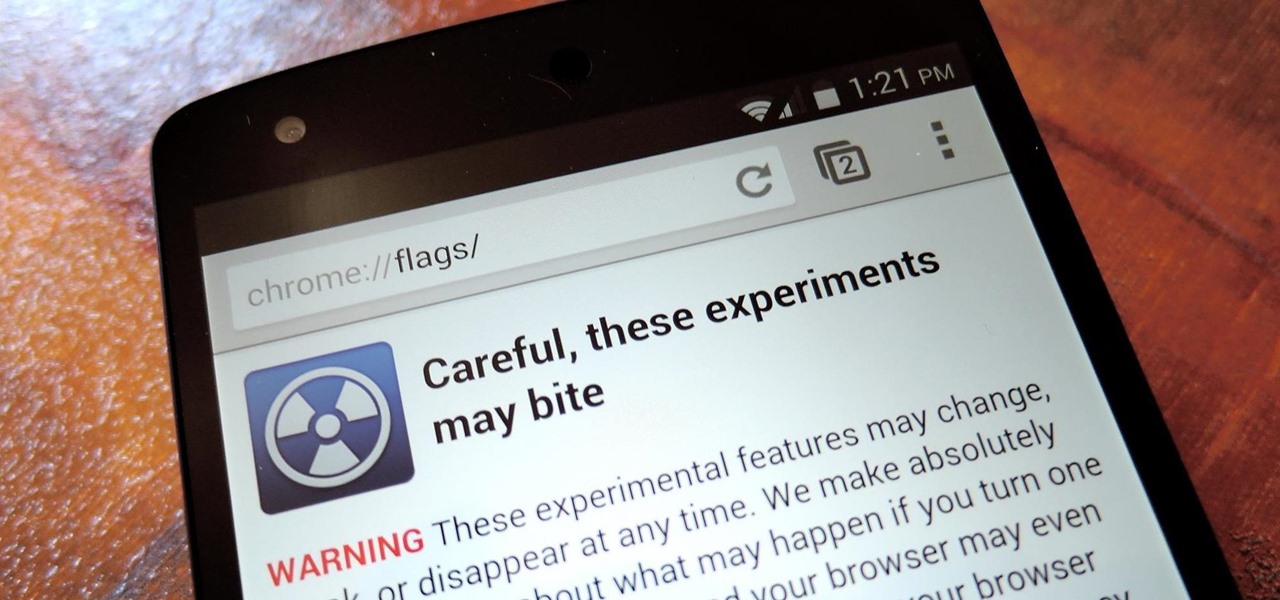
Dark themes are all the rage these days, and both Android and iOS have system-wide versions. Many big-name apps and device manufacturers have already jumped on board the night train, and Google Chrome is no different. But the Chrome mobile browser offers various ways to enable its dark theme.

Developers can now publish augmented reality experiences that are viewable through the experimental version of Chrome and ARCore.

Rovio created one of the first mobile gaming hit franchises with Angry Birds, so perhaps it is surprising that, aside from a promotional mini-game developed with Zappar, the company has yet to adapt the game to augmented reality via ARKit.

Macs are generally highly power efficient due to, in part, the optimized sleeping schedule with OS X. Yet in certain scenarios, you might not want your Mac to go to sleep: downloading a huge file, reading a book, reviewing a spreadsheet, analyzing some content on the screen... the list goes on. To resolve this, you can go to System Preferences and mess with the settings, but this can be an annoying process if you need to do it often.

Hello, everyone! If you haven't read the recent announcement on the official release of the Null Byte suite, I suggest you do so. This is going to be a quick tutorial on how to download and install the suite so you can see our communities genius. So, let's get started!

Independence Day is right around the corner, and that means three things: fireworks, cold beer, and great food. I always love to cook festive foods for the Fourth of July, and I don't just mean the classics, like grilled chicken and brats. I mean foods that celebrate the Stars and Stripes: foods that are red, white, and blue.

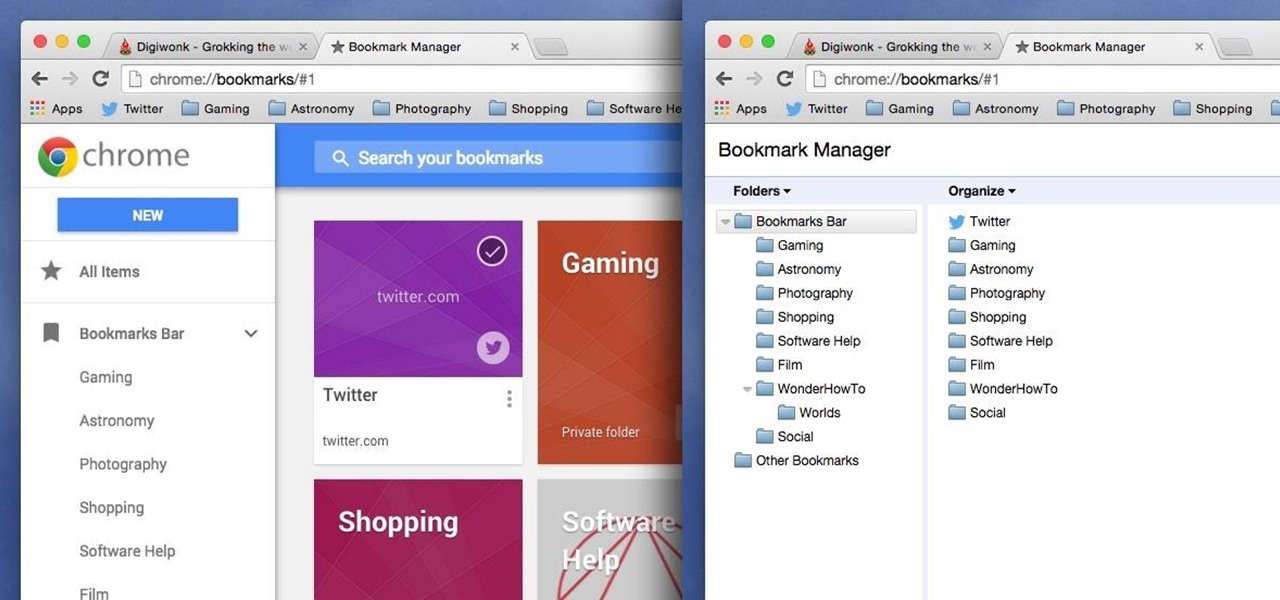
Chrome has been pushing out a lot of new changes lately, but not all of them are as good as they think they are. Earlier this year, there was an update that changed how user profiles worked, which made it harder to actually switch profiles. Luckily, there was a way to get back the old profile management interface, but now there's another "improvement" that you might want to change—Chrome's new Bookmarks Manager interface.

With the release of Jelly Bean, Chrome became the default web browser on Android. The wildly successful desktop browser was now fully entrenched in the world's largest mobile operating system.

Welcome back, my novice hackers! I have tried to emphasize throughout this "Hack Like a Pro" series that good reconnaissance is critical to effective hacking. As you have seen in many of these hacks, the techniques that we use are VERY specific to the:

One of the lesser known features brought along by the roll-out of Android 4.4 KitKat is the ability to screen record from within the device. This features isn't overtly obvious, nor is its implementation the most streamlined, but if you were ever looking for a way to capture video of what's happening on your screen, this is now the best way to do it.

Welcome back, my fledgling hackers! One of the first issues any hacker has to address is reconnaissance. Before we even begin to hack, we need to know quite a bit about the target systems. We should know their IP address, what ports are open, what services are running, and what operating system the target is using. Only after gathering this information can we begin to plan our attack. Most hackers spend far more time doing reconnaissance than exploiting.

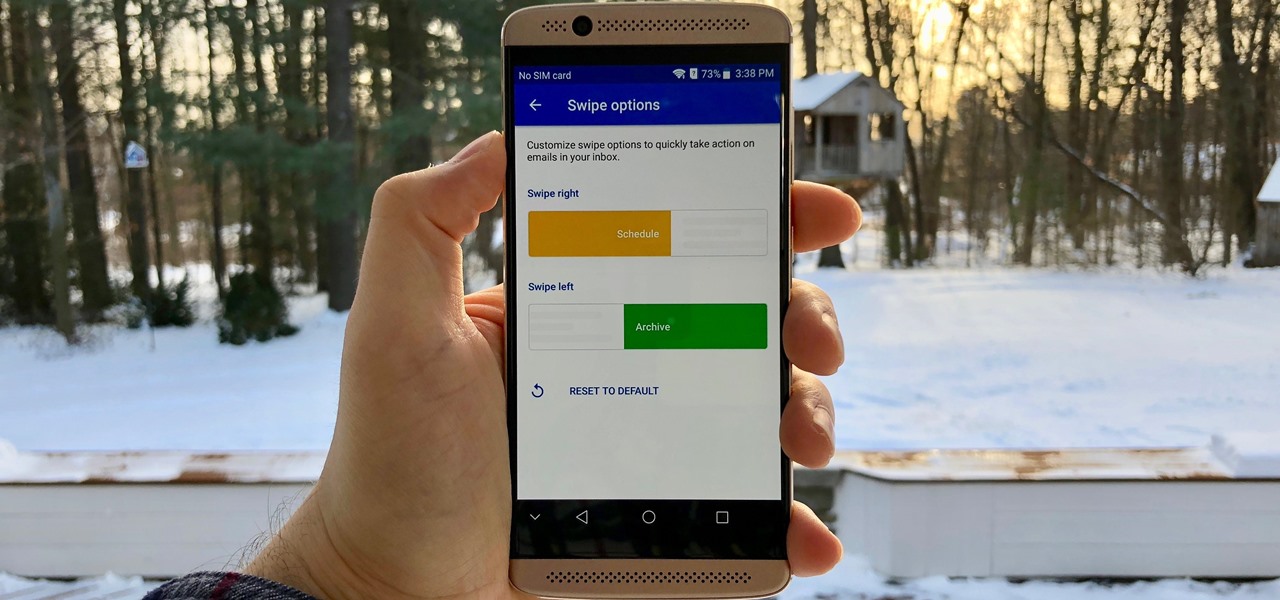
Swipe actions are an integral multitasking feature of any good email client, and Outlook is no exception. The application allows for two swipe actions at a time, but offers seven total options for those actions. We'll show you how to choose which actions go with which swipes to best tailor the app to your needs.

An attacker with shell access to a Linux server can manipulate, or perhaps even ruin, anything they have access to. While many more subtle attacks could provide significant value to a hacker, most attacks also leave traces. These traces, of course, can also be manipulated and avoided through methods such as shell scripting.

Ever wanted to communicate with another driver on the road, but just didn't know how? Sure, you could flag them down by waving or honking at them, but that assumes that they're in close proximity, that you have a unobscured path, and that they're paying attention. And if you're in a fit of road rage, flagging them down probably isn't the best idea for either of you.