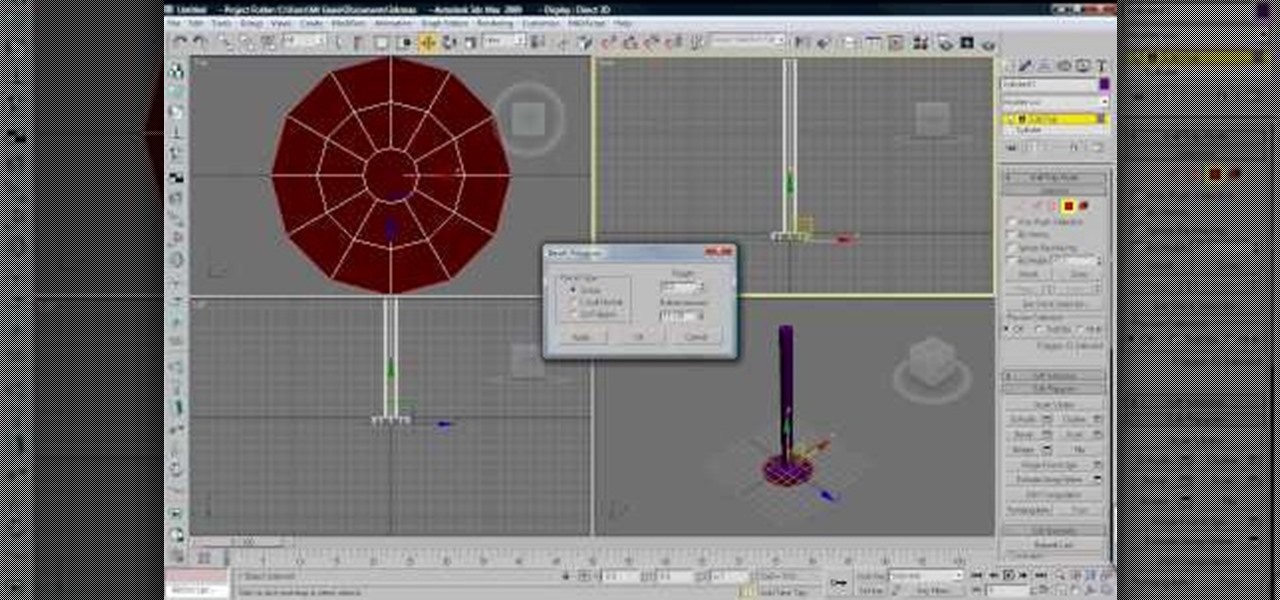
Cloth is an essential part of almost any 3D modeling project involving people. This video will show you how to properly use the cloth modifier in 3D Studio MAX to create the waving, tarnished American flag shown in the thumbnail. This tutorial does NOT feature Reactor, the in-program physics engine included with 3DS MAX, only the actual 3D Studio MAX cloth modifier.
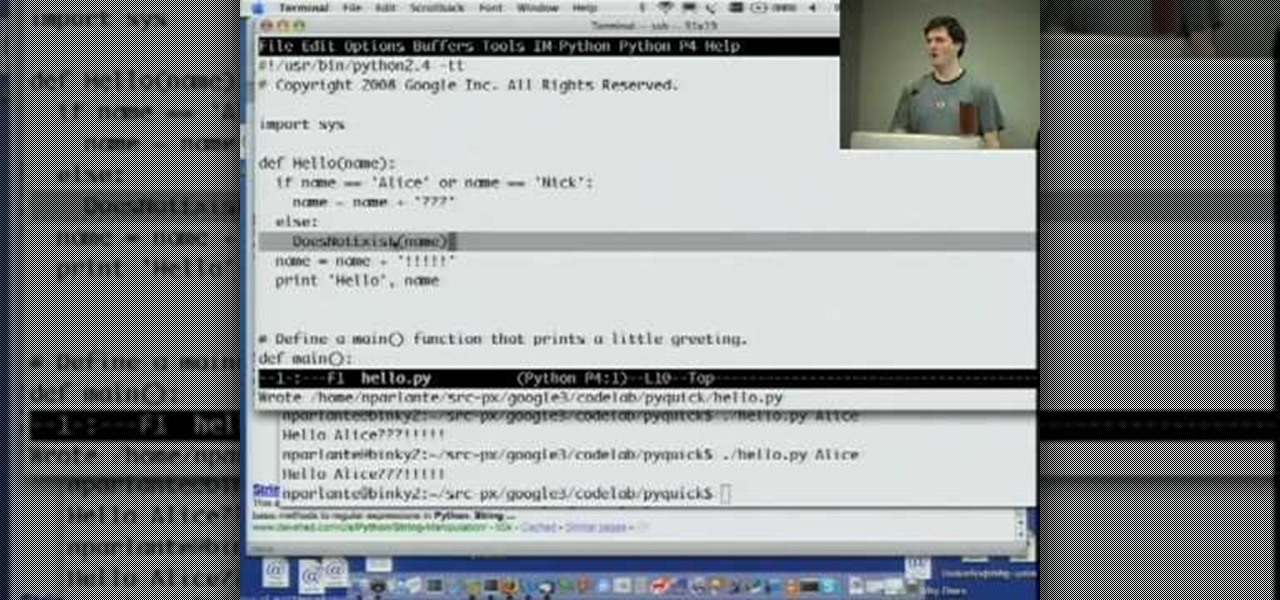
Welcome to Google's Python Class – a seven-segment, two-part free virtual class for people with a little bit of programming experience who want to learn Python. The class includes written materials, lecture videos, and lots of code exercises to practice Python coding. The first exercises work on basic Python concepts like strings and lists, building up to the later exercises which are full programs dealing with text files, processes, and http connections. The class is geared for people who ha...

Azimuth is simply the angle of an object in the sky along the horizon. Yes, it's spherical trigonometry but it's not difficult! Check out this video and in just a few minutes you will be able to solve azimuth problems on your own.

EternalBlue was a devastating exploit that targeted Microsoft's implementation of the SMB protocol. Metasploit contains a useful module that will automatically exploit a target, as long as it's vulnerable. But what if we wanted to exploit this vulnerability without Metasploit holding our hand? It can be done using a Python file to exploit EternalBlue manually.

In the latest update to the ongoing Meta Company patent infringement case, the court has responded to a request from the defendants, and the answer isn't good news.

Cracking the password for WPA2 networks has been roughly the same for many years, but a newer attack requires less interaction and info than previous techniques and has the added advantage of being able to target access points with no one connected. The latest attack against the PMKID uses Hashcat to crack WPA passwords and allows hackers to find networks with weak passwords more easily.

If you've ever made graphs and charts, you know it can be a struggle to represent a large amount of data. It's something that just doesn't work very well on a flat surface. In virtual and mixed reality, however, the data can exist all around you.

In the Harry Potter world, there was a character by the name of Beedle the Bard, who told a story about witnessing the three Peverell brothers building a bridge out of magic and successfully crossing a very dangerous river that had claimed many lives.

PowerPoint 2008 for Mac can help you turn boring old bulleted lists into something nobody would forget. With SmartArt graphics in PowerPoint you can now make your bullet lists pop using pre-formatted charts, graphs, and more. The Microsoft Office for Mac team shows you just how to make a bulleted list more visual in this how-to video.

Dull and drab bulleted lists are no longer necessary with the help of PowerPoint 2008 for Mac. When you make a bullet list in PowerPoint, you can now transform those boring text charts with actual visual charts and graphs and more. The Microsoft Office for Mac team shows you just how to convert text to a SmartArt graphic in this how-to video.

Micro misters allow for low volume of water over a wide area. They give good moisture coverage. Systems can be pulled up, changed and made into what you need it to be. Keep potted plants separate from other plants. They should have their own system. There is a system to encourage growth of root systems of various plants. Shrubs get two emitters in case one clogs up, the plant still has moisture. Having the water at the base of the plant limits weed growth. There is a temporary system to get t...

Fourth of July is near, which means we'll soon be seeing an influx of red, white, and blue flags, banner, and of course patriotic sweets for those who indulge in the foodie side of the holiday.

Without looking, peeking, or even cheating, you will be able to figure out who will win in a virtual game of rock-paper-scissors.

Buddha doesn't just sit on a lotus flower because it's kind of fun sitting on a flower throne. In many Asian traditions, the lotus flower represents sexual purity and non-attachment, which are the core tenets of Buddhism.

With this two-part painting lesson, you'll learn how to paint "Three Friends of Winter," a traditional Chinese motif depicting pine, plum and bamboo — three plants admired for their beauty and, in Taoism, Buddhism and Confucianism, said to be representative of good virtue.

Connecting the flags on eighth notes, sixteenth notes, etcetera, is very important to neat, legible music. This how to video teaches you when to connect the flags in the music notes. Learn how to read and write music better with this music theory tutorial.

Dr. Aaron Katz explains what red flags men need to watch out for that could indicate prostate cancer and also explains what the PIN test is and how it relates to prostate health.

The soles of your feet represent a map of your body. There are over 7000 nerve endings in your feet.

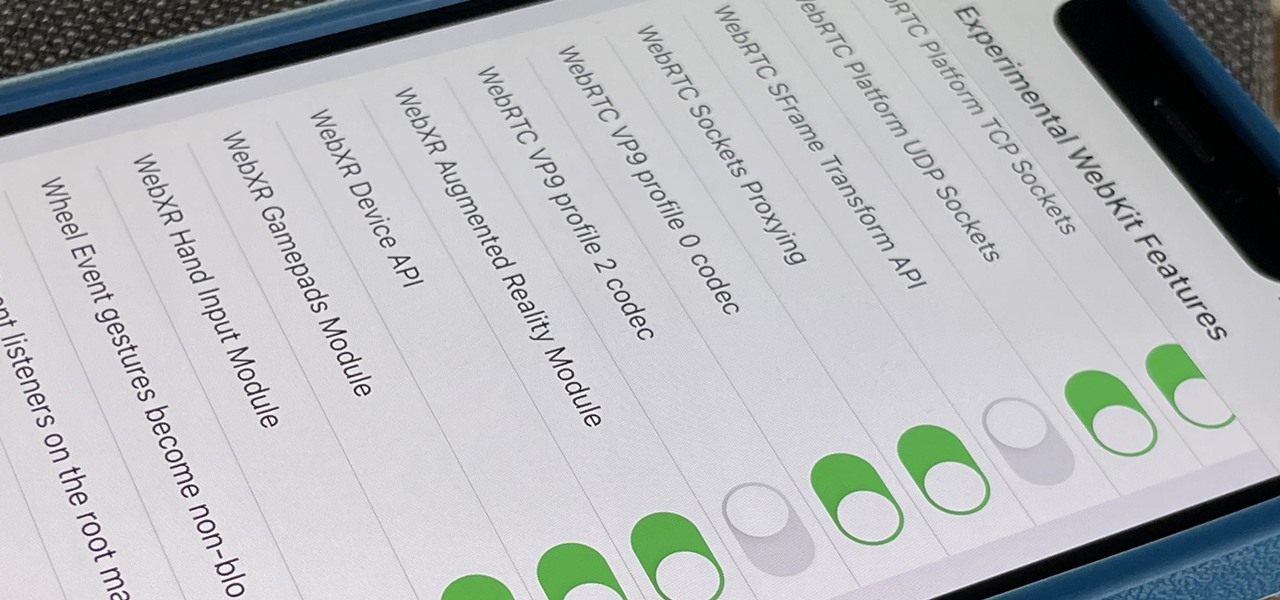
Safari's advanced experimental features give you access to new browser initiatives, upcoming web tools, element changes, behavior adjustments, and other preliminary feature tests in development by Apple. If you use them on your iPhone, you can either improve your Safari experience or wreck it. Resetting the flags provides a fresh start.

When it comes to iOS beta updates, developers get their updates first, and once they do, public testers play the waiting game. Sometimes Apple releases the public version three hours later. Other times it waits 24 hours. It's a roll of the dice almost every time. As for iOS 13.4 public beta 2, it's the latter case, coming exactly one after developer beta 2.

Web applications are a prime target for hackers, but sometimes it's not just the web apps themselves that are vulnerable. Web management interfaces should be scrutinized just as hard as the apps they manage, especially when they contain some sort of upload functionality. By exploiting a vulnerability in Apache Tomcat, a hacker can upload a backdoor and get a shell.

Gathering information on an online target can be a time-consuming activity, especially if you only need specific pieces of information about a target with a lot of subdomains. We can use a web crawler designed for OSINT called Photon to do the heavy lifting, sifting through URLs on our behalf to retrieve information of value to a hacker.

When it comes to customizing Android, there's no better way to make it your own than by installing a custom ROM. You gain new features that were not accessible on the stock firmware that came with the phone, and you get complete control over how your system looks and feels. But there's definitely a learning curve.

Microsoft Office files can be password-protected in order to prevent tampering and ensure data integrity. But password-protected documents from earlier versions of Office are susceptible to having their hashes extracted with a simple program called office2john. Those extracted hashes can then be cracked using John the Ripper and Hashcat.

With the number of web applications out there today, it comes as no surprise that there are just as many vulnerabilities waiting for hackers to discover. Finding those vulnerabilities can be a difficult task, but there are plenty of tools available to make the process easier. While it won't help find any zero-days, web scanners such as Uniscan will detect common vulnerabilities.

The ability to execute system commands via a vulnerable web application makes command injection a fruitful attack vector for any hacker. But while this type of vulnerability is highly prized, it can often take quite a bit of time to probe through an entire application to find these flaws. Luckily, there is a useful tool called Commix that can automate this process for us.

Analysis of photographs and social connections can be a huge component of social engineering. Understanding who a person is, as well as who they know, can establish links within a company. This information could be used by hackers to execute elaborate social engineering attacks.

With the release of the Mirai source code, botnets are back in a big way. In the early days of botnets, zombies (infected hosts) would report to IRC (Internet Relay Chat) channels for CNC (command and control) instructions. Modern botnets have evolved, but they continue to use the same concepts as their predecessors.

In the last iteration of how to train your python, we covered basic string manipulation and how we can use it to better evaluate user input. So, today we'll be covering how to take user input. User input is very important to scripting. How can we do what the user says if we can't tell what the user wants? There are multiple ways to take input, we can give the user a prompt and take input from them directly, or we could use flags/switches, and take their input before the script is even execute...

In the Apple's iOS beta 3, we were introduced to a new iCloud Drive feature, an option to disable QuickType, time indicators for Recently Deleted pics, and a way to keep "self-destructing" media.

This video represent a bit of a digression for the Google Webmaster series of videos, spotlighting a cool Google-designed Android app and how to use it. The app in question is My Tracks, a free app that allows runner, bikers, and other distance exercisers to keep track of their distance, pace, splits, elevation, and all sorts of other information automatically with their phone. It will even create and save a map of your course, which you can then share online.

In this video tutorial, viewers learn how to draw a rose garden. Begin by marking the locations of the objects. Then draw the rose bushes around the garden pathway. Draw the lines with some cross hatching. This will give the bushes some form and feel. Add some circular boxes in the bushes to represent the roses. On the pathway, add some grass on the edges and stones on the path. In the center, draw a center piece and draw an arch over it. Finish by adding details to the roses. This video will...

This video shows the method to solve word problems using proportions. In the given problem, we have to find the time taken by a person to type 390 words if the person takes 1 minute to type 30 words. This can be solved using proportions. We take two fractions which are equal. We type '30 words' in the numerator of the first fraction and 1 minute in its denominator. This fraction must be proportional to the second fraction. The second fraction has '390 words' in the numerator and the variable ...

Learn Newton's laws of motion from the utmost authority on aeronautics -- NASA aka National Aeronautics and Space Administration. See how Newton's laws apply to aircrafts from the powerhouse of space exploration. They talk about thrust force as applied to aviation.

The powerhouse of space exploration, NASA (National Aeronautics and Space Administration), sheds light on Newton's laws of motion as pertaining to drag force on aircrafts. This is a great source for any aeronautics major. The infamous government agency breaks drag down for you.

Camera angles can be expressed in both physical and psychological terms. The first episode presents the physical angles: low-angle, high-angle, and dutch angle.

Everybody's favorite food is pizza. But not everybody knows how to actually make a pizza, which is practically a sin. And this "margherita" style pizza is a great one to learn, full of Italian simplicity— red tomato sauce, mozzarella cheese, and green basil— all the colors of the Italian flag. Check out the recipe for this delicious margherita pizza.

Figure out the 10th puzzle, Apollo, in Assassin's Creed 2. Image 1: Highlight the lunar lander just down and to the left of the moon. Puzzle wheel: Another linked-ring rotation puzzle. Your job here is to align all the channels; do this by moving the fifth ring to the left six times, the second ring to the left four times, the fourth ring to the right three times and the third ring to the left five times. Then snap the first ring into place. Image 2: Move the cursor down between the flag and ...

Why have a plain old barbecue when you can host an Oktoberfest? Make it authentic with these tips. You Will Need

Sure, you can go online and send the first flowers you see, but a little thought and planning will go a long way toward impressing her. Sure, you can go online and send the first flowers you see, but a little thought and planning will go a long way toward impressing her. You will need a friend or relative of the recipient. Send her favorite. If she’s ever mentioned a favorite flower, buy that. You’ll get bonus points for listening to her. If you have no clue, ask a friend or relative of hers ...