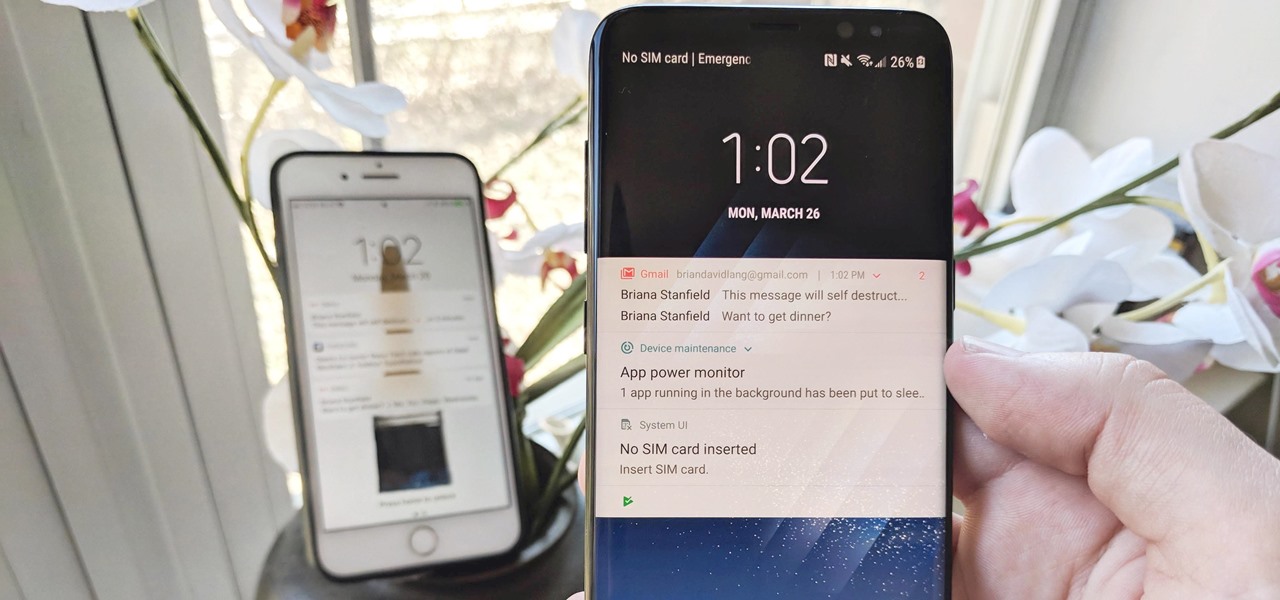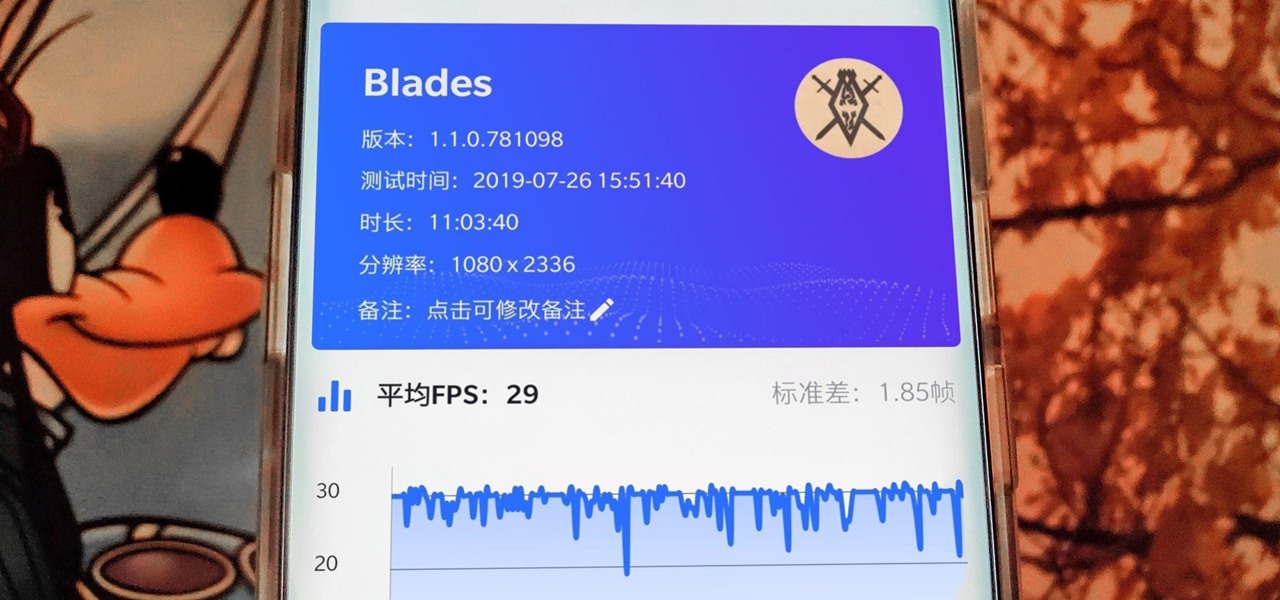
When you're gaming on your Android phone, does it sometimes feel "slow" and you can't figure out why? That means a drop in performance, which is when the frame rate dips, causing some noticeable stutters and lag. There's not really a way to know what's wrong unless you made the game yourself. But on the bright side, you can check any game's FPS with a simple tool.

If you've read or watched anything Harry Potter before, you know friendship and teamwork are huge parts of the story. The same goes for Harry Potter: Wizards Unite, with its "Wizarding Challenges." Here, you can tackle Fortresses full of Foes alone, but why do that when you can battle with up to four other friends at once? Here's how it all works on Android or iOS.

For many, the stock version of Android is often considered the epitome of what the operating system should look and feel like by default. It's clean and clear of unwanted extra apps that come pre-installed with the system, provides a fluid and fast user experience, and runs on just about any device that has an unlocked bootloader to install a custom ROM with the stock version ready to go.

One of the most powerful features when editing videos with Enlight Videoleap is the keyframe tool, which allows you to add custom transitions, animate text, granularly adjust audio, move video clips across the frame, supplement effects, and more. If you want your video to change color over time or for captions to move across the screen, use keyframes in combination with Videoleap's other tools.

While the Galaxy S10 is a beautiful phone, its software isn't for everyone. One UI makes huge strides toward undoing the mess known as TouchWiz, but for purists, it's still not quite on par with stock Android. Fortunately, the beauty of Android is you can change this with a few apps.

Business hours and addresses change, but they're not always updated on Yelp by business owners for the rest of us to see. Showing up when a business is closed or going to the incorrect address is a major annoyance, which is why the company allows us, the customers, to help update business information through the Yelp mobile app on iOS and Android. If owners won't do it, somebody has to.

With the number of web applications out there today, it comes as no surprise that there are just as many vulnerabilities waiting for hackers to discover. Finding those vulnerabilities can be a difficult task, but there are plenty of tools available to make the process easier. While it won't help find any zero-days, web scanners such as Uniscan will detect common vulnerabilities.

The gym can be pretty distracting. With the slamming of weights and pieces of equipment, loud music blasting through the speakers, and plain old grunting, it can be challenging to focus on your workout. However, with your just your phone, you can not only eliminate these distractions but make the most of your time there.

Waking up your Apple Watch to see "your heart has shown signs of an irregular rhythm suggestive of atrial fibrillation" might come as a shock. While your watch can send you warnings if it detects a fast or low heart rate, those messages are pretty vague, while the abnormal arrhythmia alert can downright scary. So what should you do if you receive one of these AFib notifications?

You're minding your business when your Apple Watch taps you. To your surprise, the watch claims your heart rate dipped abnormally low. The news might come as a shock — especially if you have no history of a heart condition — but before you panic, you should take the time to fully understand what this alert is really saying and what you can and should do about it.

On Tuesday, the smartglasses startup known as North finally took the wraps off its Focals product, but in a very unique way: The team simply opened a couple of stores and invited the public in.

One of the best ways to improve your skills as a hacker is to learn to combine different avenues of attack to achieve success. What if it were possible to get a victim to connect to our machine and execute a chosen payload on our behalf? This is indeed possible with the almighty Metasploit and the aid of a technique known as command injection.

The Pixel 3 XL versus Galaxy Note 9. Stock Android versus Samsung Experience. When I began this comparison, I thought the Pixel 3 XL would be unfairly outmatched. But after looking at the specs side-by-side, you'll see a different picture. This year, Google delivered a worthy alternative to Samsung's best offering.

Besides the Apple vs. Samsung competition, few battles are as vocal as the battle between the best Pixel and best iPhone. This year, it's the Pixel 3 XL and iPhone XS Max, two phones that are equipped with minor hardware updates from their predecessors, though both showcase significant OS-level improvements.

The battle between the Pixels and the iPhones has been heating up over the last few years, and this year's bout is the best one yet, with Google's Pixel 3 taking on Apple's iPhone XS.

With the new iPhones coming out, many see the current mobile market as just another epic battle between Samsung and Apple. But let's not forget there are many other phones that run Android. And when you start to sift through the specs, one stands out as a competitive alternative to the iPhone XR, the LG G7 ThinQ.

Web 2.0 technology has provided a convenient way to post videos online, keep up with old friends on social media, and even bank from the comfort of your web browser. But when applications are poorly designed or incorrectly configured, certain flaws can be exploited. One such flaw, known as CSRF, allows an attacker to use a legitimate user's session to execute unauthorized requests to the server.

After gaining access to a root account, the next order of business is using that power to do something more significant. If the user passwords on the system can be obtained and cracked, an attacker can use them to pivot to other machines if the login is the same across systems. There are two tried-and-true password cracking tools that can accomplish this: John the Ripper and Hashcat.

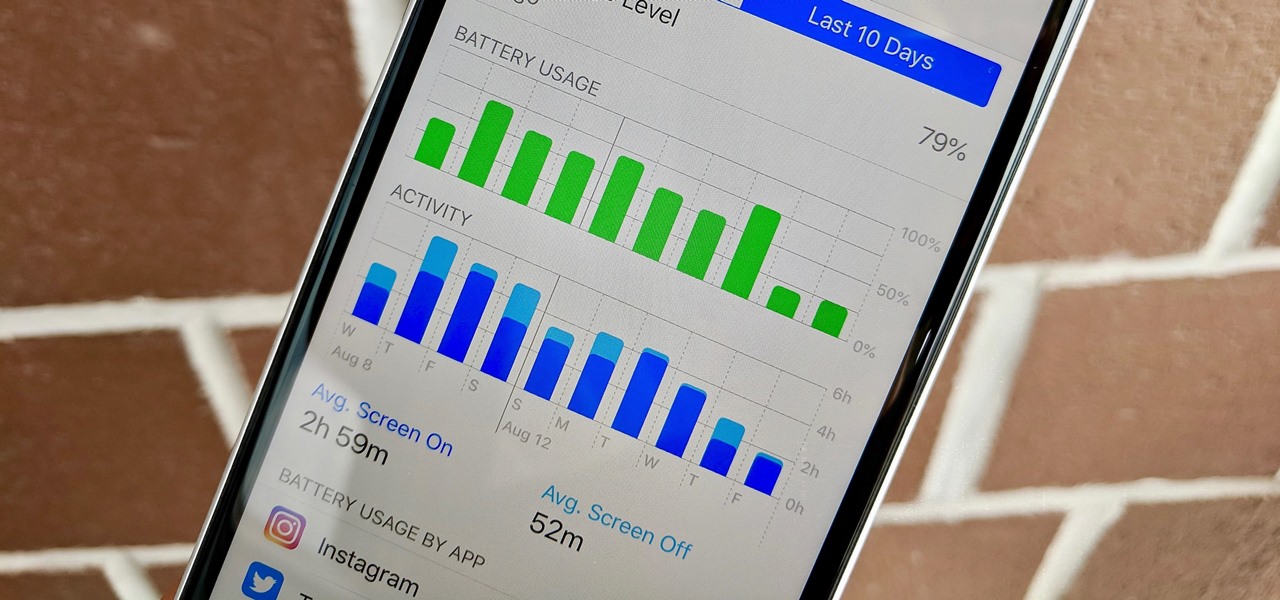
With iOS 12, Apple is making up for mistakes from the past, with iPhone batteries being no exception. The new update builds upon both battery health and performance throttling tools introduced in iOS 11.3 by offering users more information about your iPhone's battery usage than ever before.

The transcribing app can be an invaluable tool, especially if you're a student or are in a profession that relies on audio journals or interviews. These apps can convert important recordings like lectures and meetings into text for you to carefully read through to better comprehend.

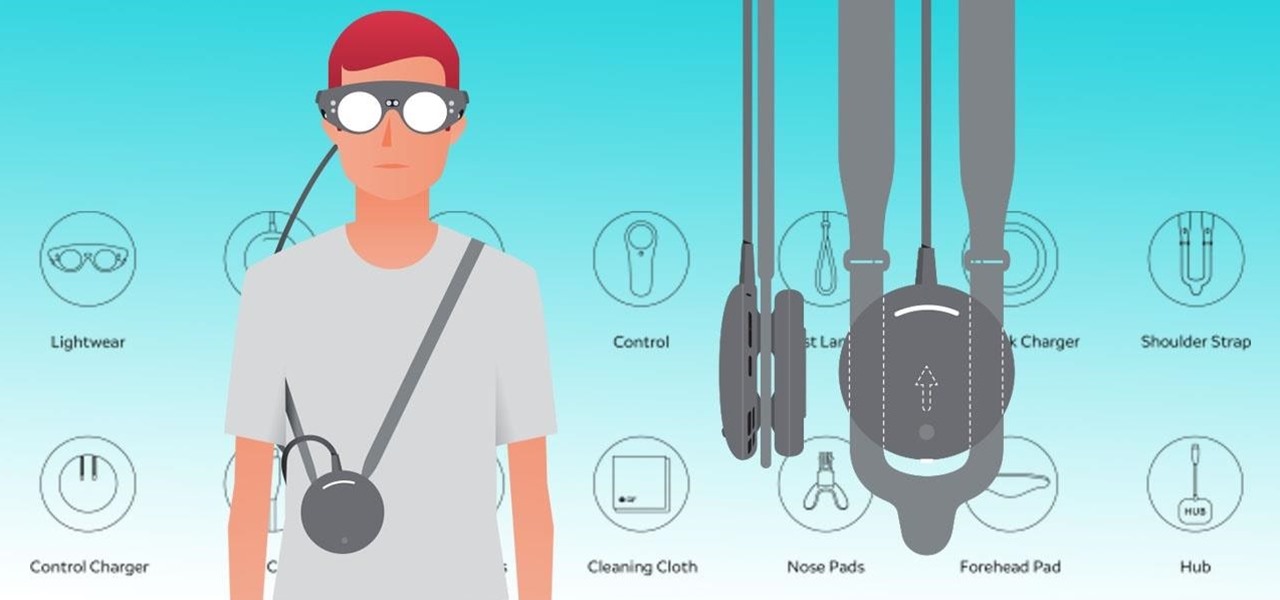
I've had a few days to live with the Magic Leap One, and it's time to finally weigh in with some thoughts as someone who has been tracking this company from the beginning, for almost five years now.

Now that the Magic Leap One is officially out in the wild, users are already beginning to find out exactly how it works and what it might be useful for in the augmented reality space. But there are still other, more unique questions that remain unanswered.

Due to weaknesses in the way Wi-Fi works, it's extremely easy to disrupt most Wi-Fi networks using tools that forge deauthentication packets. The ease with which these common tools can jam networks is only matched by how simple they are to detect for anyone listening for them. We'll use Wireshark to discover a Wi-Fi attack in progress and determine which tool the attacker is using.

Wi-Fi devices are continually emitting "probe frames," calling out for nearby Wi-Fi networks to connect to. Beyond being a privacy risk, probe frames can also be used to track or take over the data connection of nearby devices. We'll explain how to see nearby devices emitting probe frames using Probequest and what can be done with this information.

On Wednesday, the tech world woke up to fairly shocking news with the announcement that AT&T would be the exclusive wireless carrier for the forthcoming Magic Leap One, as well as an investor in Magic Leap.

Developers creating login systems know better than to store passwords in plain text, usually storing hashes of a password to prevent storing the credentials in a way a hacker could steal. Due to the way hashes work, not all are created equal. Some are more vulnerable than others, and a little Python could be used to brute-force any weak hashes to get the passwords they were created from.

During its presentation at Unite Berlin, Magic Leap gave attendees a crash course in developing experiences for Magic Leap One (ML1), we found out quite a bit more about how the device works and what we can expect to experience with the device.

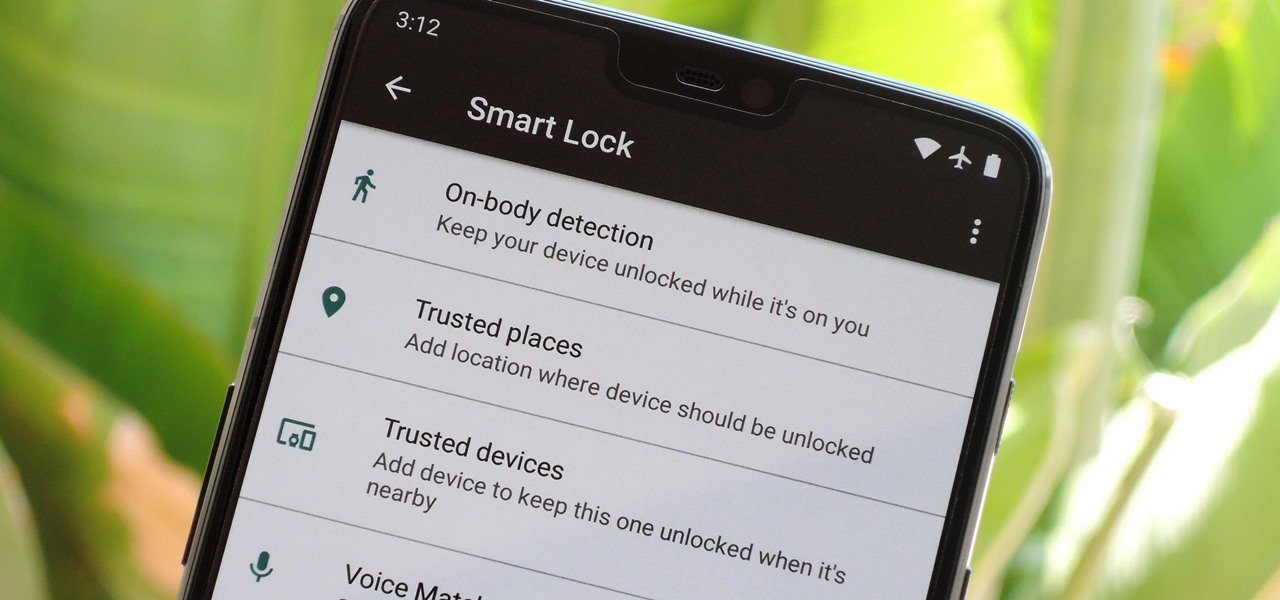
When it works, Android's Smart Lock feature is incredible. There's no need to enter your PIN when your phone "knows" it's in your hands — just unlock and go. But Smart Lock, particularly its Trusted Places feature, can be finicky sometimes.

Apple's own Photos app received some pretty amazing updates in iOS 11, but does iOS 12 have what it takes to one-up last year's Photos improvements? We think so.

Database technology has vastly improved the way we handle vast amounts of data, and almost every modern application utilizes it in one way or another. But the widespread use of databases naturally invites a slew of vulnerabilities and attacks to occur. SQL injection has been around for awhile, and as such, there are many defense methods in place to safeguard against these types of attacks.

After years of struggling, it appears BlackBerry has finally figured out how to update its iconic design for modern times. The BlackBerry KEY2 pays homage to past devices such as the Bold 9000 while adapting to modern times with the Android OS. The result is a device that might be the best BlackBerry to date.

Apple knows their products can be addicting, and with iOS 12, they are doing something about it. With the help of Screen Time and few other new tools, it should now be a lot easier to get off your phone and enjoy life in the real world.

The share menu is a vital part of Android that lets you send data between between apps. Many of your favorite apps support the feature, including the new Direct Share sub-menu, which can lead to a messy share menu. However, there are a number of tools to clean up this clutter, three of which don't require root.

There's always been a clear divide between flagship and midrange phones. Flagships will run you at least $700, while midrange typically falls between $250 and $550. The main difference is the processor, with midrange phones sporting a 600-series Snapdragon and flagships rocking the 800-series. Now, Qualcomm may have just created another smartphone tier with their newly-unveiled 700-series chip.

Analysis of photographs and social connections can be a huge component of social engineering. Understanding who a person is, as well as who they know, can establish links within a company. This information could be used by hackers to execute elaborate social engineering attacks.

| Update: ZTE's issues with the US government have finally been resolved. Check out the details below.

The iPhone vs. Android debate is almost as old as smartphones themselves. While there are a number of reasons to skew towards one operating system or the other, the Samsung Galaxy S9 models have a ton of great features that help set them apart from Apple's iPhones. The coolest feature, in my opinion, is the way notifications are handled.

Update February 25: The Nokia 9 PureView was announced at Mobile World Congress! Read all of the official specs and details at our full rundown of Nokia's latest flagship.

Continuing our series on building a dynamic user interface for the HoloLens, this guide will show how to rotate the objects that we already created and moved and scaled in previous lessons.

Conducting phishing campaigns and hosting Metasploit sessions from a trusted VPS is important to any professional security researcher, pentester, or white hat hacker. However, the options are quite limited since most providers have zero-tolerance policies for any kind of hacking, good or bad. After researching dozens of products, we came out with 5 potentials that are ideal for Null Byte readers.