
How To: Use a car tie-down with adjustable axle strap
This is a 2 inch by 8 foot long, 10,000 pound rated tie down with a built in axle strap. In this video you'll learn how to use it properly to protect your axle and secure the vehicle.


This is a 2 inch by 8 foot long, 10,000 pound rated tie down with a built in axle strap. In this video you'll learn how to use it properly to protect your axle and secure the vehicle.

There's no shortage of ice cream recipes out there, but one ice cream shop in London has found a unique recipe to sell to its customers, and of course it's controversial—breast milk ice cream.

Battle Temperantia is this episode of the Xbox 360 game Bayonetta. In Chapter 7 - The Cardinal Virtue of Temperance, prepare for a fight. This chapter consists of a boss fight. You'll start on a platform. Temperantia will punch the platform with his fists and they will stick in the platform. Attack the lighted area of his wrist. While you are attacking he will shoot at you with his other hand. He slowing sweeps his guns, so you can attack until his bullets get close to you, then jump as his l...

Would you know what to do if someone ingested poison? Equally important, would you know what not to do?

Learn how to do full situps with dumbbells and alternate cross punches. Presented by Real Jock Gay Fitness Health & Life.

Learn how to do single leg cable curls. Presented by Real Jock Gay Fitness Health & Life. Benefits

Learn how to do dumbbell squat thrust with speed alternate neutral presses. Presented by Real Jock Gay Fitness Health & Life.

Check out this video to learn how to pick a lock using a bobby pin and pliers. With enough force most locks can be undone pretty easily. This video shows you how to use these tools to open the lock with ease.

Controlling your breathing in yoga is one of the ways to bring in more energy, life force, or in yoga it is called "Prana". In this fitness how to video, Pius Ruby and Deborah York will guide you through one yoga breathing method. Yoga help us both obtain physical balance and helps us in keeping balance in our lives. Watch this tutorial and you will learn how to gain strength and flexibility through yoga.
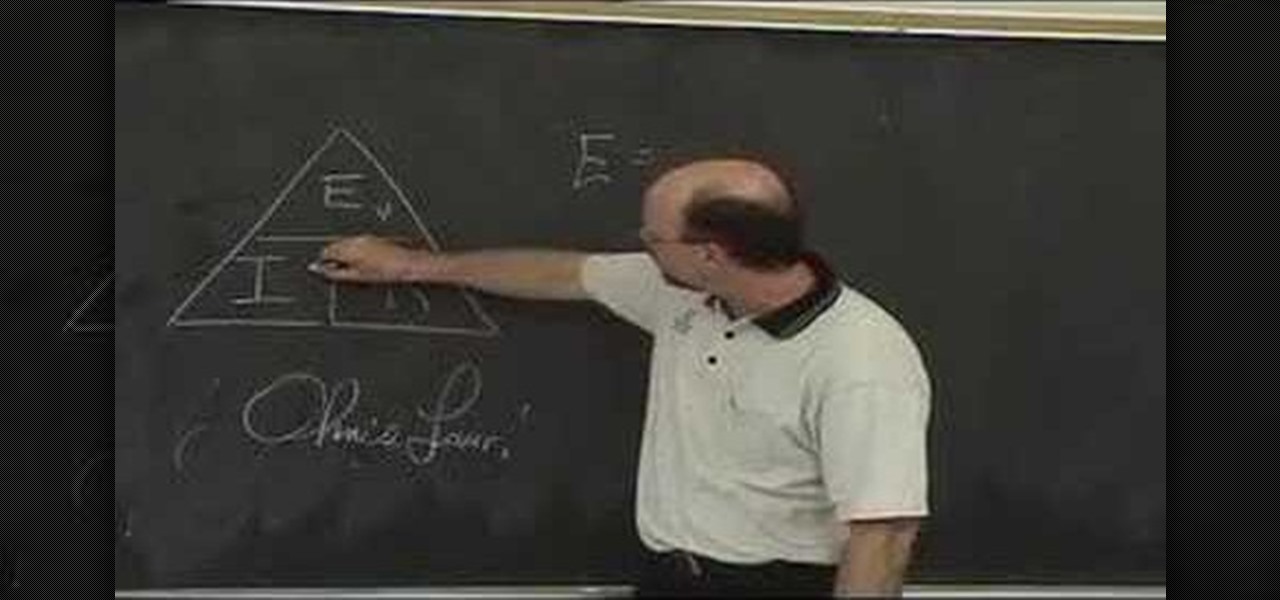
Watch this educational how to video to review Ohm's Law. This math and physics concept is derived from electric motive forces, intensity of current flow and resistance values of conductor. Watch and learn more about Ohm's Law.

Do you consider yourself a survivalist? Well, you can't be a survival expert if you don't know how to start a fire without a match or lighter. The bow drill is an ancient tool for making fire. The bow rotates the drill, and the friction produces enough heat to start a fire.

In this video, GoPlanetEarth.com shows viewers how to make bath bombs. The ingredients needed are: a half cup of Epsom salt, a half cup of citric acid, one cup of baking soda, one teaspoon of liquid glycerin, one teaspoon of water, three teaspoons of oil (the fragrance for your bath bomb), three tablespoons of sunflower or canola oil, one-fourth of a teaspoon of Borax, and food coloring (liquid). You will also need to have bath bomb molds, latex gloves, a bowl, a glass measuring cup, and pape...

Step 1. Understand that opening a coconut requires a considerable use of precise force. Because you are using a knife or cleaver, it is very important that you keep your fingers and other body parts away from the blade. Step 2. Clear off a stable cutting surface. Step 3. Begin scraping off the white, sinewy upper layer around the pointed top of the coconut, using your knife. Scrape off the top layer until a brown ridge is revealed around the base of the pointed top. Right where this brown lay...

With this two-part painting lesson, you'll learn how to paint "Three Friends of Winter," a traditional Chinese motif depicting pine, plum and bamboo — three plants admired for their beauty and, in Taoism, Buddhism and Confucianism, said to be representative of good virtue.

Find a good work area where you can sit down and be comfortable. A kitchen table works perfectly for this. Be sure to cover the surface of your table with a plastic garbage bags and a thick layer of newspaper to soak up spills and prevent damage to your table's surface. Get all your supplies ready at hand. You don't want to be hunting for them mid nail removal. Have them all spread out in front of you on the table. Using a pair of nail clippers, cut the acrylic nails down as short as possible...

You’d like to be strong and supportive for your wife in the delivery room… if only your knees would stop knocking. Keep both of you from freaking out with these tricks. Watch this video to learn how to stay calm when your wife is in labor.

Learn how to 50-50 grind with a skateboard. After you've mastered some skateboarding fundamentals, try moving on to the 50-50 grind.

Ditch those namby-pamby clichés like skeleton decals and peeled-grape eyeballs. This year, give your guests a real scare.

Sound Like a Duck or a Fog Horn! All sounds are created by vibrations. You can discover this next time you're out at a fancy restaurant. All you need is that straw in your soda and a pair of scissors. Makes sure you flatten it out really good to make this work, then make sure you parent tip your server well.

Learn how to use more English phrasal verbs with this instructional English language lesson. get...over with

Learn how to do cable Russian twist. Presented by Real Jock Gay Fitness Health & Life. Starting Position

Step 1: from the original six step position, kick your left leg to the right side as if you were going to 3step.
If your new 2020 iPhone SE is frozen, unresponsive, or won't load the system, and a standard power down and up procedure didn't work, there are few more things you can try. Force-restarting the device may do the trick, recovery mode is a last-ditch option, and DFU mode is your fail-safe.

In a departure from Apple's newer iPhone models with Face ID technology, the 2020 iPhone SE goes back to the old days where the Home button ruled, and Touch ID was the biometrics method. But if you've never owned an older iPhone with a Home button, something as simple as shutting down and restarting the iPhone SE could elude you.

Many online users worry about their accounts being breached by some master hacker, but the more likely scenario is falling victim to a bot written to use leaked passwords in data breaches from companies like LinkedIn, MySpace, and Tumblr. For instance, a tool called H8mail can search through over 1 billion leaked credentials to discover passwords that might still be in use today.

Apple's macOS operating system is just as vulnerable to attacks as any Windows 10 computer or Android smartphone. Hacker's can embed backdoors, evade antivirus with simple commands, and utilize USB flash drives to completely compromise a MacBook. In this always-updated guide, we'll outline dozens of macOS-specific attacks penetration testers should know about.

Although the Galaxy Note 9 is an amazing phone, many members of the Android community won't even look at it. This isn't just because of the Samsung Experience skin, but the large amount of bloatware that comes with this device. However, with a little work, you can remove all of it.

While the iPhone XS and XS Max come equipped with 4 GB of random access memory, and the iPhone XR with 3 GB of RAM, Apple's latest flagships are still susceptible to occasional slowdowns in performance in iOS 12. This can be fixed by clearing RAM, but the process is now a little trickier compared to iPhones with Home buttons.

If you haven't heard, another big OEM has decided to drop the headphone jack. OnePlus, the hero of the people, has just announced that the OnePlus 6T will not have the popular port. With this decision, audiophiles and others are limited to just three big-name options.

When we are building programs that communicate over a network, how can we keep our data private? The last thing we want is some other lousy hacker sniffing our packets, so how do we stop them? The easy answer: encryption. However, this is a very wide-ranging answer. Today we're going to look specifically at how to encrypt data in Python with dynamically generated encryption keys using what is known as the Diffie-Hellman key exchange.

Microsoft has always been pretty good with customer service, especially from the developer's end point. In recent years, since Satya Nadella took over as acting CEO, the level of customer and developer care has become something much more. This software giant has gone out of their way to learn about what works and what doesn't and to adjust.

With all of the bare-bones setup out of the way in our Mac for Hackers series, your Apple machine should be ready to run a significant amount of pentesting tools. We can pull tools from GitHub and compile them, we can pull dependencies or tools from Homebrew, we have both Python and Ruby. Everything is ready to go and now it's time to start building a toolbox on our local host.

Once again, you've found yourself inviting comrades, companions, and compatriots over for beverages on a Friday evening whim... but alas, your alcohol cabinet is looking rather meager, and your skills are lacking. No worries—just utilize these 10 tricks and spice up your at-home mixology game. Your friends will be none the wiser (and swear that you are a cocktail-concocting genius).

Android has a single text file named build.prop that determines tons of various system-wide settings on your device. You need root access to edit this file, since it's stored on the system partition—but the various lines of codes it contains are actually fairly easy to interpret and modify.

Task Manager got revamped quite a bit in modern versions of Windows. First introduced in Windows NT 4.0, it's become pretty popular among more advanced users. In Windows 10, Task Manager is not just a task manager anymore, it's also a system monitor, startup manager, history viewer, user controller, and the list goes on.

If you're one who enjoys a good DIY project, or if you're just tired of paying exorbitant labor fees to have your vehicle serviced every 5,000 miles, changing your own oil can be a rewarding endeavor. Even though cars and trucks are becoming increasingly over-engineered these days, manufacturers generally see to it that the basic maintenance items can still be taken care of in your driveway with a few common tools.

Welcome back, my rookie hackers! So many readers come to Null Byte to learn how to hack Wi-Fi networks (this is the most popular hacking area on Null Byte) that I thought I should write a "how-to" on selecting a good Wi-Fi hacking strategy.

Whisking liquids seems somehow quaint, especially since there are good, cheap devices out there like immersion blenders and hand mixers that can whip cream, turn egg whites into meringue, and mix batters for you.

Cryptography is the science of keeping secrets, or more specifically, the science of disguising them. As a point of fact, cryptography has progressed quite a bit farther and now encompasses file and message integrity, sender authentication, and pseudo-random number generators.

The iPod changed the music and electronics industries when it was first introduced way back in 2001. It is credited with ushering in the age of "connected devices," and has held a huge market share of around 70% for years. At the height of its popularity, the iPod made up almost 50% of Apple's revenue. Now that the smartphones and tablets we use every day have the ability to store and play music, the iPod's glory days are over. Nevertheless, there are millions of people who still use them, an...