SSH is one of the most common protocols in use in modern IT infrastructures, and because of this, it can be a valuable attack vector for hackers. One of the most reliable ways to gain SSH access to servers is by brute-forcing credentials. There are a few methods of performing an SSH brute-force attack that will ultimately lead to the discovery of valid login credentials.

While attempting to hack a web app, there may come a point where the attacker may have to escape the default directory in order to access unauthorized files. This is known as a directory traversal attack. Much as the name implies, this attack involved traversing the servers directories. But in order to move to an unauthorized directory, we need to know where those directories are. Today we'll be building a tool to brute force these directory locations based on HTTP response codes. Before we g...

These days, you can FaceTime with family and friends whether you're at home connected to Wi-Fi or on-the-go with mobile data. You may have noticed, however, that your iPhone will sometimes drop Wi-Fi and rely on cellular instead — whether you're placing or receiving a FaceTime call. While that's not an expected result, there is a workaround to get your FaceTime calls back on track.
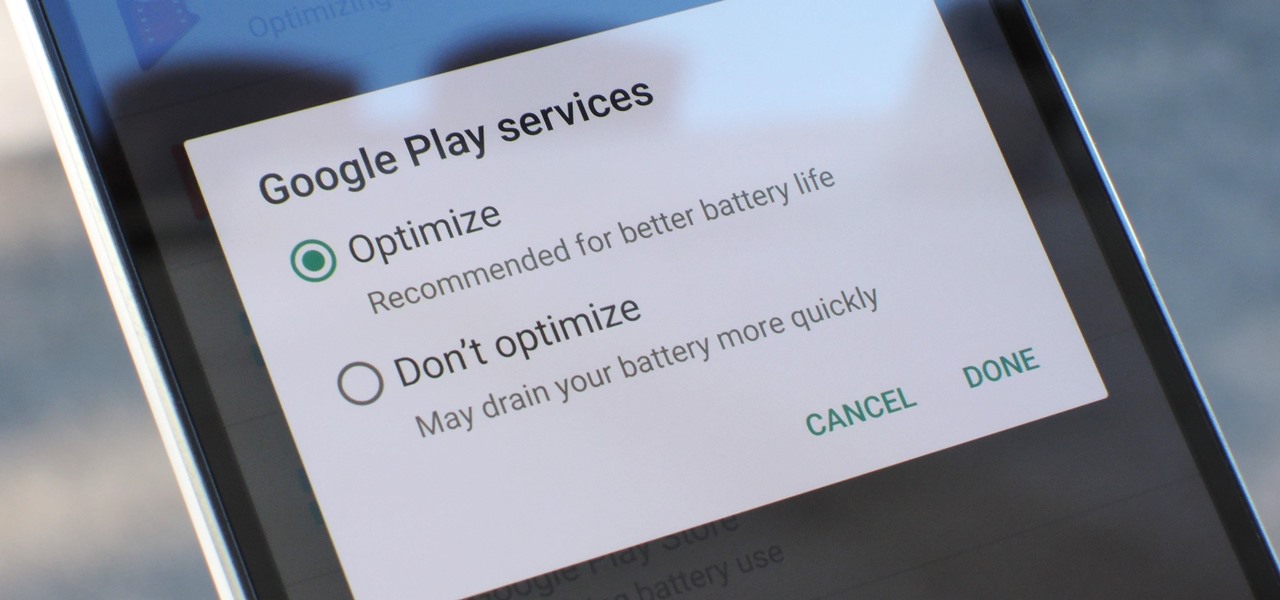
Google Play Services has been near the top of every Android user's list of battery-sucking apps for years now. It's a core system app, so you'd expect some battery drain, but for many folks, it runs rampant.

Starting Nov. 1, 2018, Google got a lot tougher with Android app developers. New apps being uploaded to the Play Store already had to target Android 8.0 Oreo or higher as of August, but now, every update to existing apps has to do the same. It may seem like a simple rule, but it will have some serious repercussions.

Quietly, while the rest of the world was engaged in pandemic and political concerns, a few weeks ago Facebook casually upgraded its Spark AR platform with what it calls Unified Effect Publishing.

A drill that helps you develop the ability to force your opponent to make a low percentage shot when just the money ball is left on the table.

Card tricks are among some of the most popular and infamous illusions used by magicians. In this free online video series, learn about card forcing. Our expert illusionist will reveal the secret to this magical technique with tips on how to use force cards and how to perform magic tricks based on forcing.

Impress your friends and family with this episode of "Do Try This at Home" with Mr. G and learn a brand new card trick that's sure to wow anyone! All you'll need is a deck of cards and a little practice to master this simple trick of forcing your audience to pick the card you want them to choose. You'll be sure to amaze them when you seem to fail, only to watch a video and there on the computer screen is their card! They'll be shocked at the elaborate trick you've set up for them.

In this video tutorial, viewers learn how to force cards. Card forcing is when it looks like the users has a free selection of cards, but in reality the magician has predetermined a card to be selected. The force taught in this video is the cross cut force. Take the desired card on top of the deck and place it face down on top. When you shuffle the deck, make sure that the desired card always remains on the top of the deck. This video will benefit those viewers who are interested in magic, an...

The tactic of brute-forcing a login, i.e., trying many passwords very quickly until the correct one is discovered, can be easy for services like SSH or Telnet. For something like a website login page, we must identify different elements of the page first. Thanks to a Python tool for brute-forcing websites called Hatch, this process has been simplified to the point that even a beginner can try it.

Brute-forcing is an easy way of discovering weak login credentials and is often one of the first steps when a hacker finds network services running on a network they gain access to. For beginners and experienced hackers alike, it's useful to have access to the right tools to discover, classify, and then launch customized brute-force attacks against a target. BruteDum does it all from a single framework.

Using Hydra, Ncrack, and other brute-forcing tools to crack passwords for the first time can be frustrating and confusing. To ease into the process, let's discuss automating and optimizing brute-force attacks for potentially vulnerable services such as SMTP, SSH, IMAP, and FTP discovered by Nmap, a popular network scanning utility.

Developers creating login systems know better than to store passwords in plain text, usually storing hashes of a password to prevent storing the credentials in a way a hacker could steal. Due to the way hashes work, not all are created equal. Some are more vulnerable than others, and a little Python could be used to brute-force any weak hashes to get the passwords they were created from.

When you press the Home button on your iPhone SE, you're not quitting your current app. Instead, it stays open in the background. If an app ever bugs out on you or you don't want it to run in the background, you'll need to force-close to quit it completely. Doing so is also helpful when your app switcher gets too cluttered, and you find it hard to switch between apps because of it.

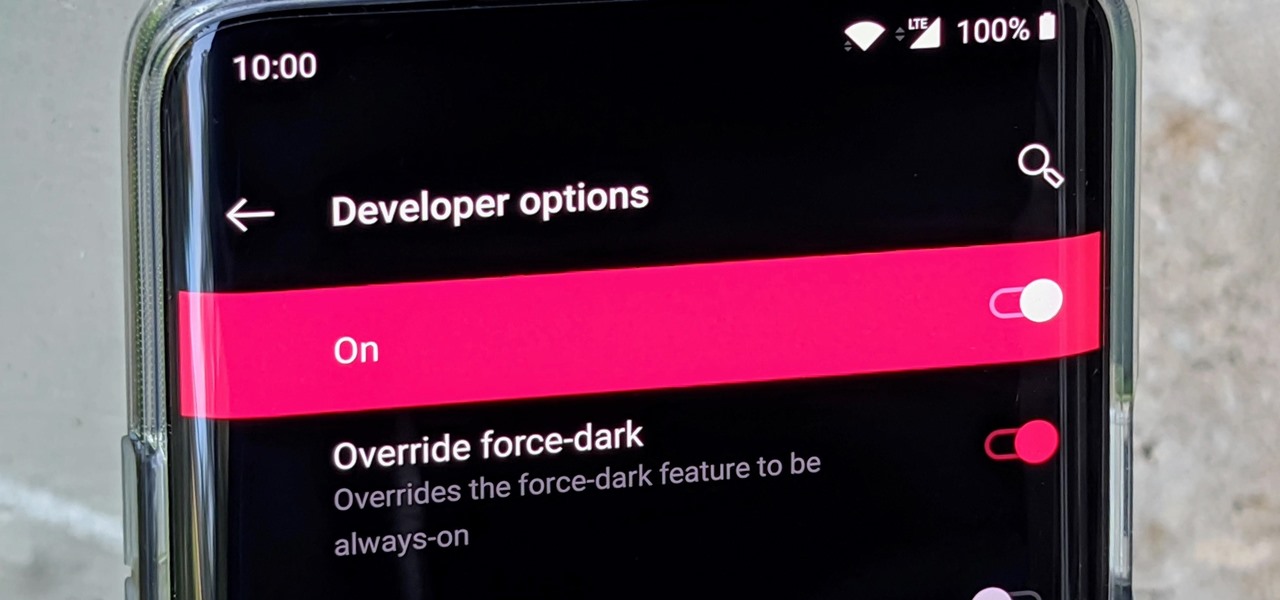
Google brought its official dark mode to Android 10 not long ago, but it might take a while for all apps to support the new feature. That doesn't mean you have to wait around for each app developer to add dark mode — just follow this guide to learn how you can force all apps in Android 10 to use dark mode.

Hi, my name is Alan, and I am not a script kiddy brat from Xbox Live asking you how to boot someone offline for being mean to me. I am an amateur white hat hacker hoping to learn and teach and this is my first tutorial.

One vital part of Android 10's new navigation system is the "QuickStep" gesture. Swipe up from the bottom of your screen, then pause. You'll see your recent apps along with a dock containing a handful of icons for quick access. This dock is provided by the phone's launcher, which means your home screen is now integrated into the multitasking UI. So what happens if you change your home screen app?

Having a dropped call can be incredibly frustrating, especially when you look down and see that your iPhone has full reception. While there's any number of issues that can cause this, one common and often overlooked issue is your iPhone failing to switch cell towers as appropriately needed.

If you own a Pixel or Nexus device, Project Fi is a great alternative for cellular service outside of the four major US carriers. Project Fi is a Google-managed MVNO, providing service primarily through the T-Mobile and Sprint networks. One of the biggest mysteries on Fi is which network you're connected to at any given time, but there's a simple solution.

With protests springing up across America, there's a chance you may have your first interaction with law enforcement. Many demonstrators will have their phones in-hand to film the action, which, sadly, could prompt an officer to demand the device and any self-incriminating data it may contain. Before this happens, you should know there are tools at your disposal to protect your data in such situations.

It's almost impossible to use Apple News at night without having to mess with the white point and zoom filters. That might sound a bit dramatic, but it's really not when you consider that iOS 13 has a perfectly good Dark Mode that should work for News. So why are we stuck reading most news stories in Light Mode? We're not, but you have to put a little work into it going dark in News.

There has been significant debate over law enforcement's right to access our digital devices in recent years. New tools from Grayshift and Cellebrite are popping up faster than ever to help government agencies, as well as traditional hackers, break into iPhones. If you're concerned, you can take steps right now to beef up your passcode and prevent outsiders from gaining access to your device.

To name just a few companies, VK, µTorrent, and ClixSense all suffered significant data breaches at some point in the past. The leaked password databases from those and other online sites can be used to understand better how human-passwords are created and increase a hacker's success when performing brute-force attacks.

This League of Legends guide from CLG showcases how to use zone control against your opponent by forcing them to stay out of range of minions and preventing them from damaging you. This will allow you to win your lane so that you can move into the late game.

Use this rigged game to cheat your friends twice in a row! The game functions just like 31, only this time you'll always win if you follow the instructions in this video.

One way to get your kids to read more books is not by forcing them to do so, but by making the reading experience fun by giving them these cute handcrafted bookmarks.

This extremely difficult yet highly effective training combination is designed for athletes looking to strengthen their core, glutes, and shoulders.

The dolly zoom shot is also known as the Vertigo Effect in filming. It's that dizzying, slightly unstable camera effect you see in shows like "Glee" and sometimes "The Office." It creates audience confusion, thus forcing them to keep watching in interest.

Sometimes the simplest pranks are the best ones! They take no time at all, and they're so simple that no one would even expect to look for the obvious. Like this windshield prank. It involves chocolate syrup and a cup of milk.

Christmas means decorating trees with store-purchased ornaments and tinsel, decorating stairwells with store-purchased garlands, and decorating the exterior of your house with store-purchased lights. These days everything you need can be puchased pre-made somewhere, and while that saves us time, what happened to the good ol' days when we crafted ornaments out of popsicle sticks and strung cranberries on a string?

This video shows how to make a paper "popper" that you can use to make a loud popping noise. Start with piece of paper. first fold it in half the skinny way, then fold it in half again the other way. Set the paper down on a table or flat surface so that the flaps of the paper make an "M" shape. Now take the paper in your hands and grab the outer sheets of the "M" with the index finger and thumb of your right hand. Pull the inner sheets out with your other hand. Take the popper in your right h...

Some of the new poinsettia plants will continue to "bloom" year round, but others need a little encouragement. The blooming is actually leaves of the plant itself. One way of forcing it to change color is to withhold fertilizer and/or light for a time, then put it back into a sunny location and it will begin to bloom. The video also addresses spots on Ligustrum plants. It has to do with cold weather in the winter and lack of nitrogen. There's not much you can do about winter damage, but ferti...

This video tutorial shows how fifteen dollars and a half an hour of assembly can produce a working bare-bones laminar flow nozzle that attaches to a garden hose for a makeshift fountain.

Veggies don't have to be boring, and you should never feel like you're forcing yourself to eat them. Just check out this recipe for baked tomatoes topped with delicious melted blue cheese to see just how satisfying an all vegetarian meal can be.

Beginners learning brute-forcing attacks against WPA handshakes are often let down by the limitations of default wordlists like RockYou based on stolen passwords. The science of brute-forcing goes beyond using these default lists, allowing us to be more efficient by making customized wordlists. Using the Mentalist, we can generate millions of likely passwords based on details about the target.

Tic-tac-toe is one of the easiest games to play and most difficult to win. Most games end in a tie, boredom, and frustration. But do they have to? This video will show you how to predict the winner of a tic-tac-toe game by forcing it to go the way you want with strategic moves. Try using this prank to win you free drinks the next time you're out at the bar.

You know how people always get frustrated when they open up a Valentine's Day chocolate gift box to find no labeling device for the chocolates there, forcing them to taste test each one to see if they like 'em? Recreate this frustration and relish in the schadenfreude by baking these melt in your mouth chocolate bars, each one filled with something different, from caramel and peanuts to almonds and more chocolate.

In this video tutorial, viewers learn how to perform the DDT wrestling move. Begin by setting up the move with a toe kick, forcing the opponent to bend over. While standing, wrap your arm around the opponent's neck. Users may choose to give a signal before they execute the move by slapping the opponent's back. When you go down, do not keep the grip on the opponent. As you go down, loosen your arm so that the opponent can pop their head out and prevent any real injury. This video will benefit ...

Most dogs will be able to tell the difference between a pill and, let's say… a piece of cheese. They aren't as stupid as you think. One is for eating and one is for spitting out. Well, this is a short video tutorial to teach you how to feed your dog multiple pills without fuss.