If you're looking to get into the nitty gritty of DNS (Domain Name System) hacking, you MUST check this video out. In this in-depth tutorial, you'll get to adventure into the wonderful world of DNS. Explore the vast and intricate details of our beloved Domain Name System while exploiting mis-configured routers, brute forcing, and even look up Wikipedia entries from TXT records.

Anyone who has flown across multiple timezones is familiar with the negative effects of jet lag, especially when traveling for business on a tight schedule. This video features four easy tips for avoiding the effects of jet lag. These include hydrating properly, going outside, exercising, and forcing yourself into the rhythm of whatever place you are in rather than napping in order to remain on your normal schedule.

In sailing, the term "heave to" means slowing down the boat's progression in such a way that the boat doesn't need to be steered directly. Take a look at this instructional video and learn how to heave to in sailing. To do this, the rudder will need to be turned so it's forcing the bow into the wind. The rudder and the jib counteract one another in the process, and the boat ends up stalling.

Did your eyeshadow or blush cracked while depotting? Sometimes the pans are well glued that you can't avoid forcing the pan to pop out causing your shadows to crack. Here's a quick tutorial on how to fix it.

This will help you identify which algorithms to use to get to "the Fish". If you don't know what "the Fish" is, then maybe you should watch. Or not, nobody's forcing you.

We all know how it goes: You've just come home from a grueling day at work followed by a grueling drive back, and you're beat. Even the thought of forcing your feet to the kitchen and turning on the stove makes you shudder. So you pick up the phone and order a pizza and buffalo wings. Sure, it's tasty, but is that really the best thing you could be eating?

No pain, no gain, right? In this fitness video you'll learn how to do a standing rowing exercise with a little twist: adding dumbbells. By holding on to a substantial weight while doing a bent rowing exercise, you'll be adding a lot more resistance to your workout, forcing your triceps to work harder to contract.

Is your roommate's food always in the fridge longer than it should be? Is their meat rotting, forcing you to take care of it? Living with other people can be a pain, especially when it comes to the one place that you all share— the refrigerator. Keep your sanity and senses by transforming your funky smelling fridge into a pleasant aroma of charcoal...

Bros Icing Bros is a new Internet phenomenon/drinking game that men are playing on each other across the country. In this clip, learn all about the rules of Icing a Bro and how to do it right.

More and more parents are choosing to forego circumcision and leave their newborn sons penises intact. This video is about how to care for your infant's foreskin. In the first few years of life no special form of care is needed for your baby's intact foreskin. Forcing the foreskin to retract is painful and is no longer recommended because it is not necessary. Clean the baby's penis just as you do the rest of the diaper area. Over time the foreskin will begin to retract naturally through norma...

In this video from fatlosslifestyle we learn how to get a smaller waist and to burn belly fat. In this exercise he is lying down, bending the knees. You are creating a vacuum in a sense. You take a deep breath in forcing your belly button to push up towards the ceiling, then as you blow the air out, feel your belly button going down. When you have 3/4 of the air out, hold your breath, and suck in through your throat with your breath being held. Visualize your organs going up into your diaphra...

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to secure remote desktop.

To be the best at the Madden NFL video game, you have to be willing to get advice, but not just any old advice... professional advice. To beat everyone, you have to be ruthless and know all of the strategies and gameplay tricks. To master Madden 08, check out this quick, football game, video tip from Madden Nation (EA Sports and ESPN) with video game pro Steve Williams (or Coach or The Old Skool Gamer).

Not sure how to properly warm up your voice before belting a tune? Learn the right way to warm up your voice so you can surprise friends without setting off the neighborhood dogs.

Do you consider yourself a survivalist? Well, you can't be a survival expert if you don't know how to start a fire without a match or lighter. The bow drill is an ancient tool for making fire. The bow rotates the drill, and the friction produces enough heat to start a fire.

Hashes containing login passwords are transmitted between Windows computers on local Wi-Fi networks. By intercepting and decrypting these hashes using Responder and John the Ripper, respectively, we can learn a target's login credentials which can be later used to gain physical access to their computer.

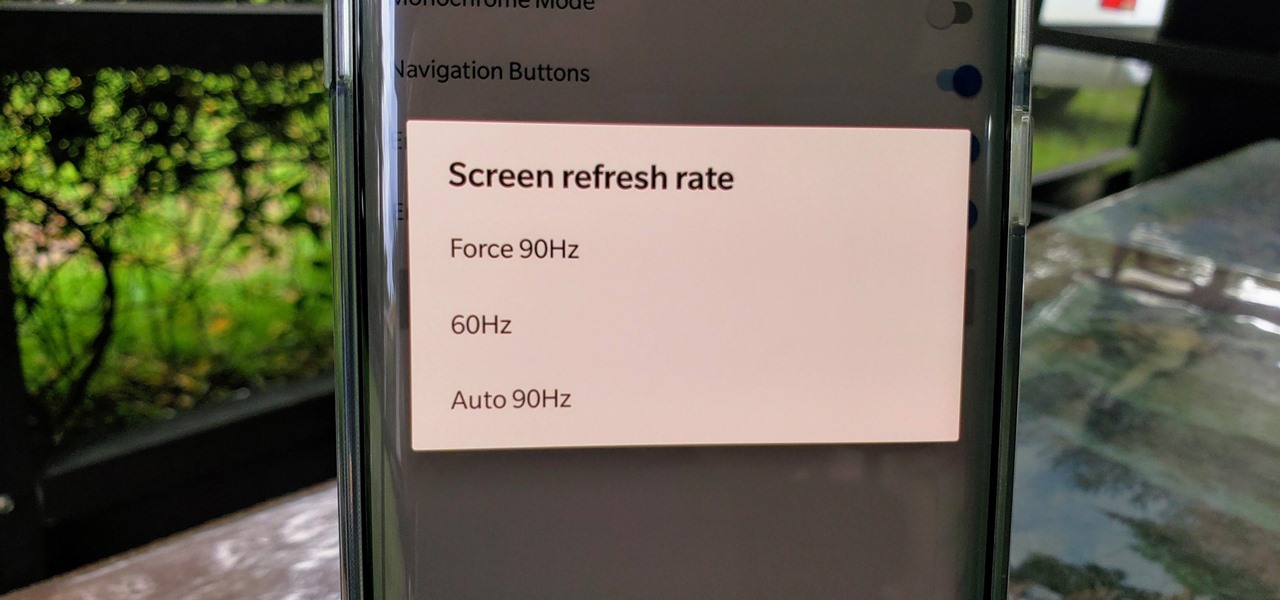
One of the standout features of the OnePlus 7 Pro is the 90 Hz display. A higher refresh rate means smoother gameplay for all your favorite games, which is precisely what you'd want out of your gaming experience. However, not all games play nicely with these higher refresh rates — but luckily, there's a pretty simple fix.

Here's a quick video tutorial on using eyelet pliers. These work with the smaller eyelets by forcing the grommet through the fabric and curling it back on itself on the other side. Eyelet pliers are very quick and easy to use to attach grommets.

Tired of fishing that garlic press out of the gadget drawer? Kitchen Contessa Dani Luzzatti doesn't mince words when it comes to discussing the bitter flavor that happens when forcing a garlic clove through a garlic press.

The first thing any Android power user does with their phone is unlocked the Developer options. The hidden menu has many low-level tweaks, such as forcing Dark mode on all apps, speeding up animations, or enabling hidden Quick Setting tiles. And most modifications require nothing more than hitting a toggle.

Router gateways are responsible for protecting every aspect of a network's configuration. With unfettered access to these privileged configurations, an attacker on a compromised Wi-Fi network can perform a wide variety of advanced attacks.

Unless you're tightrope walking, stability is quite a fun killer. Relish in the unknown by learning how to do bicep curls with an exercise ball incline. By forcing your core and your back to deal with the bouncy, unstable nature of the ball, you'll have to work those areas in addition to the biceps.

There are many tools out there for Wi-Fi hacking, but few are as integrated and well-rounded as Bettercap. Thanks to an impressively simple interface that works even over SSH, it's easy to access many of the most powerful Wi-Fi attacks available from anywhere. To capture handshakes from both attended and unattended Wi-Fi networks, we'll use two of Bettercap's modules to help us search for weak Wi-Fi passwords.

Pyrit is one of the most powerful WPA/WPA2 cracking tools in a hacker's arsenal, with the ability to benchmark a computer's CPU speeds, analyze capture files for crackable handshakes, and even tap into GPU password-cracking power. To demonstrate how quickly it can hack a WPA/WPA2 password, we'll use it to play a Wi-Fi hacking CTF game anyone can practice for less than $10.

Cracking the password for WPA2 networks has been roughly the same for many years, but a newer attack requires less interaction and info than previous techniques and has the added advantage of being able to target access points with no one connected. The latest attack against the PMKID uses Hashcat to crack WPA passwords and allows hackers to find networks with weak passwords more easily.

Leaked databases get passed around the internet and no one seems to notice. We've become desensitized to the data breaches that occur on a daily basis because it happens so frequently. Join me as I illustrate why reusing passwords across multiple websites is a truly awful practice — and compromise hundreds of social media accounts in the process.

With the Galaxy Note 9's 6.4-inch AMOLED display, split screen is far more useful since each half of the screen is relatively large. The problem is that there are some noticeable omissions in the list of apps which support the feature. However, Samsung offers a fix for this.

Many Android users woke up on January 10 to discover that their phone's performance took a nosedive overnight. Battery life is draining fast, overall performance has been sluggish, and devices seem to be overheating for no apparent reason. Not to worry, this isn't happening because of something you did.

Hacking Wi-Fi is a lot easier than most people think, but the ways of doing so are clustered around a few common techniques most hackers use. With a few simple actions, the average user can go a long way toward defending against the five most common methods of Wi-Fi hacking, which include password cracking, social engineering, WPS attacks, remote access, and rogue access points.

Design flaws in many routers can allow hackers to steal Wi-Fi credentials, even if WPA or WPA2 encryption is used with a strong password. While this tactic used to take up to 8 hours, the newer WPS Pixie-Dust attack can crack networks in seconds. To do this, a modern wireless attack framework called Airgeddon is used to find vulnerable networks, and then Bully is used to crack them.

The nemesis of music streamers is data caps, cell phone or otherwise. Restricting monthly data and forcing users to decide between quantity and quality of music has had audiophiles tearing their hair out since streaming toppled the iPod. While the problem regarding music quality seems difficult to tackle, it's far from impossible.

Some of us woke up at the KRACK of dawn to begin reading about the latest serious vulnerability that impacts the vast majority of users on Wi-Fi. If you weren't one of those early readers, I'm talking about the Key Reinstallation Attack, which affects nearly all Wi-Fi devices.

There are hidden Wi-Fi networks all around you — networks that will never show up in the list of available unlocked and password-protected hotspots that your phone or computer can see — but are they more secure than regular networks that broadcast their name to any nearby device?

It's no secret that the vast majority of Null Byte readers range from beginner to seasoned coding pros and developers. Regardless of whether you're interested primarily in building websites or creating best-selling apps and games, working with a wide variety of programming languages remains one of the best ways to make serious money in an increasingly app-driven world.

Compromised uTorrent clients can be abused to download a malicious torrent file. The malicious file is designed to embed a persistent backdoor and execute when Windows 10 reboots, granting the attacker remote access to the operating system at will.

Windows 10 passwords stored as NTLM hashes can be dumped and exfiltrated to an attacker's system in seconds. The hashes can be very easily brute-forced and cracked to reveal the passwords in plaintext using a combination of tools, including Mimikatz, ProcDump, John the Ripper, and Hashcat.

With a tiny computer, hackers can see every website you visit, exploit services on the network, and break into your Wi-Fi router's gateway to manipulate sensitive settings. These attacks can be performed from anywhere once the attacker's computer has been connected to the router via a network implant.

Your social security number, credit card information, and medical history can fall into the wrong hands if you're not careful about how and where you share your data online. If you really care about your data, there are tools and techniques you can utilize to protect yourself from cyberstalkers, advertisers, and hackers in a time when digital lives are a high commodity.

Following the most recent election, some argue that increasing political polarization is dividing Americans. A new app, called Read Across the Aisle, is aiming to combat this by encouraging users to read news from media outlets on both sides of the political spectrum.

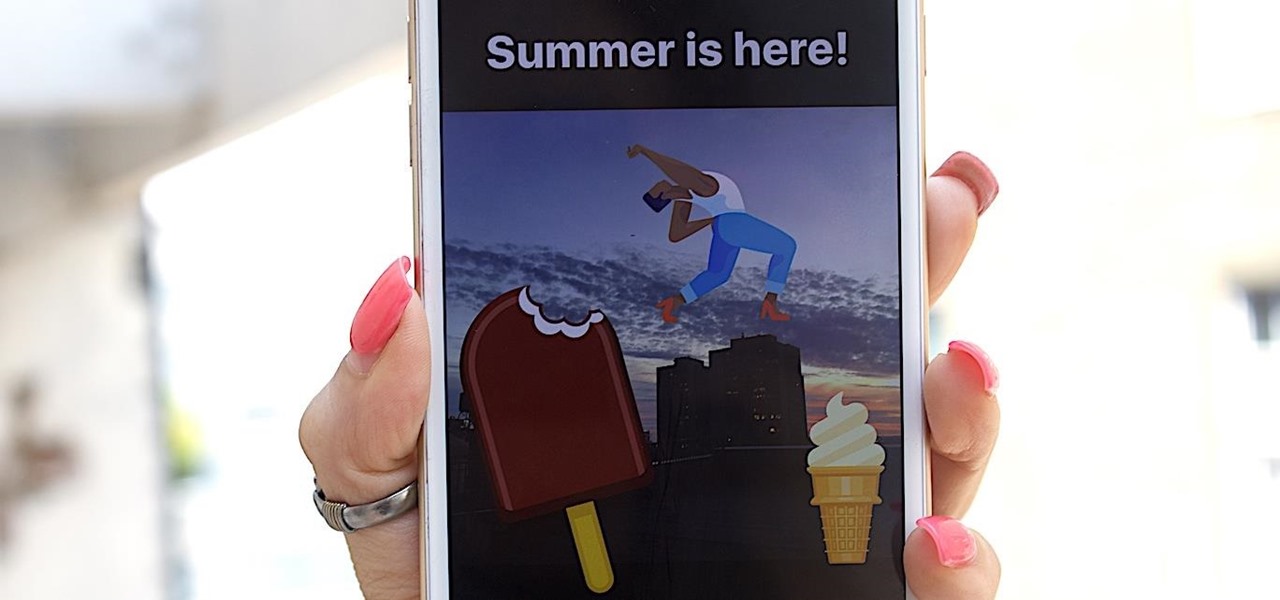
Although Instagram's summer stickers will only be here for the summer, the ice cream cone is still currently one of the most fun ones to play around with in Stories. It's also one of the stickers that lets you pick your preferred flavor of ice cream, rather than forcing just one type of flavor on you.