Are you interested in beginning research of your family's history? I began this journey about 3 or 4 years ago and here is what I found. I've done almost ALL of my research online, and gotten farther, faster and more comprehensively than anyone else who has researched my family the old fashioned ways. This is the kind of thing that technology is made for. Here's how to use it.

If you read my article on the OSI model, you got a good overview on communications from that model's perspective, but how does that relate to TCP/IP? We're going to take it a step further, getting into the idea behind the two address concept. How does an IP address and a MAC address work together? If you want to hijack sessions and all sorts of lulz like that, you need to understand these concepts. Let's get into it, mates!

Someday, maybe not today, maybe not tomorrow, but someday, you'll find yourself on the road in your car, maybe on the highway, and you'll hear something.

I'm always looking for solutions to problems people are having with their smartphones. This means I spend a lot of time browsing forums and release sites looking for new apps. In doing so, I find a lot of apps that don't quite solve a major problem, but are nonetheless pretty cool. I came across four of those this week.

Every summer for the last 26 years, hoards of hackers have descended on the Las Vegas Strip for DEFCON, the biggest hacker conference in the US. There's a wealth of talks every season (DEFCON 27 has at least 95 scheduled), and there have been some essential topics to learn from in past discussions. We've dug through the last ten years and found the 15 most popular talks you should watch.

Since the Razer Phone's announcement in 2017, we've seen a new subgroup of phones emerge. Gaming phones are now a thing, leading to companies like ASUS creating phones that are thoroughly optimized for the mobile gaming experience. And with their second iteration, they perfected it.

It's the icing on top of your cake (or whipped cream on top of your Android Pie) of despair. You may have not had the easiest time rooting your device, but you feel like you overcame all of the obstacles. Only now to discover that those very apps and mods you were rooting for still won't work — and the signs point to a lack of root access. Don't lose hope, because we have some tricks up our sleeve.

It's easy to have your password stolen. Important people like executives, government workers, journalists, and activists face sophisticated phishing attacks to compromise their online accounts, often targeting Google account credentials. To reduce this risk, Google created the Advanced Protection Program, which uses U2F security keys to control account access and make stolen passwords worthless.

There's no doubt Kali has established itself as the most popular penetration distribution available. However, just because it's the fan favorite of beginners and security researchers doesn't make it right for everyone. Manjaro Linux is a beginner-friendly Arch-based distribution which can be easily weaponized with the Black Arch expansion, creating a friendlier first-time Arch experience.

Over the past several weeks, I’ve had the pleasure of test driving Samsung’s next big thing, the Galaxy S4. After putting the GS4 through its paces, I have a clear picture of what this device is capable of. I’ve covered the features of the device before, and now I’ll tell you why I believe it's currently the best Android phone on the market. Initial Impressions

If you've been to a convention of any sort before, you know that there are good and bad panels, and that their inherent goodness or badness often has little to do with the actual content being discussed. That's because giving a panel is a skill that not everyone has. However, it is a skill that everyone could have! In this article, I'll tell you how to give a good panel on practically any subject. Image by Shannon Cottrell

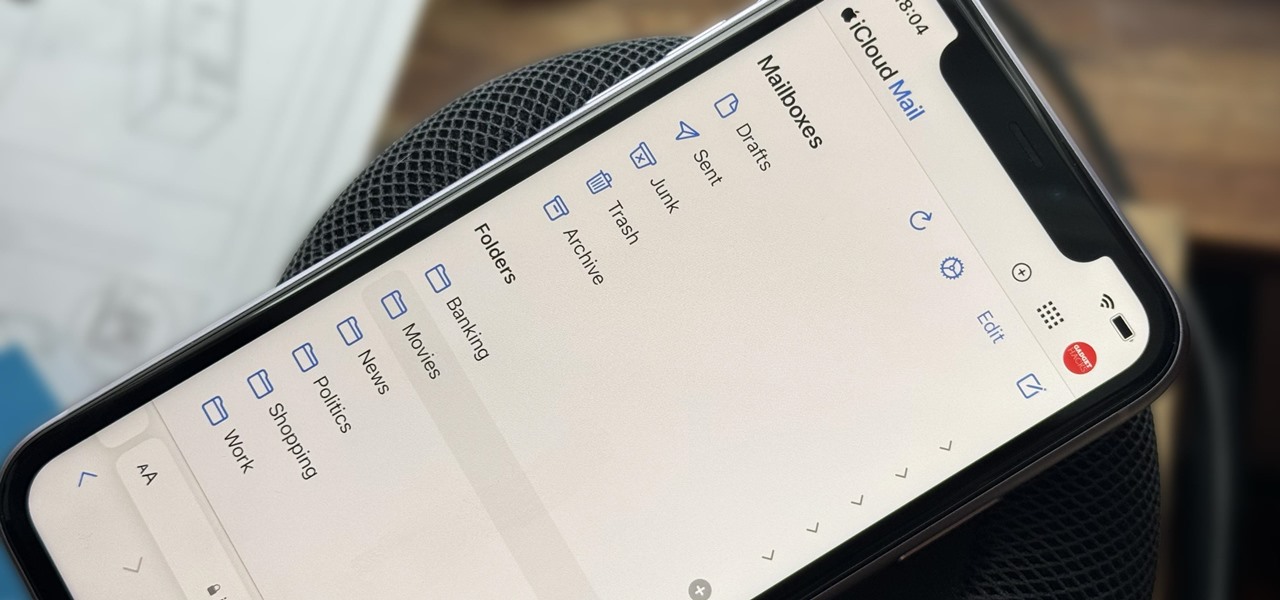
Apple includes a lot of helpful features for iCloud email addresses, but one of its best-kept secrets will give you total control over organizing your inbox like a pro.

In a tradition dating back to the Nexus days, Google has always used fish-themed codenames when communicating internally about their phones. Their laptops and tablets are usually named after video game characters. These names often give us the first evidence of an upcoming device when they're used in software commits in Android's open source code.

After shipping a redesign of Google Photos and adding a neat new Map View feature for exploring photos, Google has made another change to manage the volume of photos and videos the app is handling during the Social Distancing Era.

The gig economy is thriving, and if you aren't already making money with your phone, you could be missing out on easy residual income. Some people just want extra cash, and some even manage to completely ditch the 9–5, enabling them to work at their own pace and set their own hours.

Andre was enjoying the carefree life of a 12-year-old with his friends, riding his bike and playing sports, like all kids that age. Schoolwork wasn't hard for him, and his grades showed that.

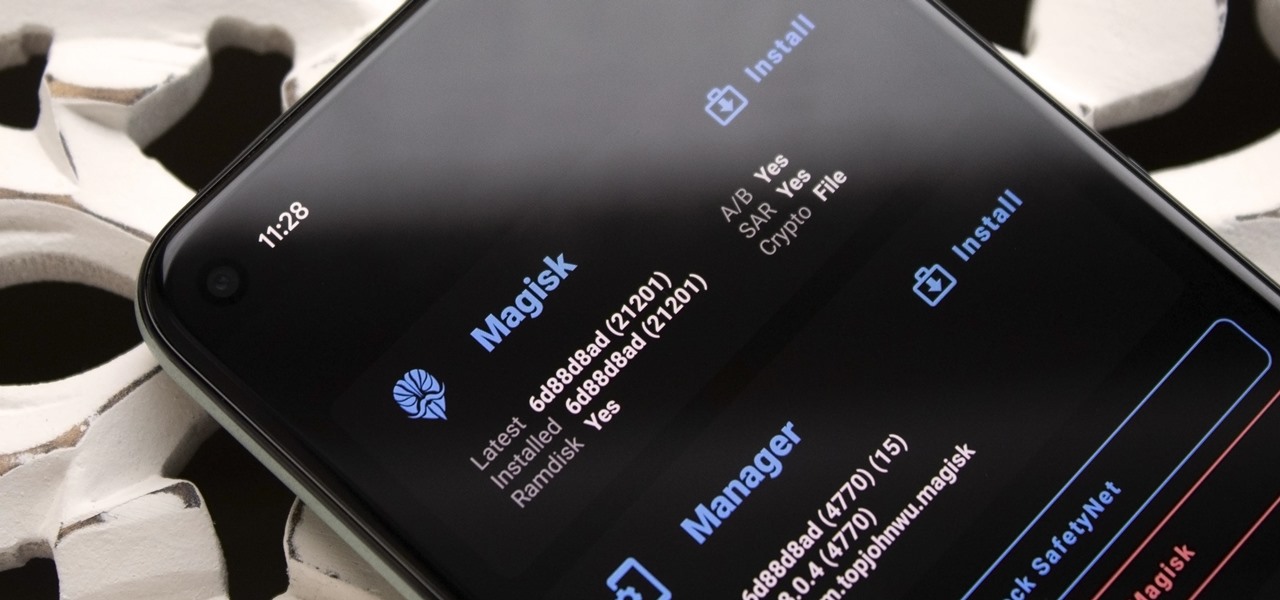
Okay, so you rooted your Android phone .... now what? There are a few ducks you need to get into a row, like backing up your stock boot image, getting SafetyNet sorted, and improving security with biometrics. But there are also awesome root mods waiting for you — just don't get ahead of yourself.

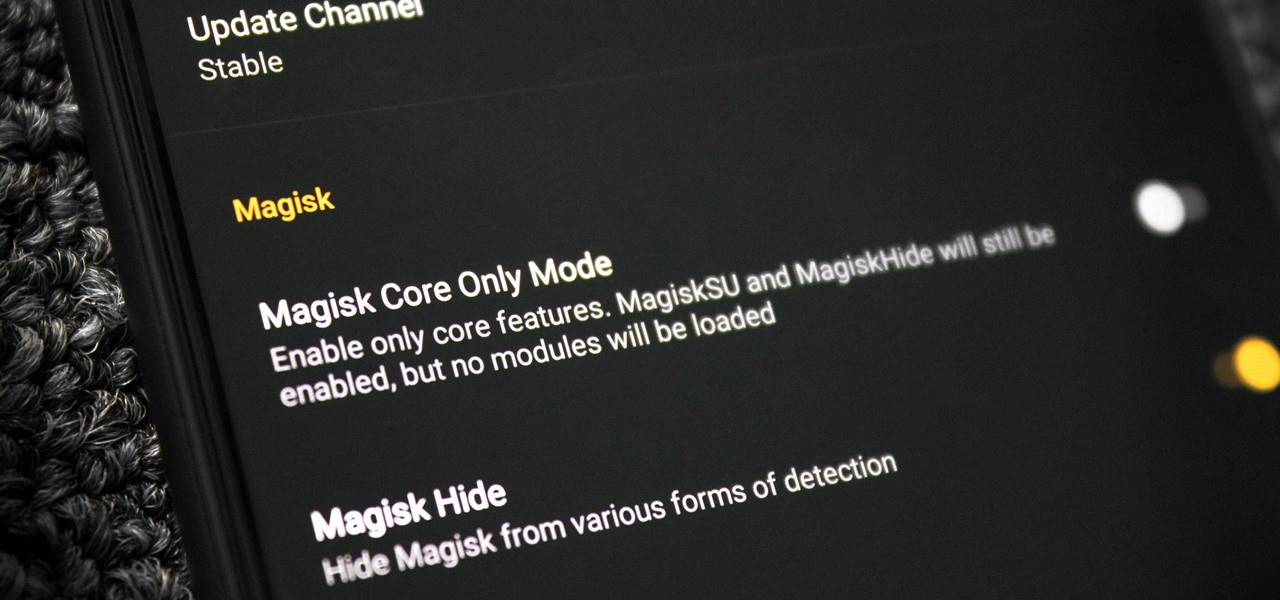
Bootloops are a risk inherent to rooted devices — with great power comes great destroyability, after all. While custom recovery sometimes provides a quick fix when you flash the wrong Magisk module, with TWRP becoming more challenging to implement thanks to Android 10, the solution is a bit more complicated nowadays.

Your social security number, credit card information, and medical history can fall into the wrong hands if you're not careful about how and where you share your data online. If you really care about your data, there are tools and techniques you can utilize to protect yourself from cyberstalkers, advertisers, and hackers in a time when digital lives are a high commodity.

To name just a few companies, VK, µTorrent, and ClixSense all suffered significant data breaches at some point in the past. The leaked password databases from those and other online sites can be used to understand better how human-passwords are created and increase a hacker's success when performing brute-force attacks.

A PirateBox creates a network that allows users to communicate wirelessly, connecting smartphones and laptops even when surrounding infrastructure has been disabled on purpose or destroyed in a disaster. Using a Raspberry Pi, we will make a wireless offline server that hosts files and a chat room as an educational database, a discreet local chat room, or a dead-drop file server.

It can be very frustrating: You open your Messages app, send an iMessage, and then see that dreaded red exclamation point or horrible green SMS bubble. At this point, you may be curious whether it's just your iPhone or whether iMessage is broken for everyone, but how do you find out?

Data can be injected into images quickly without the use of metadata tools. Attackers may use this knowledge to exfiltrate sensitive information from a MacBook by sending the pictures to ordinary file-sharing websites.

Since our Canon 5D World is just starting out, there's not a lot of activity in the forum. If you have a question about your 5D or 5D Mark II, then ask away. But there are other communities on the Web that already have great information from its members. Hopefully, the Canon 5D World forum will be just as helpful to everyone, but for now, here are some of the best forums on the Internet that can help you with Canon's EOS 5D and 5D Mark II cameras.

*WH2* Make Your Avatar Invisible* (click here) *wh2*- located in forums- **MORE M2 STUFF**

WonderHowTo user lex lugo of Bootleg Entertainment posted this fun spoof on musical classic Westside Story to the Canon 7D World forum. The short starts off with some pretty (amazingly) goofy dance-offs; stay tuned 'til the end if you dig 2D violence.

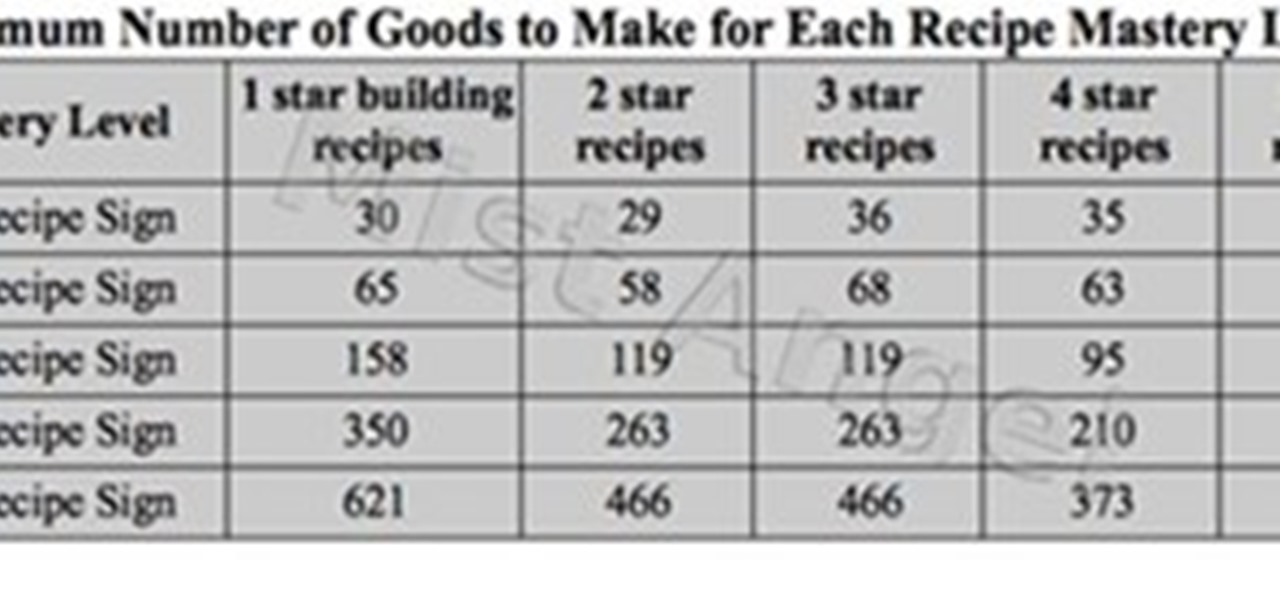
I'm using this page as an image uploader for official forum charts. Here's one for crafting mastery if you want to see it in action :)
Check out our Forum and give us your opinion! We want to know what you think.

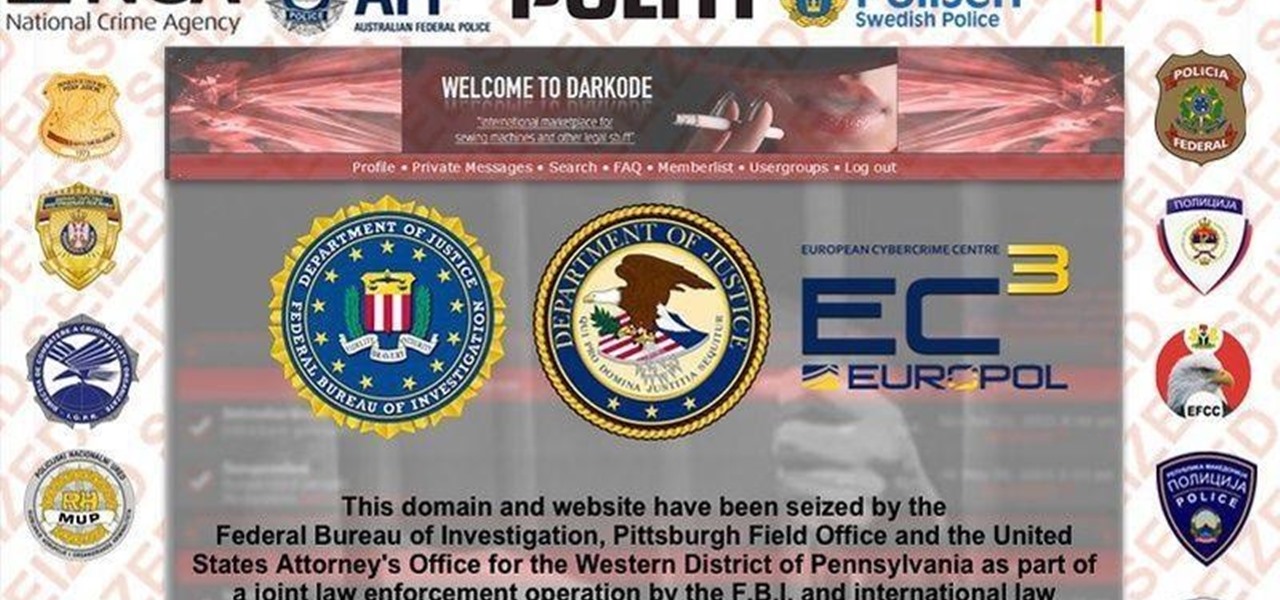
FBI has taken down a notorious hacking forum called "darkode" where cyber criminals bought, sold and traded hacked databases, stolen bank accounts, and malicious software that steal information from other computer systems and helped each other to infiltrate other computers. The FBI called the site one of the most serious threats to data security in the world. criminal charges has been filed against 12 individuals who were associated with the forum and the investigation is still ongoing, more ...

This Revit Architecture 2009 video tutorial covers how to create and control schedules. In this tutorial we schedule different wall types to manage the quantities of a buildings facade in Revit. If you are a beginning Revit user, check out the video and learn how to use schedules properly.

This Revit Architecture 2009 video tutorial covers how to use conditional statement when scheduling curtain panels. The techniques put forward in this intermediate Revit tutorial are done in an effort to avoid making different families for one curtain system. By using techniques like these, one can manage variable parts within one Revit Family while making it easier ti manage a schedule. This video is part of a series David Fano is working on, in which he hopes to show ways Revit can be used ...

Hello world! I thought it was about time that wonderhowto had its own World of Warcraft community. A place where gamers from all over the real world can come together to discuss the in and outs of the biggest and best MMORPG.

When I was unemployed I looked for different ways to make money. Most of that work was connected with online stuff; I’ve tried writing content, refreshed my old Photoshop skills and even created postcards, but then I realized that my passion to music can bring me more money than all of the other work. I was an active member of a few musical forums and started to add affiliate links to my posts instead of simple ones, so they can be profitable.

This awesome seed of survival island (Oliver Anderson) Found by A8OrAnGeJuIcE on Minecraft forums. The seed spawns you on this awesome survival mountain with a pool at highest altitude, a waterfall, a cave, a beach, and 3 trees and a great biome to work in.

Cool world. Check it out and post your ideas to the forum.

This forum has a discussion about painting PVC that has some opinions from very accomplished people, including Volpin Props. They go over primers, adhesion promoters, sanding and more, and if you see these people's work, they are the go-to guys for informed ideas on this subject.

This is actually a forum page, but they're discussing making you own finder scopes and medium power telescopes. There's a lot of information here.

This is that one that is in incomplete form in the furniture forum.