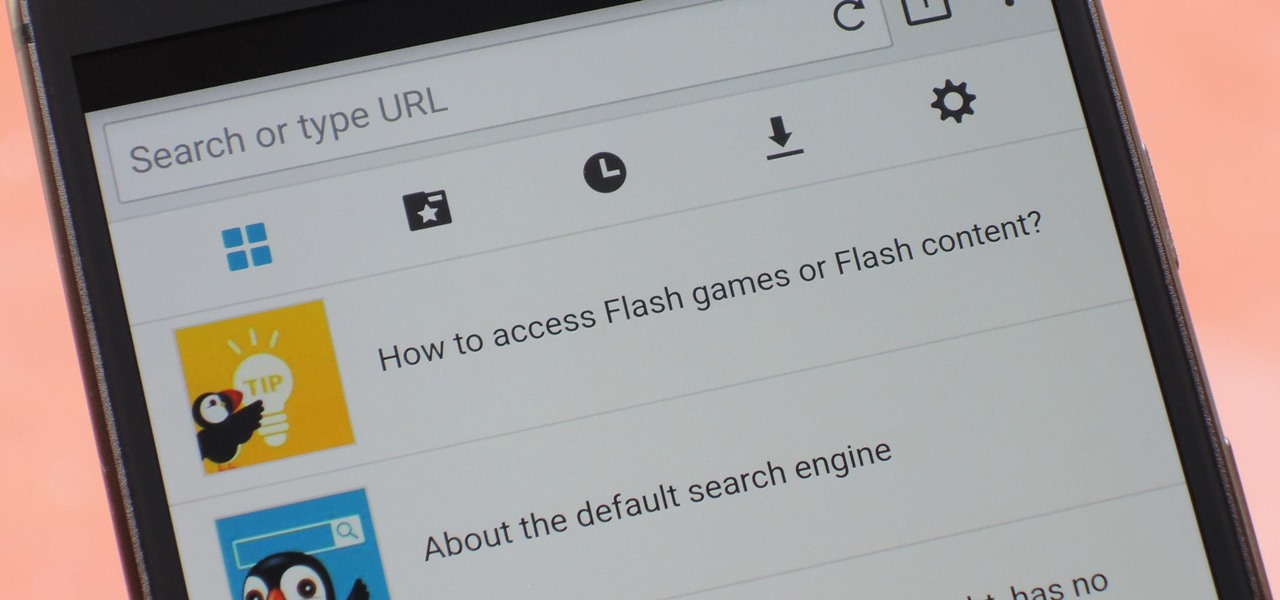
Once upon a time, Flash games reigned as some of the best entertainment the internet had to offer. But then came the smartphone, which quickly overtook this genre with similar games that you could play no matter where you were. If you yearn for the good old days, though, you'll be happy to know that you can still use the Puffin browser to safely play old favorites and discover new gems.

In this first part of our tutorial series on making physical objects come to life on HoloLens, we are going to set up Vuforia in Unity.
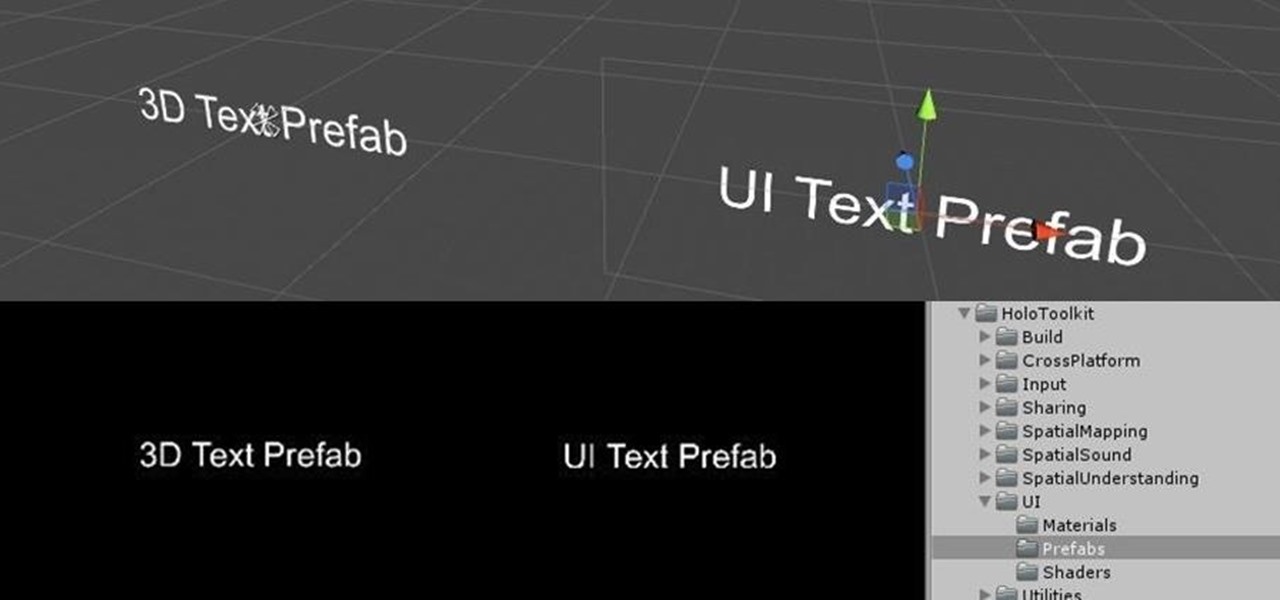
You may remember my post from a couple weeks ago here on NextReality about the magical scaling ratios for typography from Dong Yoon Park, a Principal UX Designer at Microsoft, as well as developer of the Typography Insight app for Hololens. Well, his ideas have been incorporated into the latest version of HoloToolkit, and I'm going to show you how they work.
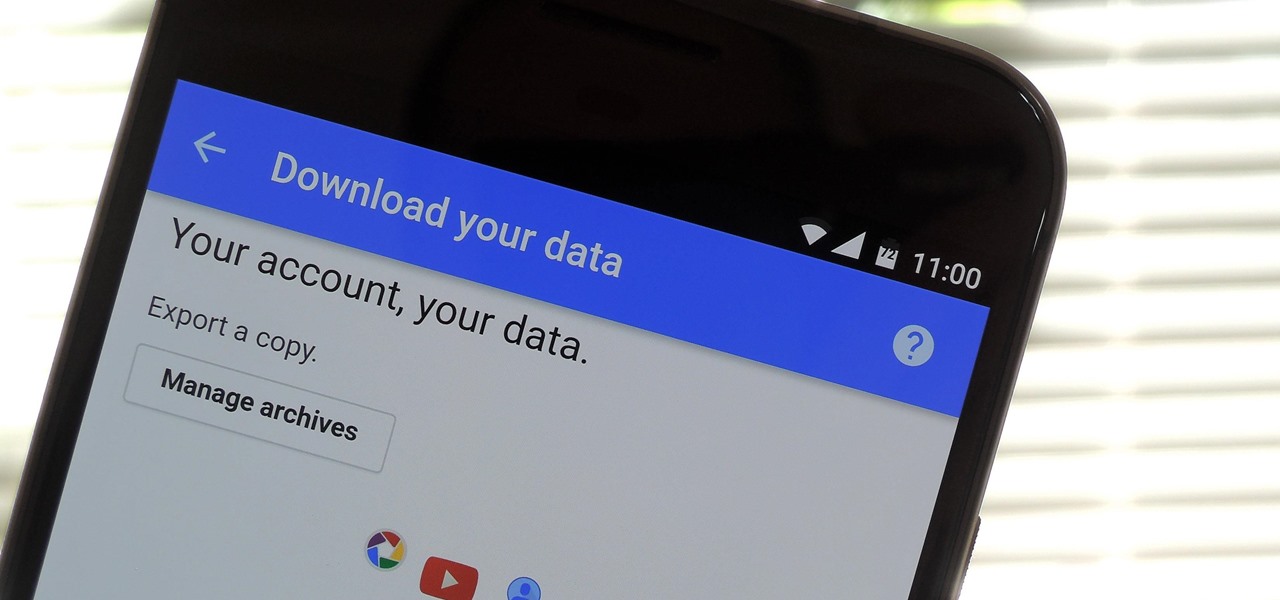
If you're an Android user, Google probably has almost your entire digital life stored on its servers. Family pictures are backed up on Google Photos, your e-book library resides with Google Play Books, videos are on YouTube, chat logs in Gmail and Hangouts, starred places and location history in Google Maps, and so much more.
No matter which smartphone you buy, it will come with an internet browser preinstalled. Depending on your OEM, the default browser might be called Samsung Internet, HTC Internet, Silk Browser by Amazon, ASUS Browser, or Google Chrome—there's just so many stock browsers available.

Finding Pokémon in the wild isn't the only way to add to your collection in Pokémon GO—you're also able to hatch your own from eggs that you've gotten from PokéStops.

Google seems to be growing tired of the way links appear in its Search results page, because they're currently experimenting with a color change (that's already causing lots of controversy).

Amazon just unveiled the Kindle Oasis, the latest model in its popular line of e-readers. There are a couple of nice new features, but it's pretty hard to see how any of them justify the whopping $290 price tag (or $310 if you don't want ads littering your screen).

Nobody's supposed to know where the Batcave is, but as most everyone thought, Batman's underground lair lied below the estate of his secret identity, Bruce Wayne, in Gotham City.

Welcome back, my hacker novitiates! In the previous part of this series, we looked at how to use Metasploit's web delivery exploit to create a script to connect to a UNIX, Linux, or OS X machine using Python. Many members of the Null Byte community have asked me, "Can we do the same for a Windows systems?" The answer is YES!

Whether you're ready to admit it or not, we've all got our alter egos—especially when it comes to the internet. Perhaps you have one Facebook account that you use publicly, while maintaining a second account for more private interactions.

Spaghetti squash is a versatile vegetable, but it has a reputation for being intimidating to prepare... not to mention time-consuming. Heating it up in the oven can take at least 30-40 minutes, which is a definite time-suck for those who want to get dinner on the table, stat.

OS X is built upon a UNIX foundation, which grants you access to the benefits that UNIX offers, including the standard toolkit (make, gcc, clang, git, perl, svn, size, strings, id, and a lot more) via the command line developer tools, which are an essential if you're a developer. Aside from developers, the command line tools can offer benefits to normal users as well, like the ability to purge RAM for better performance.

Some of the best images I've seen were shared via Snapchat, but once they're expired, they're gone forever, with no way to view them again unless I want to take a screenshot. But that will, of course, alert the sender.

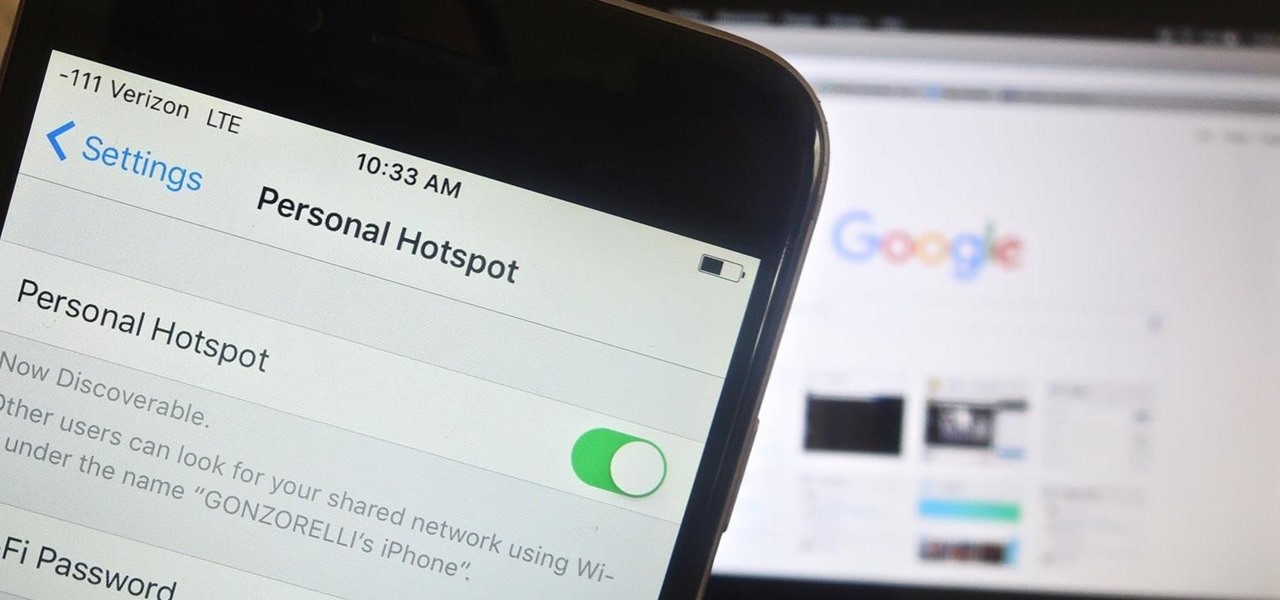
When you're in a bind and need an internet connection for your laptop, look no further than your iPhone. Using the Personal Hotspot feature in iOS, you can share your iPhone's internet connection with other devices by way of Wi-Fi, Bluetooth, or even USB.

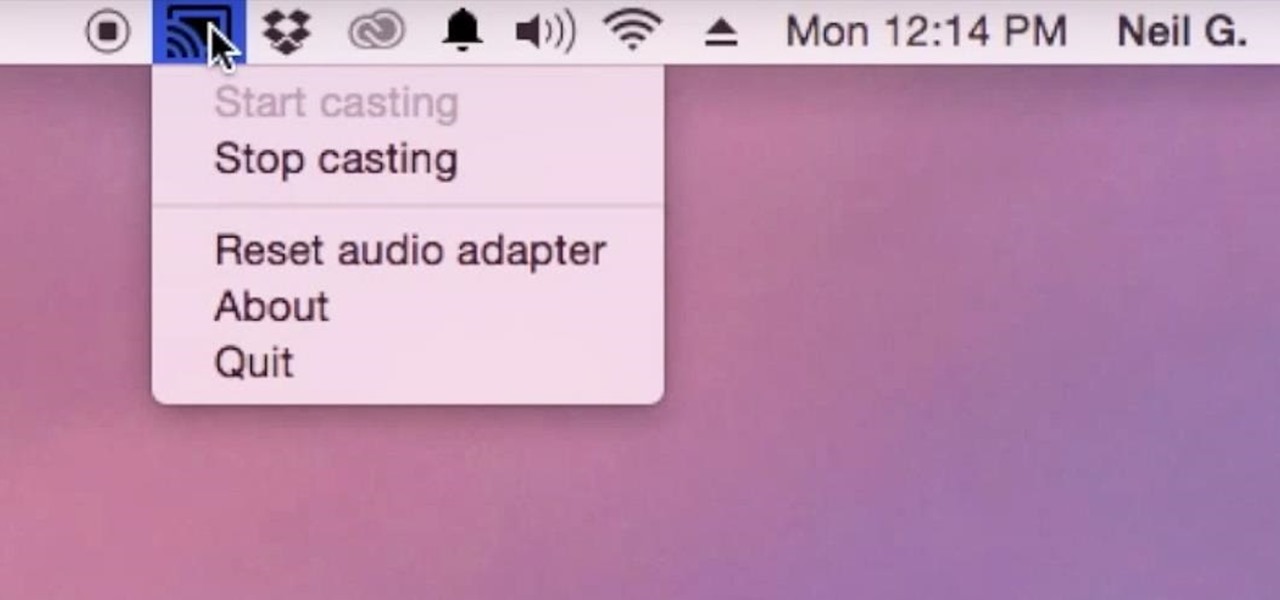
Although I know it will never happen due to Apple and Google's tempestuous relationship, I sometimes wish I could cast iTunes or Apple Music from my Mac to Google's Chromecast. When you don't have speakers to blast your music, the television is a great alternative to amplify your music.

Welcome back, my novice hackers! As most of you know by now, a notorious commercial, legal hacking group named "Hacking Team" was recently hacked. As part of the hack, thousands of emails and other material on their servers was divulged. Among the material released were three zero-day exploits. In this tutorial, we will walk through the steps to load one of them, which has become known as the CVE-2015-5119 exploit.

A good chef's knife is a thing of beauty and, with proper care, a joy forever. It can totally change the way you cook and turn even the dullest prep work into a glee-filled task.

At first glance, mandolines seem like such a good idea. After all, who wouldn't want a tool that can create picture-perfect and paper-thin slices of fruits and vegetables that would put even the sharpest chef's knife to shame? Your French fry game would never be the same. Salads would become works of art. Your casseroles would cook perfectly evenly, since the ingredients would be cut uniformly.

Welcome back, my novice hackers! As we saw in my first tutorial on Facebook hacking, it is not a simple task. However, with the right skills and tools, as well as persistence and ingenuity, nothing is beyond our capabilities.

It's a shame that one of the world's tastiest foods can be such a pain to prep. Most cooks are familiar with this conundrum: chopping or crushing garlic releases a pungent liquid that causes bits of garlic to stick your knife and hands, creating a messy affair. So what is going on here? The common assumption is that the garlic is releasing some kind of oil, but the truth is that this liquid rinses away easily in water. Yet one of the basic precepts of chemistry is that oil and water don't mix.

Coffee shops are a relaxing place to get work done on your laptop; there's free Wi-Fi, fresh coffee, and people generally leave you alone. Inevitably, those cups of coffee will go straight through you, resulting in a much-needed bathroom break. But while you're attending to your bodily functions, who's attending to your MacBook?

BlinkFeed completely changed the way I access new updates from Facebook and Twitter, but when I switched to the Google Play Edition of the HTC One, I lost access to the launcher. BlinkFeed is available in the Google Play Store, but HTC has not opened it up yet for all devices yet. While there are ways to port BlinkFeed over to other devices, it's reliability is dependent on the ROM, sometimes causing bugs and crashes.

Coffee is a topic that everyone has a strong opinion about, especially when it comes to brewing the perfect cup. Even if you buy the best beans and grind them yourself, chances are you're skipping one necessary step to make sure your coffee tastes the best it can: cleaning your coffeemaker the right way.

In early-2014, Facebook had the brilliant idea of auto-playing all of those annoying videos in your news feed that you never wanted to see in the first place. Fortunately, they realized their mistake and have provided a way to disable auto-play, which means you can now get rid of some of those plugin-blocking browser settings you have enabled.

Recipes are invaluable to cooks who are just starting out, but what if you want to get to the next level? Then it's time you learn how to apply simple math to food. In other words, learn how to cook using ratios, not recipes.

Welcome back, my greenhorn hackers!

Welcome back, my greenhorn hackers! Earlier in this series, I showed a you a couple of different ways of fingerprinting webservers. Probably the easiest way, is to use netcat and connect to port 80 and pull the webserver banner.

Whether it's because you want to make a quick tutorial video or want to show off your gameplay skills, recording the screen your Nexus 7 tablet isn't an easy feat. At least, until now. Hidden inside Android 4.4 KitKat is a built-in screen capturing feature, but it takes a little effort to dig it out.

What can be said about Spotify that most of us don't already know? It's the most popular digital music streaming service out there, giving you access to millions of songs on your computer. However, the mobile service was once an exclusive feature for paid subscribers. Not anymore, suckers.

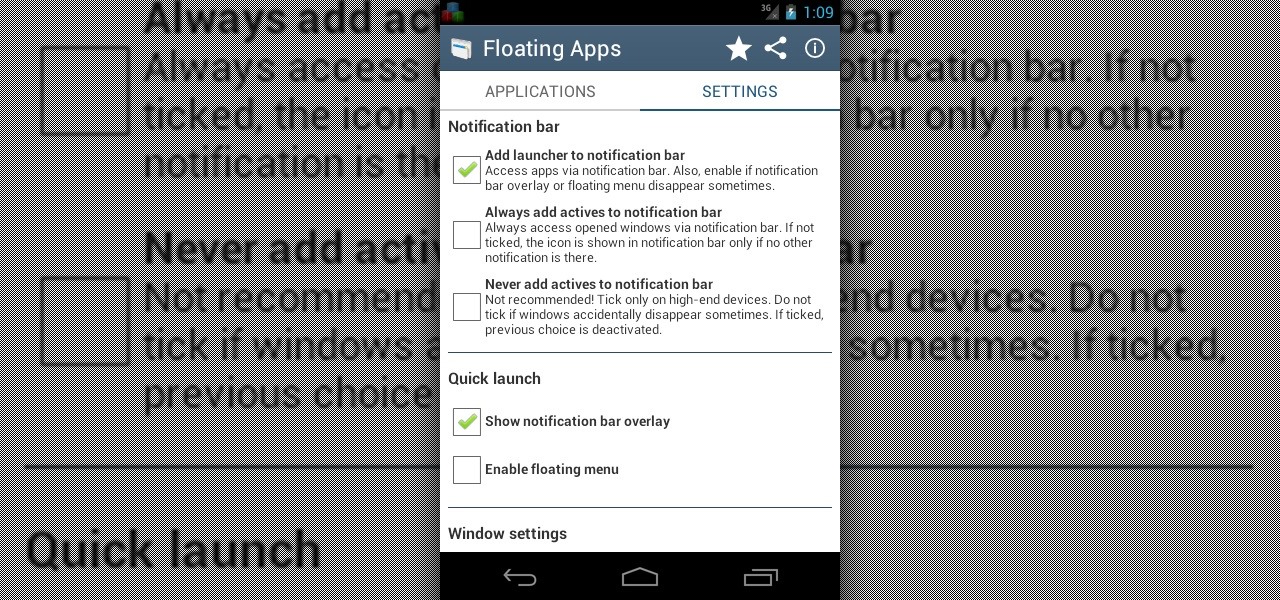
Sometimes, it's very useful to be able to use more than one app on Android phone or tablet. For example, if you want to watch a movie while surfing or if you need calculator, find some contact, write a note, search web or wikipedia for some facts, etc.

For the first time ever, iPhones will be getting live panoramic wallpapers in iOS 7, but it's something Android devices have always embraced.

Welcome back my fellow hackers! In my last few articles, I've concentrated on what is called a listener, which is basically the same thing as backdoor and rootkit, only "listener" sounds much less malevolent than the other two terms.

Like most new things, the Start Screen in Windows 8 has its adorers and detractors, but either way you slice it—it's here to stay. I'm still getting used to the Start Screen, so I'm not sure if it's a love or hate feeling yet, but I do know one thing—I want my own background!

Do Not Disturb is the best way to block out all interruptions on your iPhone without having to power down. All notifications and alerts are silenced, but the same can't be said for phone calls. By default, repeat calls will bypass Do Not Disturb, which can be quite frustrating when you're in a movie, classroom, or board meeting. It's good for emergencies, but not for people who can't take the hint.

Semi-untethered jailbreaks are here to stay, as evidenced by iOS 11's Electra method, Chimera for iOS 12, and even the new bootrom-based Checkra1n tool for iOS 13. While not as convenient as fully untethered, re-enabling a semi-untethered jailbreak is still pretty easy once you get used to the steps involved.

One of the major additions in the Google Pixel 4 is the new Soli chip. It's the miniature radar sensor that powers Motion Sense, a new way to interact with your phone without touching it. There are a few new gestures you'll need to learn to take advantage of Motion Sense, so let me break them down for you.

Every model iPhone since the 6s has boasted a 12-megapixel rear camera. You can take some pretty spectacular, professional-looking photos with it, especially on devices that have more than one rear lens. But the file size of each photo can become a problem when sending as an iMessage, which can eat up data.

NetBIOS is a service that allows for communication over a network and is often used to join a domain and legacy applications. It is an older technology but still used in some environments today. Since it is an unsecured protocol, it can often be a good starting point when attacking a network. Scanning for NetBIOS shares with NBTScan and the Nmap Scripting Engine is a good way to begin.

To combat their poor coverage in rural areas, T-Mobile spent nearly $8 billion on 600 MHz spectrum in 2017, which was converted to LTE Band 71. With such a low frequency, the signal can travel further, providing LTE speeds to more Americans. But your phone also has to support this frequency, and so far, only a handful do.