
How To: Turn Your Nexus 4 or Nexus 5 into an LG G2 Clone
The advent of a new Nexus phone begins with the bigwigs at Google partnering with a manufacturer, then selecting that manufacturer's flagship as the model for the new Nexus hardware.


The advent of a new Nexus phone begins with the bigwigs at Google partnering with a manufacturer, then selecting that manufacturer's flagship as the model for the new Nexus hardware.

You probably already know by now that a custom Android ROM can change your user experience and give you what feels like a new OS on your device, and there's no shortage of them out there to try out.

The holidays are quickly approaching, which means everyone will be scrambling over the next couple of weeks to find the cheapest options for flights to wherever home is. There are so many sites to buy them from that it can be hard to know where to start, so we've compiled some tips and tricks for making the process as painless as possible, whether you're flying home for Thanksgiving, Christmas, or whenever.

Old people are usually perceived as wise and enduring, whereas an old smartphone, like my iPhone 4, becomes the butt of a joke every time I take it out of my pocket. I mean, come on, it's not like I'm still rocking one of these... And if I was, I guarantee you wouldn't beat my score on Snake.

It may not be as large as the Samsung Galaxy Note 2, but the Galaxy S3's screen size is still big enough to make iPhone owners cry themselves to sleep. The 4.8-inch AMOLED display with 720 x 1280 pixels makes the GS3 a great mobile companion—and an even better portable gaming device.

Back in 2010, iOS developer Daniel Amitay developed a camera security app for iPhones that used an unlock screen almost identical to that of the iPhone.

What I'm going to do in this tutorial is, as the title implies, teach you how to make nearly anything look like metal. This can especially come in handy in Steampunk, as most of us don't have the ability to machine brass. We do, however, have access to wood, PVC, and spray paint. Not to mention that, as a costumer, I can speak from personal experience when I say that things made of brass are really, really, really heavy!

Learn music theory from music instructor Mark W. Black, owner & founder of "Promethean Studios" Dallas, as he teaches basic essentials of music theory for beginners in this video series. Mark covers such topics as: the staff, treble clef, bass clef, how to identify notes on the staff, measure, pitch, the quarter rest, ledger lines, notes above the staff, half-notes and whole-notes, counting beats, rests, intervals and counting intervals, half-steps, guitar half steps, characteristics of Weste...

This video series is a must for anyone thinking of paragliding at all but especially powered paragliding. Our expert, Hugh Murphy, is the owner of his own para gliding company and he will walk you through every aspect of a powered paragliding trike from getting into the harness properly to how to stand up with the motor attached to your back to how to take off and land.

Learn music theory and learn to write songs from music instructor Mark W. Black, owner & founder of "Promethean Studios" Dallas, as he teaches advanced topics of music theory and songwriting for beginners in this video series. Mark covers such topics as: lyrics, rhyming, mood and consistency, melody, step back, tension and resolution in a melody, consonants and movement, combining harmony with lyrics, chords and emotions, how chords effect the mood, chord usage, language of chords, normative ...

It's been done for ages, but for most of us, "regift" entered our vocabulary after the 98th episode of Seinfeld—"The Label Maker." In this episode, Elaine calls Dr. Whatley (played by Bryan Cranston) a "regifter" after he gives Jerry a label maker—the same label maker that Elaine gave Whatley.

On June 7, Apple will reveal to developers what's in store for its upcoming operating systems, but anyone can watch the livestream to see all the new features coming this fall to iOS 15, iPadOS 15, macOS 12, tvOS 15, and watchOS 8.

After integrating Snapchat into its latest Galaxy A Series smartphones, Samsung is trying out a new AR camera app for its army of mobile devices.
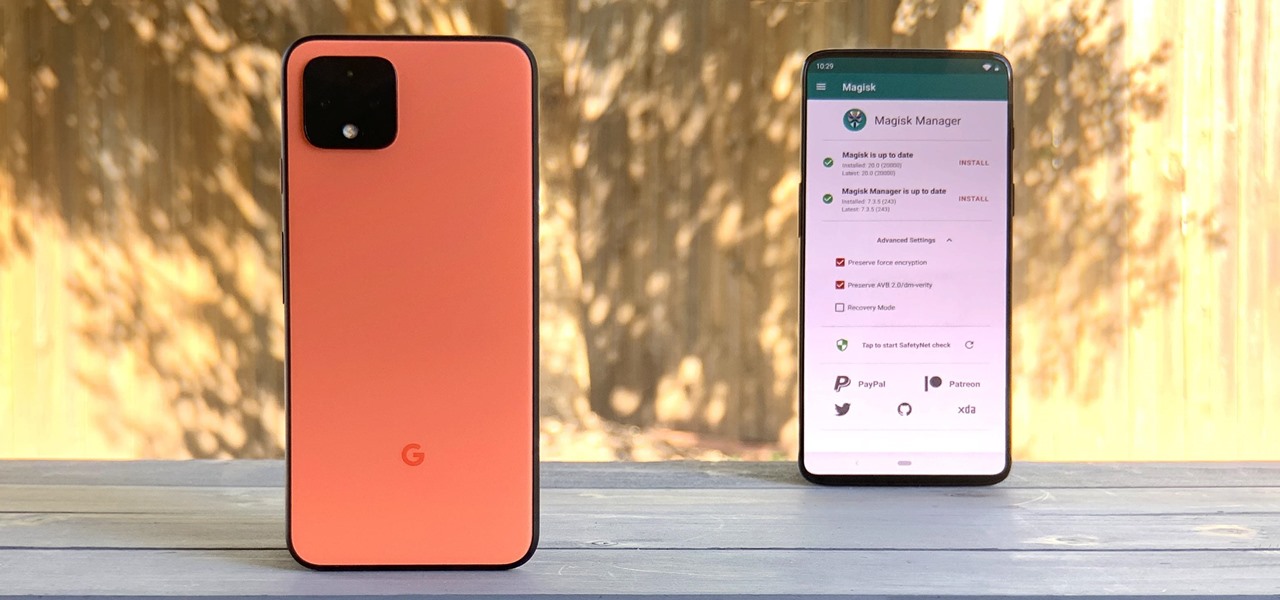
According to a study done by Kaspersky, 7.6% of Android users root their phones. That may not sound like a lot, but with over 2 billion Android devices out there, the math works out to over 150 million rooted phones — more than the total population of Russia, Mexico, or Japan — so root nation is an important demographic that deserves being catered to.

You may not have thought of dorks as powerful, but with the right dorks, you can hack devices just by Googling the password to log in. Because Google is fantastic at indexing everything connected to the internet, it's possible to find files that are exposed accidentally and contain critical information for anyone to see.

Kali Linux is probably the most well-known hacking distribution among penetration testers. However, there are alternative distros which offer versatility and advanced package management systems that are absolutely worth considering.

Cracking the password for WPA2 networks has been roughly the same for many years, but a newer attack requires less interaction and info than previous techniques and has the added advantage of being able to target access points with no one connected. The latest attack against the PMKID uses Hashcat to crack WPA passwords and allows hackers to find networks with weak passwords more easily.

Leaked databases get passed around the internet and no one seems to notice. We've become desensitized to the data breaches that occur on a daily basis because it happens so frequently. Join me as I illustrate why reusing passwords across multiple websites is a truly awful practice — and compromise hundreds of social media accounts in the process.
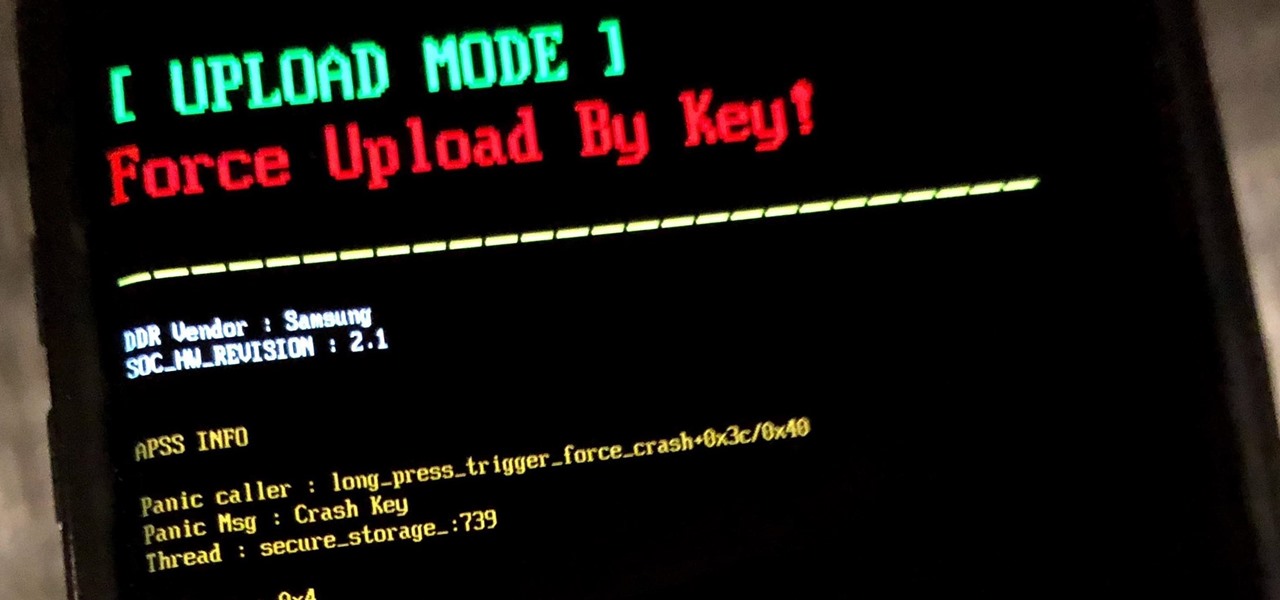
If you own a Samsung phone and enjoy rooting or modding your device, flashing official firmware can be very useful. Odin is Samsung's own internal program for loading such updates for testing purposes, and it's quite easy to use for your own custom modification needs.

JavaScript is one of the most common languages used on the web. It can automate and animate website components, manage website content, and carry out many other useful functions from within a webpage. The scripting language also has many functions which can be used for malicious purposes, including stealing a user's cookies containing passwords and other information.

Quanergy CEO and founder Louay Eldada is, by any standard of measure, a pioneer in the development of LiDARs for driverless vehicles.

While the world is only recently becoming aware of its existence, augmented reality has been around in some form or another since the '90s. In the last decade, with the advancement and miniaturization of computer technology — specifically smartphones and tablets — AR has become far more viable as a usable tool and even more so as a form of entertainment. And these are the people behind mobile AR to keep an eye on.

At a global security conference in Munich, philanthropist and businessman Bill Gates spoke about the next pandemic and a dire lack of global readiness. Here's how his statement could come true—and how to be ready when it does.

Gmail has been the email standard for quite some time now, and for good reason: it's a free service provided by one of the largest tech companies in the world that offers users an amazing feature set to manage, send, and keep track of all their important emails.

Hello people again, I wrote my last post about crypto about 10 months ago, now I will introduce something not fresh for the science, but fresh for the people who wants to learn. In my http://null-byte.wonderhowto.com/forum/cryptography-0161538/ post of crypto concepts, there is just basics, today we will see something that targets wide concepts like Symmetric crypto, Public Key Cryptography, Hashing, Keys etc...

Greetings my fellow hackers.

Greetings aspiring hackers. I have observed an increasing number of questions, both here on Null-Byte and on other forums, regarding the decision of which USB wireless network adapter to pick from when performing Wi-Fi hacks. So in today's guide I will be tackling this dilemma. First I will explain the ideal requirements, then I will cover chipsets, and lastly I will talk about examples of wireless cards and my personal recommendations. Without further ado, let's cut to the chase.

Hello readers, and welcome to Null Byte. Before we start, for those of you who may not know me, my name is ghost_; I'm a relatively active member of our community and have been around for a while.

If you've ever owned an HTC device or anything in the Nexus line, odds are, you have typed the word "fastboot" into your command line at one time or another. That said, odds are, you have only just barely scratched the surface of what this handy little Android tool can do. Let's take a deeper look.

Anyone who has rooted their Android device has likely used a tool called Android Debug Bridge, better known as ADB, at some point during the process. For most, that is their only interaction with the ADB, but to be a true Android power user, you need to really know the tools at your disposal.

As a species, our cells are designed to use sugar for energy. Is it any wonder that as humans evolved, we grew to love the taste of sugar?
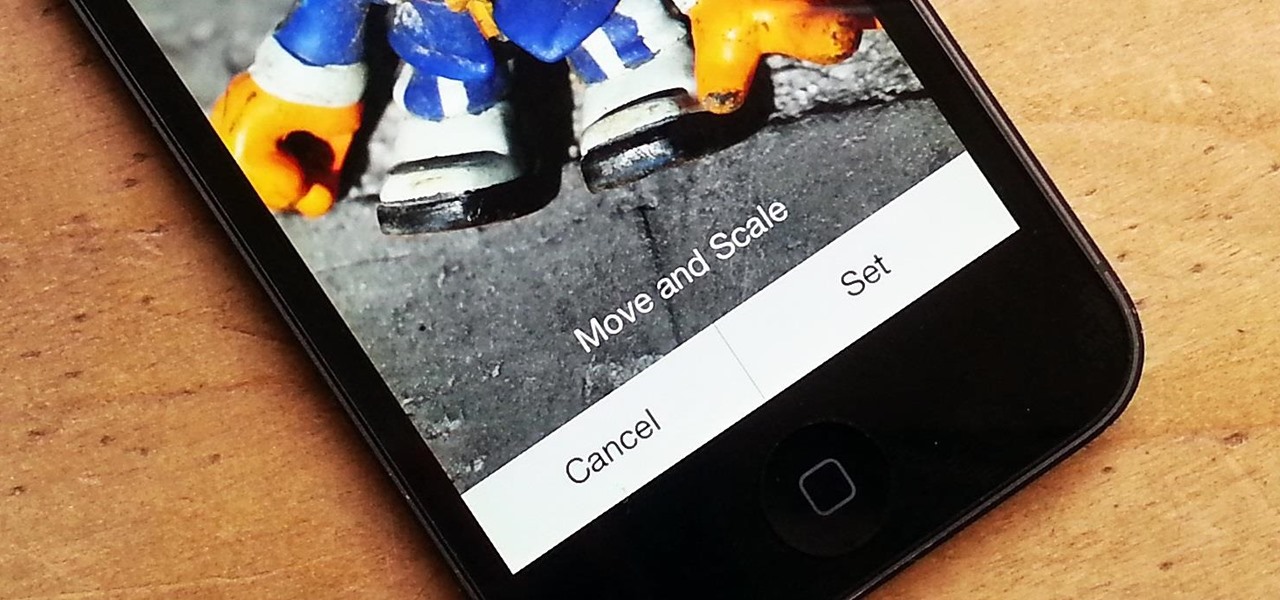
There are definitely some great things about iOS 7, but like any good piece of software, it's got some things to kink out—and how wallpapers work seems to be one of the biggest issues, since it's so much different than in previous iOS versions.
Below are the official rules and guidelines for submitting content to WonderHowTo. Please look over them before publishing any articles. Ignoring the rules could result in deletion of your article or being flagged as a spammer. Most of these rules apply to comments as well.

In my last article, I explained why text adventure games are some of the most Steampunk computer games out there. I even shared a free Steampunk text adventure game that I'd made myself!

Let's say that you've got the look down, and you have your Steampunk props all ready to go. Congratulations! You're a Steampunk!

Are you interested in beginning research of your family's history? I began this journey about 3 or 4 years ago and here is what I found. I've done almost ALL of my research online, and gotten farther, faster and more comprehensively than anyone else who has researched my family the old fashioned ways. This is the kind of thing that technology is made for. Here's how to use it.

If you read my article on the OSI model, you got a good overview on communications from that model's perspective, but how does that relate to TCP/IP? We're going to take it a step further, getting into the idea behind the two address concept. How does an IP address and a MAC address work together? If you want to hijack sessions and all sorts of lulz like that, you need to understand these concepts. Let's get into it, mates!
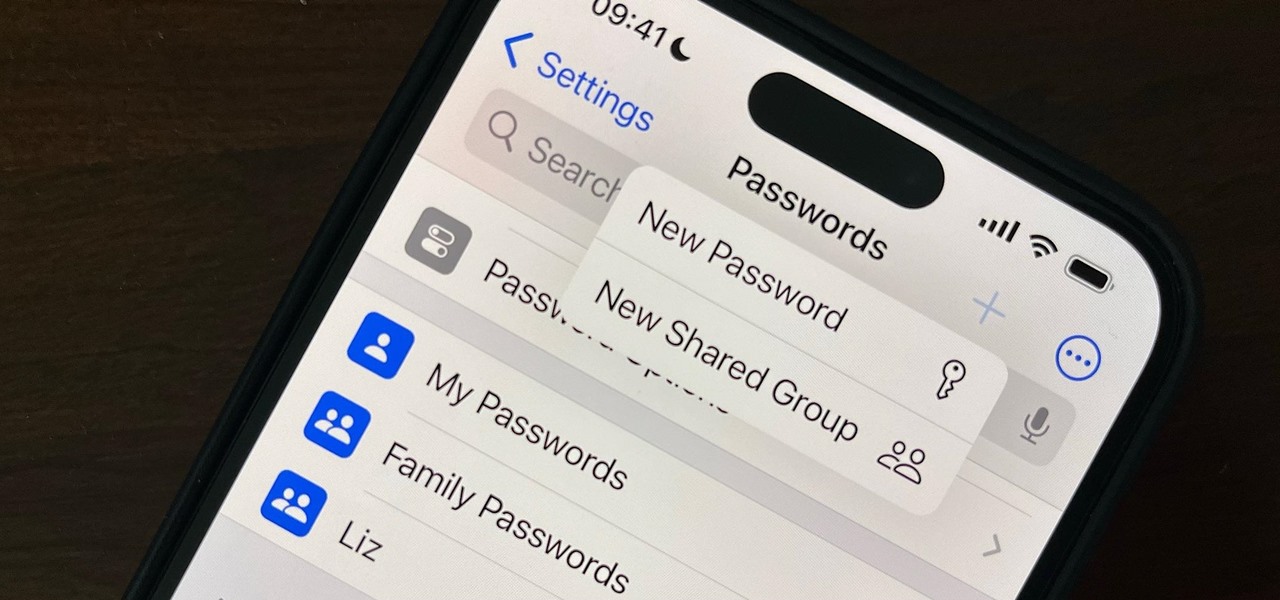
Previously, you'd have to use a third-party password manager on your iPhone, iPad, or Mac to securely share passwords with other people or groups outside of AirDrop range. And while apps like 1Password, Bitwarden, and Dashlane let you store passkeys, only 1Password has added support for passkey sharing so far. Now, Apple itself makes sharing passwords and passkeys much, much simpler.

There are a surprising number of hidden features in your iPhone's Phone app, from secret dialer codes that provide info or perform actions to special characters that dial extensions automatically. However, there's one little-known trick every iPhone owner should know when using the Phone app for calls — and it's the simplest and most useful of them all.
If you own a Google Pixel 4a or newer, there are new live wallpapers for you to explore that other Android devices can't have.