Opioids, or narcotic painkillers, serve as our primary method for alleviating physical distress. They also happen to be a leading cause of death due to their addictive nature. AppliedVR hopes to introduce a safer alternative: virtual reality gaming. They utilize the existing Samsung Gear VR for the hardware, but provides specialized software that offers up a distracting experience that fosters greater pain ignorance.

Hello, hackers and engineers! Today we are going to dive a tiny bit deeper into the secrets of psychology, and how we can use them with hacking and social engineering attacks.

If you're using iOS 10 or lower, there is no built-in way to record an iPad, iPhone, or iPod touch screen, and Apple doesn't allow any third-party apps to screen record either. If malicious, an app could theoretically continue recording even after you think it's off, allowing it to capture account and password information that you enter on your device. This changes in iOS 11, which introduces native screen recording, but what do you do if you're still running iOS 10 or lower?

This is evil and it destroys people. Let's just get that out of the way. Nonetheless, suppose you need to make someone distrust their own memory and perception of reality. Suppose you want someone to believe in you more than they believe in themselves.

The one man Sam Fisher trusts, Victor Coste, has some information for him. To find out the intelligence, Sam has agreed to meet in person. Find out what the important intel is in this walkthrough for the Washington Monument (Mission 5), and where that lead Sam next.

Take a trip into the past as Sam Fisher gets captured by terrorists in the Iraq War. Instead of playing as Sam, you'll be playing the part of Victor Coste — the only man Sam trusts. Find out how Coste saved Fisher's life in this walkthrough for the Diwaniya, Iraq (Mission 4). What happens that day in Diwaniyah? Find out.

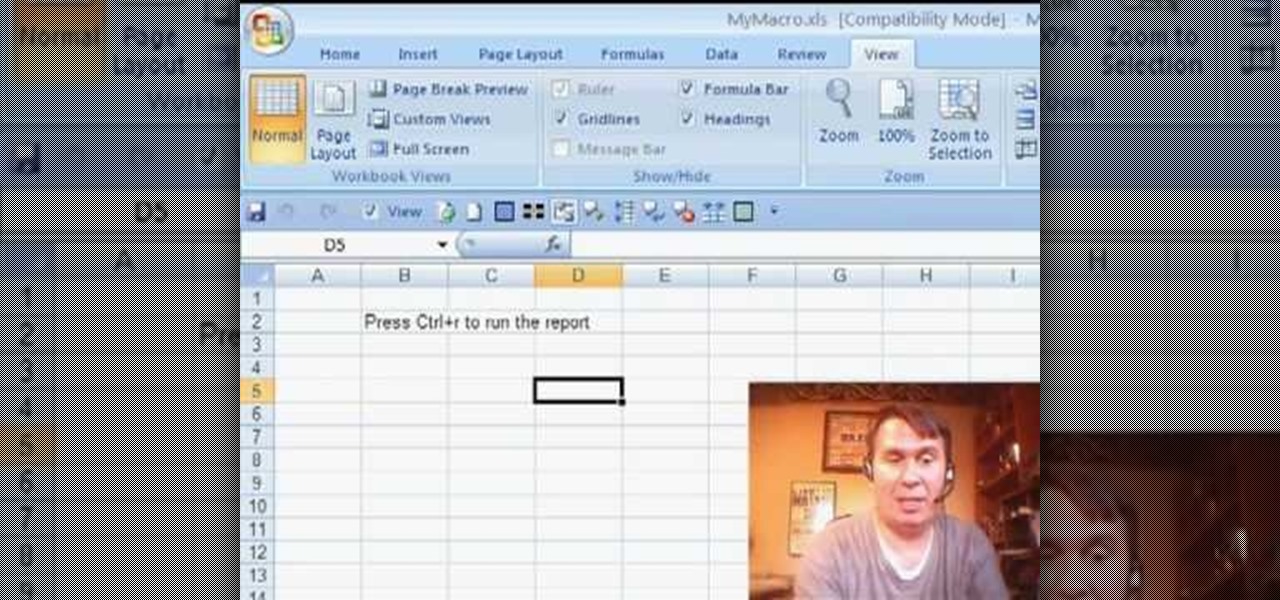
Some times when you upgrade your Microsoft Excel software to Excel 2007 your old macros may stop working. Some times this may be due to the settings and by enabling the macros you can get your old macros to work. Macros are turn off by default in Excel 2007. You can turn this on from the macro security settings. But the settings option is it self completely hidden. You cannot find it in any of the tabs present on the top of the program. Even the macros option present in the view tab has no se...

Abusive relationships are unhealthy and should be remedied immediately. There are many steps that can be taken to help end an abusive relationship.

Teaching your dog to sit establishes trust and also creates a foundation for other tricks. Learn how to teach your dog to sit with this dog training video.

If you've ever wanted to solve a Rubik's Cube and look like a genius, you're going to have to watch this puzzle solving video tutorial. This video will show you how to, yes, solve a Rubik's Cube.

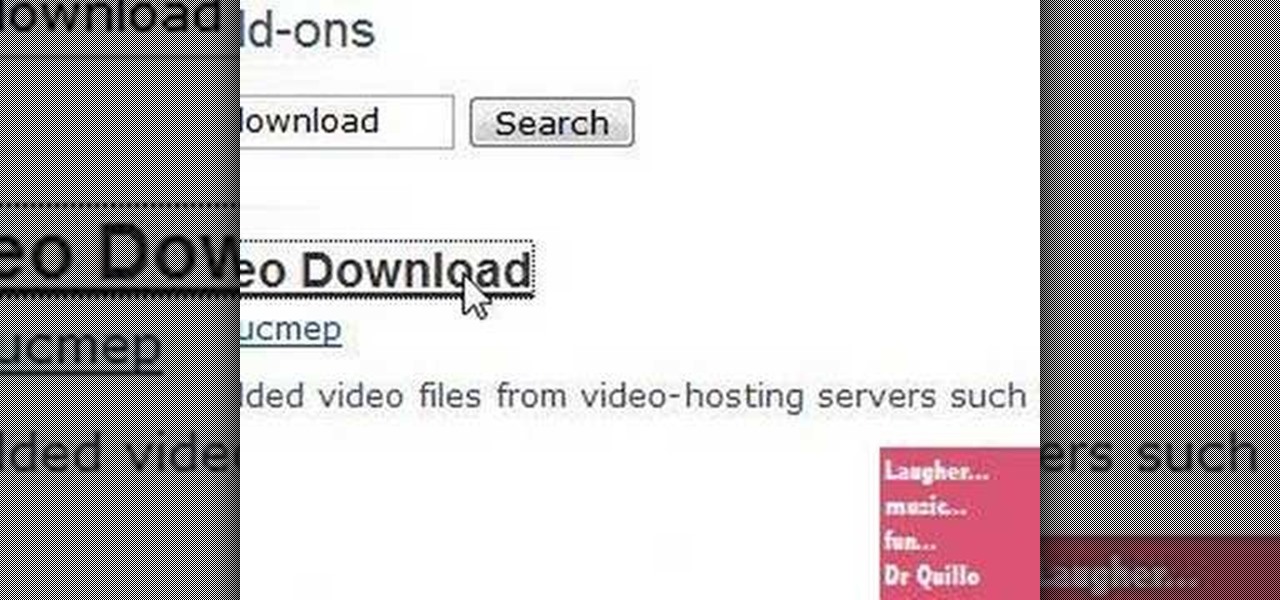
Dr.Quillo from Quillo video tutorial is explaining about downloading high quality wav sound files. According to him this is much more efficient, less time consuming and the result is of higher quality than using Audacity or winrec32. He asks us to use internet browser, preferably Firefox. He guides us through the process of downloading various tools like Mediacoder, virtualdub, fast video download through google or any search engine. Mediacoder is a freeway software device which converts .flv...

Soymilk is a well known alternative to milk for those who are lactose intolerant or just tired of regular dairy. You can spruce up regular soymilk by maing your own healthy recipe at home with oatmeal in addition to soybeans.

Cate Adair, a fashion consultant makes many important and useful points in how to find the correct bra size. The first point is that your bra size is constantly changing. Losing/gaining weight, as well as exercise can easily change the size of bra you need. Due to this, it is important to get measured frequently since your size can change. She also points out that different outfits require different types of bras. Cate gives the example that the perfect bra while wearing a t-shirt probably is...

Feebas is a special evolve thats both difficult to catch and quite difficult to evolve. Feebas needs to feel as beautiful as ever then have its level risin. This video will show you exactly how to evolve your Feebas into a Milotic.

Hypnosis can be used to manage pain, relieve anxiety, conquer phobias, prepare for childbirth, and cure insomnia, among other things. With a little practice and some simple techniques, you can amuse your friends or help them break a habit through hypnosis. Learn how to hypnotize someone with help from this how-to video.

Nexus is a pre-approved trusted traveler program that allows approved people expedited travel between Canada and the US. The card is available to US and Canadian citizens or permanent residents who travel by air or land between the two countries. Anyone traveling between the two countries must have their own Nexus card including babies. The Nexus card is considered a privilege by both the US and Canadian governments. You must have a clean record with both the Canadian Border Services and The ...

Have you ever found something funny in an awkward situation? When you feel a laugh coming, it can sometimes be hard to avoid. Check out these steps to stop your laugh before it gets you in trouble.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to build a motorcycle camera mount for under five bucks.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to homebrew and hack the PSP.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to analyze packet captures and network taps.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to extract Windows executables from packet captures.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to hide secret data inside a photo.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to backup and load Wii games for the Dolphin Emulator.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to build a free XMPP/Jabber server in ten minutes.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to track a USB device.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to edit Super Mario World levels with Lunar Magic.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to build a mini multi-touch table and photo stitch.

Learn how to play "Heal Over" by KT Tunstall on guitar, an acoustic guitar tutorial. Follow along with this demonstration, tabs and lyrics here:

This is the basic prayer that should be meant from your heart and soul, and not just saying the words from your physical tongue. A true redeeming confession to the lord Jesus Christ, asking Him to come into your heart as your personal lord and savior, asking Him to forgive you of all of your sins, rejecting all evil from continuing to be involved in your life, and rejecting this world's ways, and listening and following God's rules and directions.

Saw is no longer just a movie, it's a video game, and you can play it on the Xbox 360, PlayStation 3, and Windows. With this video walkthrough series from Committed Gamers, you can BEAT IT (for the Xbox 360).

Facebook and its Oculus subsidiary have been open about their intentions to bring AR wearables into the mainstream for some time now.

As the level of data being generated grows exponentially, past the Information Age and into the coming Hyper-Information Age of immersive computing — as resistant as many of us are to the idea — personal data security is becoming a necessary consideration in our everyday lives. Recognizing this, Mastercard, Qualcomm, and Osterhout Design Group have teamed up to show what secure shopping could look like in the very near future with iris authentication.

This article is to all the newbies on here wanting to become a hacker. Since I have seen many newbie questions on here, I need to address this.

Malware often disguises itself inside of seemingly non-malicious files, such as installer packages, where it can then gain root access to your computer to track activity or steal your information.

Inspiration for tutorial: Foxtrot's "How to Trap a Tracker"

While we now know that iCloud was not exploited by hackers to steal private celebrity photos, Apple did admit that guessed (aka brute-forced) passwords and/or iCloud security questions were to blame for the breach.

This is about how to make a rabbit become less wary of you and more trustful with you also. I myself have a Dutch that was released by its previous owner, then I rescued it. She never wants to be took out of her cage, but now she doesn't mind as long as I'm gentle and nice.

Merrill never fails to amaze. In this video, he instructs you to "come as you are— but bring a pencil." And you don't have to be a diehard Nirvana fan to understand what this tutorial's about— Kurt Cobain. Watch and learn how to draw Kurt Cobain in a portrait, step by step, using pencils and a few art tricks.

Heartbroken? If your girlfriend threw in the towel before you were ready, there are a few ways you can try to win her back. Follow along with this tutorial and try to mend your broken heart.

Striking up a conversation with a group of people you don't know can be an intimidating task. Come prepared with some interesting comments and ideas and you will be able to make new friends out of any crowd.