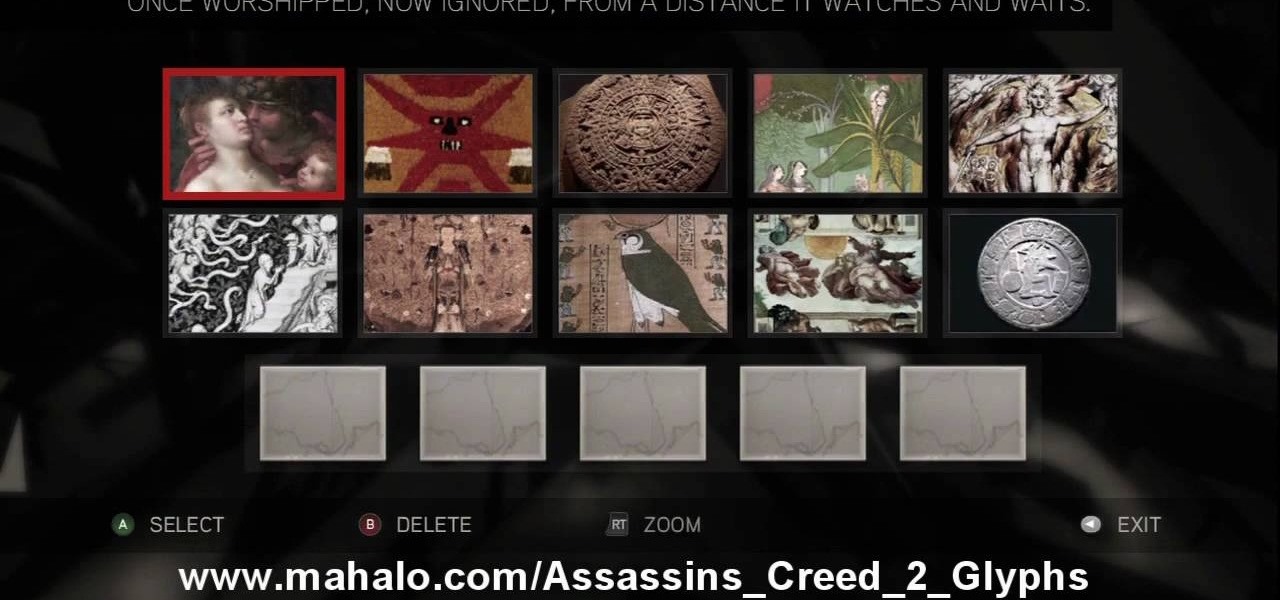
Here's the answers to the 19th puzzle, titled "The Fourth Day", in Assassin's Creed 2. Image set: What used to be worshipped by every primitive culture under the…? That’s right, the sun. Pick the five images that focus on it. Image: Find the tiny image of Earth in the lower-left quadrant of the sun. For more info, watch the whole gameplay.

And They're Off: Time's crucial in this missions, so be careful. You've got a limited amount of time to complete this fairly challenging obstacle course. A series of waypoint show up one after the other, and you've got to run through all sixteen of them, quickly. The first four are on ground level, so you don't waste time climbing any buildings. The fifth waypoint will start you on an ascent up the side of a building, and from then on you can expect next bunch to require some careful platform...

A Day at the Market: Talk to Lorenzo and he'll hand you another codex. Take it to Leonardo da Vinci across town and he'll translate it for you. For more info, watch the whole gameplay.
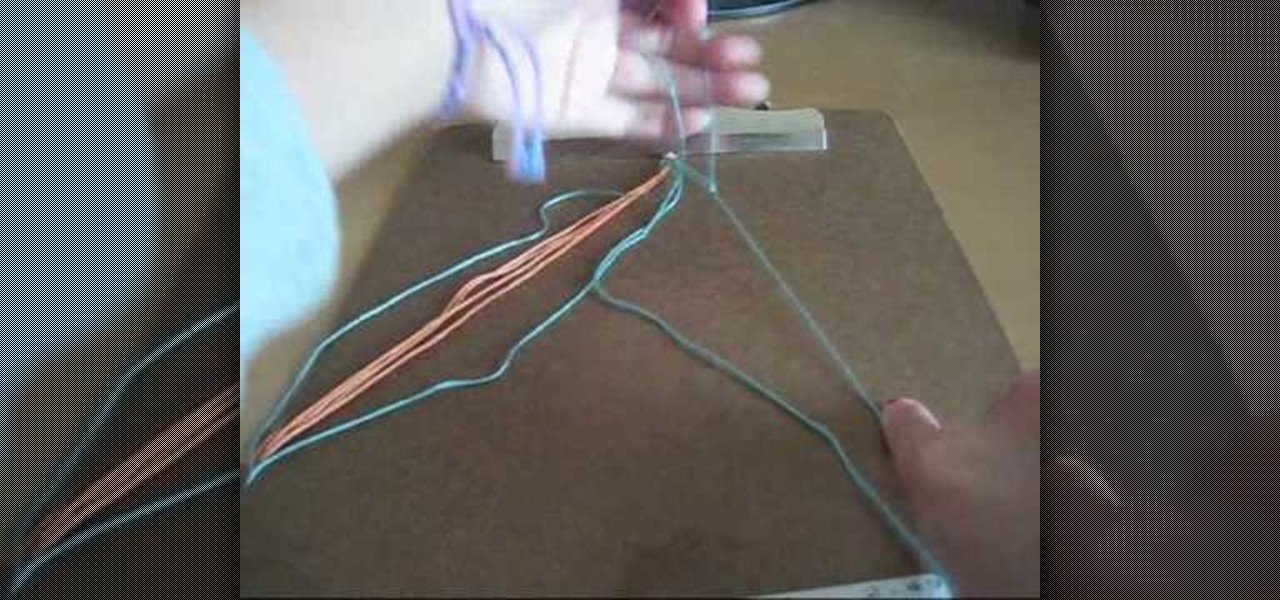
Showing a friend you really care is one reason to start making friendship bracelets. Not everybody wants to show off their friendship to everyone, but if you do, this video tutorial will show you how to make a friendship bracelet, specifically the alternating chevron friendship bracelet. This bracelet is the same concept as the regular chevron.

Abusive relationships are unhealthy and should be remedied immediately. There are many steps that can be taken to help end an abusive relationship.

Make your cat happy by giving them a sturdy scratching post. They'll sharpen their claws – without tearing up your furniture.

Turn old watch faces into appealing bracelets by using an eco-friendly recycling technique. You Will Need

Windows 7 is the hot, new operating system replacing the past XP and Vista systems. Windows 7 is the most simplified, user-friendly version that Microsoft has developed - ever. Get acquainted with your new version of Windows straight from Microsoft.

Tired of losing your gardening efforts to snails and slugs? Use these methods to banish the pests. You Will Need

Learn how to teach your dog to high-five. Make your pooch the hippest dog on the block by teaching him how to greet you with a high-five.

Teaching your dog to sit establishes trust and also creates a foundation for other tricks. Learn how to teach your dog to sit with this dog training video.

Have you ever wanted to jailbreak your iPhone or iPhone 3G or iPod Touch, but never really knew what it was or how to do it? Well fear not! The true video tutorial is here!

Check out this episode of Brian Brushwood's Scam School from Revision3 to find out how to pull the best cons, bar scams and magic tricks. It's rare to find a trick that you can actually fool yourself with...and that's exactly what you get with this episode!

K'NEX is one of the most popular construction toys on the market, right next to Lincoln Logs and LEGOs, but what makes K'NEX stand out is the fact that children can build mechanically derived toys. Instead of blocks or little logs, kids use interconnecting plastic rods and connectors, which give them tons of contraptions to build and play with. Today, K NEX has even more possibilities with wheels, pulleys, panels and flexi-rods to make amusement park roller coasters, airplanes, animals, bikes...

One day, your car may break down and you won't be able to afford to hire a mechanic, so what do you do... you look on the web for some how-to vehicle repair videos and become your own car mechanic, that's what. You don't need any advanced training to perform repairs and simple maintenance on your automobile, but you may need a few tools. Invest in the basic tools and you'll be prepared for just about any car malfunction you can think of. These tutorials will help get you on your way, as long ...

Do you like music? Do you like television? How about the acoustic guitar? How about Friends? How about the Rembrandts? Well, this video tutorial will show you how to play the theme song from the hit TV sitcom Friends. This instructional guitar lesson will teach you a few tips and tricks for playing the song.

Pyramid Head. You've heard the name before. You've saw him in action. Now cosplay as him. This costume could be used for Halloween, cosplay, or just for the hell of it. Pyramid Head is a fictional monster from the Silent Hill video game and movie. So watch this four-part video tutorial to see how to do it. If you can follow these instructions, you could never need another cosplay getup again. Unless you want to try out some anime or manga.

Watch this video series to learn how to start the conversion process of an Adobe Photoshop mockup of a website, into a real live CSS based website.

Learn how to do Smith machine inverted palms down pull-ups with release/re-catch at top. Presented by Real Jock Gay Fitness Health & Life.

Learn how to do Smith wide inverted pull ups with a hold at the top. Presented by Real Jock Gay Fitness Health & Life.

Learn how to do Smith machine inverted pull ups. Presented by Real Jock Gay Fitness Health & Life. Benefits

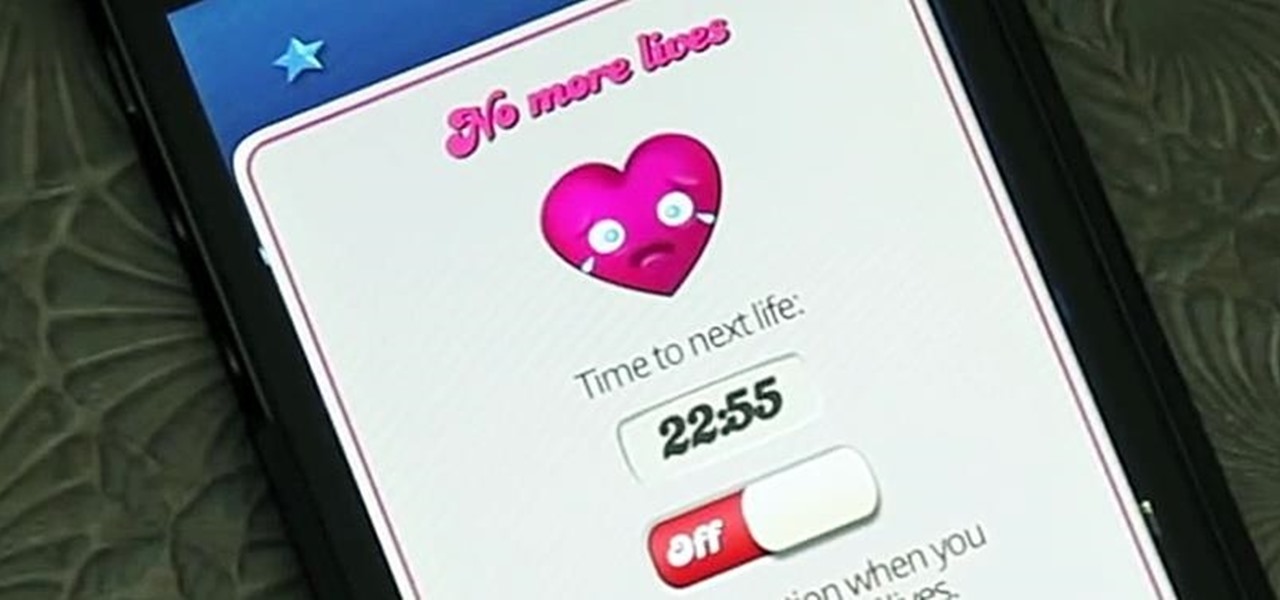
I hate waiting to play, and I hate bugging my Facebook friends even more. But that's what Candy Crush Saga makes you do if you want to get new lives and levels faster.

With protests springing up across America, there's a chance you may have your first interaction with law enforcement. Many demonstrators will have their phones in-hand to film the action, which, sadly, could prompt an officer to demand the device and any self-incriminating data it may contain. Before this happens, you should know there are tools at your disposal to protect your data in such situations.

One of the main goals of Google Wifi (and Nest Wifi after it) is to make managing your internet connections as simple as possible. A great example of this is how easy it is to prioritize one device and allot it more bandwidth when your network is bogged down with other traffic.

With today's release of iOS 13.4 developer beta 4, it seems Apple is closer than ever to releasing the official build for its upcoming iOS update. If you've been following the beta closely, you know that means new Memoji stickers, CarKey API support, and Mail toolbar updates, in addition to general bug fixes. Public testers can now take that extra step, as Apple just released 13.4 public beta 4 today.

After establishing itself as a leader among media companies in augmented reality in journalism over the course of 2018, The New York Times pulled back from the technology this year.

Web application firewalls are one of the strongest defenses a web app has, but they can be vulnerable if the firewall version used is known to an attacker. Understanding which firewall a target is using can be the first step to a hacker discovering how to get past it — and what defenses are in place on a target. And the tools Wafw00f and Nmap make fingerprinting firewalls easy.

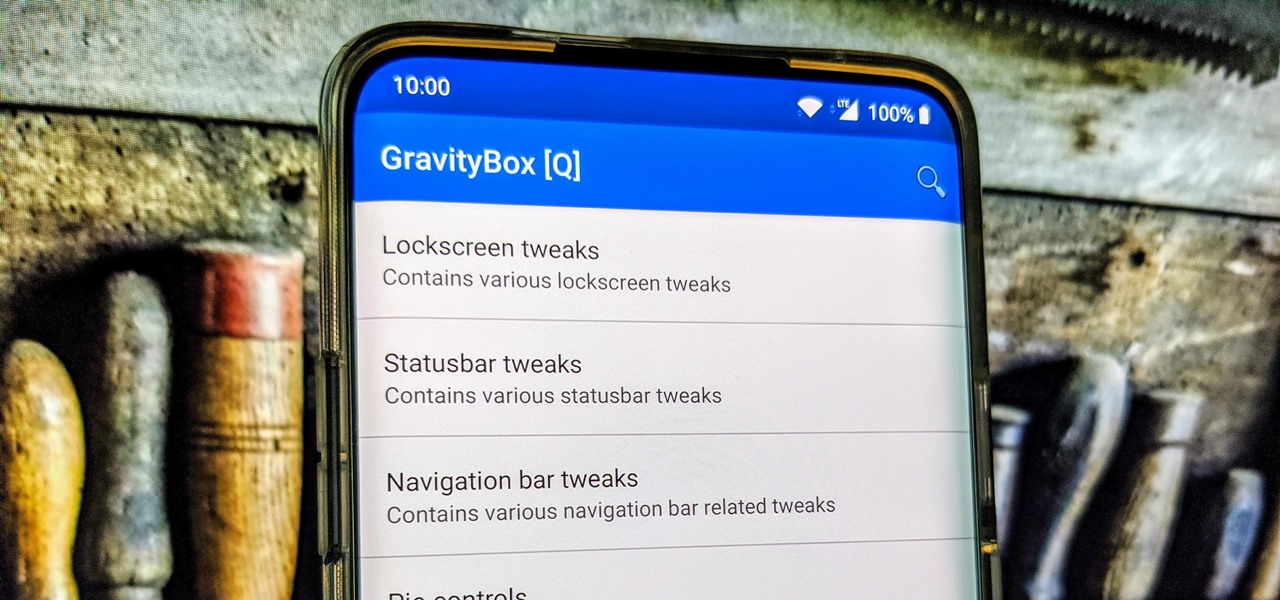
GravityBox is a name that many know as the module to rule them all when it comes to customizing your Android device. Ask any of the longtime modding pros, and they'll tell you about the good old days during the Xposed era. The community was booming and full of great ideas, and there were never any shortages of fun modules to try. Thankfully, it still lives on even years later.

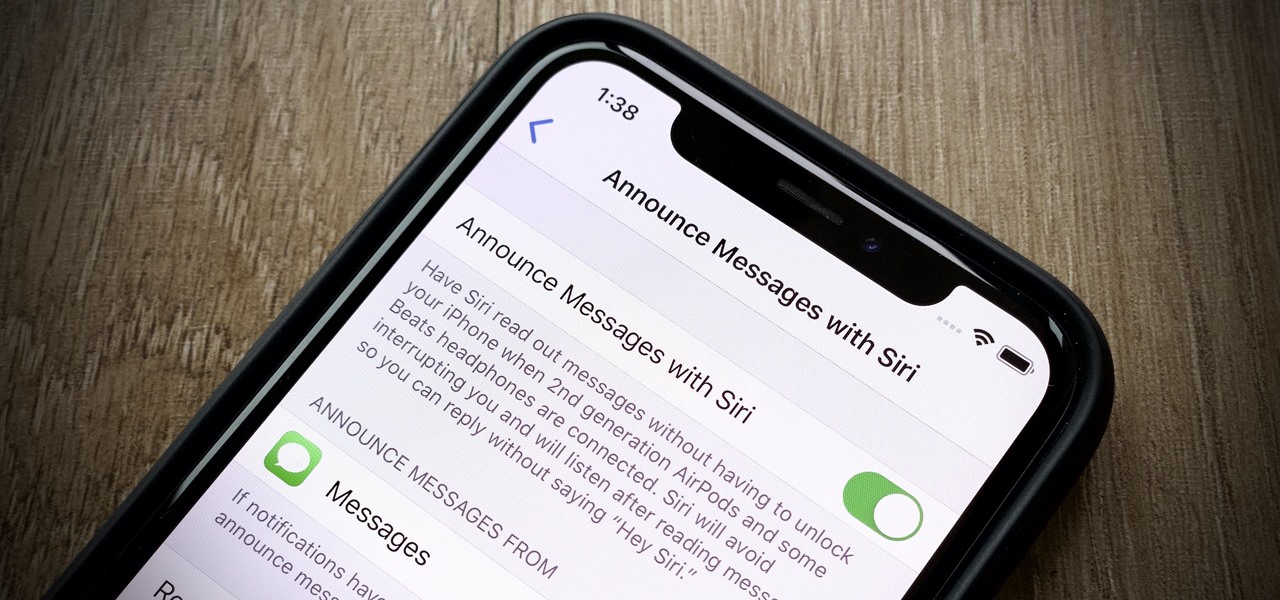
Apple's iOS 13 has been quite the disrupter. The initial update featured over 200 new features and changes, while its successor, iOS 13.1, brought another 22 to the mix. With the company's latest update, iOS 13.2, you'll see an extra 22 amendments on your iPhone, including new emojis, Deep Fusion on iPhone 11, 11 Pro, and 11 Pro Max, and Announce Messages with Siri, just to name a few.

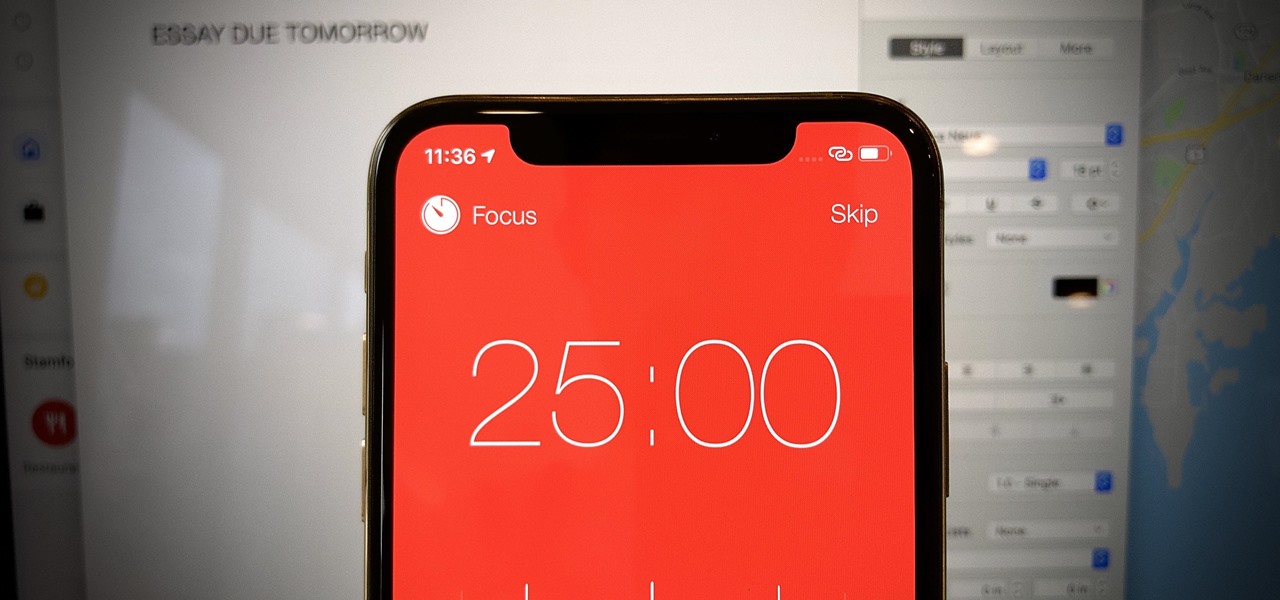
Procrastination is an ugly beast. At first, it seems so innocent to spend five minutes checking Reddit or Twitter. You'll get started on work right after. Next thing you know, it's 1 a.m. and that paper is due in seven hours. Before you start another YouTube video, know you don't have to be like Spongebob. You can be like me, taking control of your productivity with the right app.

Indian startup Dimension NXG is launching augmented reality headsets into India's consumer market with a bold idea: focusing on immersive computing in education on the high-end. The plan is to give a new kind of AR headset to schoolchildren in remote Indian villages, starting from class 5 (age 10) until graduation.

When researching a person using open source intelligence, the goal is to find clues that tie information about a target into a bigger picture. Screen names are perfect for this because they are unique and link data together, as people often reuse them in accounts across the internet. With Sherlock, we can instantly hunt down social media accounts created with a unique screen name on many online platforms simultaneously.

Sports technology company Form is testing the waters for augmented reality wearables with a product aimed at a very specific user group.

Firewall solutions for macOS aren't impervious to attacks. By taking advantage of web browser dependencies already whitelisted by the firewall, an attacker can exfiltrate data or remotely control a MacBook, iMac, Mac mini, or another computer running macOS (previously known as Mac OS X).

Magic Leap has done a great job of aggressively releasing new apps, software updates, and major franchise tie-ins. But aside from all the creative and entertainment apps, what's it like to use one of the apps the company hopes you'll use every day?

It's common for IoT devices like Wi-Fi security cameras to host a website for controlling or configuring the camera that uses HTTP instead of the more secure HTTPS. This means anyone with the network password can see traffic to and from the camera, allowing a hacker to intercept security camera footage if anyone is watching the camera's HTTP viewing page.

Seven days ago, Apple released the first public beta for iOS 12.2. Now, public testers have access to the latest beta update since Apple released 12.2 public beta 2 on Tuesday, Feb. 5. The company released the developer beta one day earlier, which includes bug fixes, new Animoji, and more.

The story of Meta and its Meta 2 augmented reality headset isn't over, there's a new development that could impact its ultimate fate.

Location-based gaming pioneer Niantic has been preparing its flavor of AR cloud, the Niantic Real World Platform, to bring more realistic and interactive augmented reality experiences to mobile apps. And now the company is looking for a few good developers to help execute its vision on the platform.

After announcing the iPhone XR, XS, and XS Max, one thing was noticeably absent from Apple's Sept. 12 event — the iPhone SE 2, the long-awaited upgrade to 2016's niche yet popular 4-inch model. Not only does Apple have no apparent plans for an update, it has also officially dropped the SE from its online store. Looking for a small iPhone that packs a punch? You might have to try the iPhone 7.