
How To: Write a sensory poem
A sensory poem is a poem that uses all five senses to describe something. These are common poems for grade school children. They are not difficult to do and only need to choose something to describe and follow the rules.


A sensory poem is a poem that uses all five senses to describe something. These are common poems for grade school children. They are not difficult to do and only need to choose something to describe and follow the rules.

Learn about the responsibilities of baseball coaches, managers, umpires, trainers, scouts, and owners with expert tips and advice on baseball rules and basics in this free online baseball video series.

David Hockings demonstrates how to play the marimba, including techniques for using four sticks at the same time.

Douglas Phillips has been performing magic for over fifteen years, and he gives you all the tips you need to know to entertain your audiences. Learn the simple rules of magic, and learn how to truly trick your audience. Douglas shows you famous sleight of hand tricks like the French drop, the delay, and the steal.

In this video series, expert Bo Feng shows you the proper stroke order for writing Chinese characters properly. The long tradition of calligraphy has developed techniques for writing that will make your characters seem more authentic. Bo teaches you the seven rules of writing Chinese characters: top to bottom, left to right, upper left to bottom right, outside to inside, horizontal before vertical, left slant before right slant, and center before wings.

Learn about the game Magic: The Gathering and how it is played, its rules, and more in this video series.

In this video clip series, our expert will explain the basic rules of the game of chess, explaining some of the moves and techniques used when playing the game.

Apple just made it easier to change a widget's size on your iPhone's Home Screen, so you no longer have to delete widgets and add different-sized versions of them. With iOS 18, you can adjust a widget's size straight from its current widget size on your Home Screen. The new method also works on iPad with iPadOS 18.

Apple's newest software update, iOS 17.5 includes one killer new feature for people who like word games: another lexical challenge to complement the crossword puzzles that Apple News already has.

There are a few significant improvements for your iPhone with the iOS 17.5 software update, released May 13, but my favorite is Apple's enhancements to the Apple News app, which is making its Puzzles section even more fun with Game Center integration and even a new type of word puzzle.
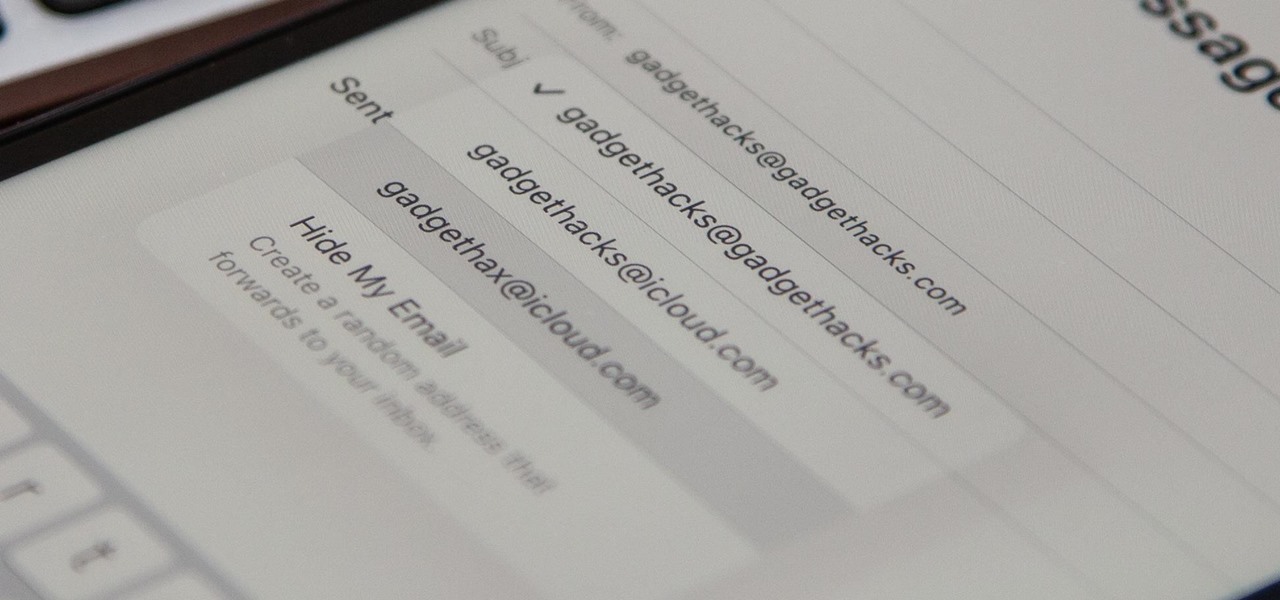
On your iCloud Mail account, you can easily use subaddressing to create hundreds of new iCloud email addresses to give to companies and other parties, all of which go straight to your primary iCloud email address's inbox. The problem with these types of alternative email addresses is that you can't ever respond to emails with the plus tag intact. But Apple has another alternative for you to start using.

There are now more emoji on your iPhone's keyboard that you can send as reactions or stickers or insert wherever else you use emoji — and it's about time. It's been nearly a year since the last emoji update for iOS, and we only received support for 31 new ones then. The new iOS 17 software update brings almost four times as many.

The new iPhone 14, 14 Plus, 14 Pro, and 14 Pro Max all come with great, never-before-seen-on-iPhone features, including the A16 Bionic chip, Bluetooth 5.3, precision dual-frequency GPS, and dual ambient light sensors. But that's only a few new features exclusive to the 2022 lineup.

A low-key iPhone feature that's been around since iOS 10 can make the iMessages you send to family and friends more exciting overall. One particular element is, if you'll forgive my decades-old slang, "da bomb" for emoji.
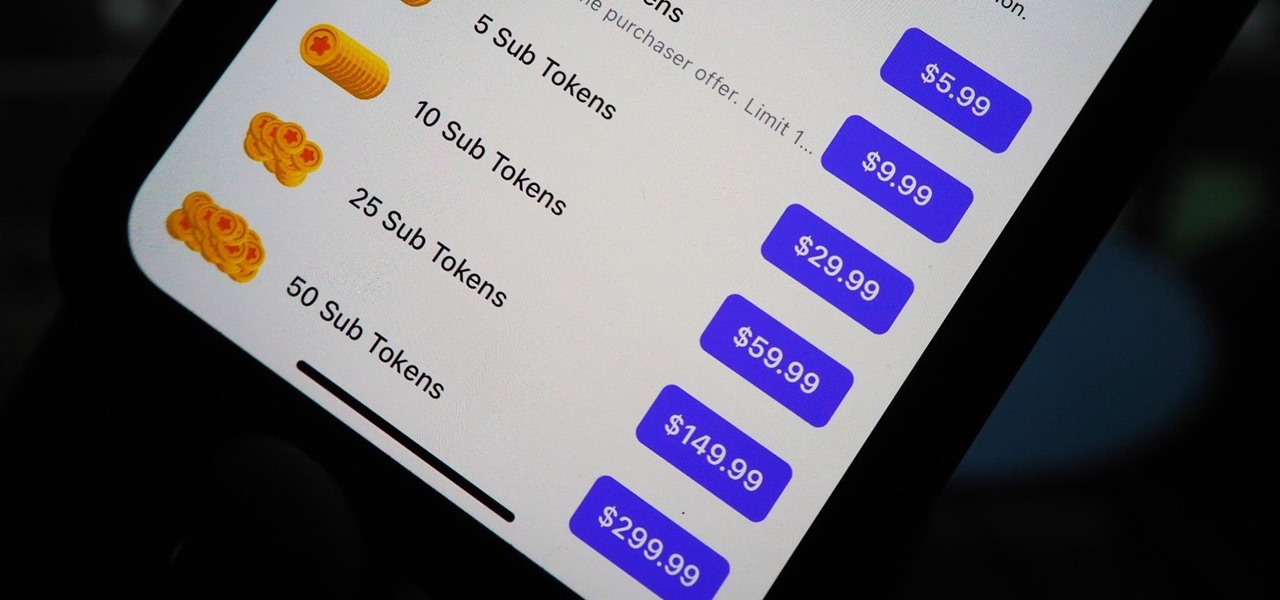
You can't hand over your iPhone to a kid and expect everything to be OK. Not only will they drop your iPhone (and they will), they could also do something much worse than a cracked screen — in-app purchases.

Apple released the fourth public beta for iPhone today, Monday, Mar. 15. The update (build number 18E5178a) comes three hours after the fourth 14.5 developer beta, and includes references in its code to a new "City Charts" playlist feature in Apple Music.

Apple just released the fourth public beta for iOS 14.2 today, Wednesday, Oct. 21. The new update adds eight new dynamic wallpapers to iOS, including four real-life landscapes, and four digital landscapes. When counting each wallpaper's light and dark mode, there are 16 possible variations to use.

Apple just released the fourth developer beta for iOS 14.2 today, Tuesday, Oct. 20. The new update introduces eight new dynamic wallpapers, including four real-life landscapes, and four digital landscapes.
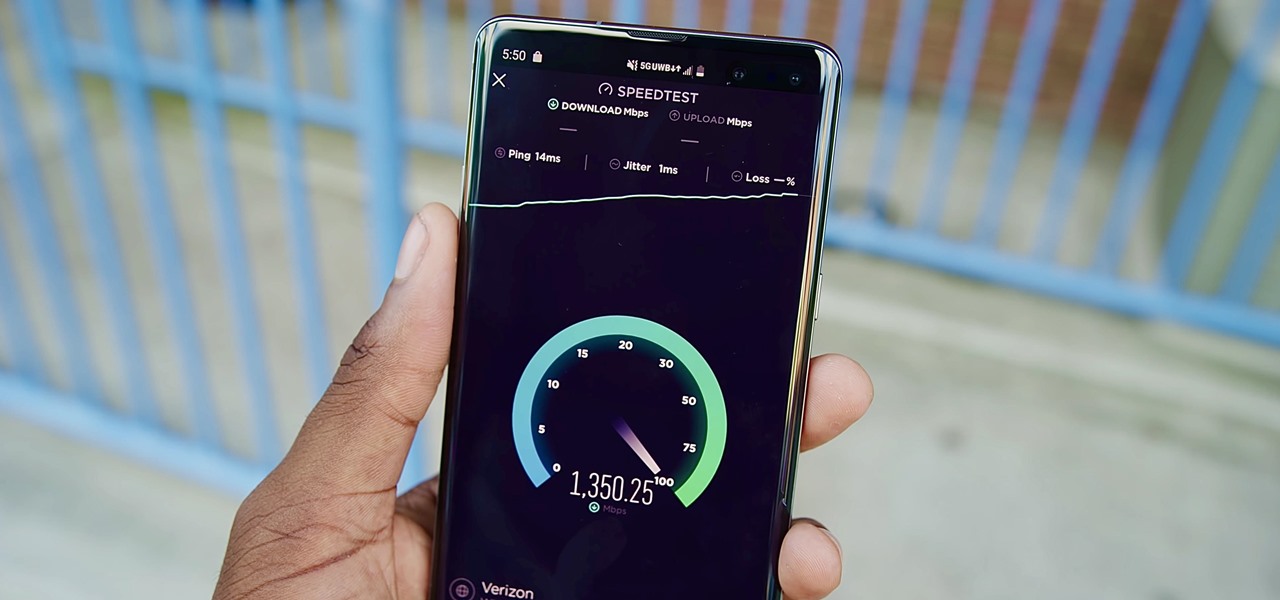
Not all 5G is equal. Even if you dropped the cash on a true 5G phone and you see it's connected to 5G in the status bar, that doesn't mean you're surfing the web, streaming Spotify, and binging Netflix faster than your friends with LTE phones.
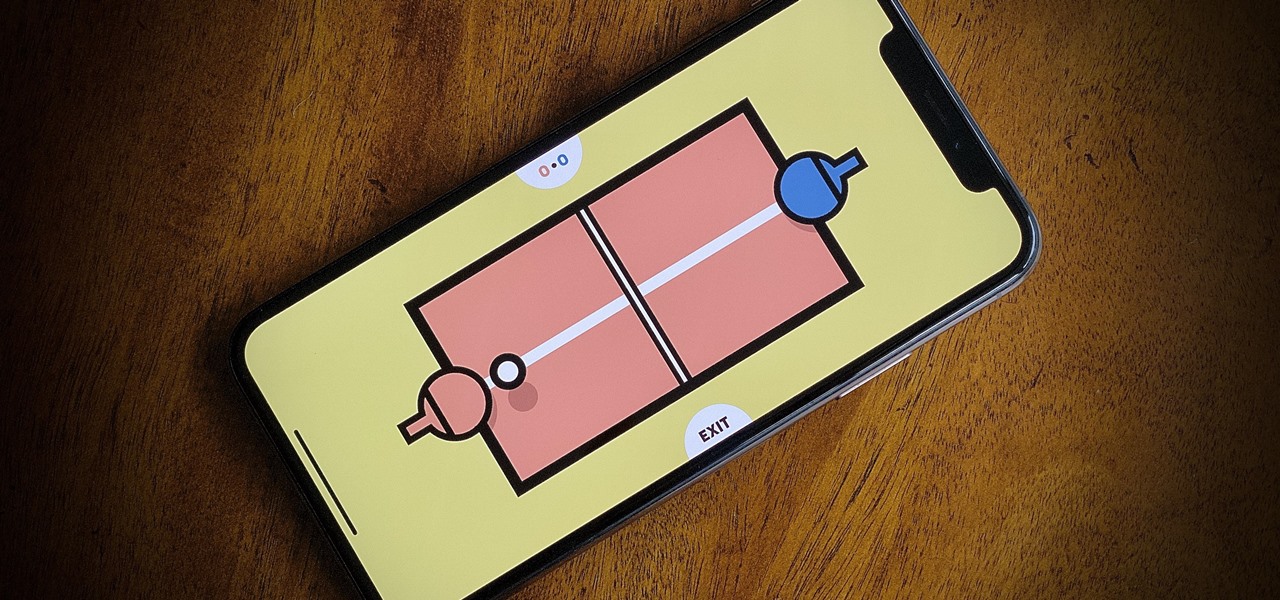
If you're quarantining with other people, consider yourself lucky — but it's not always easy. Staying in one space for so long with too many people can be challenging, so you need to find things to do to make the time go by (and to keep everyone sane). Our advice? Try out these seven free multiplayer games that only require one iPhone or Android device to play.
Every Galaxy S20 sold in the US — even the S20+ and S20 Ultra — simply can't be rooted. With the bootloader permanently locked, you miss out on the world of rooting and the customization it opens up, but modifications are still possible.

The iPhone 11, 11 Pro, and 11 Pro Max introduced a new rear camera system to the iOS ecosystem. Each model has a new ultra-wide lens in addition to the wide one, and the Pros have a telephoto lens. Both have improved selfie cams too. With so many lenses, it can be challenging to choose which to film with, but why pick when you could shoot with two at once?

If you had a phone in 2004, there's a pretty good chance it was a Motorola RAZR. The iconic phone is the tenth highest-selling of all time, and it marked the height of the flip phone era. Now that the technology has caught up, Lenovo (Motorola's parent company) is bringing it back in a big way.

If you just got a new iPhone, chances are you picked up the iPhone 11, successor to the iPhone XR, the most popular device in Apple's 2018 series. Since the XR did so well, it was predicted that the iPhone 11 would too, and so far, it has lived up to that prediction, beating the 11 Pro and 11 Pro Max in sales in 2019.

So you can't figure which one to buy. It's understandable. Apple released three iPhones, each designed for a different segment of the market. But which one is right for you? The iPhone 11, iPhone 11 Pro, or iPhone 11 Pro Max? That's a good question.

Samsung has just announced the Galaxy Note 10 and 10+. These are the latest and greatest from the largest smartphone OEM in the world. Plenty of numbers and specs have been thrown your way to showcase how good the Galaxy Note 10 is, but we wanted to simplify all this for you and key in on the most important things.

Passwords on Windows are stored as hashes, and sometimes they can be tough to crack. In certain situations, though, we can get around that by using the hash as is, with no need to know the plaintext password. It's especially interesting if we can manage to get the hash of an administrative user since we can then authenticate with higher privileges by performing an attack known as pass the hash.

If you've read or watched anything Harry Potter before, you know friendship and teamwork are huge parts of the story. The same goes for Harry Potter: Wizards Unite, with its "Wizarding Challenges." Here, you can tackle Fortresses full of Foes alone, but why do that when you can battle with up to four other friends at once? Here's how it all works on Android or iOS.

If you've ever received an email from a sketchy address purporting to be Uber, asking you to sign in with your credentials, you might be a phishing target. Hackers use a fake login page from real-looking domains to trick you into giving up your account information, and while it's been an issue in the past, Uber is making it more difficult on cyber thieves with the addition of two-step verification.
With YouTube TV and DirecTV Now starting at $40/month, and others like Sling TV offering an eye-catching $25/month plan, streaming cable services may sound like a great way to cut costs while cutting the cord. But when you look at all the factors, the price you pay may very well end up being just as high as your traditional cable bill — if not more.

So, you've lost your Apple TV remote. Maybe it's busted. What are you supposed to do now? You could go out and buy a new one, but they're expensive if you have a newer Apple TV with a Siri Remote, and wouldn't you rather spend that money on a movie? You might be without a working dedicated remote, but you likely have the next best thing already in your pocket.
With all the controversy around the Pixel 3 XL, the regular-sized Pixel 3 might be the phone of choice for most users. Thanks to the huge boost in screen size, the little brother is now an easier pickup for those who like a bigger screen. And once more, the internals are the same, giving you the same experience as the 3 XL without the display notch.
The "controversial" Pixel. No phone in the history of Google's Pixel lineup deserves this title more than the Pixel 3 XL. For some (including myself), the design is a welcome change that embodies the modern design of 2018 flagship phones. For others, it has an ugly huge display notch that destroys symmetry.

Apple's iOS 12 has finally landed. The big update appeared for everyone on Monday, Sept. 17, and hiding within are some pretty amazing augmented reality upgrades for iPhones, iPads, and iPod touches. We've been playing with them ever since the iOS 12 beta launched in June, and here are the things we learned that you'll want to know about.

When rumors first emerged of Sony's Xperia XZ3, many of us wondered why. With the Xperia XZ2 just releasing in April of this year, why is Sony already releasing its successor? But now that it is officially announced, it makes a bit more sense, as what Sony is calling the XZ3 is actually more like the XZ2S.
As the official release of iOS 12 nears closer each day, Apple continues to update its betas. The company released the fourth beta of the upcoming software to developers Tuesday, July 17, exactly two weeks after the release of the third developer beta which came out just a few days before the second public beta.

After installing Ubuntu as your primary OS, you should have protected against USB Rubber Ducky payloads, defended against hard drive forensics, and reduced the overall attack surface against physical strikes. When defending against network-based attacks, you'll want to minimize hardware disclosures, prevent packet sniffers, harden firewall rules, and much more.

A new study published by American University demonstrates how Pokémon GO and other augmented reality games can help city governments bring communities closer together.

There's a growing sentiment around the web that when it comes to Android, stock is best. Many people prefer the clean look of Google's vision for Android, but manufacturers like LG will add features and themes on top of this base to differentiate themselves from the pack. But these OEM skins, as they're called, aren't always as overbearing as you might think.
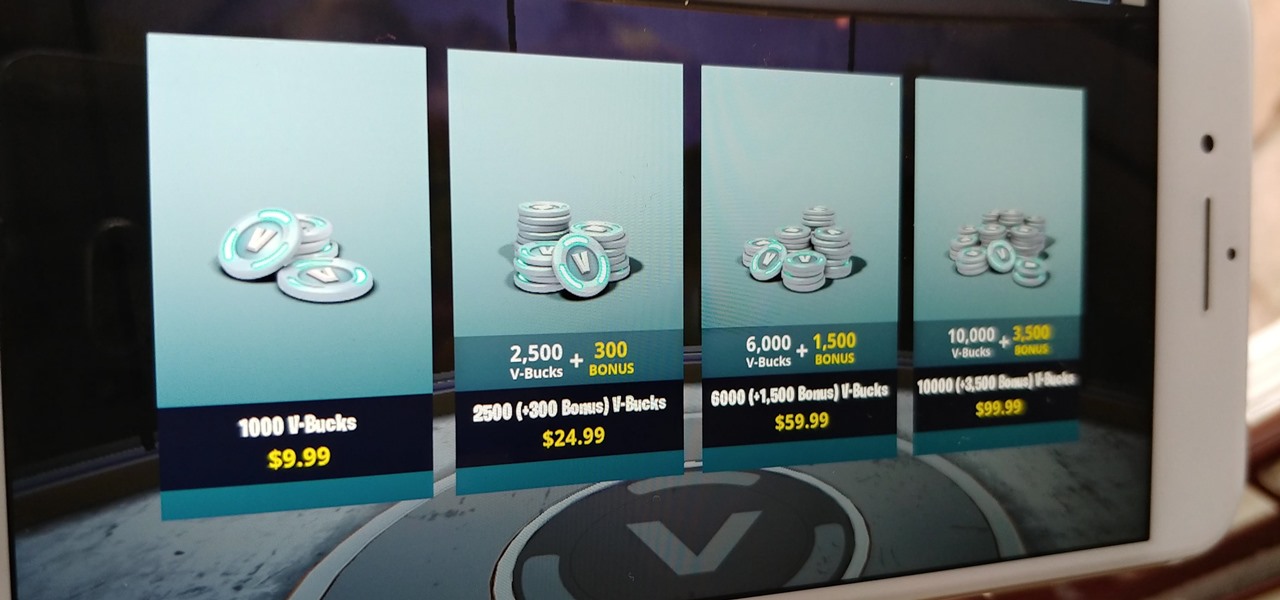
Thanks to its free-to-play strategy, many items in Fortnite Battle Royale require V-Bucks, the in-game currency. You can purchase V-Bucks with real-world money, but many would rather earn V-Bucks instead of getting nickeled and dimed by micro-transactions. While limited, there are a few ways to earn free V-Bucks in the game.