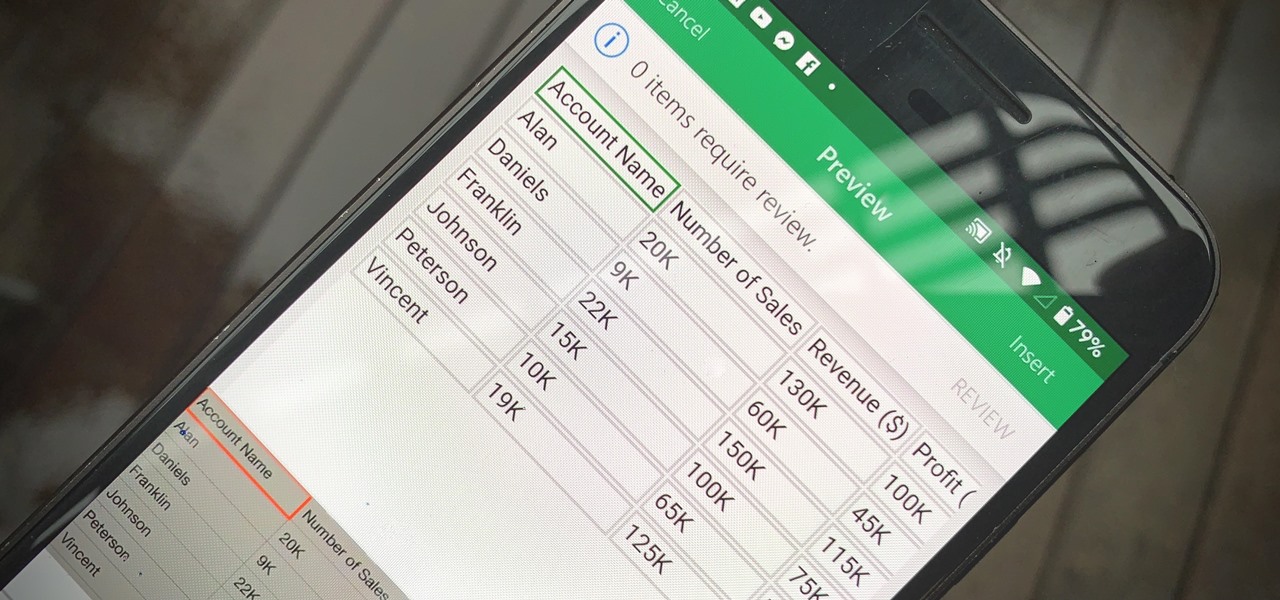
Creating a digital spreadsheet by hand can certainly be tedious, especially if you're copying a printed paper table word for word, number for number. Instead of typing information that's already there, however, use Microsoft Excel on Android or iOS to snap a photo of that printed chart and import it directly into your digital one.

When you're browsing the internet on a computer, you just need to hit Ctrl F (or Command F) and type something out to find all instances of that word in the webpage. It's a handy feature baked into most browsers (nearly all mobile browsers have a "find" feature, too), but unfortunately, it doesn't work with real-world documents, signs, and menus—or at least it hasn't, up until now.

In this series you will learn how to use PHP to perform attacks, gather information, and setup backdoors. Along with performing attacks you will learn how to protect yourself from them. In this part you will learn about PHP as well as install Apache and PHP. What you'll need for this series
This tutorial is for a great card that is ideal for any men out there, or for a travel/ Bon Voyage etc. I must admit I had great difficulty with part of this one! as you'll see when you watch it.. but stick in there as its a fab demonstration for a good idea! plus it goes to show that I can waffle when under stress.... enjoy. Step 1: Items Used

When setting up a new Mac, there can be a bunch of settings that need to be changed in order to get the system running the way you like it. That usually involves going through tons of System Preferences panes and app settings—but it doesn't have to.
Sometimes our information important. So important that we have to encode it to keep it away from criminals. What better way to encode information than to make our own encoder with Python?

Starting April 10th, you'll will be able to book 15-minute appointments online to try on an Apple Watch in person at Apple Stores across the world. With the April 24th release date just around the corner, making an appointment is a great idea for those who are unsure about which color and size to purchase—or if they'll even want one.

This is one more cool illusion by maricv84, one where you slide a transparent sheet with black bars overtop a cryptic image to create an animated effect.

One day I was contemplating about a canard paper airplane design. After several attempts, here is what I got - the Eurofighter Paper Airplane.

How To Make A Paper Boat - An easy step by step origami tutorial on how to fold a paper boat with a sail that floats in water.

The new HTC One (M8) is a large phone, no doubt about it. Still, with those BoomSound speakers, 5-inch display, and 2600mAh battery, it's a wonder they managed to cram everything in that gorgeous, unibody metal shell. By that logic, it makes sense that the M8 makes the switch from a micro-SIM card to nano-SIM to save as much space as possible.

This is easy-to-make origami heart with wings. You can fold one for a Valentine's Day gift, or for any time of the year where a flying heart is appropriate. Design by Francis Ow, Folded by Ventsislav Vasilev. What You Need:

The bread at your local supermarket will most likely always be fresh, but how do you know which loaf is the freshest out of the bunch? You can squeeze and inspect them like an annoying TSA agent, but there's actually a much simpler way to do it.

It may finally be dying down a bit, but there are still plenty of cat lovers addicted to Grumpy Cat, who has surpassed her internet meme stardom to move onto books, calendars, and even a soon-to-be film. For those of you who just can't get enough of the crotchety-faced Tardar Sauce, make this Christmas a Grumpy Christmas with this free printable paper ornament of Grumpy Cat.

This is for all you vegans out there who crave the taste of key lime pie more than Dexter. Traditionally key lime pie is not vegan, so in this inventive recipe I've made it vegan and you won't believe what makes it green!

LEDs have slowly become the standard for DIY lighting projects because they consume less power and last way longer than regular light bulbs do. Light-emitting diodes have no filament, meaning they generate their light solely by the movement of electrons in a semiconductor material.

You may or may not care about this, but sometimes it physically upsets me when I see gears stuck together haphazardly, with no concern for whether their teeth interlock. I mean, what do you do with non-interlocking gears?

RonyaSoft Poster Designer software includes lots of different ready-to-use templates. You can freely change anything you want in the template or you can just print it as it is, if you don’t want to puzzle over it. Moreover, you can create your own poster from scratch.

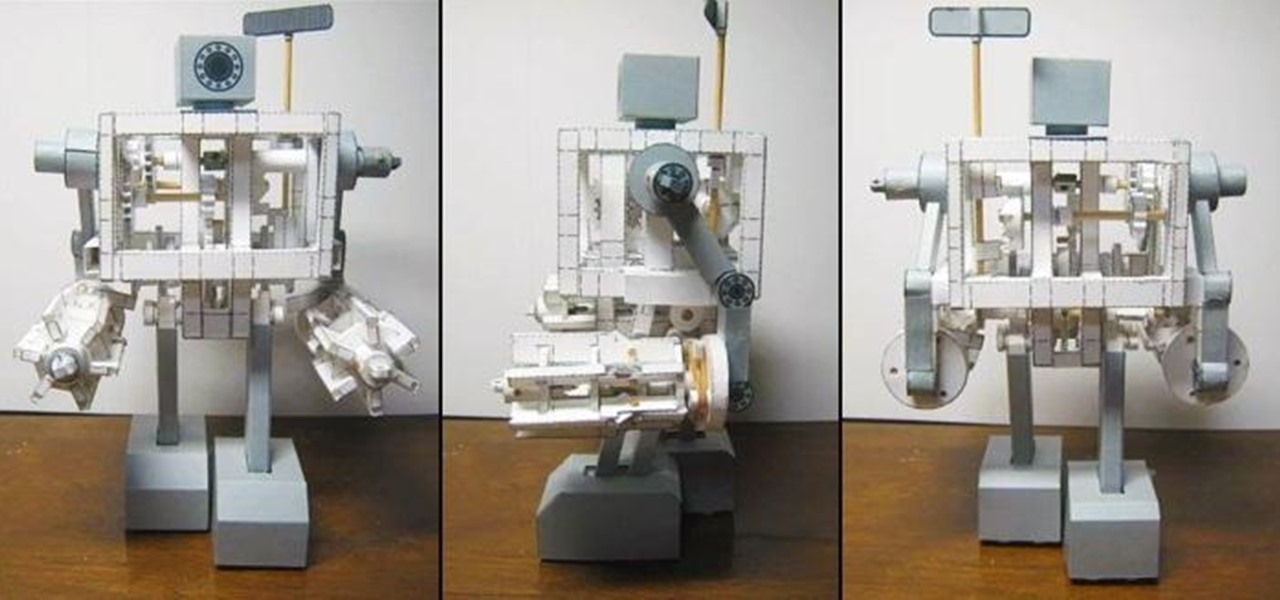
One amazing Japanese papercraft enthusiast has built a walking 'robot' that's made of nothing more than paper, rubber bands, and a few wooden shafts for stability. It's been dubbed the 'Paper Robot III,' and even the cogs and gears are made of paper. The creator made a video detailing his entire process, and he's selling kits to make your own for about $40 US, if you're too lazy to do everything from scratch.

Make monotypes on a plate made of food grade gelatin. This how-to video shows how to pull an original print and a ghost print. It is fun easy and experimental. Watch this video printmaking tutorial and learn how to make a gelatin plate monotype prints using food-grade gelatin.

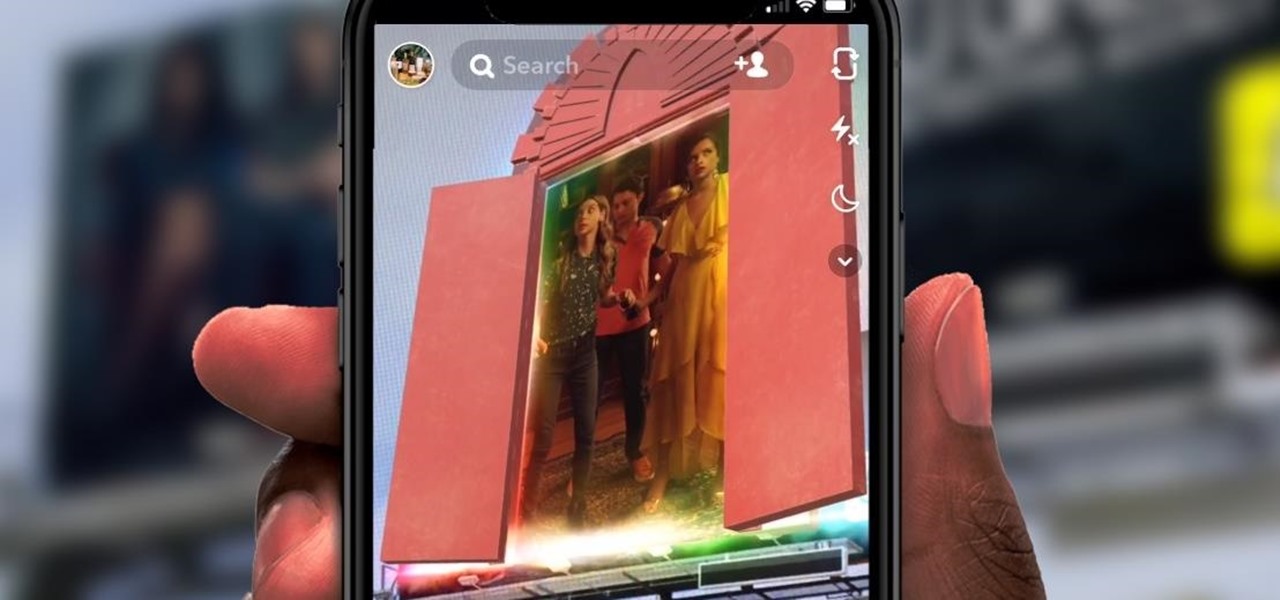
It looks like Snap's foray into augmented reality billboards last year was successful, as the company has returned with two more outdoor advertisements for its Snap Originals series.

As one of the leading 3D engines for augmented reality development, a new release of Unity is a significant event that carries the potential to facilitate huge leaps forward in AR content creation.

In the current state of the augmented reality space, Leap Motion is the only well known name in DIY AR headset kits with its Project North Star design, which gives makers the blueprints to build their own headsets.

Designing and manufacturing waveguides for smartglasses is a complex process, but DigiLens wants us to know that they have a software solution that partially solves that problem.

The Super Bowl of bicycle racing, the Tour de France, added augmented reality to its TV broadcast this year.

Less than two months since unveiling Project North Star, Leap Motion has released the reference design that will allow developers, makers, and even manufacturers to build their own augmented reality headsets based on Leap Motion's work.

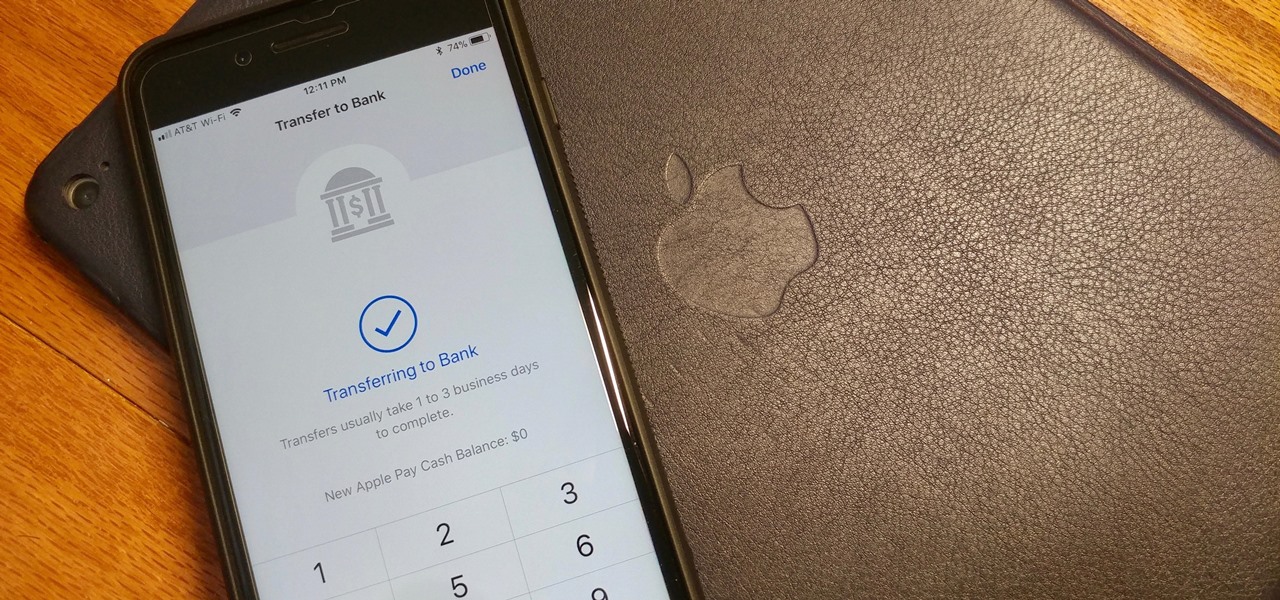
Let's say you receive $10 from a friend through Apple Pay Cash via an iMessage. You could spend that money in the App Store or at any retailer that supports Apple Pay using your Apple Pay Cash card. If you'd rather save it or use it for bills, it's easy to transfer that money to your bank account in iOS 11.2.

The first teaser for Jurassic World: Fallen Kingdom just hit computer screens on Sunday, but now plans for an augmented reality book for the film have also emerged.

The iPhone X is sure to be a hot seller this holiday season. You probably know someone with the $1,000 iPhone on their wishlist, and with a price tag that high, Black Friday is probably the best chance of them getting one. But there's only one store we've found so far that's even offering a real holiday deal for the iPhone X.

The standing desk movement has gained momentum over the past few years as research has pointed to the detrimental health effects of sitting at a desk all day.

At IFA in Berlin today, Sony introduced the latest models of the Xperia line, with new features in tow that should appeal to creators of augmented and virtual reality content.

The Washington Post believes augmented reality adds an extra layer to stories, and they're doubling down on that belief by adding in new AR features into their already popular "rainbow" news (iOS and Android) and Classic (iOS and Android) news apps.

Late last year, two surgeons from the Instituto de Ortopedia e Traumatologia de Jaraguá do Sul in Brazil started using a combination of 3D printing and the Microsoft HoloLens to help plan spinal surgeries. And now, with the rest of their team, they've successfully performed a surgical procedure on their first international patient using their 3D impression planning and augmented reality process.

True innovation tends to come from the places we least expect as developers. The Microsoft HoloLens is still a very new product, and some of the other headsets are still just ideas, so the rules for mixed reality are not set in stone. That means all the real problems to be solved are yet to come.

I'm back! We're learning Java WhileLoops today.

Right, So i've been asking alot of questions here on Null-Byte and everyone has been really helpful to me.

In this article I will show you how to obtain victim's credentials without cracking any hashes. There are a couple of ways to perform this task (for example dumping the SAM file and cracking the NTLM hashes), but here I will explain how to do it using PowerShell and a bit of social engineering. We are going to create a fake login popup.

In many programs on Linux, you'll come across programs which allow you to specify additional arguments instead of just simply running the program by itself. If you've used the Kali distribution, I'm more than certain you'll have come across these with the command line tools, else if you have been following these tutorials, we have already come across three tools which also use the same technique, i.e. gcc, gdb and wc. How do we do this with C? Let's find out.

What's up guys! It's time to discuss strings in more detail. Review

Welcome back, reader! In this tutorial, we will be covering our first program! So let's get to it. We all know the unspoken tradition of the first program when learning a language and of course, here we will respect and complete it. Fire up your favorite text editor (be it vim, emacs, gedit, it's all the same to me, no h8) and try to keep up.