The USB Rubber Ducky and the Digispark board both suffer from the same issue when attacking macOS computers: a keyboard profiler pop-up which tries to identify any non-Apple USB keyboards. While it's an annoying setback, the solution is a simple modification that allows Mac computers to be targeted, which affects the ability to target Windows and Linux devices.

SMB (Server Message Block) is a protocol that allows resources on the same network to share files, browse the network, and print over the network. It was initially used on Windows, but Unix systems can use SMB through Samba. Today, we will be using a tool called Enum4linux to extract information from a target, as well as smbclient to connect to an SMB share and transfer files.

When researching a person using open source intelligence, the goal is to find clues that tie information about a target into a bigger picture. Screen names are perfect for this because they are unique and link data together, as people often reuse them in accounts across the internet. With Sherlock, we can instantly hunt down social media accounts created with a unique screen name on many online platforms simultaneously.

With a simple social engineering trick, sudo passwords can be captured in seconds without the target's knowledge. The passwords can then be saved to a file or exfiltrated to another computer on the network.
Among the many partnerships mentioned early on in the life of the Magic Leap One, by far one of the most talked about has been the comic book app from Madefire.

If you've blocked out your calendar to watch the NHL All-Star Game this weekend, then you might be excited to know that USA Today has given its readers the opportunity to meet Washington Capital's John Carlson in augmented reality.

With just one line of Ruby code embedded into a fake PDF, a hacker can remotely control any Mac computer from anywhere in the world. Creating the command is the easy part, but getting the target to open the code is where a hacker will need to get creative.

Back in July, Google rolled out a new design for the web version of Gmail. The rollout included new features alongside the visual changes, one of which being Confidential Mode. This new privacy-centric feature has now finally arrived on the mobile app version of the service, and here's what you need to know.

The mainstreaming of augmented reality won't happen overnight, but it's becoming increasingly clear that traditional media is leading the charge in the effort to introduce the public to immersive computing. A recent example came from none other than USA Today via its 321 Launch app.

Most users don't realize how much valuable data is in their network traffic. With a few simple tools, an attacker can quickly pick out cookies, passwords, and DNS queries from a macOS device as it covertly streams the victim's network traffic to the attacker's system. Here, we will cover two methods for analyzing packets flowing from a Mac.

Cosmetics maker Coty is hanging an augmented reality Magic Mirror on the wall of its Bourjois boutique in Paris that will tell customers which shade of makeup will make them the fairest of them all.

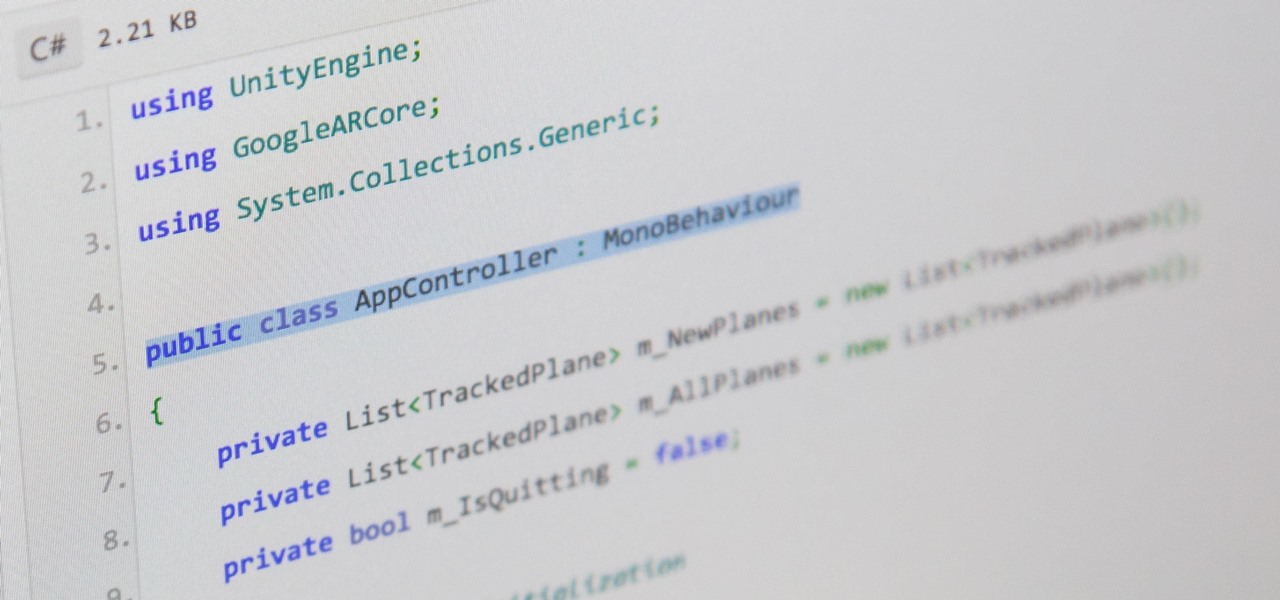
There are hundreds, if not thousands, of programming languages and variations of those languages that exist. Currently, in the augmented reality space, it seems the Microsoft-created C# has won out as the overall top language of choice. While there are other options like JavaScript and C++, to name a few, C# seems to be the most worthwhile place to invest one's time and effort.

Not all microwaves are created equal, so when you use the recommended cooking time on any microwaveable meal, chances are you're actually cooking the food too much or not enough. And unless you're really good at mental math or have a virtual assistant that's smarter than Siri and Google, you have to do things the long way — but not with these helpful apps for iOS and Android.

Before The New York Times brought augmented reality to its iPhone app, the only way Winter Olympics fans could get this close a view to the world's best athletes would be to acquire a press pass.

Using Bitcoin (BTC) or Ethereum (ETH) to buy alt-coins like TRON (TRX), Stellar (XLM), or Ripple (XRP) can seem intimidating if you're new to cryptocurrency. Though you'll still need to do your research to avoid potential disasters, Binance takes the hassle out of trading digital currencies on your smartphone.

It would be difficult to discuss the business of augmented reality without acknowledging the annual tech meat market of CES.

With all the hype surrounding meteoric rise of Bitcoin (BTC), Litecoin (LTC), Ethereum (ETH), and Bitcoin Cash (BCH), it's easy to overlook the fact that you can send and receive cryptocurrencies as a form of payment. And thanks to Coinbase, sending and receiving digital coins couldn't be any easier.

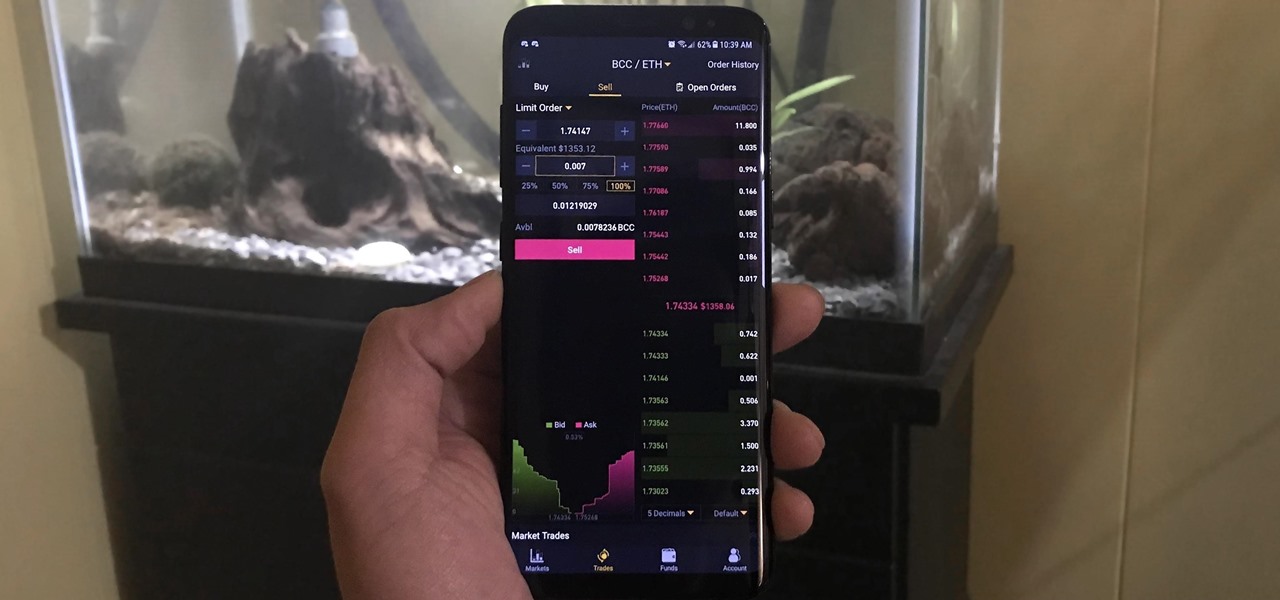
Coinbase sets itself apart from other wallet apps by making cryptocurrency transactions incredibly convenient. You can easily withdraw cash from the app and deposit it into your bank account within days — and now, if you want to cut the time from days to mere minutes, Coinbase has you covered as well.

Now that the holiday season has officially kicked off, Office Depot has updated its popular Elf Yourself app with a few new augmented reality options.

Virtual reality headsets aren't new, but they may be something you or someone on your holiday shopping list hasn't experienced yet. If you're going to dive into the world of smartphone-based virtual reality, the best time to do it is during Black Friday when all the good sales are going on.

There's a good chance that an iPhone is on one of your Christmas shopping lists, but these things are uber-expensive now, making it hard to justify as a holiday gift — even for yourself. That's what Black Friday is for, though, which can help you save a little bit of cash on an iPhone purchase — or at least, give you something in return to help you get even more holiday presents.

You can bet Thor costumes will be prominent among the superheroes seen this Oct. 31. Since the summer, there has been no shortage of coverage for Thor: Ragnarok, and the timing of its November release couldn't be better as a tie-in with the cosplaying holiday known as Halloween. This year, the success of pulling off the Thor costume will rely on how well your new Thor helmet looks, which as it happens, you can DIY at home, using a few simple supplies and perhaps a trip or two to the craft and...

General Motors (GM) seems to have gone to great lengths to avoid lawsuits as it launches its first hands-off driving system in its soon-to-be-launched Cadillac CT6.

Paying for street parking in New York City just got so much easier. Instead of searching for loose change or hoping you didn't forget your wallet, you can use a device you always have with you: your phone.

Think of the coolest, most unique way to create art that you can. Got it? Now think about creating that art out of living things.

Last week, Next Reality wrote about how the Microsoft HoloLens team is partnering with thyssenkrupp. Their mission? To bring mixed reality to the workplace. Now, Microsoft has just confirmed in a blog post that the HoloLens has passed the basic impact tests for protective eyewear in North America and Europe.

Acanthamoeba keratitis (AK), a rare eye infection caused by the Acanthamoeba ameba found in tap water, affects a few dozen people in the US every year. In some cases, it can have devastating effects, like what Irenie Ekkeshis has experienced; She was blinded by AK in her right eye due to a contaminated contact lens.

For anyone who has spent an entire afternoon attempting to assemble a set of IKEA chairs, these wooden masterpieces probably seem pretty appealing.

If print is a dying media, you might as well destroy books in the most beautiful way possible. Guy Laramée is a Montreal-based interdisciplinary artist who turns old books, such as the Encyclopedia Brittanica, into intricately-carved works of art using mostly a sand blaster and some paint.

If you've ever been inspired to try out 3D modeling after enjoying computer-generated imagery in video games and movies, chances are you've checked out an paid applications like 3ds Max (previously called 3D Studio Max), or even free ones like Blender, then just went "No Way! It's way too complicated."

You're all kale-d out, you've had it up to here with golden milk, and you're on the prowl for the next superfood. Well, get ready for some unicellular goodness: the next superfood is an algae named Spirulina, also known as Blue Majik. (Kudos to the marketing exec that came up with that, am I right?)

Whether or not The Purge franchise will be as successful as Friday the 13th, A Nightmare on Elm Street, Halloween, or even the Saw movies remains to be seen, but it's definitely winning in the Halloween costumes department.

Gaining access to a system is always exciting, but where do you go from there? Root or bust. Sure, a compromised host is a great way to run a botnet, or do some other boring, nefarious thing—but as hackers, we want root. We also want to take the easiest path possible, search out low-hanging fruit, and exploit them. SUID programs are the lowest of the low-hanging fruit.

Welcome back, my hacker novitiates! If you have been following this new Snort series, you know that Snort is the world's most widely used intrusion detection/protection system. Now a part of the world's largest network equipment company, Cisco, it is likely to be found everywhere in one form or another. This makes a compelling argument for learning how to use it, as it will likely be a necessity in any security-related position.

Welcome back everyone. I apologize for the lack of training articles, but I've been rater busy lately. I've recently picked up a second job and my college courses are now back in session, so I'm a bit strapped for time.

Over the course of the past century or so, media consumption has gone from a few readers enjoying their local print publication to billions of users viewing countless hours of video across the globe each day. This was a gradual evolution at first, but recent advancements in mobile connectivity have sent us into a climb the likes of which we have never seen before.

Welcome back everyone! In the last training session we covered basic file input and output. We're going to leave this topic for a bit and start on something that will change the way we write scripts, classes.

How's it goin'? In this tutorial, we will learn about the security issues of the popen and system functions. I've seen a few people attempting to run command line utilities or whatever it is they require with calls to these two functions but may not know the security implications which come along with it. I will show you using an example from the wargame IO Smash The Stack.

Hey guys, in this tutorial, we are going to learn about the heap segment and how to use it for storing data in our programs. We will also go into the details of its use in conjunction with the char pointer and struct data types.

First of all, Merry Christmas and Happy New Year to all Null-Byters that learn and teach in this wonderful site. In this article we will explore the basics of the meterpreter's IRB (Interactive Ruby Shell).