What's up readers? We have ever so slightly touched upon this concept of scope with variables but still don't really know what it means. In this tutorial we will learn the behaviors of variables existing in our programs and within functions.

Before I continue with a topic on strings, we first require some fundamental understanding of how memory works, i.e. what it is, how data looks in memory, etc. as this is crucial when we are analyzing vulnerabilities and exploitation. I highly suggest that your mind is clear and focused when reading the following article because it may prove to be confusing. Also, if you do not understand something, please verify all of your doubts, otherwise you may not completely understand when we touch on...

These days, if you're having friends over, they'll probably ask to log into your Wi-Fi network before asking for a drink. But if you've forgotten your password, it can be quite hard to find, since most devices obscure the characters with asterisks.

In the tech world, it's all too common to slap a fake label and packaging on a lower quality product, especially SD cards. If you've ever bought an SD card on the cheap from a slightly-less-than-reputable source (or even a reputable source, in some cases), how do you know if it's the real deal?

In this article, we will explore the basics of radare2, a powerful package that comes with Kali. We are going to write a simple program, and then disassemble it, to see what is really doing in the processor.

Star Trek Communicator badges rule. If you're a Trekkie, you know they are iconic to the TV series. The Next Generation, Voyager, and Deep Space Nine all had these awesome communicator badges.

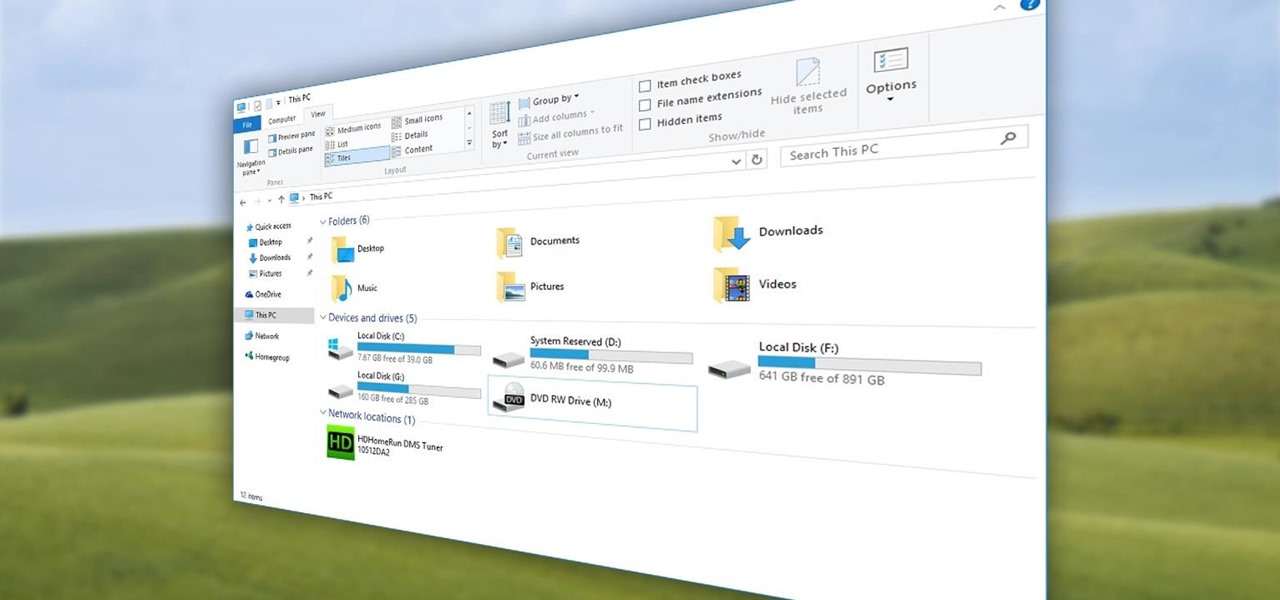
Quite a few things have changed with Windows 10, but one of the more central features that has received a makeover is the old Windows Explorer program, which has been renamed to File Explorer in this version.

Hello fellow grey hat hackers, as hackers it becomes necessary for us to be able to send emails anonymously. Whether for whistle blowing or pranks or social engineering or whatever, it just is necessary for us to do that.

If you've updated your iPhone 4S or iPad 2 to a version of iOS 7, iOS 8, or even iOS 9, you've probably noticed that its performance is a little more sluggish than it was back when it had iOS 6 and lower on it.

Welcome back, friends! Many times, businesses, friends, and family will lock their zip files with a password to keep their files secure. It is reasonable, and understandable. Well, thanks to hackers, there are many ways to get past this wall of security.

Imagine this scenario: You exploited a system using metasploit and you want to install a backdoor. You have a few options;

For 365 days of the year, our mothers show their love for us by driving us places, cooking us food, doing our laundry, and being our number-one cheerleader. But for one day of the year, we all get up early in the morning and show our love for our favorite women. Often, that means cooking breakfast or making brunch, or running to the store to grab a pre-selected bouquet of flowers.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

With only a few days until Apple Watch preorders begin, and just a couple of weeks until its official release, the biggest question in Apple Land seems to be: "Are you going to get an Apple Watch?"

When it comes to making pancakes in the morning, most of us probably follow the instructions on the box. Mix all the ingredients together, pour onto a hot greased pan, and form perfect circular flapjacks one by one.

As far as wallets go, mine is as full as they come; think something like George Castanza's overstuffed wallet on Seinfeld. I've got receipts, pictures, and tickets jammed inside, but what takes up the bulk of the space are all of the cards—credit, debit, gift, rewards, customer loyalty... I've got pretty much any card you can think of squeezed in. While it is a strain on my rear end, there's nothing I can do besides keep some of the cards elsewhere. However, looking for them when I need them ...

Welcome back, my greenhorn hackers!

Hate slogging through pages and pages of weighty books and lengthy work documents? You may not be able to depend on speed-reading apps, but with the right font, you can increase the number of words you scan each second, speeding up your reading pace exponentially.

So, you're scanning the internet for some cool articles to read during your lunch break and you come across something pretty interesting—"The 50 Most Incredible Things Every Person with a Brain Should Know." That sounds interesting, so you click, and boom, you are hit with the utterly obnoxious Page 1 of 50. Really?

Ah, the age-old problem of sharing pictures with friends and family. Ten years ago, the best method available to us was passing around duplicate photos printed out at the local drug store. As easy as smartphones have made this act, you'd think we'd be satisfied by now.

While we now know that iCloud was not exploited by hackers to steal private celebrity photos, Apple did admit that guessed (aka brute-forced) passwords and/or iCloud security questions were to blame for the breach.

While some mobile sites have built-in text-resizing tools, many do not. A lot of those that don't won't even let you pinch-to-zoom. That makes it difficult for people with low vision to read small fonts on their iPhones. In some cases, like with photo captions, even those with perfect eyesight suffer.

A friend of mine has a crazy amount of Reddit karma and gold, and yesterday he let me in on his secret. This person, who will remain unnamed for obvious reasons, created a Python script called Reddit Karma Crawler that finds rising posts before they get too popular.

Welcome back, my greenhorn hackers! Lately, much of the discussion here on Null Byte has revolved around evading detection and not getting caught hacking. Several of you have written me asking for a series on evading detection and forensics, and while I began a series 5 months ago on just that, we have changed hacking platforms from BackTrack to Kali, which has a much more highly developed forensic toolset.

3D has been all the rage for the past few years. It seems like every other film has a 3D aspect to it, our TVs have 3D capabilities, and we can even print functional objects using increasingly affordable 3D printers. And after some trial and error (ahem, Evo 3D), it's finally taking shape on mobiles.

If you've ever used IFTTT, you know how well it can automate your online world. The premise is simple—If This, Then That—but the results are powerful. From automatically printing images based on hashtags to getting around Twitter bans, the service is quite useful with a wealth of possibilities.

Photo mosaics have interested me since I was a kid. I could never understand how someone took the time and effort to make one large masterpiece out of hundreds of smaller images. Maybe I'm too daft to grasp the concept, but it seems extremely difficult. I certainly don't have the necessary skills to make my own work of art, but luckily my Nexus 7 does.

NSA aside, Apple makes it difficult for users to extract and download text messages from their iPhones onto a computer. For whatever reason (legal, devious, neurotic, etc), we've all found a time where we'd like to save backups of certain meaningful, important, or perhaps incriminating conversations (including all MMS or iMessage pictures and videos). While there are a handful of third-party applications that can help with this process, the majority of them cost money and implement certain te...

Amazon.com has been around for a long time now, but there are still a few things most people don't know about when it comes to buying products from them. Here's a quick roundup of tips to help you get the most out of Amazon and save some money in the process. The holidays are the busiest time of year for online shopping, but these tricks will work all year around.

Video: . Here there are some DIY gift ideas perfect for the Christmas season. They are really easy to personalize depending on what your likes are.

With only a few days left until Halloween, your options might be rather limited if you still don't have a costume. You may have laughed while some people spent the entire month of October painstakingly crafting their ridiculously detailed costumes, but now that the big day is so close, the joke's on you because you still have nothing to wear.

I know it's a very first-world problem, but I really can't stand it. Email was invented to speed up communications between people across the world, even just across the office, yet when I'm on my super awesome iPhone running iOS 7, I have to go back and forth between my gallery and my email to send more than five photos at one time.

This week, Silk Road was shut down for good when the FBI seized the anonymous online marketplace after Ross Ulbricht, aka Dread Pirate Roberts, was arrested. This comes just two weeks after another illegal marketplace called Atlantis shutdown. However, there are plenty of other black markets hiding within the Deep Web, freely and anonymously accessible using the Tor browser.

2011's The Artist was the first silent film to win an Academy Award since 1927. It was old school versus new school, and it won in unprecedented fashion.

"Ahoy-hoy." If telephone titan Alexander Graham Bell had his way, we'd all be answering phones like Mr. Burns. Thankfully, frienemy Thomas Edison had enough sense to realize we weren't always on the briny. He preferred "hello" as our standard telephone greeting, which he is credited with coining in 1877. Fellow American pioneer Davy Crockett actually used it as a greeting first in 1833 (as compared to an exclamation)—but in print, not over the phone.

Text adventure games, such as the well-known Zork series, were some of the first computer games ever made, second only to the likes of Spacewar! and the better-known Pong. So let's travel back in time for a moment, to a time that never was.

When was the last time you bought a CD? Most of us listen to music through a number of digital channels—MP3s, Internet streaming services like Pandora and Spotify, and satellite radio, to name just a few.

While one second may not seem like much, it's the perfect amount of time to encapsulate your day. Photographs are just that, instant snapshots of your day that can send you flying back to that exact moment of time. A couple of months back I visited New York, but I don't recall what I ate, what I wore, or even what I felt. Whenever I look at this picture though, it all comes flooding back to me. I remember that it was a Friday. I remember I ate a brownie, because after I got off the bus I was ...

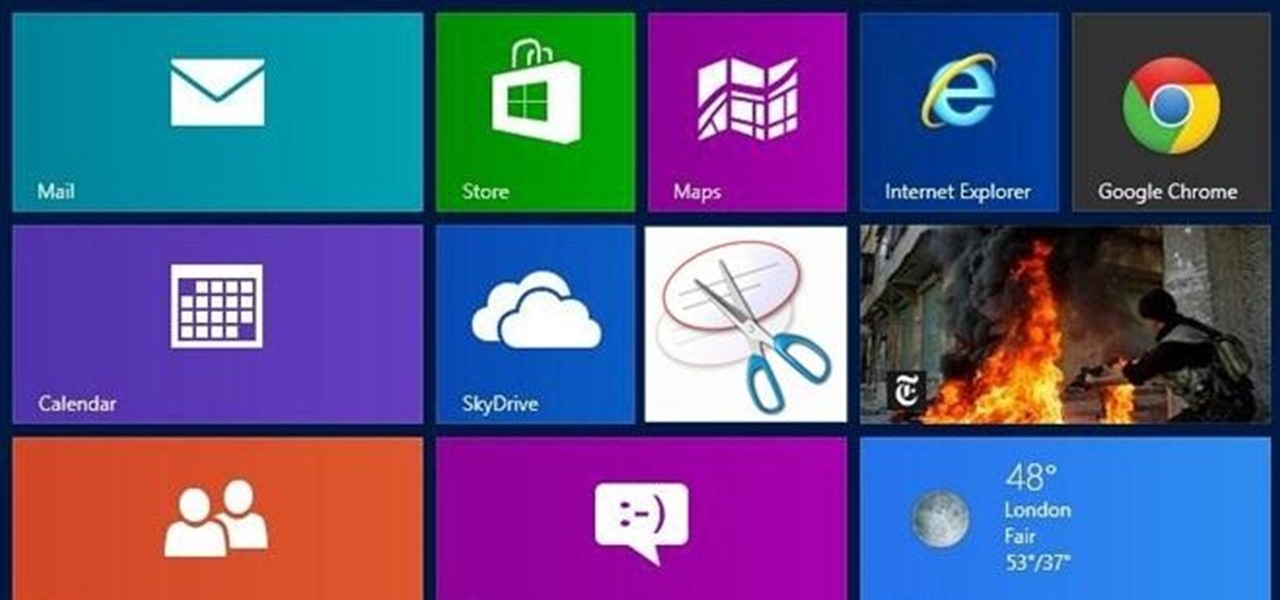
I know what you're thinking—taking a screenshot is super simple. While that is partly true, taking of a screenshot of the Start Screen in Windows 8 is little bit tricky, unless you're on your Surface.

Are you feeling like you've got the hang of Google+? Or do you, as I do sometimes, feel like there are just a few too many quirks to keep track of? Here, I've given you 15 quick tips you should know about Google+ so you can maximize the way you want to use it.