You can create basic 2D games with Objective C and the frameworks that the Apple iPhone already has, but the cocos2d framework allows developers to make their games much better, with animations, sprites, cool menus, special effects and more! Most game developers for the iPhone start out using cocos2d because it's a powerful tool, and best of all— it's free.

The Operative Framework is a powerful Python-based open-source intelligence (OSINT) tool that can be used to find domains registered by the same email address, as well as many other investigative functions. This reconnaissance tool provides insight about your target through examining relationships in the domains they own.
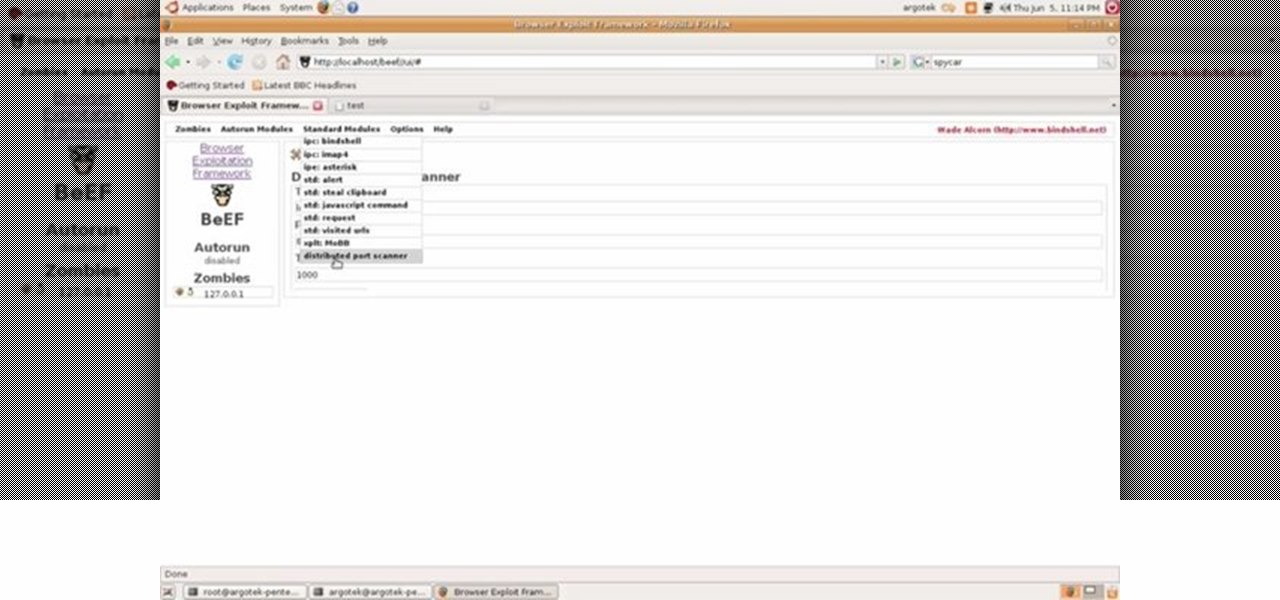
This video tutorial talks about browser exploitation. Particularly, it talks about tools, like BeEF, that can be used to hack known vulnerabilities within browsers and some cool frameworks that you can use to check the security of your own browser. To get started hacking your own browser, watch this how-to.

New to billiards? Well, that probably means you're new to eight-ball, too. In this video tutorial, you will learn the rules and regulations to the 8-ball game, along with some of the basic frameworks to get you, the player, started playing pool.
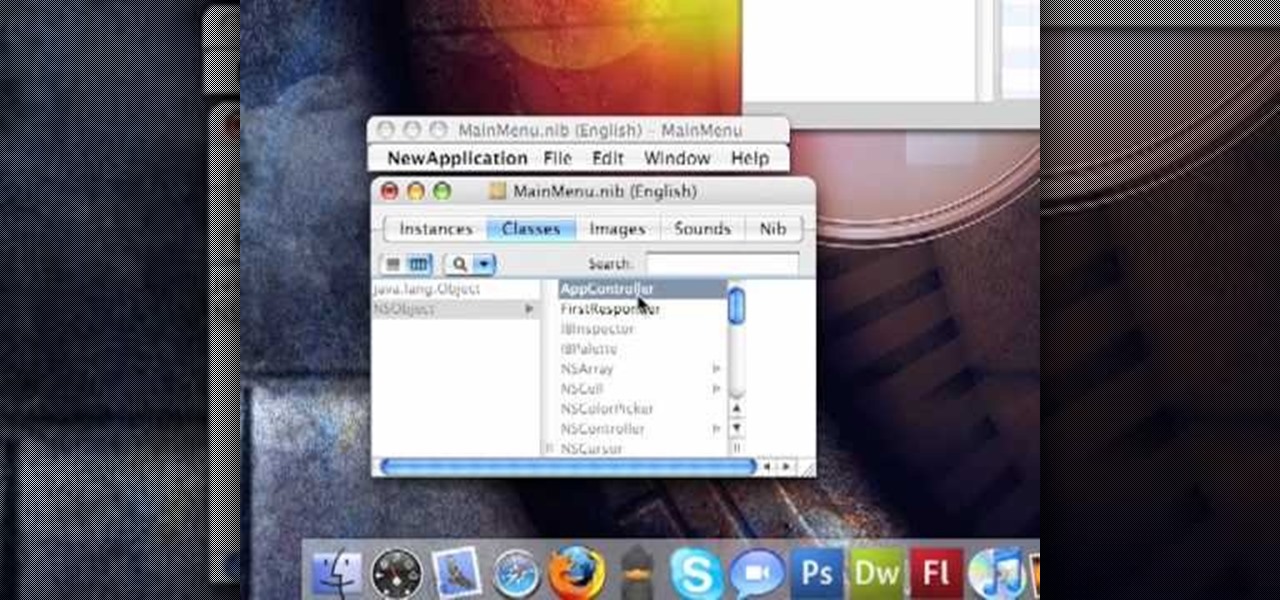
New to programming for OS X or simply after a brushup? If so, you're in luck: this tutorial outlines the basics necessary for using Objective-C and the Cocoa Frameworks alongside Xcode and Interface Builder to create powerful Mac OS X applications. Take a look!

In this tutorial, we learn how to make a web browser in Xcode. First, open up Xcode on your Apply computer, then create a new project. Now go under actions and click 'add', then 'existing frameworks'. Next, click add twice, then scroll down to where you see "menu.xib". Double click on this, and interface builder will open up. You will now have four windows on your desktop opened up. Now go to web view and drag and drop the screen. From here, you can create buttons for the web browser and deci...

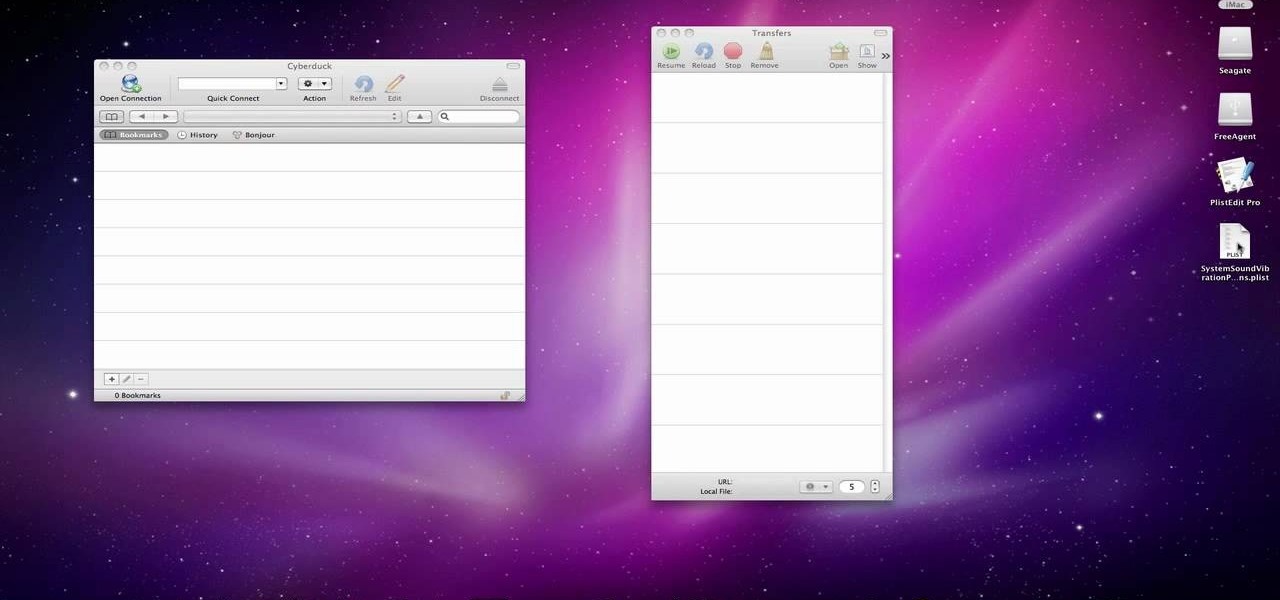
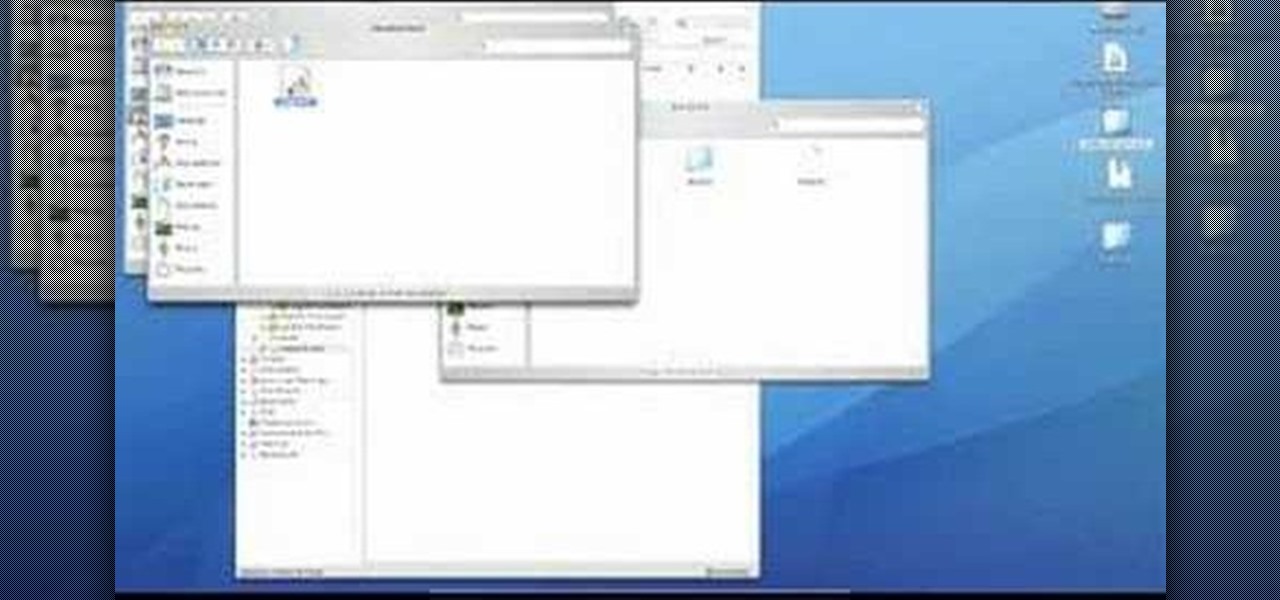
In this video we learn how to make your iPhone vibrate your notifications longer. For this you need an SSH program like cyberduck. You also need plist edit pro. Once you have SSH in your phone, go to system, library, private frameworks, celestial framework, then find vibration patterns. Double click that. Download it to the desktop. Open it. Open up the plist file. Go to default, look at total duration, click into that to change the time of the vibrate duration. Change the On Duration too. No...

Wondering how to create an app bundle in Mac OS X? In this two-part video tutorial series, you'll learn how to create an application that is completely self-contained and is drag-and-droppable/relocatable. Frameworks, PlugIns, and Resources are embedded in the .app bundle, thus avoiding the need for installers and avoiding issues like dll-hell. There is also a quick demonstration on how to enable Universal Binary building at 15:46. Take a look!

Web applications are ubiquitous in the modern online world, and knowing how to attack them is an increasingly valuable skill. But the key to a successful attack is good recon since it's easier to be focused and efficient with the more information you have. There are many fingerprinting tools available, such as httprint and WebTech, but there are even more that can aid us in reconnaissance.

Wi-Fi tools keep getting more and more accessible to beginners, and the LAZY script is a framework of serious penetration tools that can be explored easily from within it. This powerful and simple tool can be used for everything from installing new add-ons to grabbing a WPA handshake in a matter of seconds. Plus, it's easy to install, set up, and utilize.

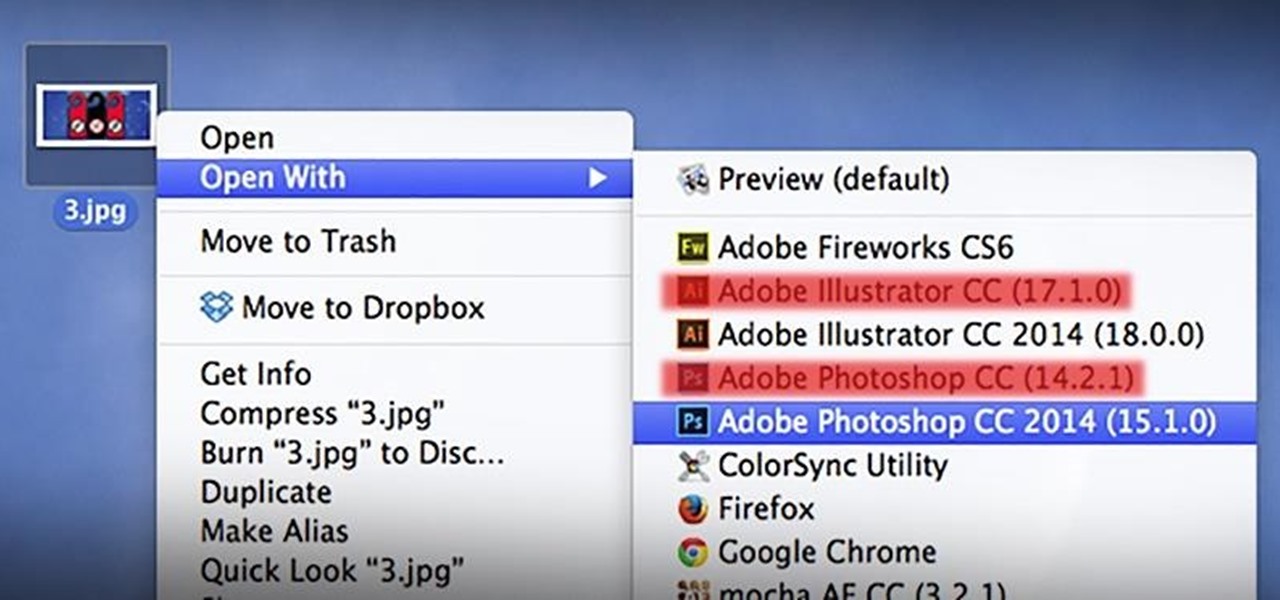
As a regular Mac OS X user, I have a love/hate relationship with the "Open With" contextual menu. Sometimes, it has just what I need. Other times, it's often packed with unnecessary or duplicate items, or missing the app I want to open the file up with the most.

The advent of ARKit and ARCore has strengthened the demand for development tools to build augmented reality experiences for compatible iPhones, iPads, and Android devices.

With Apple ready to unleash ARKit to millions of iPhones and iPads and ARCore on its way to supporting millions of Android devices, is there room in the world for a cross-platform mobile AR platform?

In this project I have use a die from the Tim Holtz range of Frameworks dies, in the standard lattice style and I show you how I use the Lattice and the throwaway pieces to make a great background for your cardmaking, scrapbooking and paper projects. Step 1: Now Watch the Tutorial

Step 1: What Exploit Development Is and Why Should I Be Interested on About This Topic

There are many tools out there for Wi-Fi hacking, but few are as integrated and well-rounded as Bettercap. Thanks to an impressively simple interface that works even over SSH, it's easy to access many of the most powerful Wi-Fi attacks available from anywhere. To capture handshakes from both attended and unattended Wi-Fi networks, we'll use two of Bettercap's modules to help us search for weak Wi-Fi passwords.

RouterSploit is a powerful exploit framework similar to Metasploit, working to quickly identify and exploit common vulnerabilities in routers. And guess what. It can be run on most Android devices.

Between acquisitions, hirings, patent applications, and insider reports, all signs point to Apple building a smartglasses product that could ship as soon as 2020, but the company has not officially confirmed such plans.

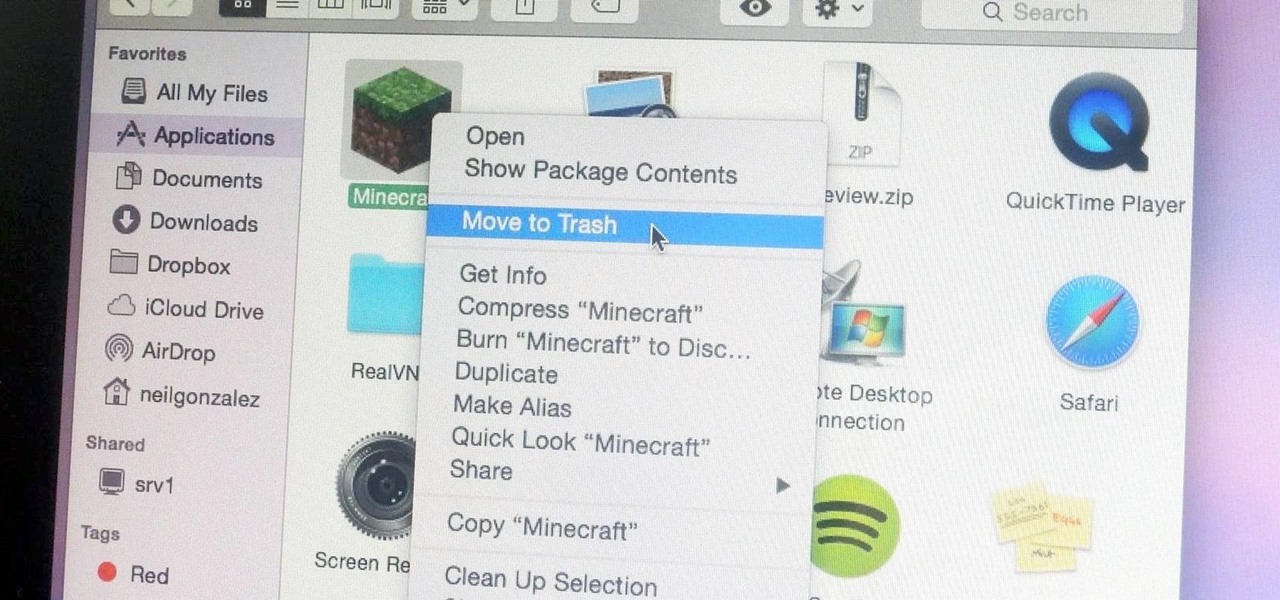
Uninstalling an app on your Mac isn't as straightforward as you would think. When you drag and drop an app into the Trash, then empty it, the main app itself may be gone, but many associated files and folders are left behind. So how do you get rid of them? There are a couple of ways.

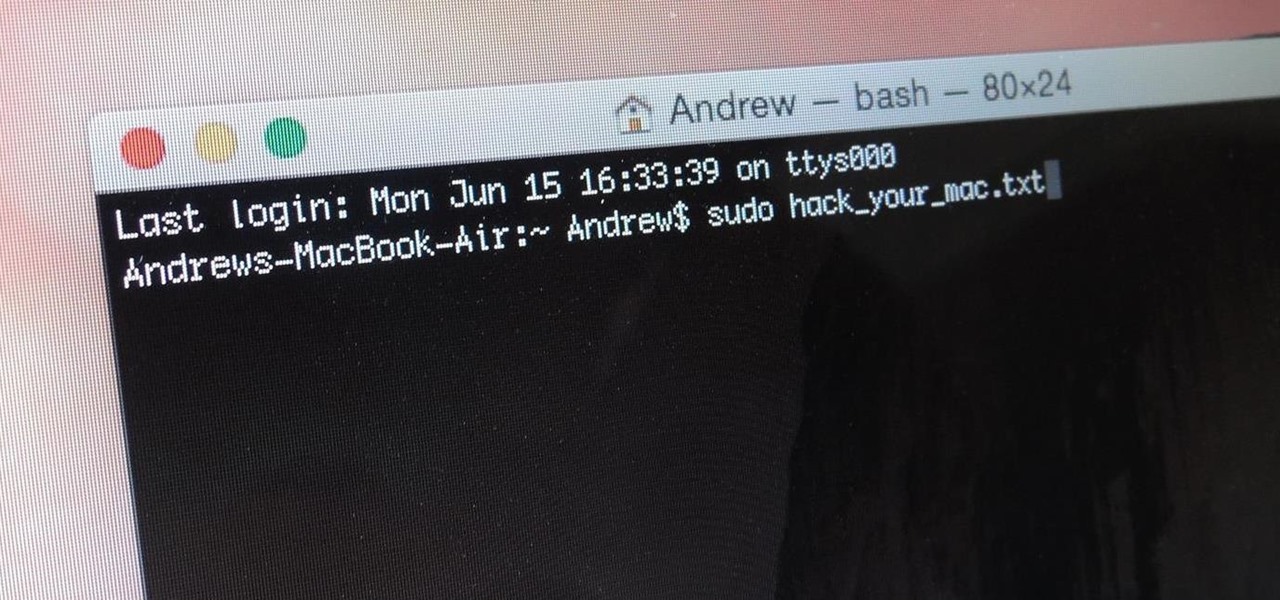
When you think of Terminal, you probably imagine some hacker sitting in front of their computer in a dimly lit room trying to break into an FBI database. In reality, it's just a simple tool that can make using your Mac much easier.

More and more tech-savvy leaders are flocking to the lucrative and exciting world of project management thanks to the high-pay, analytical environment, and nearly unparalleled flexibility. But this means that competition for the best positions in this dynamic field is fierce. If you want to stand out from the crowd, you're going to need to have more than a few base-level certifications on your résumé.

If you're reading this, you're likely a tech-savvy coding pro whose analytical talents are mostly applied to designing apps, cracking passwords, and infiltrating networks — all of which are admirable activities for both aspiring and seasoned white hat hackers. But there are other profitable ways that you can put these types of skills to use, namely in the world of investment and trading.

After the spectacular rise and fall (and rebirth) of Glass, Google is taking another run at augmented reality smartglasses.

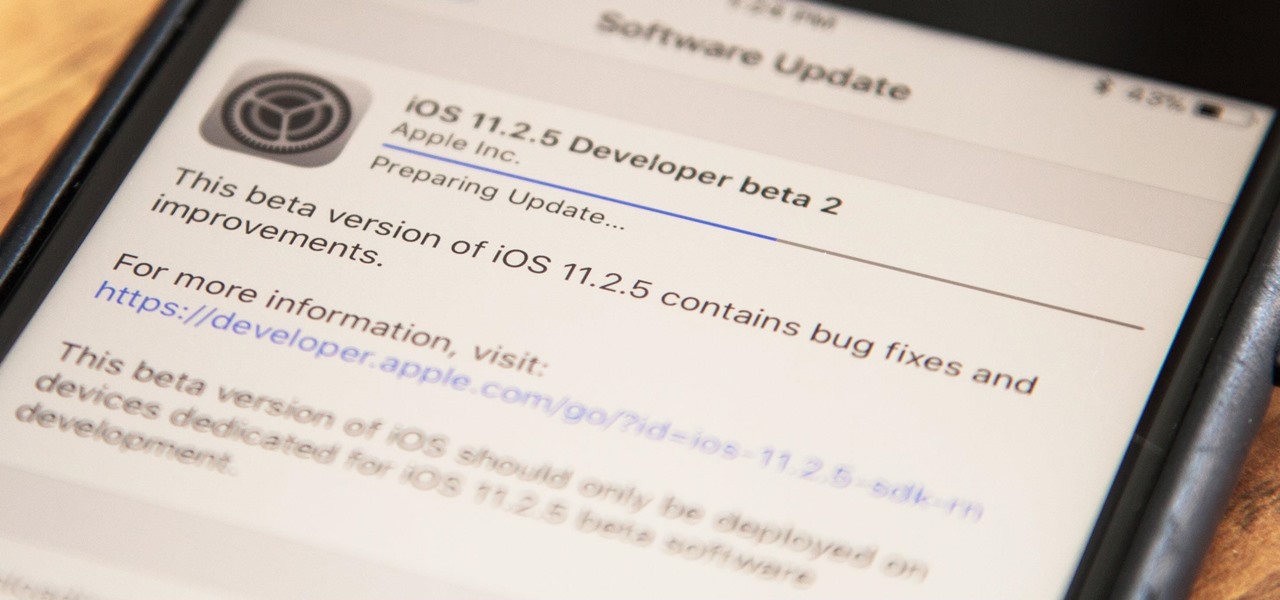
Apple has released the second beta for iOS version 11.2.5 for developers on Dec. 19. The update comes six days after the release of the first 11.2.5 beta which updated the Music app to include a persistent "play bar" at the bottom of the window, along with some bug fixes. Public beta testers received the update on Dec. 20.

Social engineering makes headlines because human behavior is often the weakest link of even well-defended targets. Automated social engineering tools can help reclusive hackers touch these techniques, but the study of how to hack human interactions in person is often ignored. Today, we will examine how to use subtle, hard to detect persuasion techniques to compromise a human target.

The most common Wi-Fi jamming attacks leverage deauthentication and disassociation packets to attack networks. This allows a low-cost ESP8266-based device programmed in Arduino to detect and classify Wi-Fi denial-of-service attacks by lighting a different color LED for each type of packet. The pattern of these colors can also allow us to fingerprint the tool being used to attack the network.

Knowing just one or two programming languages is no longer sufficient if you want to make serious money in the lucrative world of web design and development. But the good news is that you don't need to spend an excessive amount of time or money on a traditional coding education to get the skills you need to thrive.

Few things are more important than being well-versed in data analytics and interpretation when it comes to succeeding in today's increasingly data-driven world. As a data scientist, these skills are the key to a high-paying career. For hackers, there's no better way to defeat the enemy than to become the enemy.

We've shared a capture-the-flag game for grabbing handshakes and cracking passwords for Wi-Fi, and there are some upcoming CTF games we plan on sharing for other Wi-Fi hacks and even a dead-drop game. While security-minded activities and war games are excellent ways to improve your hacking skills, coding a real video game is also an excellent exercise for improving your programming abilities.

Communication is an essential skill for successfully launching products. Whether you're developing the latest and greatest app or trying to get ahead of a large data science project, effective communicators are always in high demand.

After improving hand-tracking and adding multi-user sharing features in the last Lumin OS update, Magic Leap has upped the ante yet again.

Over the past year, two trends have emerged among augmented reality development software: make it easier to create AR content, and give AR apps better environmental understanding with just a smartphone camera.

On Thursday, Epic Games released Unreal Engine 4.20, which finally includes support for the latest iterations of ARKit and ARCore, as well as Magic Leap One early access.

The Washington Post believes augmented reality adds an extra layer to stories, and they're doubling down on that belief by adding in new AR features into their already popular "rainbow" news (iOS and Android) and Classic (iOS and Android) news apps.

While most people have only begun hearing the term augmented reality in the last year or so, AR has been around in some form since the early '90s. It all started with heads-up displays (HUDs) for pilots to see instant information in their visors, but has graduated to a far more useful and widespread technology thanks to the advancement of computers and, more recently, smartphones.

UPDATE: A patch to fix the exploit has been released. Download it here.

With technology giants like Apple and Google finally entering the fray, the move toward mass adoption of augmented reality is ramping up. Apple's ARKit and Google's ARCore will allow entirely new categories of apps to be made. Unfortunately, in a world of heavy competition, getting these two frameworks to work together wasn't a priority for either company.

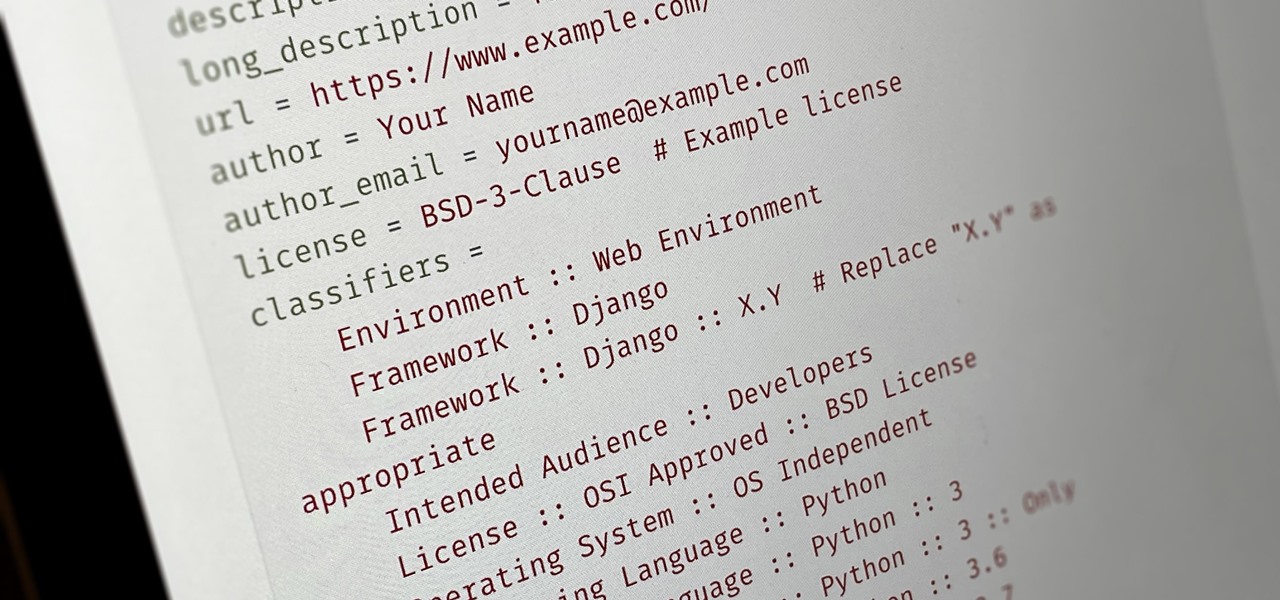
Everybody wants to build an app, but no one wants to start it from scratch. Building a full-blown application — or any other digital product for that matter — from the ground up entails some tedious work, which is why frameworks exist. Django, a Python-based framework, happens to be one of the best

Data makes the world go round. It has gotten to the point that it's considered the most valuable resource, perhaps even more important than oil. Businesses use data to collect critical information about their users and improve their services; governments utilize it to improve things like public transportation; doctors analyze data to find more ways to save lives.

Penetration-testing frameworks can be incredibly useful since they often streamline certain processes and save time by having a lot of tools available in one place. Of course, the most popular pentesting framework is undoubtedly Metasploit, but there are many others out there that cater to particular needs. For auditing web applications and servers, Tishna comes in handy.