
News: Syphilis Outbreak in in Oklahoma County Linked to a Social Network Defined by Drugs & Sex
There has been an outbreak of syphilis in Oklahoma County with 75 confirmed cases connected by a social network driven by drug use and sex.


There has been an outbreak of syphilis in Oklahoma County with 75 confirmed cases connected by a social network driven by drug use and sex.

Security journalist Brian Krebs recently suffered a record-breaking DDoS attack to his his website, clocking in at or near a whopping 620 Gbps of traffic. Krebs' site was down for over 24 hours, and it resulted in him having to leave his CDN behind.

MagicTree is often the go-to tool for data collection and reporting for many pentesters. It organizes data in nodes in a tree-structure which is very efficient at managing host and network data. Reports can be completely customized to meet the user's needs. Also, MagicTree allows you to import XML data and has XSLT transforms for Nessus, Nmap, OpenVas, Burp, Nikto. MagicTree comes pre-installed in Kali.

With troves of sensitive information, like receipts and password reminders, hiding in your email, your inbox can become a sort of Holy Grail for hackers—or anyone with your password. Although my crazy ex-girlfriend had no hacking experience, using my email login, she was able to find a lot of account information with just a general search for "password" in my inbox.

Yes, "Safer Internet Day" is a real thing, and it's actually been around for 12 years. This year, Google again will be commemorating the event by giving away a 2-gigabyte storage bump for their Google Drive cloud service if you simply run through a security checkup.
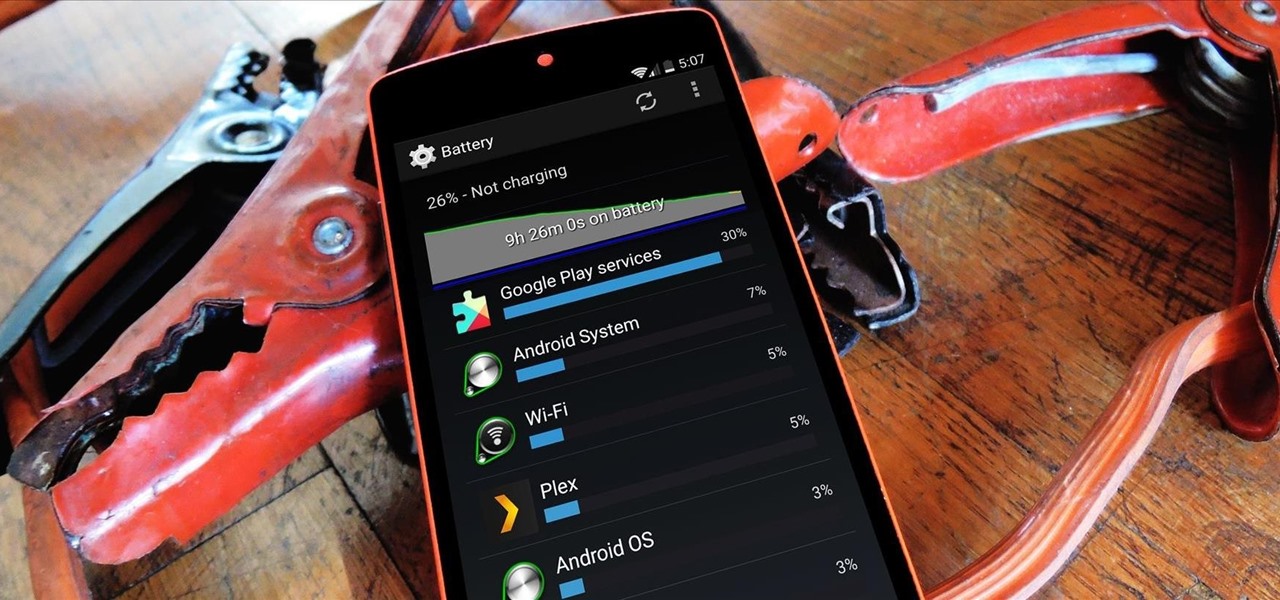
An app can request a wakelock to prevent your Android device from entering sleep mode so that it can sync data in the background. This obviously drains your battery, because instead of running in low-power sleep mode, your processor is fully activated while it performs its tasks.

The @DesignGears guys have been busy today, leaking an unofficial KitKat build (Android version 4.4.2) for the AT&T Samsung Galaxy Note 3. The latest is a peek into what the international variants are beginning to see, although this build is far from official. Still, if you want to give it a shot, I'll show you how to install it, but make sure to check out the details below the how-to to see what you can expect, good or bad.
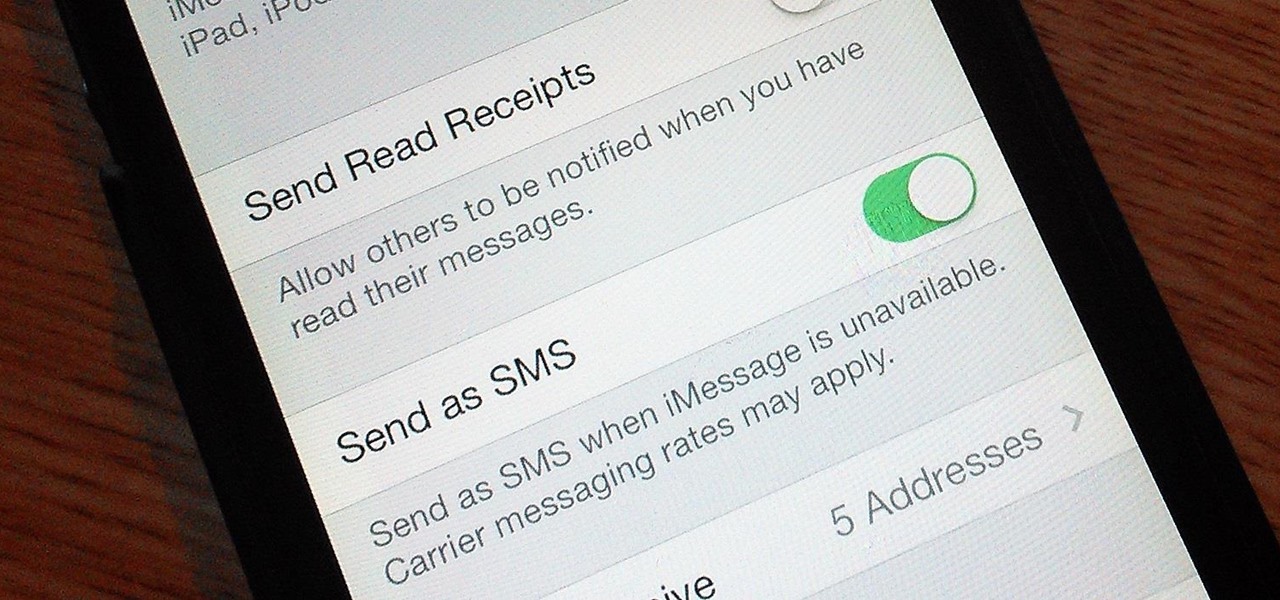
If you're an iPhone user, iMessage is great for cutting down on SMS costs from your carrier, but it doesn't always work right away.
An amazing amount of news this week; new proposals and new agreements have sprung up. But so has our "need" to spread our presence. The military warns of another war, while 26 congressmen decry the use of drone strikes. Read on:

Non-stick cookware is a great way to cook and not have to deal with foods that stick to regular pans or deal with the cleaning up after cooking. A few rules to keep in mind are to not preheat a non-stick pan and do not use a heat level above medium. If you break or damage the surface of the pan, it could cause more damage than you think. There have been reports where you could develop flu-like symptoms just from cooking with a bad pan.

New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this MS Excel tutorial from ExcelIsFun, the 255th installment in their series of digital spreadsheet magic tricks, you'll learn how to create a two-variable data table in Excel for what-if analysis. See the PMT function and learn about the formula equivalent to a data table.
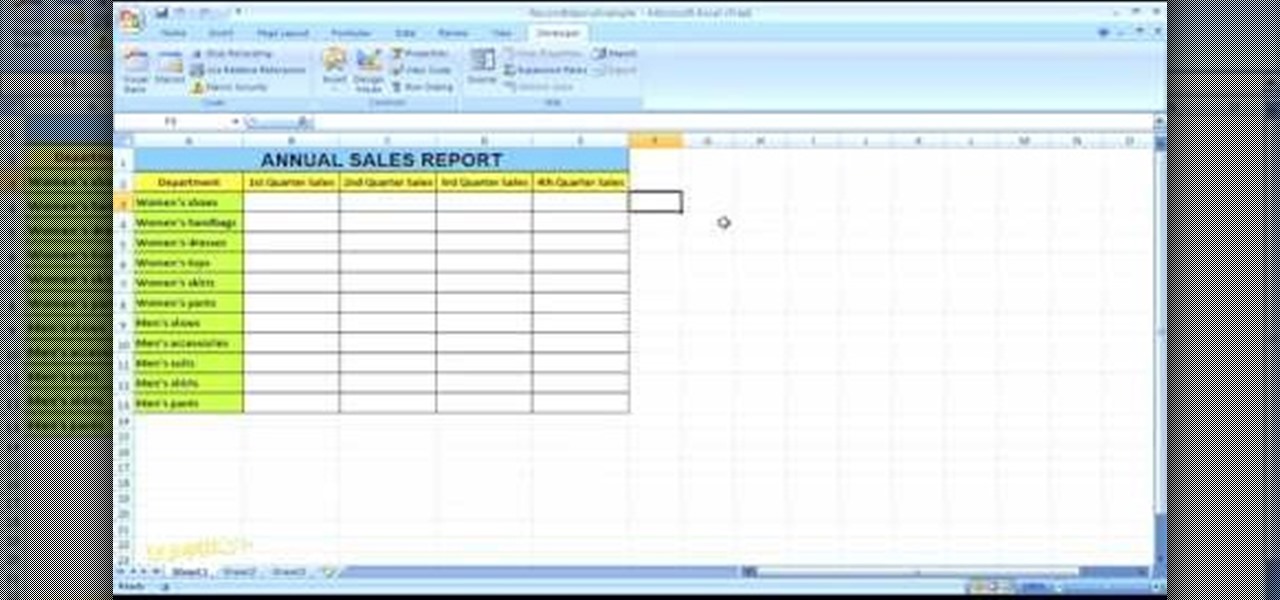
In this Microsoft Excel 2007 for Dummies video the instructor shows how to record a Macro. Macros let you create a shortcut to perform a sequence of commands all at once. For example you can create a macro to quickly build a sales report template that you frequently use. When ever you run that macro the Word will automatically build the template for you based on the recorded commands. To write macros you need to have the developer tab enabled. To enable it click on the office button and at th...
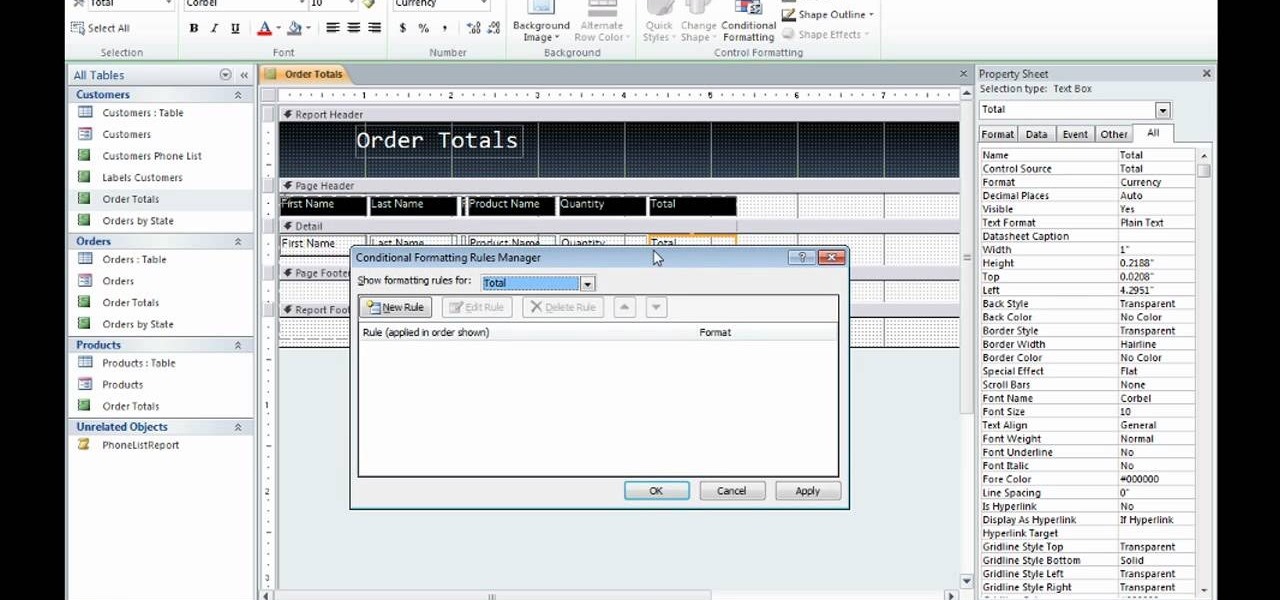
lyndapodcast teaches you how to apply conditional formatting withing Microsoft Access 2010. You click View - Design View. Click the Total tab and you'll notice some highlighted options above. Click Format and then Conditional Formatting. This where you will create rules. Click the new rule button. Now you will see the conditions with drop-down menus. Type in the numbers you want and then select the formatting you want when the rule is true. The preview below will show you how the numbers will...

Master mixologist Chris McMillian walks us through the history and preparation of the Bloody Mary. What a great way to start the day! The Bloody Mary is a classic pick me up reported to have been created in Paris during prohibition. The drink has also been called the Red Snapper, though most people still know it as a Bloody Mary.

Rumors around Apple's not-so-secret development of an AR/VR headset have been prevalent throughout the young year, but the latest round of reports move speculation of the device into a clearer view.
Rumors of Apple developing smartglasses have persisted as prophecy since 2016, but the arrival of what many herald as the savior of augmented reality have eluded even Nostradamus himself.
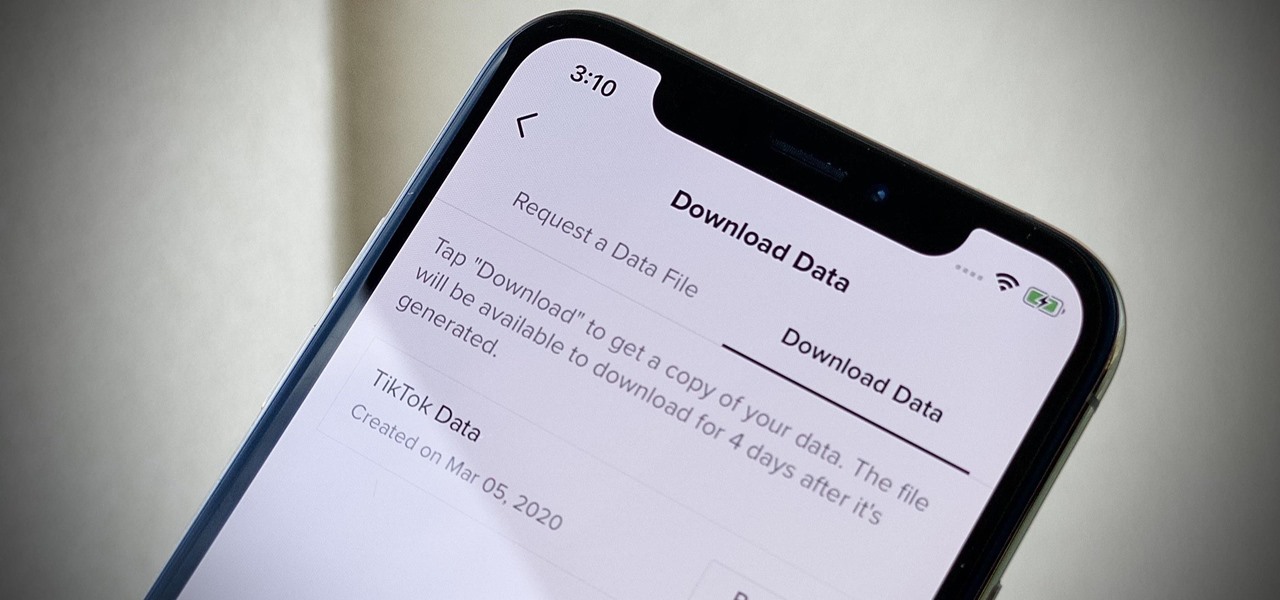
If you're concerned about your privacy, TikTok might not be the app for you. Its shady practices with user data have been the subject of concern, criticism, and even legal action by the US government. Then again, it's just so addicting. If, like me, you're not going to stop using TikTok anytime soon, you should at least know how to view the personal data it has collected on you.
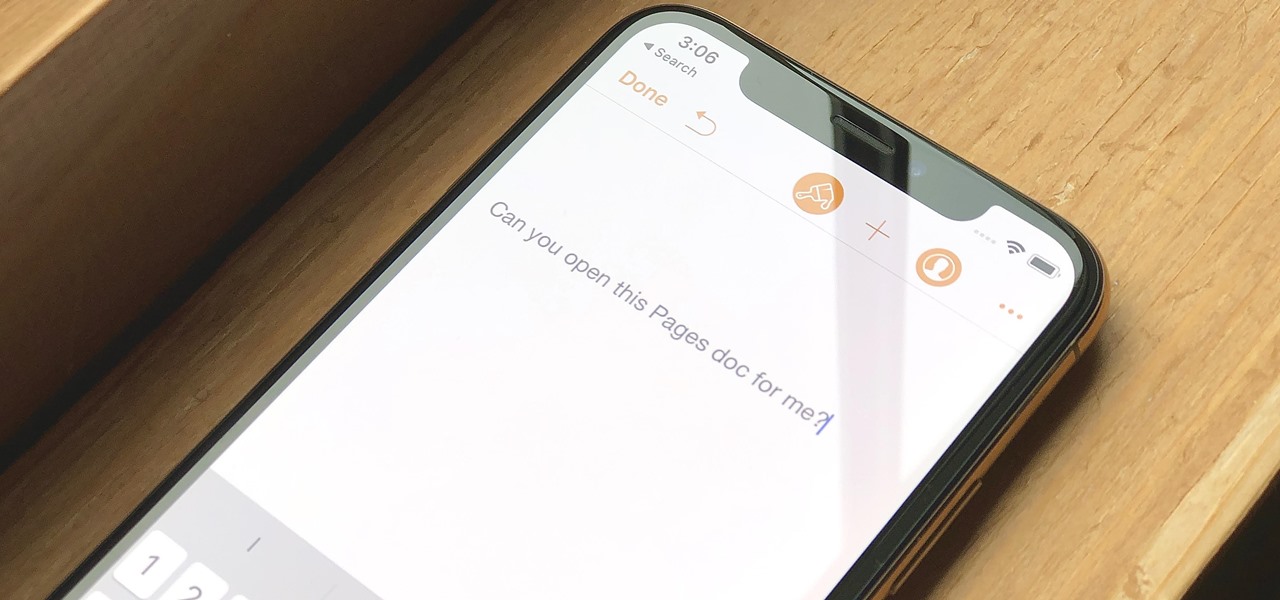
Let's say you have an important report to submit, but you want to check it over for any last-minute edits or changes. Times running out, and you simply can't find this Pages document anywhere. Wouldn't it be great if you could just ask your iPhone to open the report for you, so you could stop wasting time searching and finish the paper? Well, thankfully, Siri can help you out with that.
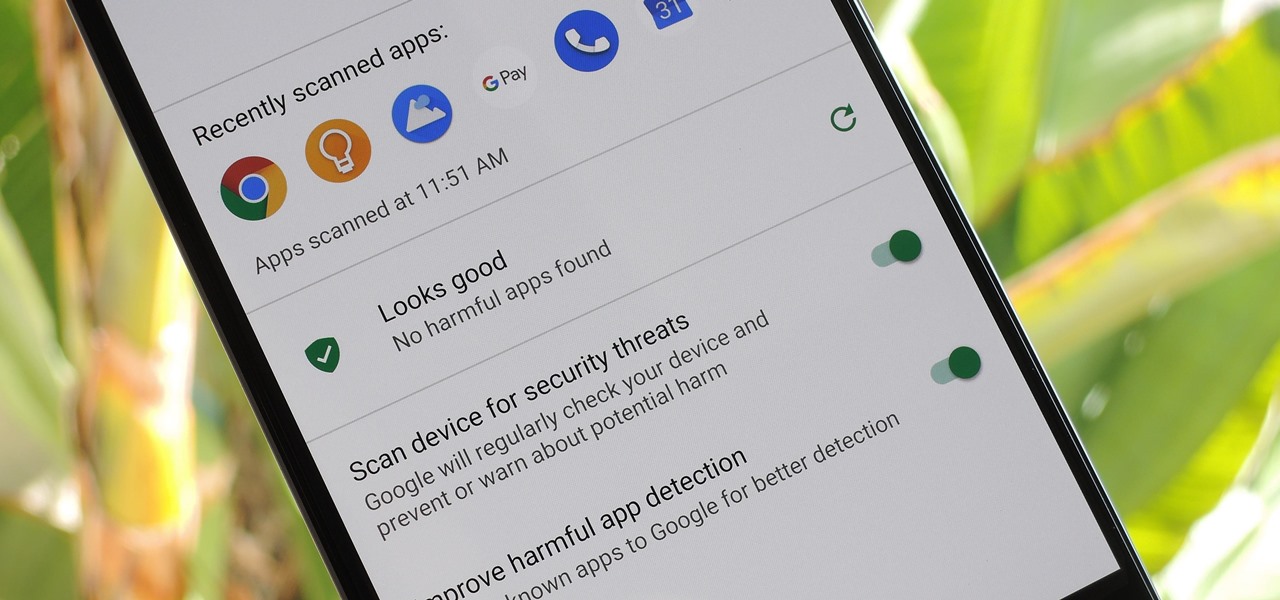
According to Google's new Android ecosystem transparency report, you're eleven times more likely to be infected by malware if you're running Android Lollipop (5.0) as opposed to Android Pie (9). The same report shows that if you sideload apps, you're almost seven times more likely to be infected than if you stick to Google Play as your app source. All of the data provided in the report is quite interesting, but there's a clear pattern among malware-infected users.
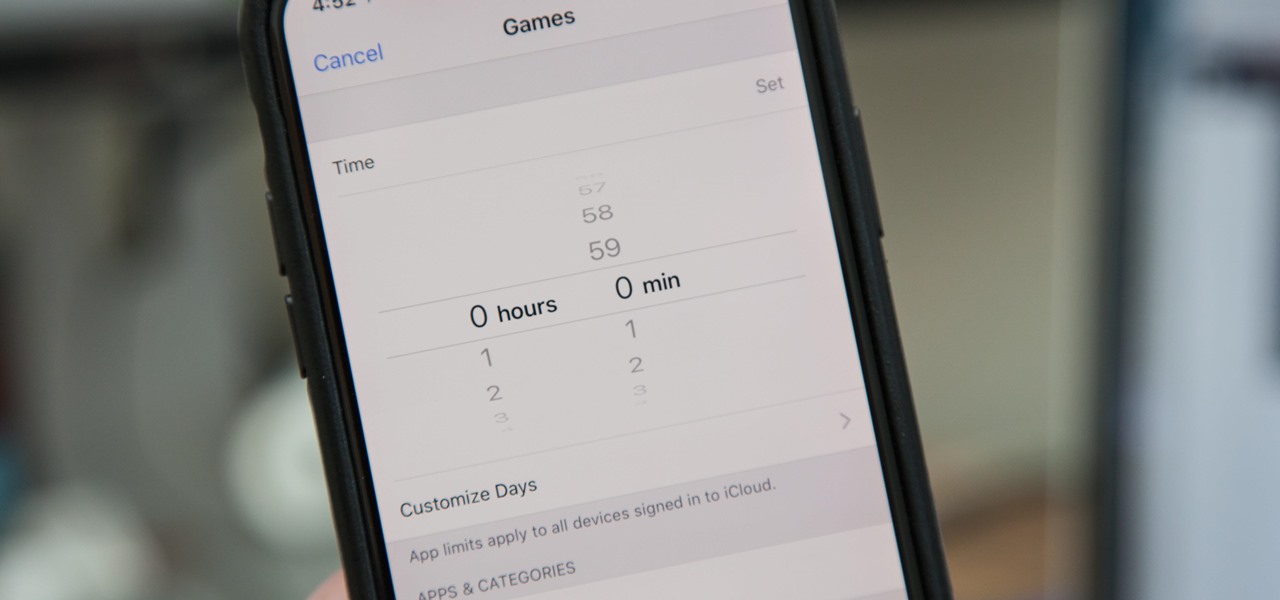
Most of us have, at one point or another, found ourselves glued to our smartphone in a trance-like state, totally unaware of what's around us. Well, Apple has a way to curb overuse with an awesome tool for iPhone starting in iOS 12. It can help nudge us away from our phones to spend more time attending to real-life matters.
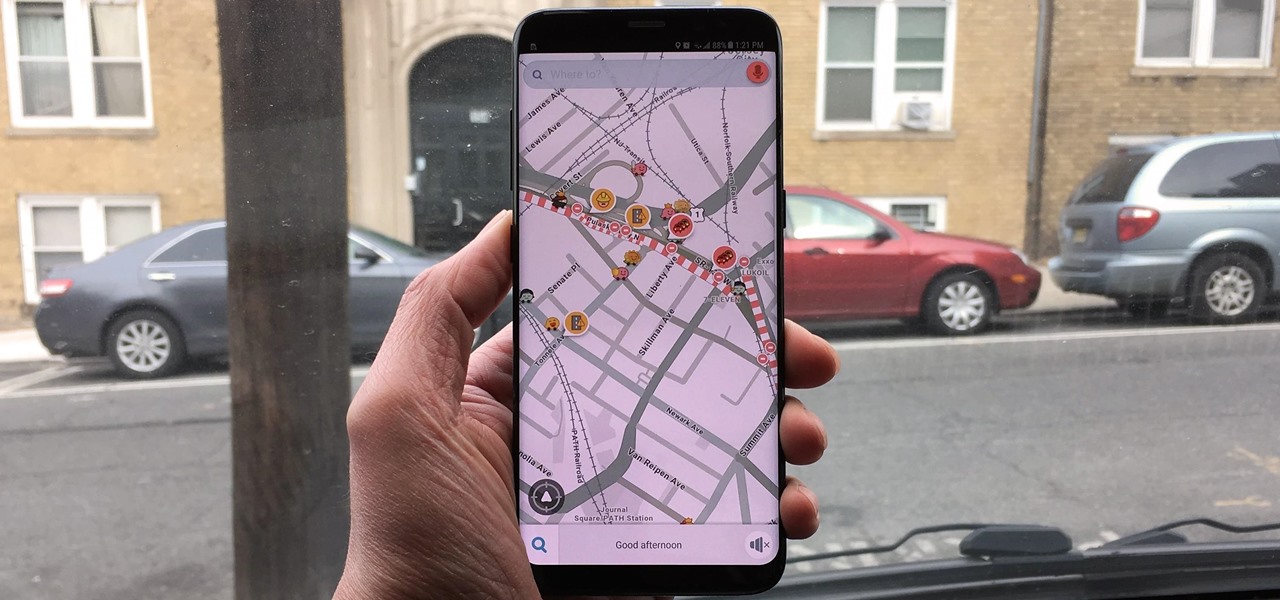
Because it sources a majority of its vital data from actual drivers on the road, Waze is easily one of the best navigation apps to use if you prioritize safety. Benefits such as crowd-sourced traffic data, police trap locations, and road work avoidance, when combined, help you anticipate traffic conditions with unprecedented accuracy and make adjustments accordingly.

Now that we finally have vertical plane recognition in ARKit (at least on a developer level until the spring iOS 11.3 release), the real promise of mobile augmented reality is beginning to come into focus on iOS. But a new report indicates that a major near future advancement of ARKit that could change everything has been put on hold by Apple.

With the big reveal of the Magic Leap One: Creator Edition in December 2017, and now the update on Feb. 13, 2018, we no longer have to speculate as to what the augmented reality headset will look like or when (in general) it will be available.

This week, two companies looking to capitalize on the growing augmented reality industry, raised funding from starkly different sources.

In my previous article, I discussed installing and configuring OpenVAS on Kali Linux. Now it's time to start using OpenVAS with the Greenbone Security Assistant to audit networks for security issues. This can be extremely helpful when you are looking for vulnerabilities or misconfigurations in a large number of hosts.
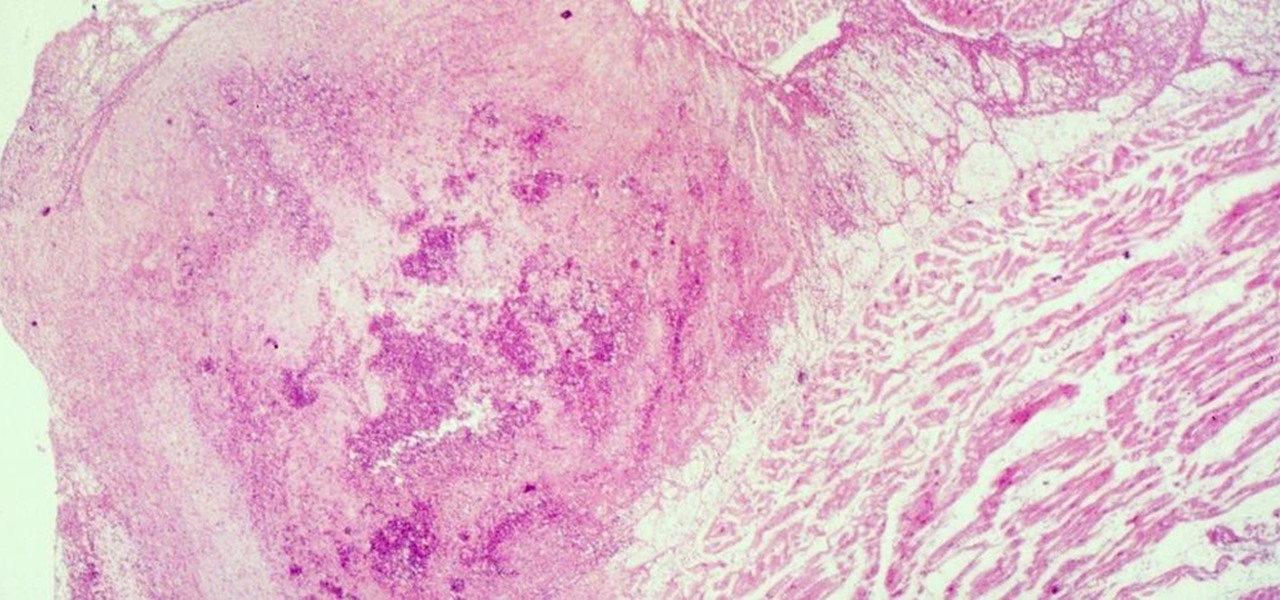
Four million Americans misused prescription opioid painkillers in 2014. Those who do are 40 times more likely to inject heroin or other drugs than other people. Now, the Centers for Disease Control and Prevention (CDC) are blaming that misuse for a 12-fold increase in endocarditis, an infection of the heart valves.

Paying for street parking in New York City just got so much easier. Instead of searching for loose change or hoping you didn't forget your wallet, you can use a device you always have with you: your phone.
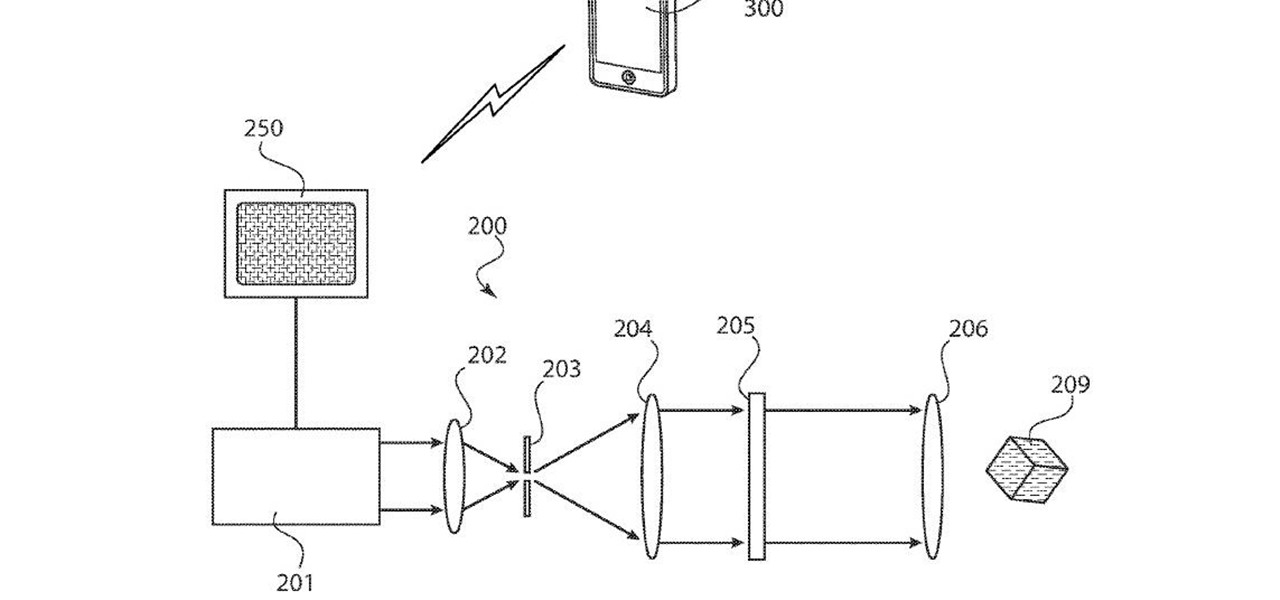
One inventor wants to bring augmented reality to internet radio and home audio speakers. Meanwhile, a leading consumer electronics company has opened up access its deep learning tools for building augmented reality apps. In addition, analysts examine how augmented reality will impact the design and construction and profile the top developers in augmented and virtual reality.

Food is both a necessity and a joy. Many people enjoy exploring, cooking, eating, and learning about foods from around the world. But the picture isn't always rosy. A new report from the Centers for Disease Control and Prevention (CDC), highlights the ways and whereabouts of food that make us sick.

At this point, I'm ready to give Apple CEO Tim Cook a piece of my mind. The hype surrounding the iPhone 8 is crazy, and rumors are circulating constantly. So many different things have been said about its release date that no one can even keep track anymore. If Cook could throw us all a bone and give us a hint, it would quiet the speculation. Unfortunately, it doesn't look like that'll happen anytime soon, but — in the meantime — a new report allegedly has the inside scoop. Recent rumors surr...

The Cloud Security Alliance (CSA), a leading IT trade association, has published its first report on risks and recommendations for connected-vehicle security, ahead of when driverless cars are about to see volume production in the near future.

Over 90% of ride-or-die iPhone users will upgrade to the latest Apple smartphone, according to a recent survey. Really, though? Well, Morgan Stanley certainly seems to think so.

Updated 5/2/17: CultofMac reports analysts at Deutsche Bank are confirming the delays. The analysts believe the delays are due to "component shortages and technical challenges." This would corroborate the rumors listed below. We here at Gadget Hacks will bring you more on this story as it develops.

Reports of Zika-related birth defects are coming in at shockingly low rates in Puerto Rico. While that might be something to cheer, one former US government official is saying there could be a nefarious reason for the low numbers.

For some, drinking raw milk is a way to get back to nature, improve family nutrition, and hedge against asthma and allergies. However, according to public health authorities, drinking raw or unpasteurized milk is a big mistake—even fatal. So what's the story?

Sleep lets our body processes rest and restores us for the next day, so a bad night's sleep can ruin the following twenty-four hours and even make us feel sick. Now, new research published in the journal Sleep cements the idea that loss of sleep actually leaves us vulnerable to sickness.

Many users across the web have reported issues with receiving notifications from the Gmail and Hangouts apps on Android. The problem is most prevalent with users running Marshmallow, and the gist is that notifications from these apps are extremely delayed or don't come through at all.

While CNN, FOX News, and MSNBC are valuable sources of information for what's going on in the world today, they may not be the best news stations to watch if you actually want to learn something. They, along with local news stations, are great at grabbing your attention, but if you truly want to learn something about recent events, you're tuning into the wrong channel.

Welcome back, my novice hackers! Most of my tutorials up until this point have addressed how to exploit a target assuming that we already know some basic information about their system. These include their IP address, operating system, open ports, services running, and so on.

Will the predicted apocalyptic date—December 21st, 2012—really be the end of the world? In this ongoing five-part series, we examine what would happen if zombies, nuclear weapons, cyber wars, earthquakes, or aliens actually destroyed our planet—and how you might survive.