Web application vulnerabilities are one of the most crucial points of consideration in any penetration test or security evaluation. While some security areas require a home network or computer for testing, creating a test website to learn web app security requires a slightly different approach. For a safe environment to learn about web app hacking, the OWASP Juice Shop can help.

Leaked databases get passed around the internet and no one seems to notice. We've become desensitized to the data breaches that occur on a daily basis because it happens so frequently. Join me as I illustrate why reusing passwords across multiple websites is a truly awful practice — and compromise hundreds of social media accounts in the process.

Hackers rely on good data to be able to pull off an attack, and reconnaissance is the stage of the hack in which they must learn as much as they can to devise a plan of action. Technical details are a critical component of this picture, and with OSINT tools like Maltego, a single domain name is everything you need to fingerprint the tech details of an organization from IP address to AS number.

JavaScript is one of the most common languages used on the web. It can automate and animate website components, manage website content, and carry out many other useful functions from within a webpage. The scripting language also has many functions which can be used for malicious purposes, including stealing a user's cookies containing passwords and other information.

Dirty, malformed, and outright mischievous text strings have long been the enemy of interactive website developers. Strings contain any combination of letters, numbers, spaces, and punctuation, and are entered into text boxes on websites by users. These strings in particular can do everything from highlighting XSS vulnerabilities to soliciting 404 error pages.

This weekend, Atlanta, Georgia will be the battleground for a large group of HoloLens designers and developers. HoloHack, a 24-hour hackathon put on by elevator manufacturer ThyssenKrupp, will be taking place at The Garage, and the design theme will be smart cities.
Have you ever used an open wifi, which after you connect displays a website to enter your credentials to get internet? That website is called captive portal and widely used in airports, hotels, universities etc. Have you ever wondered what would happen if someone would set up an open wifi with the same name displaying a very similar web page asking for credentials? Usually if there are multiple wifi networks with the same name and encryption, devices only display the one with the highest sign...

Welcome back, my greenhorn hackers! Throughout this series on Metasploit, and in most of my hacking tutorials here on Null Byte that use Metasploit (there are many; type "metasploit" into the search bar and you will find dozens), I have focused primarily on just two types of modules: exploits and payloads. Remember, Metasploit has six types of modules:

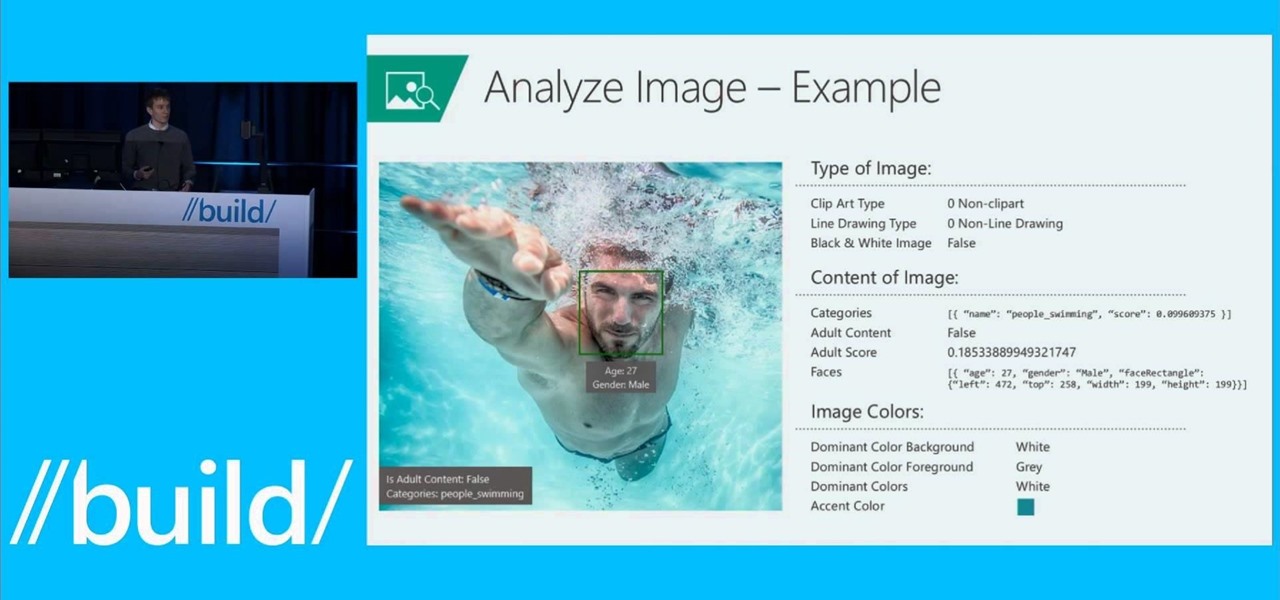
Microsoft is developing a new API project called poject "Oxford," and it includes face, speech, and more "smart" API technology. Despite being Microsoft, I actually found this to be very useful. ;)

Heads up! We've done a new, more thorough review of the best Android file-sharing apps. You can check that out here. Our old file-sharing app roundup can still be viewed below for posterity.

Reddit is a force to be reckoned with. What started out as link aggregator has become one of the world's most popular websites, with over 170 million unique visitors and 6 billion monthly pageviews. Whether you're into cute animals, crazy conspiracy theories, sports, or Taylor Swift's armpit, Reddit definitely has something for every taste, interest, and morbid curiosity.

Welcome back, my novice hackers! In my series on cracking passwords, I began by showing off some basic password-cracking principles; developed an efficient password-cracking strategy; demonstrated how to use Hashcat, one of the most powerful password-cracking programs; and showed how to create a custom wordlist using Crunch. In this tutorial, I will show you how to create a custom wordlist based upon the industry or business of the targets using CeWL.

Using Facebook and Twitter as a news source can be frustrating at times, mainly because opening links will divert you away from your current application. Instead of a smooth process, you find yourself going back and forth from app to browser, over and over again.

When browsing the web, you may not be quite as anonymous as you think, especially if you are using public WiFi. The easiest way to stay as anonymous and safe as you are going to get, is to use a VPN (there are a number of great free ones). In this tutorial, we will show you how to set up a VPN on Android, and how this protects you.

T-Mobile continues to make waves in the U.S. wireless market behind CEO John Legere's UnCarrier program. At the latest installment in a series of industry-challenging announcements, Uncarrier 5.0 unveiled Test Drive. The new program is set to allow would-be customers to try out the "latest generation" iPhone for seven days on T-Mobile's network without any financial commitments.

Welcome back, my novice hackers! There are SOOOO many ways to hack a system or network, which means you need to think creatively in order to be successful.

Below are the official rules and guidelines for submitting content to WonderHowTo. Please look over them before publishing any articles. Ignoring the rules could result in deletion of your article or being flagged as a spammer. Most of these rules apply to comments as well.

You'd think the ability to block calls from certain numbers would be built in to most phones by now, but that's certainly not the case with the iPhone.

Welcome back, my novice hackers! Most of my tutorials up until this point have addressed how to exploit a target assuming that we already know some basic information about their system. These include their IP address, operating system, open ports, services running, and so on.

In this web design tutorial learn how to use the straight line tool. Although the straight line tool might seem like a useless tool I can tell you from experience it is very useful. Especially if you have ever attempted to draw a straight line with a tool other than the straight line tool. There are many ways you could use the straight line tool such as dividing content, design graphics, separating navigation menu headers and much more. My recommendation would be that you take a look at some ...

Who wouldn't want to know if someone was trying to log onto their personal computer without their permission? Be it your annoying co-worker or your girlfriend, there are many cases where people may try to gain access to your desktop or laptop.

While there is definitely no shortage of video game emulators in the Android Market, it lacks in modern gaming consoles. Nintendo 64, Game Boys, and Sega Genesis are all accounted for, but what about emulators for some of the gaming consoles that have come out in the, let's say...past decade?

There's nothing more inherently awesome than looking up into the stars and wondering WTF is really out there. Outer space is one of those rare items that a Google search cannot provide all of the answers for.

Many social networks have become a part of our daily routine. Checking Facebook or sending out a Tweet are things millions of people do every single day. So, one would think that having a great app offering for Windows 8 would be a no-brainer. But, and this is a huge but, there are still no official Twitter or Facebook apps for Windows 8.

Check out this informative video tutorial from Apple on how to add a photo album in iWeb '09.

Check out this informative video tutorial from Apple on how to add a countdown clock in iWeb '09.

Right out of the box, iPhone is incredibly easy to use. If you want to get the most out of every feature, you’ve come to the right place. This video tutorial straight from Apple will teach you how to browse the web with Safari on the Apple iPhone 3G. The iPhone redefines what a mobile phone can do.

Having a secure password is essential in today's interconnected world. Hackers are just around the corner, and if you have an easy to guess or hack password that you use for all of your accounts, someone can login to all of your websites very easily. Look at this guide on how to create a strong password by following the right password rules so that your accounts stay secure.

What's the point of having a browser on your Android phone if you're only seeing part of the internet. Visit the full versions of your favorite web sites by configuring your Android browser to show nonmobile websites on your mobile phone.

This video will introduce you to a couple of websites that will let you know whether or not your Apple I device- iPhone, iPod, or iPad can be jailbroken. Check out this site or this site if you are interested in jailbreaking an iPhone 4, iPod touch, or iPad 2.

If you'd like to use your Firefox or Chrome browser bar for more than just navigating to websites, this little how-to from lifehacker will show you what you need to know. It's a handy trick that can expand your browser's functionality.

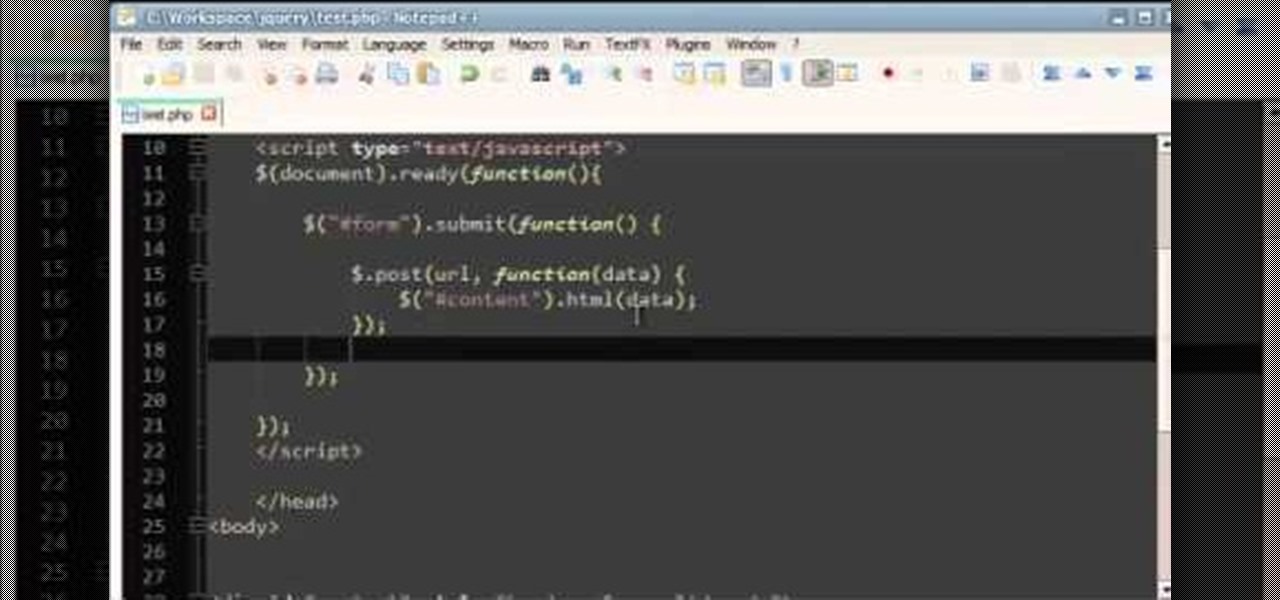
This tutorial is a quick introduction to the $.post() function when you're using JQuery. This function is most often used to submit data to your website server, and is also a useful function when you're programming in AJAX as well.

This tutorial shows you how to use some of the basic functions in Adobe Photoshop, including the ability to save an image in multiple file formats, to create a picture that you can easily use on your website or blog.

Take a regular font, type the name of your business or website into a text box, and then follow along with this tutorial. Break it apart and manipulate the layers so you can end up with a classy and eye catching logo.

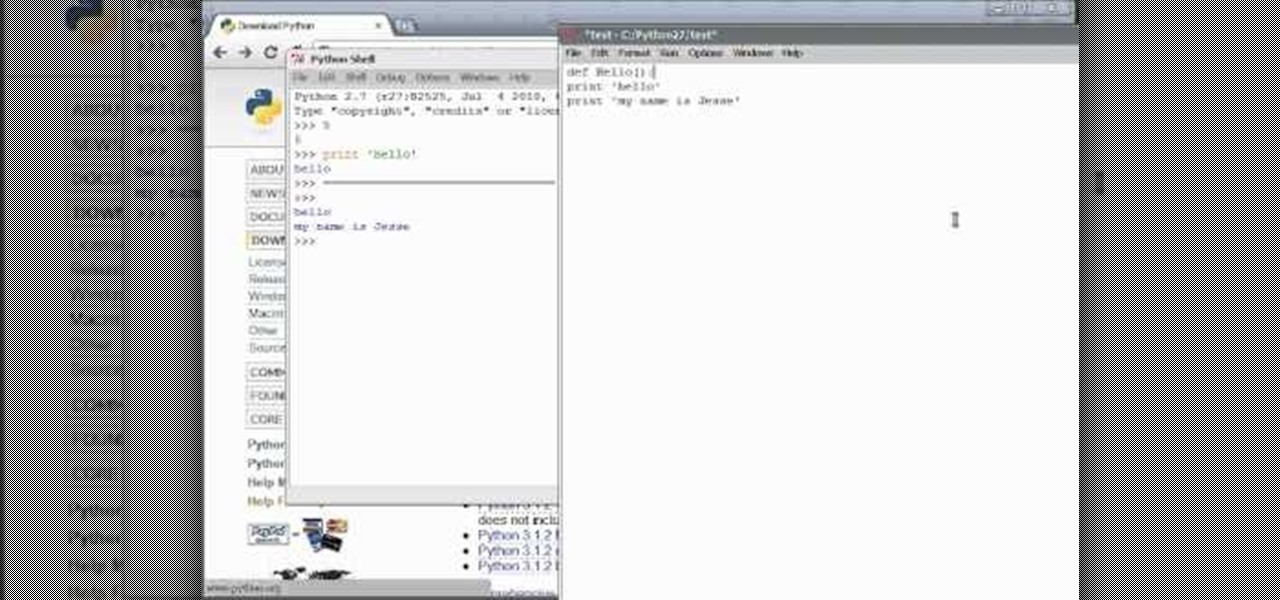
Python can be used for games, websites and operating system GUIs; and you can work with it on PCs, Macs or Linux machines. This tutorial shows you how to install the compiler and get started teaching yourself how to program in Python.

Want to be able to play Minecraft with all of your friends? This tutorial shows you how you can use a Mac so you can set up a server for playing multiplayer Minecraft. Download the program from the Minecraft website, then follow the procedure in the video.

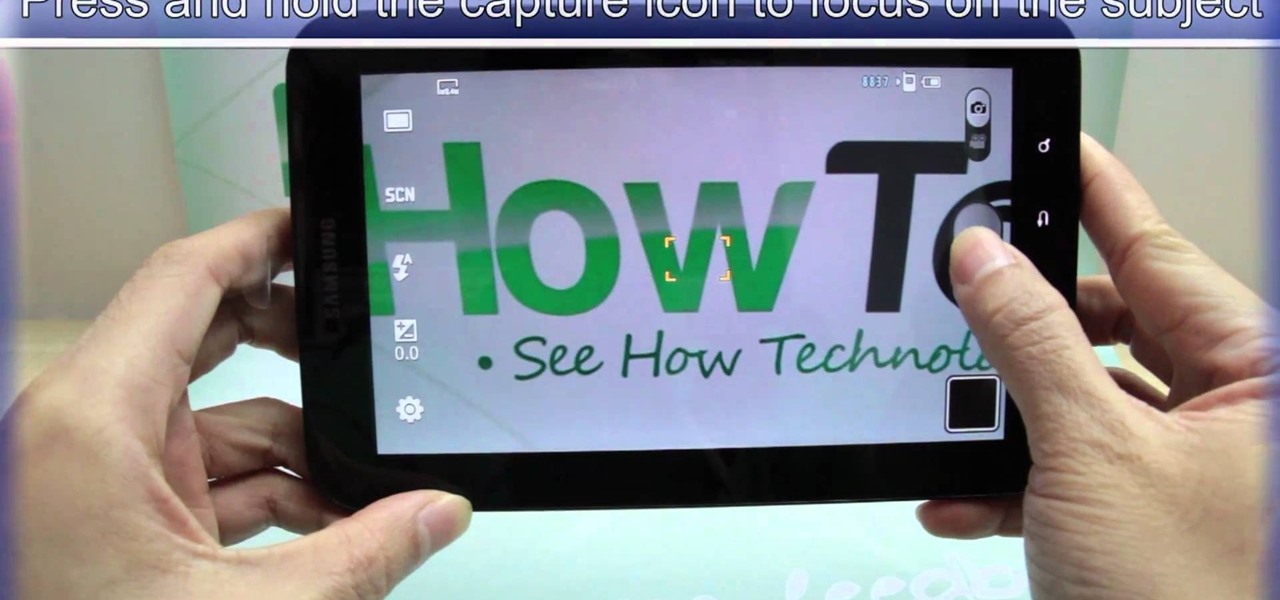
This video shows you how to use the camera on Samsung GALAXY Tab.

In this webmaster's guide, you'll learn how prevent Google from displaying the date when presenting a snippet from your website. Whether you're new to the world of search engine optimization (SEO) or are merely looking to pick up a few new tips and tricks, you're unlikely to find a better source than this official video guide from Google. Take a look.

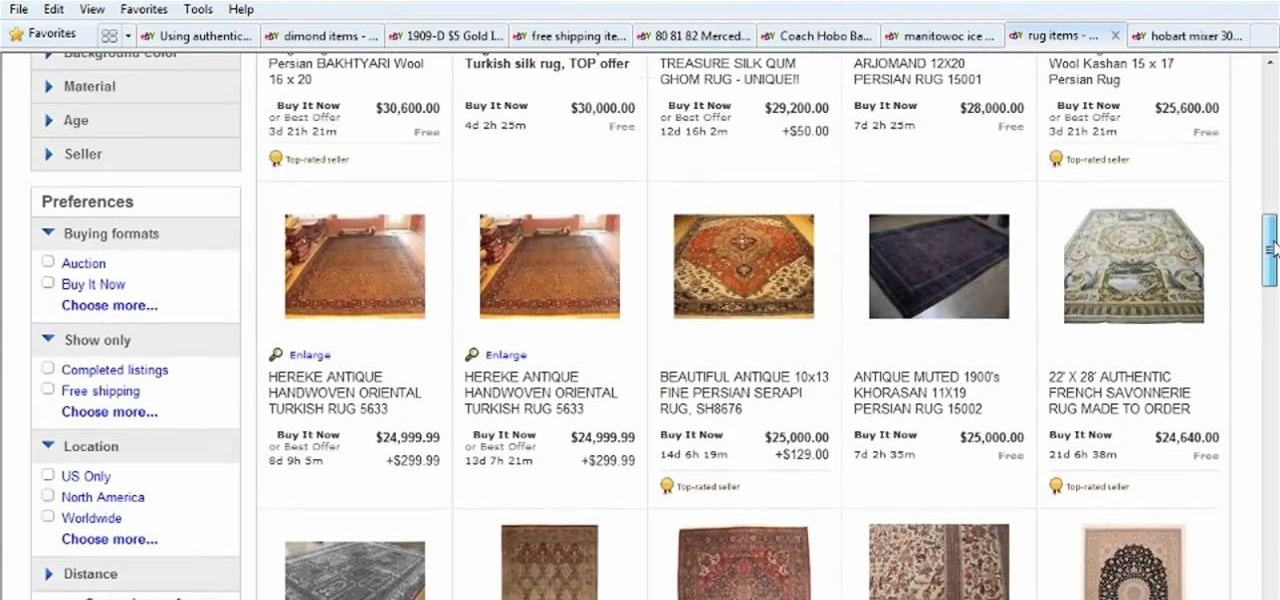
In this brief video guide from the folks at Lynda, we learn how to keep an eye on competing venders when selling merchandise on eBay, the popular online auction website. For all of the relevant details, including easy-to-follow step-by-step instructions, watch this video guide.

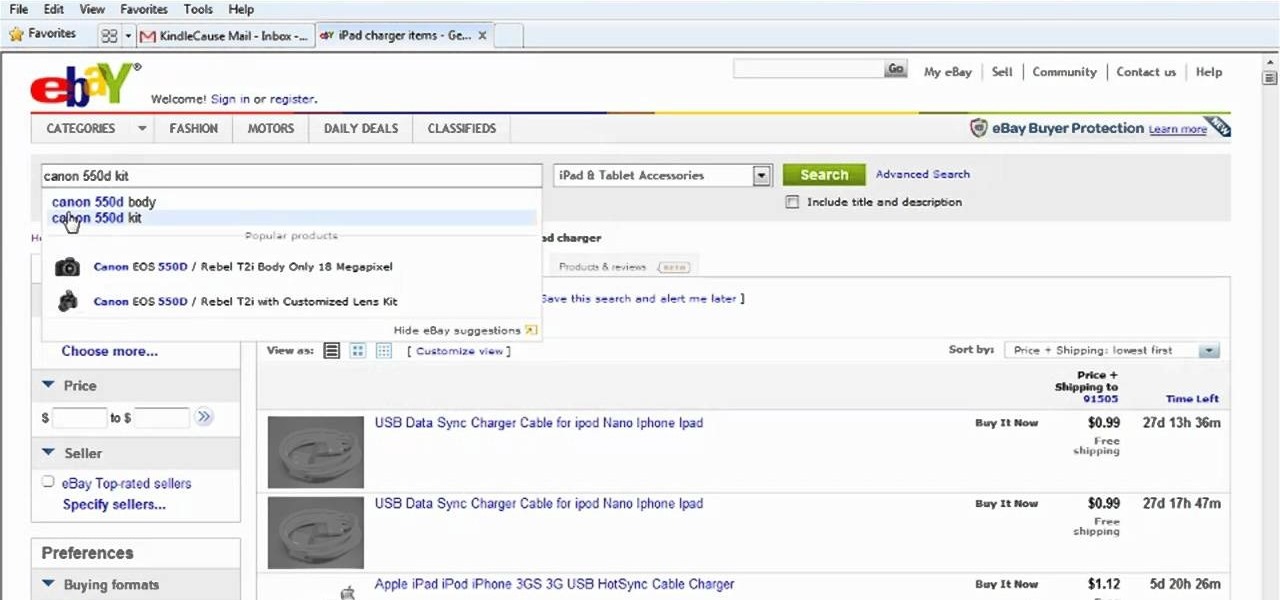
In this brief video guide from the folks at Lynda, we learn how to effectively search eBay, the popular online auction website. For all of the relevant details, including easy-to-follow step-by-step instructions, watch this video guide.