Instagram has long-resisted easily resharing content. While it's been testing a "regram" feature for a long time, it still lags behind apps such as Twitter and Facebook when it comes to resharing content. But while Instagram is a bastion of original material, there is a feature in place for you to reshare stories from those you follow. Your friends can reshare your stories too.

After two dramatic Conference Finals, the dust has settled to reveal ... the Golden State Warriors and the Cleveland Cavaliers. Well, at least the Irving-less Celtics and Rockets (short of Chris Paul for Games 6 and 7) gave it their all. With these teams battling for the fourth straight time, people want to know if the Cavs can even up the score at 2-2.

In what's becoming something of a regular occurrence, Magic Leap has yet another internal, unforced error on its hands. Thankfully, this time it's not about legal skirmishes or theft, but a rather unusual break from company protocol that has been quickly swept under the rug.

The stock home screen app that comes with your phone is nothing compared to Nova Launcher. Not only is Nova faster, but it's got tons of customization tweaks like gestures, adjustable grid sizes, and icon packs, just to name a few.

One of the most exciting features in iOS 11 was the fully revamped Control Center, which improved the overall interface visually, made it one page only, and finally made it possible to customize what controls actually appear within it. Customizable controls was previously only available to jailbreakers, but now it's available to anyone running iOS 11 or iOS 12.

Whether you simply can't stand it or consider it a separate food group (or not food at all), there's no denying that Spam is everywhere. America's favorite canned mystery meat got its humble beginning in Minnesota, but is now used in dishes and found in homes around the globe.

In the moment, buying a dozen donuts always seems like a good idea. In retrospect, however, it's always too much... and you inevitably end up with a box of stale donuts a few days later.

There is a huge myth that most Americans believe, and it might be the marketing triumph of the 20th century. We pay an absurd markup (Zero Hedge says as much as 280,000% for "designer" water) on something we can get for free because most of us believe that bottled water is healthier than tap water. But is it? Here are 5 reasons why tap water is probably better than that bottled stuff you drink. 1. It's Not Cleaner (& Might Be Dirtier) Than Your Tap Water

Airports are terrible germ-infested purgatories where people sit around for hours without Wi-Fi while they anxiously await to get wherever they really want to go. Unfortunately, there isn't much we can do about waiting, but this little Wi-Fi hack could help make the waiting a little less boring.

PRL, or Preferred Roaming List, basically tells your phone which towers to connect to first. Changing PRLs can improve reception and data speeds, and in some cases even give you access to corporate/test towers.

Creative Commons is awesome—really. If an image, video, or audio file is tagged with a CC license, that means you can use it as long as you give appropriate credit to the owner. For bloggers with no money for pricey stock media, it's a godsend. When you license your own media under CC, you can choose how you want it to be used by others and whether or not it can be used commercially.

The biggest win in the race for consumer augmented reality smartglasses to date belongs not to Apple, Facebook, or Google, but Snapchat's parent company, Snap.

Snapchat parent company Snap took a huge step towards the realm of smartglasses with the third iteration of its camera-equipped Spectacles sunglasses.

Tossing an old Android smartphone with a decent battery into your hacking kit can let you quickly map hundreds of vulnerable networks in your area just by walking or driving by them. The practice of wardriving uses a Wi-Fi network card and GPS receiver to stealthily discover and record the location and settings of any nearby routers, and your phone allows you to easily discover those with security issues.

In this video series, expert jazz musician Ryan Larson will teach you how to read and play jazz bass in the key of F major. Learn the different scales and techniques in this step by step bass guitar lesson. Improve your ability to groove with other musicians and move freely along the neck of the bass.

In this video series our expert, Brandon Sarkis will show you how to use and customize the lightroom interface, how to use the modules and their control bars, and how to use stacks. He will also show you how to import and export images, how to use keywords, and how to use collections.

In this video series, expert jazz musician Ryan Larson will teach you how to read and play jazz bass in the key of E Major. Learn the different scales and techniques in this step by step bass guitar lesson. Improve your ability to groove with other musicians and move freely along the neck of the bass.

In this video series, expert jazz musician Ryan Larson will teach you how to read and play jazz bass in the key of Eb major. Learn the different scales and techniques in this step by step bass guitar lesson. Improve your ability to groove with other musicians and move freely along the neck of the bass.

Anyone who's worked in web development or graphic design long enough knows that one of the most difficult job elements is finding high-quality stock images that aren't tangled in red tape. Whether you're trying to build a website, ad campaign, or email newsletter, you need to have reliable graphics that are easy to find and use across multiple platforms.

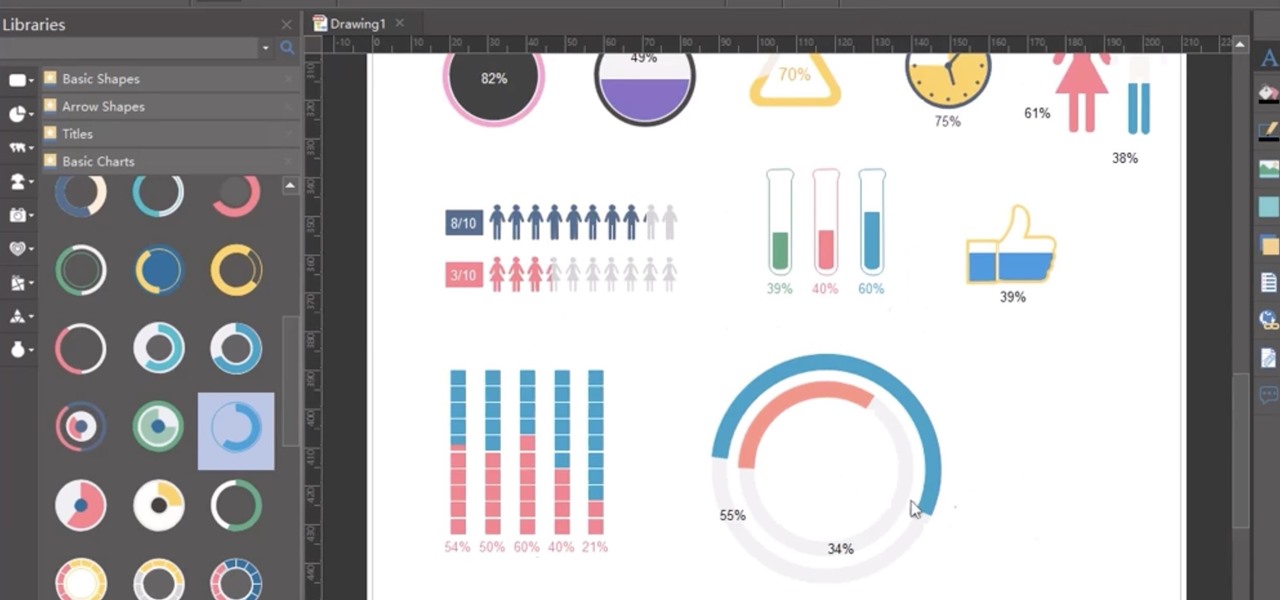
Did you know there is a simple trick to making beautiful, professional charts? Whether for your work or for making running your own business easier, Edraw Project Software will make all your projects simple. Right now, a Perpetual License, which includes three-year upgrades and maintenance, is on sale for almost half off, at just $89.99 — that's a 49% discount off the regular price of $179.

Penetration-testing frameworks can be incredibly useful since they often streamline certain processes and save time by having a lot of tools available in one place. Of course, the most popular pentesting framework is undoubtedly Metasploit, but there are many others out there that cater to particular needs. For auditing web applications and servers, Tishna comes in handy.

With its 3D engine being responsible for approximately 60% of augmented and virtual reality experiences, Unity is continuing to place a premium on tools that not only keep developers working in its development environment but also make their workflows easier.

Current-generation mobile augmented reality apps offer users numerous opportunities to punch up photos and videos with 3D content, but there's surprisingly few options for users to express themselves using virtual characters.

Safari has a convenient "Find" feature to search for specific words and phrases in a webpage, and Apple Books has a similar feature for e-books and PDFs. But those do nothing for you when searching text in the real world. Hardcover and paperback books are still very much a thing, as well as paper-based documents, and finding what you need is as simple as pointing your iPhone's camera at the page.

Having an efficient workflow is an integral part of any craft, but it's especially important when it comes to probing apps for vulnerabilities. While Metasploit is considered the de facto standard when it comes to exploitation, it also contains modules for other activities, such as scanning. Case in point, WMAP, a web application scanner available for use from within the Metasploit framework.

The first few minutes after gaining access to a MacBook are critical — but where do we begin? Using tools built into macOS, we can develop an in-depth understanding of running background processes, detect antivirus software, locate sensitive files, and fingerprint other devices on the network. All of this can be done without installing additional software or modifying any files.

Alright, let's dig into this and get the simple stuff out of the way. We have a journey ahead of us. A rather long journey at that. We will learn topics ranging from creating object filtering systems to help us tell when a new object has come into a scene to building and texturing objects from code.

Google Photos is one of the best photo management services out there. It allows you to back up an unlimited amount of high-quality images without ever paying a dime, the photos and videos sync flawlessly across all of your devices, and its neural network-powered visual search feature seems like something that was pulled directly out of a Sci-Fi movie.

As Android's official app provider, the Google Play Store is packed with thousands of useful programs. But Google's terms of service is extremely restrictive, which means that countless apps simply don't qualify to be hosted on the Google Play Store.

You might be familiar with the use of zucchini blossoms in cooking and maybe even know how to make herbal simple syrups. But if you really want to show off as someone who knows how to use flowering plants in food, try adding some flower water to your cooking/baking repertoire.

In this article, we will build a parallel password cracker using the techniques explained in the previous part. As SHA-512 is the digest function that Kali (and most modern Linux distributions) use to store our passwords, we will make a SHA-512 password cracker.

Welcome back, my nascent hackers! Although my favorite TV show, Mr. Robot, had completed its first season already, I have not completed demonstrating the hacks that Elliot used in the show. (By the way, I can't wait for season 2!)

If you're one who enjoys a good DIY project, or if you're just tired of paying exorbitant labor fees to have your vehicle serviced every 5,000 miles, changing your own oil can be a rewarding endeavor. Even though cars and trucks are becoming increasingly over-engineered these days, manufacturers generally see to it that the basic maintenance items can still be taken care of in your driveway with a few common tools.

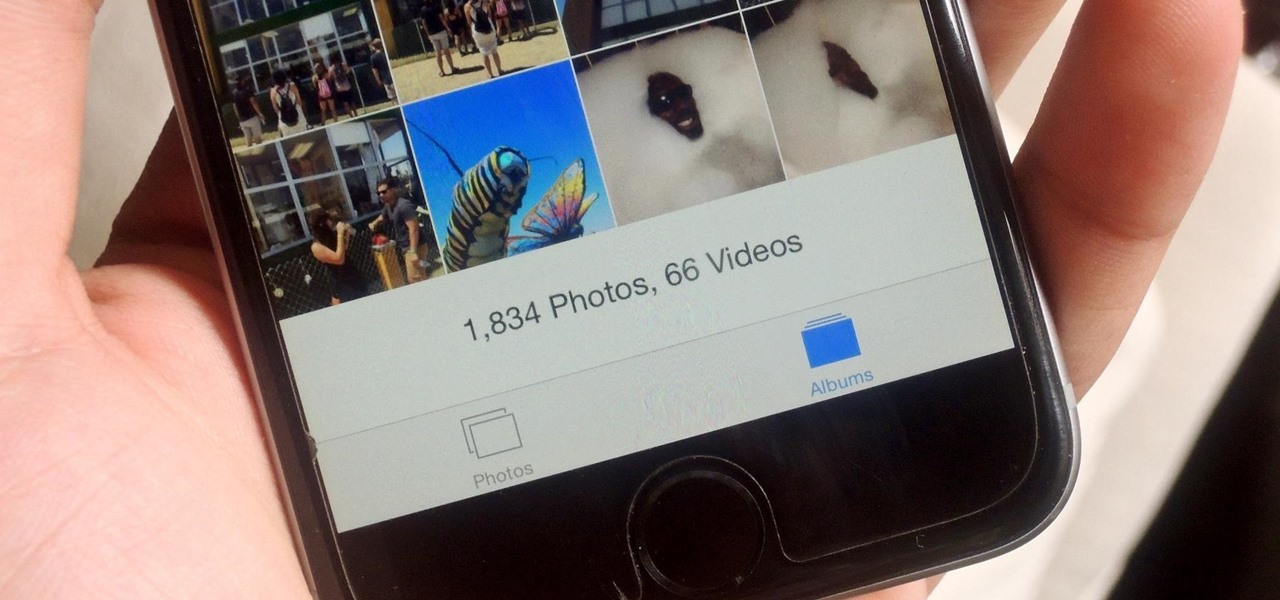
If you have a ton of photos and videos on your iPhone, backing up to iCloud is probably a no-go since it only provides 5 GB of free storage. Yes, you can buy more storage, but who wants to do that? And what happens if you run out of storage, stop backing up, and your phone gets lost, stolen, or damaged.

Everyone has the same five spirits in their bar: vodka, rum, whiskey, tequila, and gin. They're all great, but every so often the mood strikes to try a cocktail with a little something different. We'd like you to meet three spirits from South America that would make a welcome addition to your next cocktail party.

Your iPhone's home screen is a tricky thing. You can sort your collection of apps in any order you'd like, but where you place those apps is a totally different story. App and folder placement follows a strict grid on iOS from left to right, top to bottom. No exceptions, and that's how Apple wants it. So you might think without a jailbreak you're stuck with this layout — but you're wrong.

Voicemails are like chores for me. I have to listen to them, but never really feel like doing it. When I finally do, most of them get deleted right away, but every so often they'll be one I save and listen to over and over again, whether it's a cute birthday wish from grandma or a hilarious joke from my friend.

Welcome back, my budding hackers! As you know, I firmly believe that to be a true professional hacker, you need to be proficient in Linux. This is for a number of good reasons.

Welcome back, my budding hackers! Previous to this tutorial, we've focused mostly on hacking the target system. If we're successful in owning the target system, we'll then want to make certain that the system administrator doesn't know we were there, and that he or she cannot track us.

In the UK, 20 percent of divorce filings include the word "Facebook." You may think you're being slick by using the site to chat with your ex, but the problem is that Facebook saves everything, and I mean everything. All someone needs is your login information and they have access to everything you've ever said on Facebook, public or private.