Now that Google+ is open to everyone, there are a lot of new people who aren't techies trying out the service. When you first sign on, it can be overwhelming. I've decided to round up a bunch of resources to help you get started, and recommend some people for you to follow, if you want to stay on top of tips and new announcements.

Difficulty Level: If you have eyes, you can do this.

MyShoppingGenie is an online shopping application that can help you find the best deals on products you search for.

The deep side part is a classic technique and in this video we'll show you three different ways to quickly and easily style it for beautiful looks. Find and Set Your Side Part

Back in the eighties, I used to hate television commercials, but I eventually got used to them. Had to, in order to enjoy my favorite shows. Then, the increasing number of billboard ads annoyed me in the nineties. They followed me everywhere I went—no escape—persuading me to buy the newest whatever. It seemed like Big Brotherism—like They Live. But, I got used to it. When I finally entered the digital age and became a web addict, I was peeved at the constant sight of online ads everywhere I v...

Choosing a nanny or au pair for your children is a process that should be organized and performed carefully, to ensure you find someone who can be trusted, will contribute significantly to the development of your child and integrate well into your family.

TOP MOVIES 2011 The Artist (2011)

This week's FIGRR is all about games that are old-new (or new-old, if you like) school. Each celebrates a different vital, yet largely taken for granted, aspect of video game history in the decidedly new-school world of indie games. Their titles betray them. Blocks That Matter is all about blocks. Recettear: An Item Shop's Tale is all about item shops. Neither are particularly sexy aspects of gaming, but both are ubiquitous elements of great games that can stand on their own.

House Café offers traditional American food with a heavy Mexican influence. The restaurant is located near Crescent Heights and Beverly Blvd, sandwiched between The Grove and The Beverly Hills Mall. We’ve (wife and I) visited this restaurant several times, here are our impressions of our most recent visit.

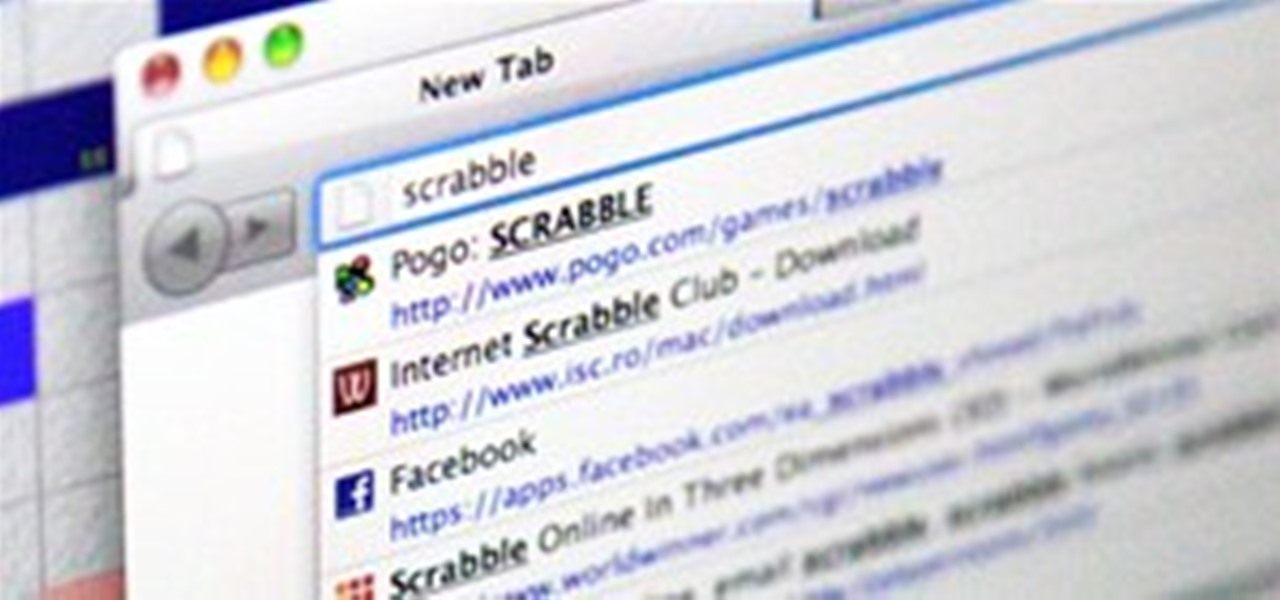
There's nothing better than playing a game of Scrabble, feeling the smooth wooden tiles in your hand and savoring the heavy fumes of cardboard, cheap wood and plastic as you rearrange the letters on your rack into the perfect word. You try to keep a straight face while you watch your opponent sweat, but you can't help but release that diabolical grin of self-admiration as you play the elusive triple-triple. The score's recorded and you feel sorry for your bitter rival, but then you remember y...

This is a prank on the public by the Jackass guys, not a prank on the Jackass guys. This would take a bit of planning and pre-production but could be pretty funny. Start skit a par 5 golf hole, preferably one with a dogleg so you can't see the green from the tee box where an unsuspecting 4-some comes up to tee off. Right in the middle of one of their swings, a hearse cruises by them on the cart path and goes down the fairway. The players will obviously be take aback and wonder what the hell i...

You're sitting in front of your grandmother's Windows XP machine that has the worst infection you've ever seen. Safe mode? No dice. Restore points? They're compromised. Even worse, all of the files are hidden and none of the executables will run! This leaves her computer in a bricked state. Without some serious CPR, it will be lost to you. Sure, you could just reinstall the system, but then you might lose all of that valuable data.

Remember that scene in The Matrix when Trinity uses a realistic Nmap port scan, followed by an actual SSH exploit (long since patched) to break into a power company? Well, believe it or not, but that scene is not far fetched at all. If you want to exploit vulnerabilities and root boxes, you'll need to learn how to perform the necessary reconnaissance first. In fact, you will spend far more time researching your target then you will exploiting it. In this article, I am going to show you the fi...

Culinary collective Studiofeast is known for thinking outside the box, especially when it comes to food. They've hosted inventive and spectacular events like the L Train Lunch, where a high-end meal was served to guests on a moving train, and the Datalicious Last Supper, where results from a survey of people's desired "last meals" informed the menu.

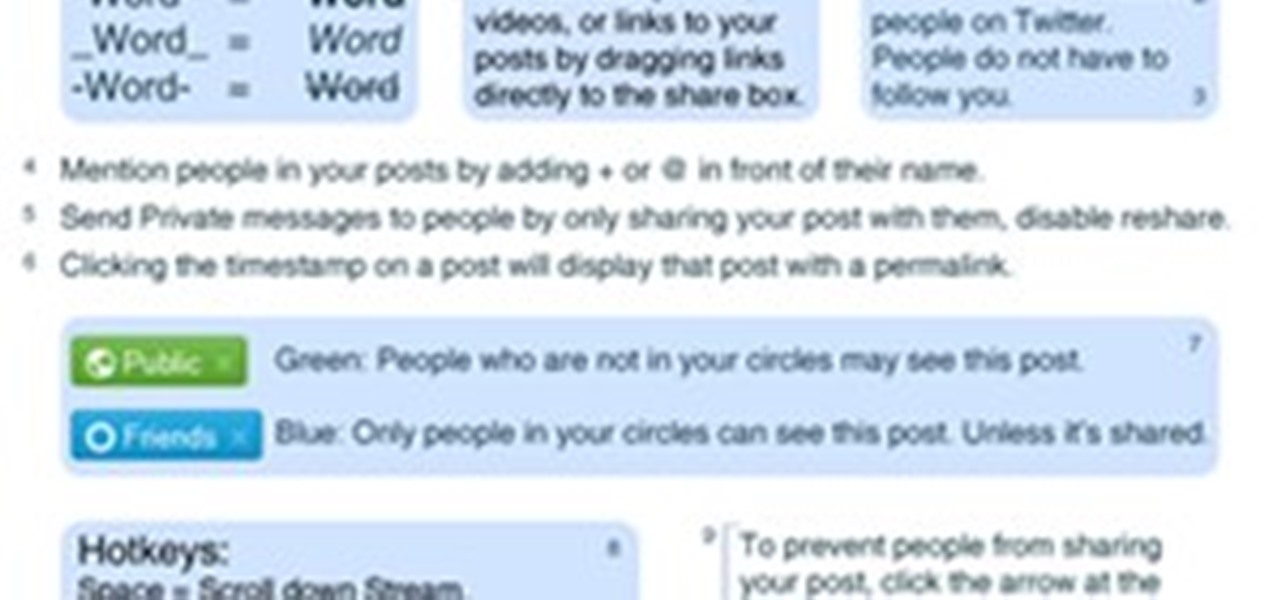
With the Google+ team members being generous and free-flowing with advice on some of the more advanced features of Google+, we'll be publishing a weekly summary of the latest pro tips. Chances are, if you've been following the Google+ team members, you've seen some of these already but you don't have them all in one handy place.

Introduction to the Basics of Off-Camera Flash

RESPECT - What It Means (in the picture above are my parents, both of whom I respect and cherish dearly)

I first heard the term molecular gastronomy while watching an episode of Bravo's Top Chef a few seasons back. Intrigued by the concept, I sought to find out more about this modern, deconstructed type of cookery. If you happen to be around foodies and the topic of molecular gastronomy comes up (which very likely will at some point) you'll want to have a few points to contribute and maybe even give them a run for their money.

Imagine you're in Paris and you need to get to Versailles. Looking around for directions, you come to a cold realization—you do not speak a lick of French! How are you going to get to Versailles and what happens if there is a detour? It will be a difficult struggle, and you'd probably get lost and eventually fail. This is why it's important to know some of the country's language before taking that trip in the first place.

If you're on a tight budget for food, whether you're in college, or someone just starting out living on their own, you're probably low on money and sick of ramen noodles. Don't get me wrong, ramen can be tasty and filling, and there is almost nothing cheaper.

Sometimes an iDevice is best used for idle, pointless fun. Today's segment of Making Art on Your iOS Deviceis a mixed bag of time-wasting cool effects and random, but useful art-making tools. Below, 10 apps for creating anything from erratic hand-shaken digital effects to your very own DIY Andy Warhol prints.

Banksy, Cope2, Invader, Retna, Mr.cartoon, They all have a few things in common. Firstly, they are all extremely talented and well known urban artists. Secondly, they all have very memorable and very, very cool names.

Mark Burnett is, financially speaking, perhaps the most successful television producer today. While I had launched America's Most Wanted and COPS a decade earlier, Mark exploded onto network television with Survivor, the glossy and fantastical innovation to reality television. With Survivor now entering its 11th year, I recently interviewed Mark at the Los Angeles public radio station KCRW, where the podcast will be made available. Below, Mark's 10 steps from soldier-to-nanny-to-premiere-Holl...

What happened to please and thank you? When did asking someone to come look at your build degenerate into COME NOW or FOLLOW or sending out teleport requests to any and all currently on the server without asking?

No doubt you've seen some of the hack logs being released. One part that stands out over and over again is the heavy database usage. It used to be early on that virus and hackers would destroy data, usually just for lulz. However, with the explosive commercial growth of the Internet, the real target is turning into data theft. You should learn how this happens so you can protect yourself accordingly. Let's take a look at what makes this possible and dare I say, easy.

Over the past couple of weeks, there have been a series of high-profile hacks and leaks. From the rooting of CombinedSystems, to a secret FBI conference call leak, all the way to the distributed denial-of-service (DDoS) attacks on U.S. government sites—with a lot in-between. As governments move to close their long fingers around the free speech that exposes their secrets, this shadowy collective of loose-knit, but like-minded individuals are hell bent on preventing them. Or are they?

ACTION MOVIES The Hunger Games (2012)

No matter what word game you're playing, whether it's Scrabble or one of its near-homogeneous counterparts like Lexulous, Wordfeud or Words with Friends, one of the easiest ways to stay on top of your opponent is knowing all of the legal two-letter words you can play. You're not going to win by only playing two-letter words, but there are definitely occasions when the game could slip from your hands by not playing them.

Via WonderHowTo World, SCRABBLE: Dirty SCRABBLE. Everybody likes to play dirty, but we're not talking bluffing with fake words or closing up the board—we're talking actual "dirty" and offensive words.

Dirty SCRABBLE. Everybody likes to play dirty, but we're not talking bluffing with fake words or closing up the board—we're talking actual "dirty" and offensive words.
International Pet Travel: Taking Your Pet Animal to a Foreign Country If you are taking a pet to another country (permanently or for a visit), contact that country's consulate or embassy for information about any requirements that you must meet. A list of consulates can be found at Foreign Consular Offices in the United States