As excitement looms for Apple's annual parade of pomp and circumstance for its latest lineup of iPhones, some hidden hints in an internal build of iOS 13 has Apple enthusiasts salivating for what Cupertino is testing in the AR wearables realm.

Long before the HoloLens or the Magic Leap One, a California-based team of independent filmmakers envisioned what the future of augmented reality might look like.

Update February 25: The new Sony Xperia flagship has been announced, and it has a new name: The Sony Xperia 1. You can read all of the official specs and details at our full article on Sony's new model.

Last week, Twilio showed off how avatar-based chat communications will work on the Magic Leap One, and now a new startup has unveiled yet another way that augmented reality telepresence and remote collaboration can take place on the device.

This week, we continued our NR30 series highlighting the leaders of augmented reality space by profiling the venture capitalists and strategic corporate investors that sustain the industry.

This week, Next Reality published profiles on the leaders in augmented reality hardware industry, with Magic Leap CEO Rony Abovitz topping the list. So, it should be no surprise that two app makers want to align themselves with Magic Leap's flagship product.

This week, we're beginning to see the wide ranging impacts of some of the early iterations of augmented reality hardware and software.

Magic Leap's recent flurry of patent applications prompted us to look around for any trademark movements from the company, and it turns out that the Florida-based company has been quite busy.

Unscheduled pit stops go hand in hand with road trips, no matter how well-planned they are. In the past, making a stop due to low fuel or an emergency bathroom break may have snowballed into massive delays when you went off course on your own, but thanks to a feature in Apple Maps, you can do this in the most efficient manner possible.

When a firm like Techstars believes that augmented reality is an attractive industry to invest in, there's a high probability that it's right.

A new study casts real suspicion on the possibility of life on Mars. Why? It seems the surface of the planet may be downright uninhabitable for microbial life as we know it.

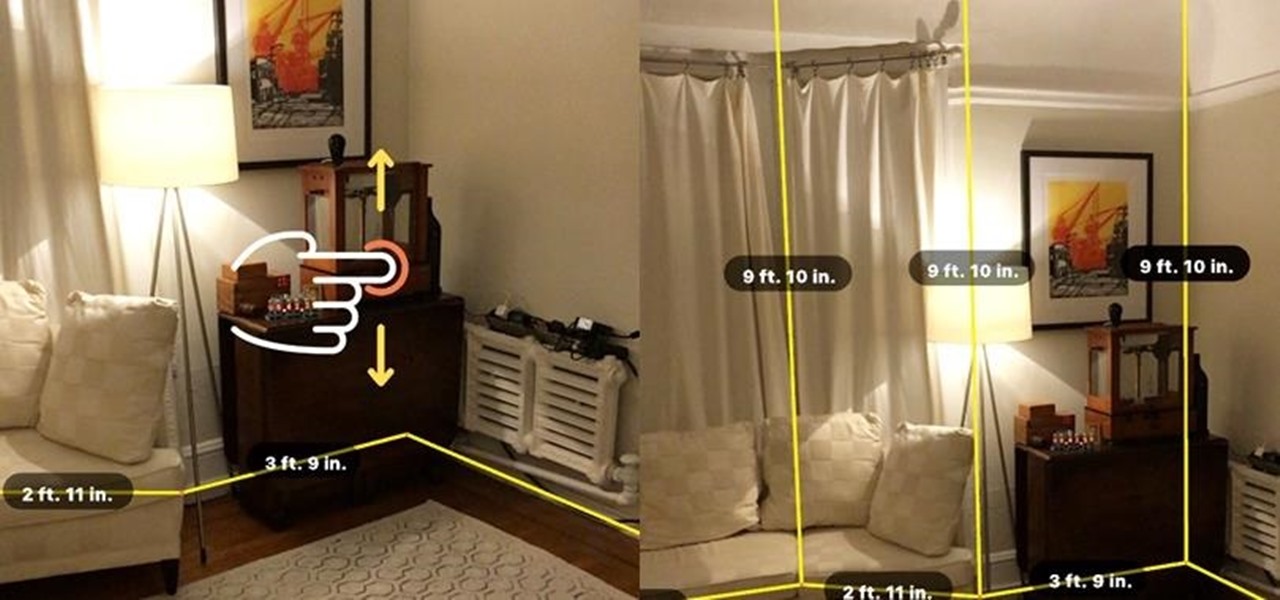
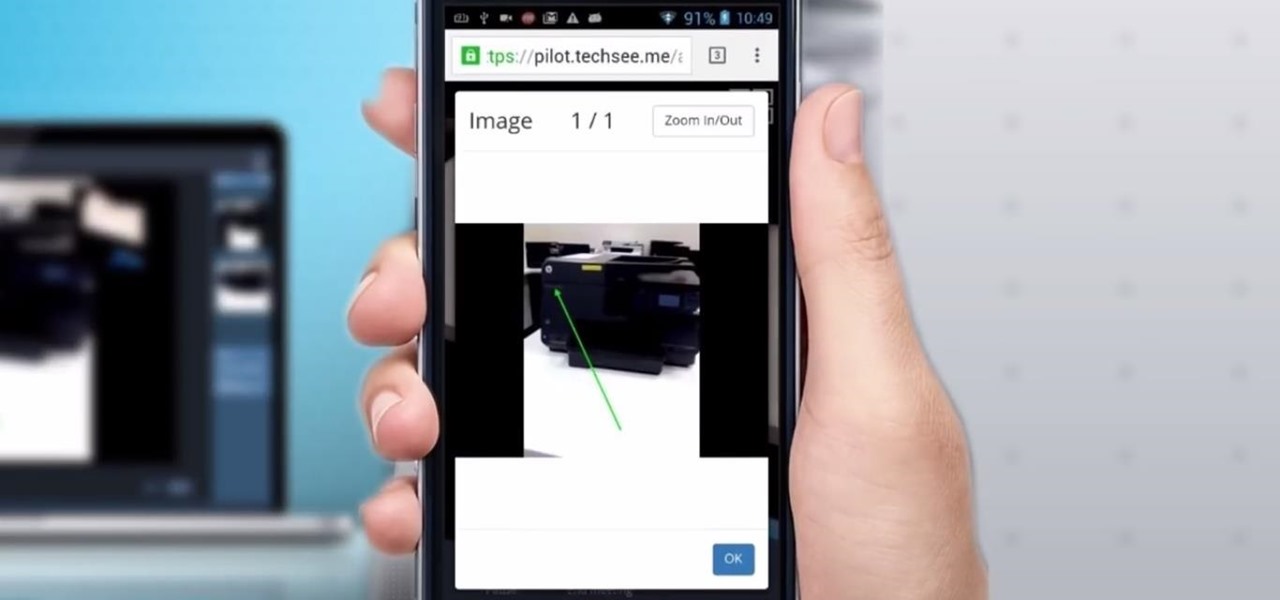
Four augmented reality companies made deals this week to grow their businesses. Two companies, TechSee and Car360, completed funding rounds, while DAQRI signed with a production partner and Decalomania landed a prime spot with a top retailer.

On October 17, 1943, a story in the New York Herald Tribune read "Many laymen — husbands, wives, parents, brothers, sisters, friends — beg Dr. Keefer for penicillin," according to the American Chemical Society. Dr. Chester Keefer of Boston was responsible for rationing the new miracle drug, penicillin.

Our quest to find new antibiotics has taken a turn — a turn down the road, that is. A team of scientists from the University of Oklahoma is scooping up roadkill and searching for bacteria on them that might yield the world's next antibiotic.

In the ongoing search to find better ways to use antibiotics, an extract made from maple syrup has some surprisingly important medical benefits.

Bitcoin, the decentralized cryptocurrency notorious for its status as the currency of the dark web, seems to be shedding its shady past and is now enjoying soaring highs not seen since 2014. The highly volatile online commodity reached parity with an ounce of gold back in March amid speculation of a pending ETF approval from the Federal Trade Commission. Since then, Bitcoin has doubled in value and analysts predict a bitcoin could reach $100,000 in value in 10 years.

Scientists are constantly on the search for new organisms, species, and other types of life. A special group of these researchers, calling themselves "bioprospectors," dive deep into mines to find unique lifeforms with special properties not found anywhere else.

Specialized cells in the lining of the gut may provide a key to preventing an infectious brain disease caused by misfolded proteins.

From our work life to our home life, we have an awful lot of projects, tasks, and activities that require more productivity than play. After working for an entire day in the office, no one wants to face even more that needs to be done at home.

As a lover of food, I'm often asked, “If you could only have one food the rest of your life, what would it be?” My answer is always the same: sourdough bread. (Okay, it's not always the same... I usually cheat and say sourdough, fancy cheese, and a good beer.) Admittedly, I'm biased by my own sentimentality. My mother is an expert bread baker, with a major in making sourdough. Her sourdough starter is older than I am, and in all honesty, she's made thousands of loaves, each better than the ne...

Humans in general are great at keeping things about themselves private, from feelings to personality traits. While smartphones and social networks are making these secrets more open, narcissists have and always will love being out in the open with everyone's attention on them.

The big fireworks day is almost here, but most of you are limited in what you can do when it comes to celebrating the Fourth of July with a bang. Unless you live in a dry area prone to wildfires, one type of fireworks you can probably still legally buy are sparklers.

When the 6.1 version of iOS was released back in February, complaints of severe battery drainage for iPhone, iPad, and iPod touch users exploded onto every Apple-related forum on the Internet. Everyone was either losing a percentage every three or so minutes, or their battery only lasted half as long as it did before the update. Earlier this month, Apple released iOS version 6.1.3, to supposedly fix a recent exploit that allowed anyone to bypass the lock screen—but as it turns out, the update...

Ralph Waldo Emerson once observed that "the seed of science" was "wonder," and taking a look at this nine-layer liquid tower from Steve Spangler's Sick Science! channel, one can't help but do just that — wonder. How is this possible? Is this magic or what?

In this how to video series, learn how to use a chainsaw and how to maintain a chainsaw from chainsaw expert George Finn. George will show you how to safely use a chainsaw, what type of safety gear to use, how to disconnect a chainsaw sparkplug, how to tighten the chain on a chainsaw, how to mix gas and oil for chainsaw fuel, how to add gas and bar & chain oil to a chainsaw, how to sharpen a chainsaw chain, how to replace the chain on a chainsaw, how to start a chainsaw, how to replace the ai...

Are you having trouble balancing the cutting deck of your small engine lawnmower? Our expert will teach you how to do this and many other things including careful removal of the engine’s cutting blade. You will also see how to sharpen the blade and reinstall it safely and efficiently. Watch as our lawnmower maintenance expert removes and reinstalls a carburetor on a small engine lawnmower. Learn how cleaning the carburetor can improve the working mechanism of your lawnmower and see first hand...

Post-exploitation is often not quite as exciting as popping the initial shell, but it's a crucial phase for gathering data and further privilege escalation. Once a target is compromised, there's a lot of information to find and sift through. Luckily, there are tools available that can make the process easy. One such tool is Postenum.

People use browsers for all types of things, and in general, we trust a lot of personal information to them. That's why browsers are a perfect attack surface for a hacker, because the target may not even know they are infected and feed you all of the information you could want.

File permissions can get tricky on Linux and can be a valuable avenue of attack during privilege escalation if things aren't configured correctly. SUID binaries can often be an easy path to root, but sifting through all of the defaults can be a massive waste of time. Luckily, there's a simple script that can sort things out for us.

Wi-Fi networks come in two flavors: the more common 2.4 GHz used by most routers and IoT devices, and the 5 GHz one offered as an alternative by newer routers. While it can be frustrating to attack a device that moves out of reach to a 5 GHz Wi-Fi network, we can use an Alfa dual-band adapter to hack Wi-Fi devices on either type of network.

A lot of time can be wasted performing trivial tasks over and over again, and it's especially true when it comes to hacking and penetration testing. Trying different shells to own a target, and testing out privilege escalation commands afterward, can eat up a lot of time. Fortunately, there is a tool called One-Lin3r that can quickly generate shells, privesc commands, and more.

The USB Rubber Ducky and the Digispark board both suffer from the same issue when attacking macOS computers: a keyboard profiler pop-up which tries to identify any non-Apple USB keyboards. While it's an annoying setback, the solution is a simple modification that allows Mac computers to be targeted, which affects the ability to target Windows and Linux devices.

The Windows 10 desktop and microphone can be livestreamed without using Remote Desktop Protocol (RDP) software and without opening any ports on the target computer. A hacker with low user privileges can monitor and exfiltrate a target's every move and private conversation in real time no matter where they are. Hackers are watching and listening, and there are few ways to protect yourself.

The ability to stay organized and be resourceful with data gathered from recon is one of the things that separates the true hackers from the script kiddies. Metasploit contains a built-in database that allows for efficient storage of information and the ability to utilize that information to better understand the target, which ultimately leads to more successful exploitation.

If you've grown bored of day-to-day hacking and need a new toy to experiment with, we've compiled a list of gadgets to help you take password cracking and wireless hacking to the next level. If you're not a white hat or pentester yourself but have one to shop for, whether for a birthday, Christmas present, or other gift-giving reason, these also make great gift ideas.

It is almost indisputable that smartglasses and head-worn displays are the future of augmented reality. However, at this precise moment, they are still a very niche market.

The misconception that macOS is more secure than the Windows operating system is far from the truth. With just one small command, a hacker can completely take over a MacBook and control it remotely.

Design flaws in many routers can allow hackers to steal Wi-Fi credentials, even if WPA or WPA2 encryption is used with a strong password. While this tactic used to take up to 8 hours, the newer WPS Pixie-Dust attack can crack networks in seconds. To do this, a modern wireless attack framework called Airgeddon is used to find vulnerable networks, and then Bully is used to crack them.

Hak5's products get a lot of attention. Popping up in popular shows like Mr. Robot, their hacking tools are bold proof of concepts with space built into the design for the community to add their own tweaks and modifications. On Friday, Oct. 27, Null Byte attended the Hak5 release event in San Francisco to check out their latest devices, including the new Packet Squirrel.

Some of us woke up at the KRACK of dawn to begin reading about the latest serious vulnerability that impacts the vast majority of users on Wi-Fi. If you weren't one of those early readers, I'm talking about the Key Reinstallation Attack, which affects nearly all Wi-Fi devices.