While the security behind WEP networks was broken in 2005, modern tools have made cracking them incredibly simple. In densely populated areas, WEP networks can be found in surprising and important places to this day, and they can be cracked in a matter of minutes. We'll show you how a hacker would do so and explain why they should be careful to avoid hacking into a honeypot.

JavaScript is one of the most common languages used on the web. It can automate and animate website components, manage website content, and carry out many other useful functions from within a webpage. The scripting language also has many functions which can be used for malicious purposes, including stealing a user's cookies containing passwords and other information.

Hello partners, first of all I would like to thank all those who have sent me positive feedback about my posts, to say that I'm always willing to learn and teach. I'm also open to answer the appropriate questions.

Welcome back, my tenderfoot hackers! As you know, Metasploit is an exploitation framework that every hacker should be knowledgeable of and skilled at. It is one of my favorite hacking tools available.

Welcome back, my budding hackers. So many of you are interested in hacking Wi-Fi that I have decided to revisit my Wi-Fi Hacking series with some updated and more in-depth material. I strongly suggest that you look at some of my earlier posts, such as "Getting Started with Terms and Technologies" and "Getting Started with the Aircrack-ng Suite of Wi-Fi Hacking Tools," before continuing here. If you're ready, you can also check out our updated 2017 buying guide here.

RC Car Action Magazine Editor Kevin shows you how to stop a nitro engine. Just bump the flywheel with a screwdriver or pinch the fuel line. Watch this video tutorial and learn how to stop a nitro engine on an RC vehicle.

Three hundred people die every year from carbon monoxide poisoning. Don't risk being a part of that statistic.

With all the web applications out on the internet today, and especially the ones built and configured by novices, it's easy to find vulnerabilities. Some are more perilous than others, but the consequences of even the slightest breach can be tremendous in the hands of a skilled hacker. Directory traversal is a relatively simple attack but can be used to expose sensitive information on a server.

After years of telling patients to finish any prescribed course of antibiotics completely, a group of researchers in the UK say it is no longer necessary, and could even be harmful if we want to preserve the antibiotics we can still use.

Cancer cells do a pretty good job of flying under the radar of our immune system. They don't raise the alarm bells signaling they are a foreign invader the way viruses do. That might be something scientists can change, though.

Welcome back, my hacker novitiates! There are many ways to hack databases, and most of these techniques require SQL injection (SQLi), which is a way of sending SQL commands back to the database from a web form or other input. In this tutorial, we will use SQL injection to get access to the underlying server. So instead of getting access to the database and its data, we will use the database as an intermediary to gain access to the underlying server.

Low battery – two words you never want to hear. Banish them with these tips. You Will Need

Check out this instructional RV video that shows you how to maintain your RV tires. On the front tire of your motor home, make sure that they are maintained properly because if you do lose a tire while driving you can very easily lose control of the vehicle. The first thing that you want to check is the tire pressure. Just remove the cap and check the pressure with your tire pressure gauge. The pressure that is needed on your tire will be listed on the actual tire. If it reads cold that means...

One can easily get rid of acne scars without surgery by means of following steps. Identify the type of acne scars you have. See a dermatologist who can tell the difference between types of scars. For example, scars may be classified as ice pick, boxing, rolling or hypertrophy scars. Not every nonsurgical removal techniques will work with each type of scar. Get a chemical peel. A solution is applied to the skin which causes the top layer to peel off. This encourages new skin growth. Peels are ...

In this video tutorial, you'll learn how to install an Airaid Poweraid throttle body spacer on a 5.3L 2006 Chevy Z71 Crew Cab truck to improve its engine power–when combined with a complete Airaid intake system, one can see up to 25-horsepower gains–as well as yield slight improvements in fuel economy. For exhaustive, step-by-step instructions on installing the Airaid throttle body spacer on your car or truck, watch this how-to.

Zippo not lighting up anymore? Unlike other lighters, you don't need to throw it away; just refill it. Add some butane fuel, and it will start working again. Watch this how-to video and learn how to refill a Zippo lighter.

Keep your wood-burning fireplace well-fueled this winter. Northern Alberta Institute of Technology Forest Technology instructor Alan Pollock shows you how to cut wood and make kindling. Watch this video and learn to chop your own timber.

Check out this video to see how to make the world's smallest fuel-free rocket that can fly 12 feet. Make it with just an empty bottle.

This video shows how to throw a Hawaiian pig roast. Remember, the most important part is to drink while you prep the pig and build the fire. Just do not burn yourself or undercook it. The longer you leave it in the ground, the better it is.

Smartglasses are the future of augmented reality, and Samsung is betting on waveguide maker DigiLens to emerge as a leader in the growing AR wearable industry.

One of the most popular mobile games out there for kids has added an augmented reality mode that brings the titular character into the real world.

A weak password is one that is short, common, or easy to guess. Equally bad are secure but reused passwords that have been lost by negligent third-party companies like Equifax and Yahoo. Today, we will use Airgeddon, a wireless auditing framework, to show how anyone can crack bad passwords for WPA and WPA2 wireless networks in minutes or seconds with only a computer and network adapter.

Most of us have conducted an investigatory science project without even knowing it, or at least without knowing that's what it was called. Most science experiments performed, from elementary to high school students and all the way up to professional scientists, are investigatory projects.

Welcome back my social engineers/hackarians! Today we'll be looking into a fantastic piece of software, The Social-Engineer Toolkit or just SET for short. SET is designed, Developed and used by several Social-engineers. So... Let's get started!

Do you guys remember those things you hold with your fingers to write stuff down? I think they're called pens, or something like that...

Backpacks are handy for camping, hiking, school and travel, but they can be difficult to pack properly. In this tutorial, learn how to pack your bag so that its light and efficient.

After achieving viral and financial success with its Gender Swap and Baby Face camera filters, Snapchat has returned with the augmented reality equivalent of Benjamin Button.

Pokémon, Google, and augmented reality go together like wasabi, soy, and ginger, and the trio has come together again for the release of the latest game from the Pokémon universe.

Augmented reality enthusiasts who expected an AR hardware unveiling at Apple's annual iPhone launch event might not have to wait much longer.

Just weeks after revealing plans to port one of its most vital augmented reality products from HoloLens to the smartphone world, Microsoft has finally opened the mobile software floodgates to the public.

Four months after unveiling the latest productivity apps for the HoloLens, Microsoft now has a series of compelling real-world use case videos showing how the augmented reality device and its apps are helping oil giant Chevron.

New York-based startup CTRL-Labs has closed a $28 million Series A round of funding from Google parent Alphabet's GV and Amazon's Alexa Fund, among others, for its next-generation neural interface technology for AR/VR and robotics.

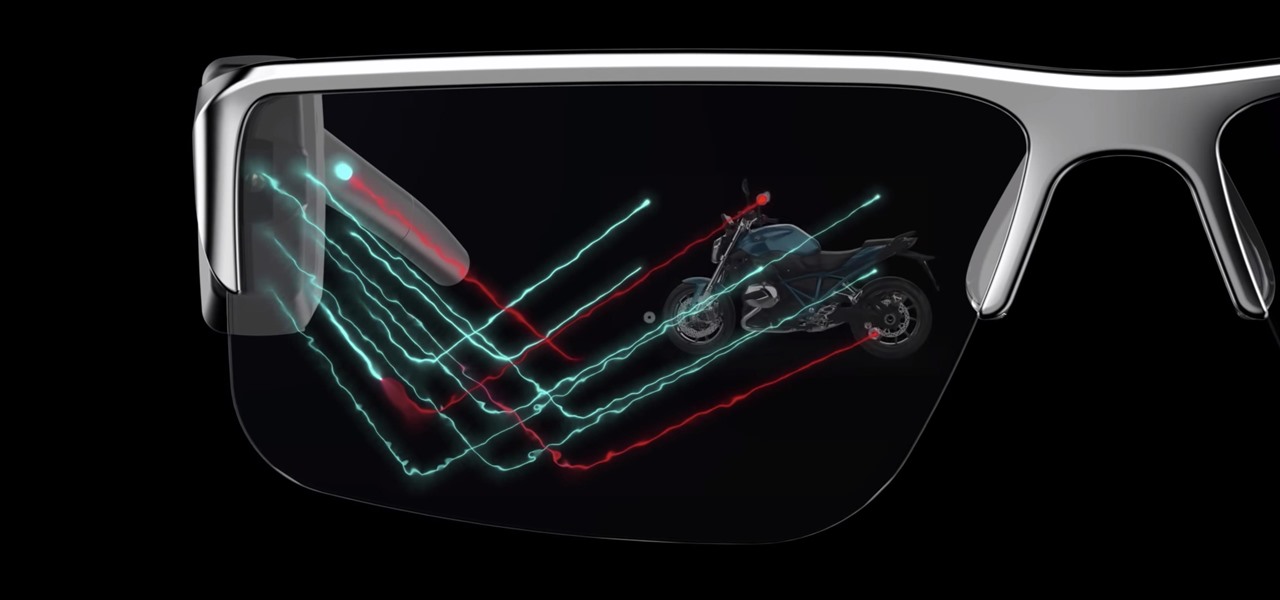
Less than a week after securing a $25 million Series C funding round for automotive HUDs, DigiLens has introduced a new waveguide display for motorcycle helmets that's thinner, lighter, brighter, and manufactured at a lower cost.

During Snap Inc.'s quarterly earnings report, released on Tuesday, the company disclosed that it snagged a revenue total of $230.8 million for the first quarter of 2018, an increase of 54% compared to last year, largely fueled by its augmented reality offerings and other advertising products.

One of the earliest players in the social virtual reality space, vTime, has just landed $7.6 million in new funding, which the company says is partially earmarked for developing and releasing an augmented reality version of its platform later this year.

Although the HoloLens is still primarily the domain of developers and researchers, the device is nevertheless on the cutting edge of showing us what will be possible with augmented reality in the coming years. The latest example comes via Microsoft Japan and a new concept video that shows off how the HoloLens will be used in the relatively near future to pilot autonomous ships.

Update: Monday, 11 p.m. ET: In a report from Bloomberg, eMagin CEO Jeffrey Lucas has contradicted what appeared to be investor information found in SEC filings that surfaced on Monday. Although Apple is listed among several other investors in the company in filing, Lucas told Bloomberg that Apple is not, in fact, an investor in the company. Offering further clarification, Lucas told the news site that eMagin "listed those companies in the filing because it had discussions with them at industr...

Just days after we found out that Apple is working on its own augmented reality headset, we now learn that the company is accelerating its AR headset efforts with the acquisition of Montreal-based hardware maker Vrvana.

Like gas on an open flame, rumors and whispers have flared up in recent months around hopes of augmented reality smartglasses from Apple. But among all the false leads and unsubstantiated chatter, we finally have a credible report that some sort of Apple AR smartglasses are actually in development.

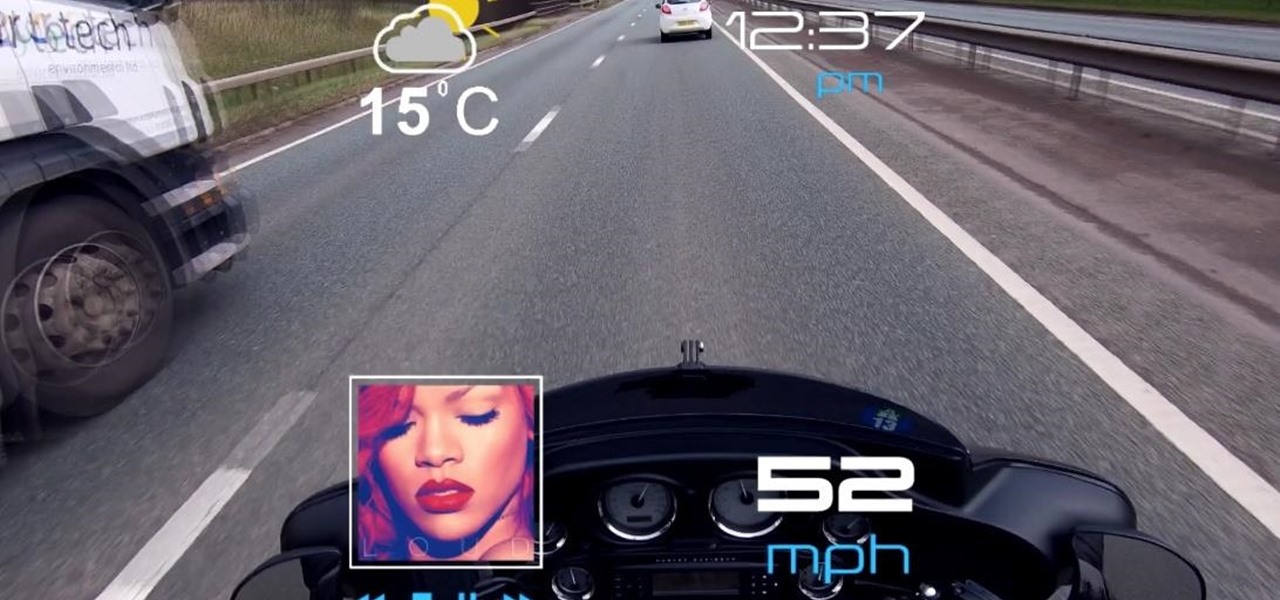
When it comes to augmented reality smartglasses, for now, it's still a mostly enterprise world, since the form and function of most are more acceptable on a job site versus your local cafe, and the still high price tags are far more palatable to major companies rather than individuals.