Smartglass maker ThirdEye Gen, Inc. has introduced an augmented reality solution for enterprises that includes their X1 Smartglass and a suite of software applications that enable completely hands-free computing.
Apple has sprung a massive AR following since the announcement of their ARKit, with users waiting to see what exactly the tech giant will do next.
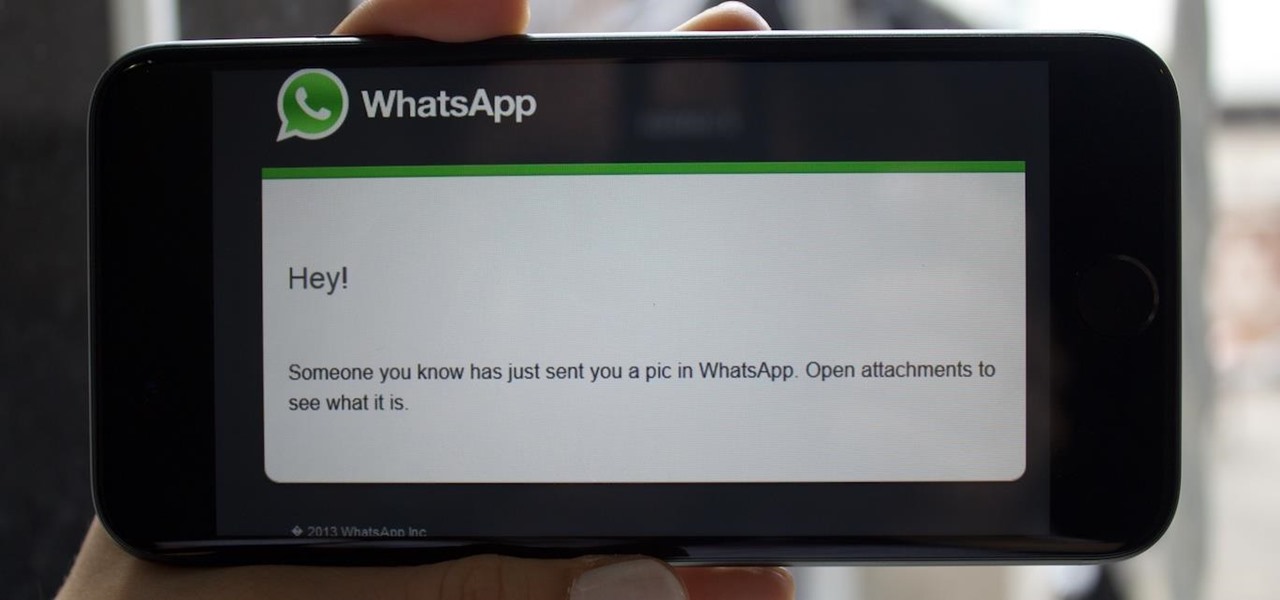
If you ever get asked to update your WhatsApp to your favorite color, don't. It's probably spam. According to Reddit user Yuexist, a new WhatsApp adware is going around disguised as an update.

It seems nowadays there's no limit to what type of companies are looking to invest in augmented reality. Given both the positive outlook on the future of AR, and its reported benefits for efficiency in employees, this makes sense. Safran, an international corporation with three main sectors—aerospace, defense, and security—is one such company taking the plunge into incorporating AR in their business.

Amazon has been toying with the idea of opening physical retail stores for some time now, even opening old-fashioned bookstores in select locations and teasing cashier-less convenience stores. But the online retailer has some new ideas in the works, including implementing virtual and augmented reality into retail home stores.

Earlier last week, there were a number of fake five-star WhatsApp reviews to be found on the Google Play Store. Now, Gmail, Chrome, Messenger, and Firefox are all the latest victims to be saturated in five-star spam that wrongly refers to the word "game" in reference to non-game apps.

Apple is combining internal and external talent in an effort to give them in edge in the augmented reality market, though we still don't know what form their foray into alternative realities will actually take.

The 2015 LA Auto Show showcases the best of the auto industry—well, at least according to car companies. Increases in horsepower, better fuel economy, and most importantly—the latest tech—is all on display during the 10-day event in Southern California. Once of my first missions at the show was to figure out who is putting the most care and thought into in-cabin electronics, mainly the ones that guide us around and play our music, affectionately known as "infotainment."

There was one company at the 2015 LA Auto Show that had everyone intrigued. They didn't have a big booth, and they only had one car on display, but they definitely had everyone's attention.

At first glance, the Big Green Egg looks like it was created by Dr. Seuss or some other whimsy-driven being, like Zooey Deschanel. And while this earthenware cooker may look cute, it produces serious results that can rival the best barbecue or grill. In fact, it's got quite a large cult following. Entrepreneur and former Navy serviceman Ed Fisher fell in love with the taste of food cooked in kamodos (traditional domed, covered earthenware vessels in Japan) and began to import them for sale in...

Brought to you by Berocca® Video: .

Collaborating with other people can be a pain, especially if you have to share one device between the entire group. Usually when you're creating a new design or trying to edit a mockup, you end up hunched around a single screen or end up emailing revisions back and forth, which can be difficult when you're short on time.

Remember those horrible, soul-crushing studies from a few years back linking grilled meats with cancer? Unfortunately, they're still true, but scientists have recently found that an unexpected ingredient can curb some of the harmful effects of high-temperature cooking.

You don't need to be a robot to be overly concerned with battery life, especially if we're talking about Terminators, which have nuclear or hydrogen fuel cells that keep them running for years straight. It will be a long time before smartphones get that upgrade, so in the meantime, we have to figure out how to make them last more than a couple hours in a single charge.

Thanks to HTML5 and dedicated video apps, watching your favorite shows, movies, or video clips on your Samsung Galaxy S4 couldn't be easier. However, there are still times when you'll run into a website that requires Flash to play a video or interact with its content. Although its mobile life has been dead on Android for 2 years, Adobe Flash Player still lives on in the desktop world, fueling millions of websites such as YouTube, Vimeo, ESPN, CNN, and more.

If you are wanting to learn how to perform small repairs to your car, then plastic repair is something you need to learn how to do. Cars are using more plastic now than ever before. With car required to increase fuel mileage, I don't see the use of plastic going away.

You may remember this badass wall of flames photo... That's because last month I highlighted a tutorial by photographer Barry Elder that showed how to light paint with fire.

I loved the Gold Rush unit back in third grade. We went up to the American River and panned for gold, and my panning skills balled above all. I got like three tiny pellets. Of course, it was all fool's gold, aka pyrite, but it was still pretty legit. And this was before wearing gold chains was cool—or not.

Here's a survival technique for making a fire with the most basic of resources—assuming you can find two sticks to rub together!

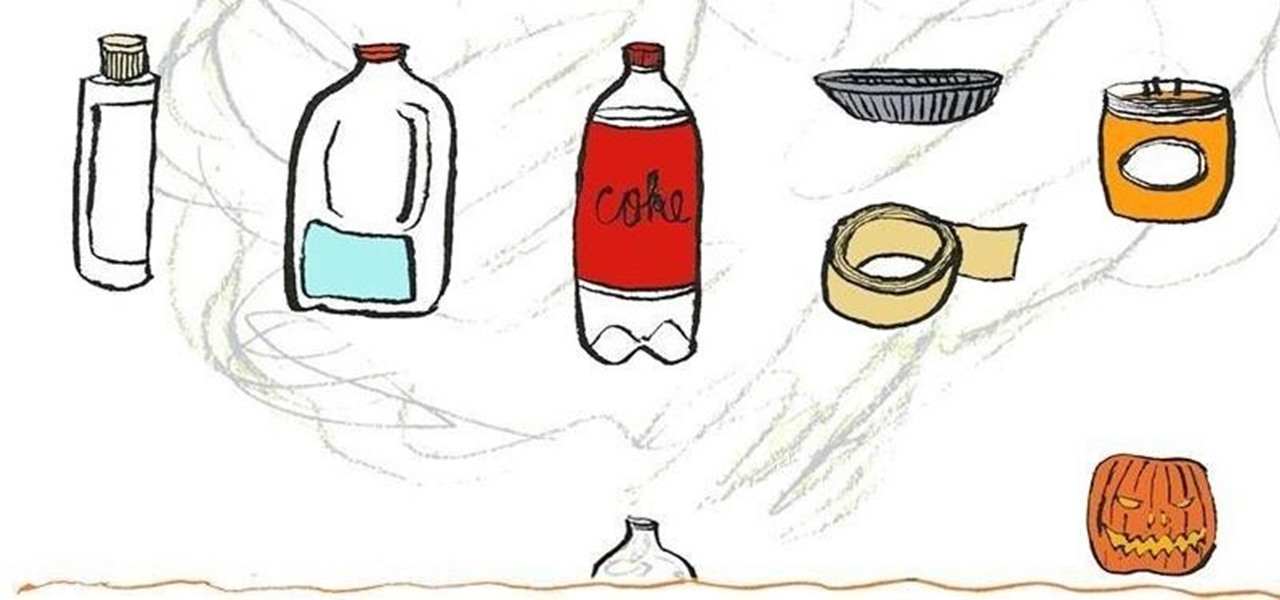
Need to add some spooky ambient fog to your super-scary Halloween party? Rather than shelling out money for a fog machine you'll probably only use once a year, make a trip to the nearest drug store and pick up a bottle of glycerin, a gallon of distilled water, a 2-liter bottle of cola, a disposable mini-pie tin, and a big candle in a jar.

This video will show you how to get rid of stretch mark scars and acne blemishes. Your treatment options depend on the type and severity of your scarring. One way to improve the appearance of a scar is through a collagen injection, given by your dermatologist. Corticosteroids can also be injected to a hypertrophic scar to flatten and soften the raised area. Another technique is laser treatment, which reduces redness and evens out the scar tissue. Skin surgery is used in severe cases to remove...

This video tutorial shows how to hack FarmVille (05/06/10). At this point, it seems like people are more interested in hacking FarmVille than they are in actually playing the thing. This video will teach you how to use Cheat Engine 5.6 to get unlimited tractor fuel, improving your farm's efficiency and increasing your profits. In the game, of course. You'd have to do work to get real money.

In this series of expert videos, you will learn more about lawnmower maintenance. You will learn how to start your lawn mower as well as clean it and keep it free of dirt, rust, and grass clippings. Get tips on changing the oil and air filter on your lawnmower. Learn how to mix two-stroke fuel for your mower. Watch as our expert removes gas, foam filters, and dirty spark plugs from a lawnmower. When changing the blades of your lawnmower, use precautionary measures demonstrated in these videos...

Need a new iPhone app? Check out Comets and Craters, a new iPhone tower defense strategy game. These ten video tutorials cover all of the gameplay troubles you may have. Steve explains the features and gameplay to help you get the most out of playing Comets and Craters on your Apple iPhone. For those more seasoned Tower Defense players, the video's also provide some insight regarding scoring, upgrades, plus Tower and Enemy capabilities.

QR codes are everywhere, from product packaging to airline boarding passes, making the scanners that read them a juicy target for hackers. Thanks to flaws in many of these proprietary scanning devices, it's possible to exploit common vulnerabilities using exploits packed into custom QR codes.

While the USB Rubber Ducky is well known by hackers as a tool for quick in-person keystroke injection attacks, one of the original uses for it was automation. In this guide, I'll be going the latter, explaining how we can use it to automate Wi-Fi handshake harvesting on the Raspberry Pi without using a screen or any other input.

Welcome back, my greenhorn hackers, and happy New Year! Now that your heads have recovered from your New Year's Eve regaling, I'd like to grab your attention for just a moment to preview 2015 here at Null Byte. I hope you will add your comments as to what you would like to see, and I'll try to honor as many requests as I can.

Your brain actually needs to be refueled throughout the day, and our brains function best on carbohydrates. Brain foods like fruits and fish are important for fueling your brain all throughout the day. Learn some tips on eating brain foods and keeping your mind active in this nutrition how-to video.

This truck repair video shows you how to remove the bed from a Chevrolet C1500 W/T truck. This needs to be done to fix certain problems, in this case the fuel lines. Whatever reason you need to remove the bed from your Chevy, this video shows you how to do it properly.

MouseJack vulnerabilities were disclosed over three years ago. Some wireless keyboard manufacturers have since issued firmware updates, but millions (if not billions) of keyboards remain unpatched worldwide, either because they can't be updated or because the manufacturer never bothered to issue one.

With an inconspicuous Android phone and USB flash drive, an attacker can compromise a Windows 10 computer in less than 15 seconds. Once a root shell has been established, long-term persistence to the backdoor can be configured with just two simple commands — all while bypassing antivirus software and Windows Defender.

With the number of web applications out there today, it comes as no surprise that there are just as many vulnerabilities waiting for hackers to discover. Finding those vulnerabilities can be a difficult task, but there are plenty of tools available to make the process easier. While it won't help find any zero-days, web scanners such as Uniscan will detect common vulnerabilities.

Cross-site scripting is one of the most common vulnerabilities found on the web today, with repercussions of this type of flaw ranging from harmless defacement to sensitive data exposure. Probing for XSS can be tedious and time-consuming for an attacker, but luckily there are tools available to make things a little easier, including Burp Suite, Wfuzz, and XSStrike.

One of the most critical bugs to come out in the last five years was Shellshock, a vulnerability which allows attackers to execute arbitrary code via the Unix Bash shell remotely. This vulnerability has been around for a while now, but due to the ubiquity of Unix machines connected to the web, Shellshock is still a very real threat, especially for unpatched systems.

Google Calendar is a cornerstone of the Google Suite, perhaps second only to Gmail itself. Whereas email is constantly plagued by phishing attacks, as of yet, the calendar is a relatively untapped social engineering attack vector. But it's relatively easy for an attacker to inject a meeting or event into a target's Google Calendar and use it to exploit them.

The USB Rubber Ducky comes with two software components, the payload script to be deployed and the firmware which controls how the Ducky behaves and what kind of device it pretends to be. This firmware can be reflashed to allow for custom Ducky behaviors, such as mounting USB mass storage to copy files from any system the Duck is plugged into.

In five short years, three generations of ultra-low-cost Raspberry Pi devices have challenged the boundaries of what a person can do with a $35 computer — especially with Kali Linux.

INTRODUCTION Hello dear null_byters here we go again with our third part of this serie.

Welcome back, my novice hackers! In this third installment of my Hacking Web Apps series, we will look at the authentication of web applications. Remember, there are many ways to hack web applications (as I pointed out in my first article), and cracking authentication is just one method.

Welcome back, my greenhorn hackers! One of the most important issues any hacker must address is how to get past security devices and remain undetected. These can include antivirus software, intrusion detection systems, firewalls, web application firewalls, and numerous others. As nearly all of these devices employ a signature-based detection scheme where they maintain a database of known exploits and payload signatures, the key is to either: