
How To: Make Indian khasta kachori (spicy puffed pastry)
Watch as Manjula prepares for you a delicous spicy puffed pastry, or khasta kachori. For this recipe you will need:


Watch as Manjula prepares for you a delicous spicy puffed pastry, or khasta kachori. For this recipe you will need:

As any informed PopSci reader will know, the iPhone is definitely a game-changing piece of hardware, but it's not without its problems. Chief among those nagging little imperfections, for me, was the recessed headphone hack that rejected any headphones but Apple's trademark gleaming white buds. Apple's 'phones aren't that bad, but my Shure in-ear pair is better for blocking out noise on the subway (and my Grado SR60s are better for listening at home). Thankfully, an easy solution to this prob...

Chilling on the beach and want some grub? If you're starving and can't afford to lose those sun rays walking around for some lunch, have the food come to you instead!
You and I know that everyone's lookin for a killer deal for cellphone service. A lot of us hear about good deals for the plans, or who's got the hottest phones at the moment. Though most of us these days are just looking for something simple, that has all we need, and is fairly cheap too. But how cheap is too cheap?
Outright is an online bookkeing service that tracks the money in and money out of a small business. The basic service is free. Clink the link and explore to see if it is right for you.
This great website has programs for drug and alcohol addiction, child services, inpatient/outpatient services, disorders, etc. Check it out!
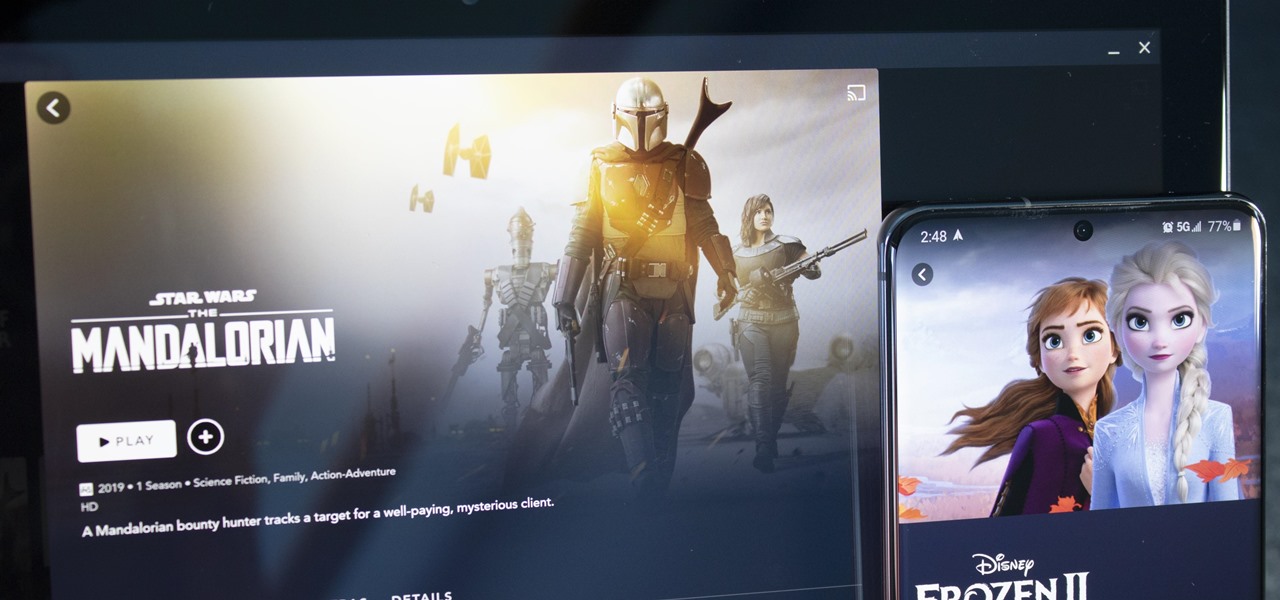
With shows like "The Mandalorian" and movies like "Frozen 2," Disney+ has quickly become a must-have streaming service. However, with Netflix, Amazon Prime Video, and Hulu, adding another subscription-based service can become expensive — but there are ways to trim down the cost.
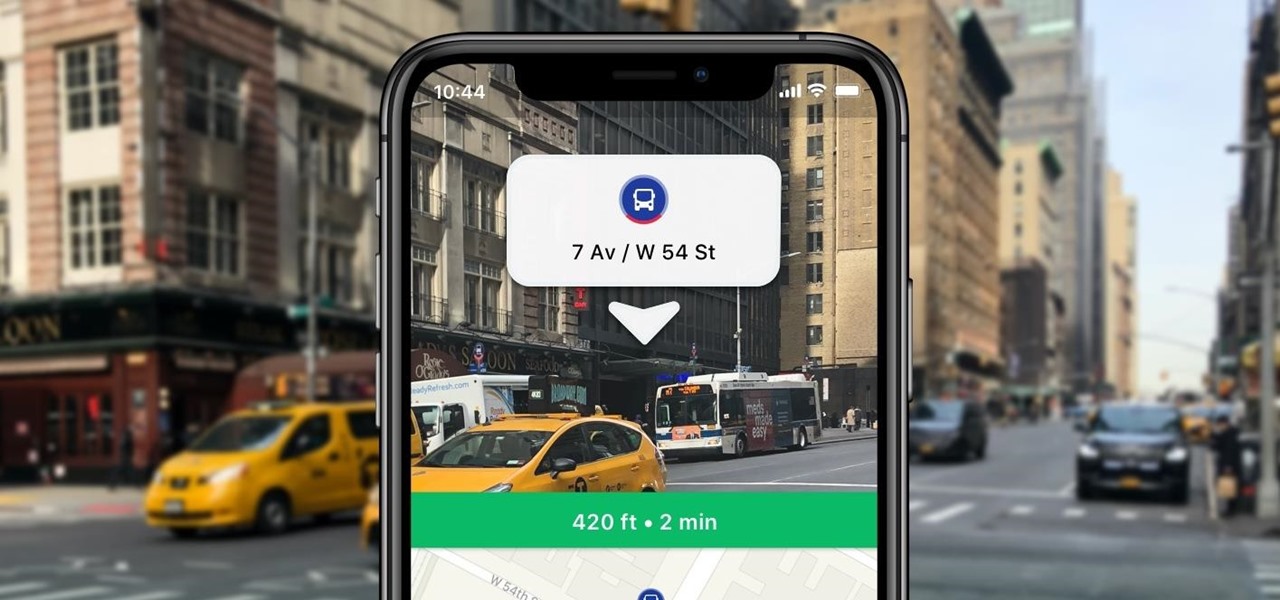
As helpful as it is, Google Maps isn't the only mapping app with augmented reality walking navigation anymore.

A lot of time can be wasted performing trivial tasks over and over again, and it's especially true when it comes to hacking and penetration testing. Trying different shells to own a target, and testing out privilege escalation commands afterward, can eat up a lot of time. Fortunately, there is a tool called One-Lin3r that can quickly generate shells, privesc commands, and more.

The landscape of augmented reality marketing is growing by leaps and bounds nearly every month, with Hollywood and the cosmetics industry leading the way.

If you have friends who aren't privacy-conscious, you've surely heard the old "What do I have to hide?" excuse. Despite the fact that billions of people are using the internet each day, many of them don't know the dangers that can find them. And many don't know the tools to combat them.

There are a number of reasons you'd want to delete your Skype account. You may have decided to move away from the app in favor of another service like WhatsApp or FaceTime, or perhaps you want to erase your account due to an online hack. Regardless of why you might want to delete your Skype account, doing so isn't quite as straightforward as it appears.

Since iCloud's introduction in 2011, you get only 5 GB of complimentary cloud storage with your Apple account. With iPhone backups, app data, iCloud Drive files, and even emails (if you have a Mac, Me, or iCloud email address), you'll quickly run out of space to back up photos and videos. Fortunately, Google offers 15 GB of free storage, making it easy to upload your Camera Roll for safekeeping.
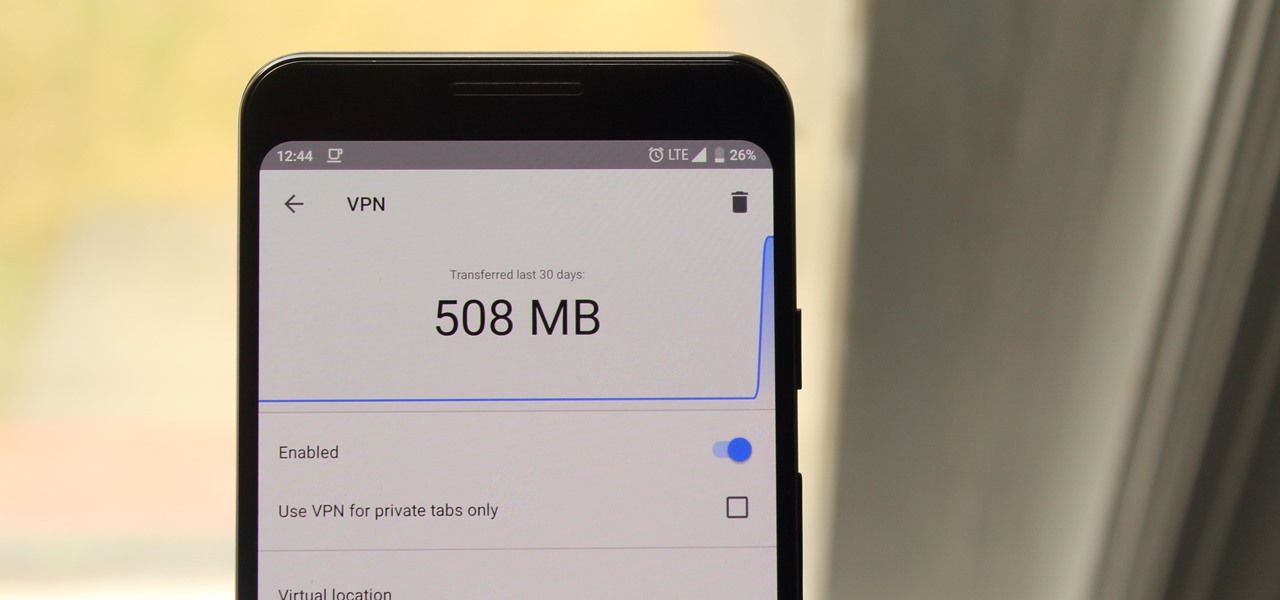
Browsing the web can be dangerous. With all of the various threats out there, it isn't enough to just avoid bad links and visit only HTTPS websites. You need to take advantage of the tools available to you so you don't end up the victim of some scam. Fortunately, Opera is making this a bit easier.

Unless you're completely new to Instagram, it's likely that you've linked your account with a third-party service at some point and forgotten about it. Those services still have access to data such as your media and profile information, so it's important that you not only know how to find these "authorized" apps, but that you know how to revoke their permissions.

If you use Apple's email services and the "From:" field in your iPhone's Mail app is cluttered with @Mac.com, @Me.com, and @iCloud.com variations of the same address — along with third-party accounts — there's an easy way to declutter things and hide the addresses you don't use anymore.

A new augmented reality cloud platform from German startup Visualix is working to give enterprises the capability to scan their own warehouses, factories, and stores and create maps for augmented reality navigation.

Augmented reality gaming developer Niantic has decided to give its players the opportunity to make their mark on Pokémon GO with a PokéStop nomination system.
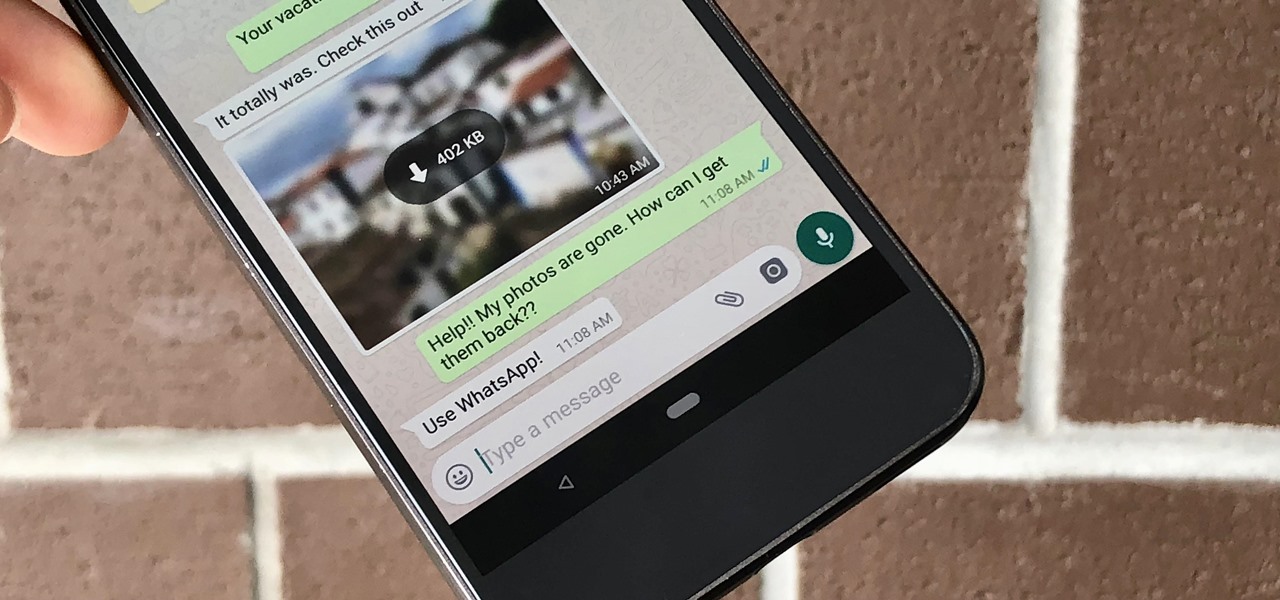
Thanks to cloud storage's increasing accessibility, permanently losing photos is becoming less and less common. Still, if you accidentally delete a picture from your smartphone without first making a backup of some sort, that data is pretty much toast — unless we're talking about photos from WhatsApp.

Thanks to recent reports, we now know third-party apps have a lot more access to our Gmail than we may have initially thought. In fact, these third-party apps have the ability to read our emails, not because these companies are necessarily shady, but because we agreed to it. Luckily, there's a way to view which apps have this access, as well as a way to boot those apps from your Gmail entirely.

In this series, we are going to get you to the edge of building your own cloud-based, cross-platform augmented reality app for iPhone, Android, HoloLens, and Meta 2, among other devices. Once we get the necessary software installed, we will walk through the process of setting up an Azure account and creating blob storage.

The cosmetics industry faced a rude awakening on Friday as beauty behemoth L'Oréal gobbled up ModiFace, one of the leading providers of augmented reality technology to the cosmetics industry (price details for the acquisition were not disclosed).
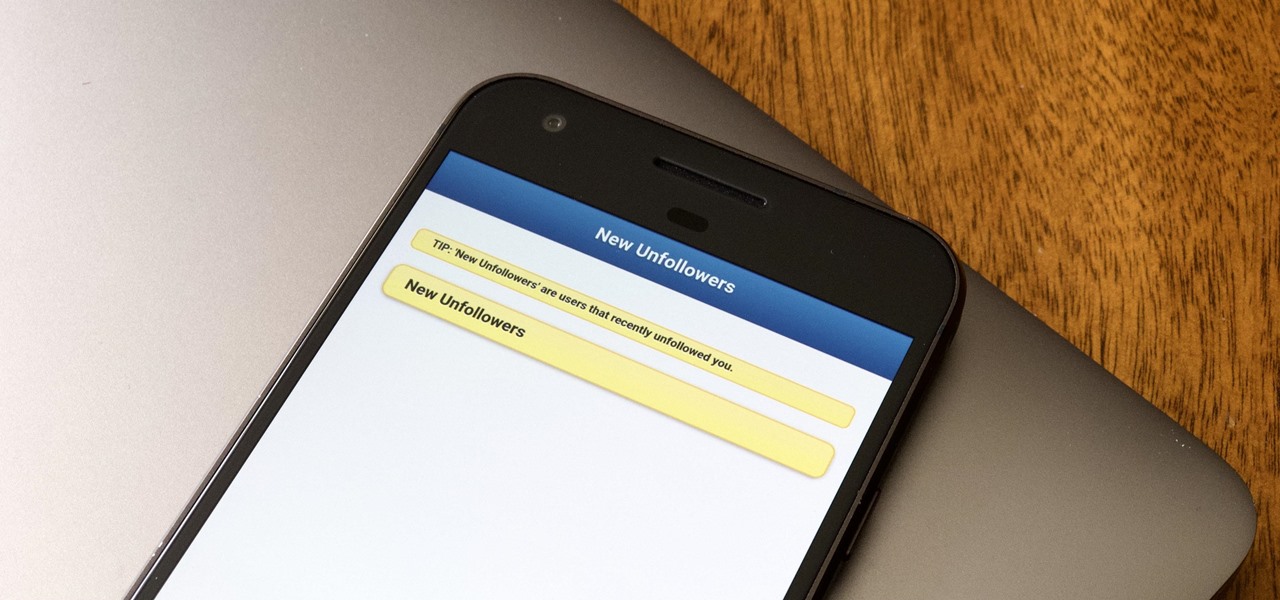
Followers are everything. After all, you need someone to listen to your tweets about last night's episode of your favorite TV show. But what about when people unfollow your account? Not only have you lost part of your follower base, you have no idea who left. Luckily, there are tools out there to help you learn just that, even if Twitter itself won't give up the info.

While the mainstream consumer market waits for cool augmented glasses to arrive from Magic Leap, or maybe even Snap Inc. (Spectacles 2.0??), AR headset maker DAQRI and its business customers are finding new, money-saving and time-saving use cases for the technology today.
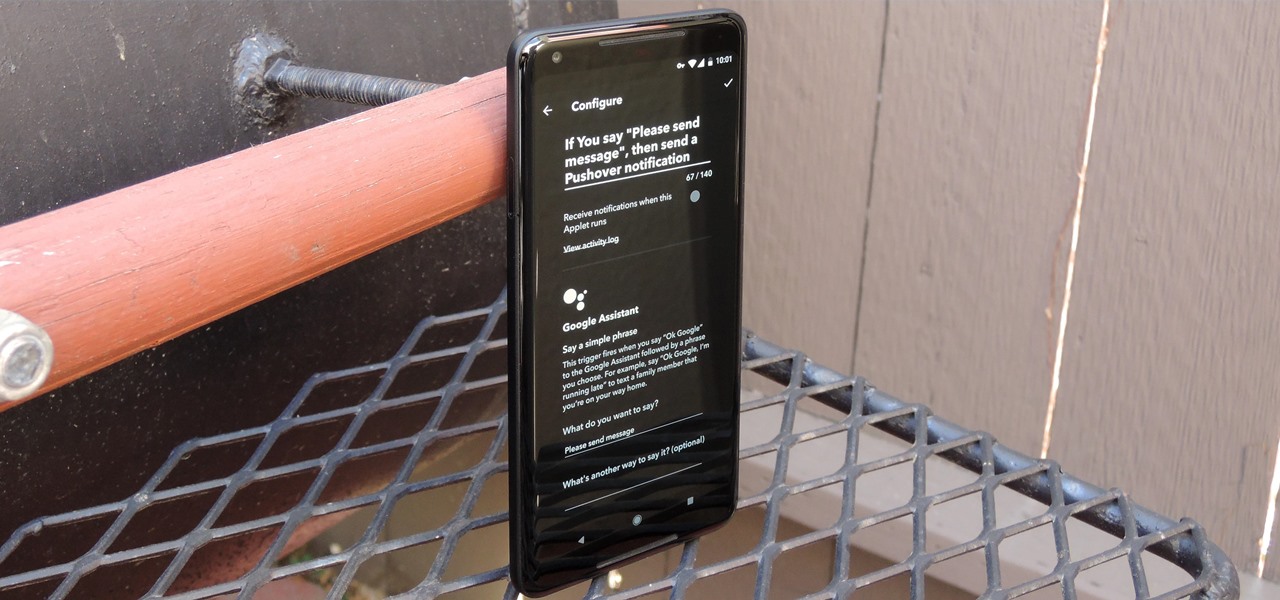
IFTTT is a fantastic tool that lets you trigger actions on your smartphone that normally require more advanced hacking. With the help of its friendly user interface, turning your phone into a more personal device has never been easier. However, the app has some more intricate options under the surface, making advanced implementations of applets difficult for beginners.

When it comes to augmented reality smartglasses, for now, it's still a mostly enterprise world, since the form and function of most are more acceptable on a job site versus your local cafe, and the still high price tags are far more palatable to major companies rather than individuals.

Tor is an excellent obfuscation network for web traffic, and while instant messaging over the network is very useful, it can be relatively difficult to configure. In this guide, we'll look at two synchronous communications platforms (instant messengers) which can be routed over the Tor network, Ricochet and XMPP.
A survey by ABI Research revealed that only 25 percent of businesses have implemented augmented reality technology in some form or fashion.

Cruise Automation, the driverless car startup General Motors (GM) bought for $1 billion in 2016, is readying a formidable fleet of robo-taxis for rollout in cities throughout the US. But when it comes to details about how the company plans to realize these lofty goals, it's been fairly tight-lipped.

Paying for street parking in New York City just got so much easier. Instead of searching for loose change or hoping you didn't forget your wallet, you can use a device you always have with you: your phone.

Wegmans recently partnered with Instacart, an online grocery-delivery app, to bring your groceries right to you. The collaboration will begin in the suburbs around Washington, DC, and Wegmans plans to expand to other areas later on.

Global design and technology services company Tata Elxsi says it has licensed its advanced autonomous vehicle middleware platform "AUTONOMAI" to a "leading automotive OEM."

The Shadow Brokers, a hacker group known for its dump of NSA hacking tools in 2016, has just leaked their remaining set of data which implies that the NSA compromised SWIFT, the global provider of secure financial services, to spy on banks in the Middle East.

Nokia, the Finnish telecommunications company, is about to shake things up a bit after its networks sales in the final quarter of last year declined 14% compared to sales in 2015.

ProtonMail has long been the favorite of journalists and security-conscious professionals, with Edward Snowden the most famous example. But these days, everyone cares about anonymity, so it's no surprise that ProtonMail currently has over 2 million users. And now the service is even better.
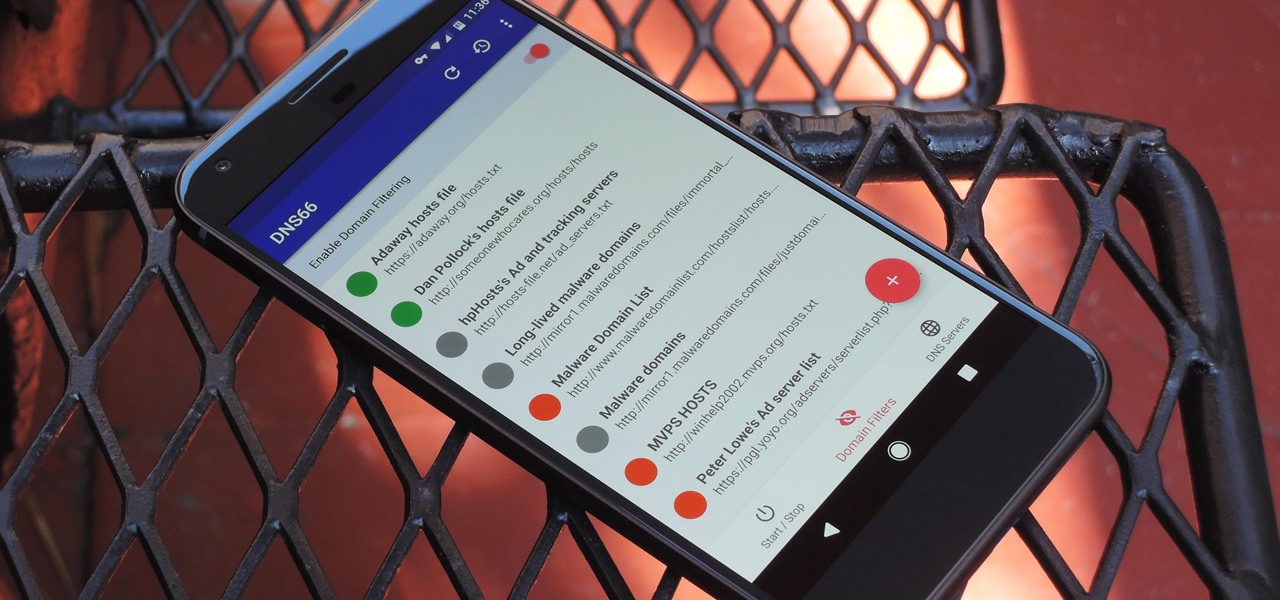
If you're in the market for a non-root ad-blocker, developer Julian Klode has an app that you'll definitely want to check out. It uses Android's VPN system in a similar manner to alternative apps like NetGuard and AdGuard, but it's got a new twist that should save lots of battery life in the process.
A few months ago, LlabTooFeR leaked a full system dump from Google's then-unreleased Pixel and Pixel XL smartphones. That may not seem like a big deal at first glance, but the system dump contained all of the preinstalled apps and services from Google's new flagships—including the much-anticipated Google Assistant.

If you want to keep your online world secure, your best bet is to have a different password for every site and service that you use, and to make sure each of the passwords are comprised of random characters instead of familiar words or numbers. But this obviously creates a problem—how exactly are we supposed to remember all of these complicated passwords?

Greetings to all geeks, hackers, nerds, and explorers of Null Byte. Welcome to my brand new tutorial, "Using BASH for Computer Forensics". This tutorial will give you a look at how the computer programming language, Bash, can be used to find out details on apple devices for later use.
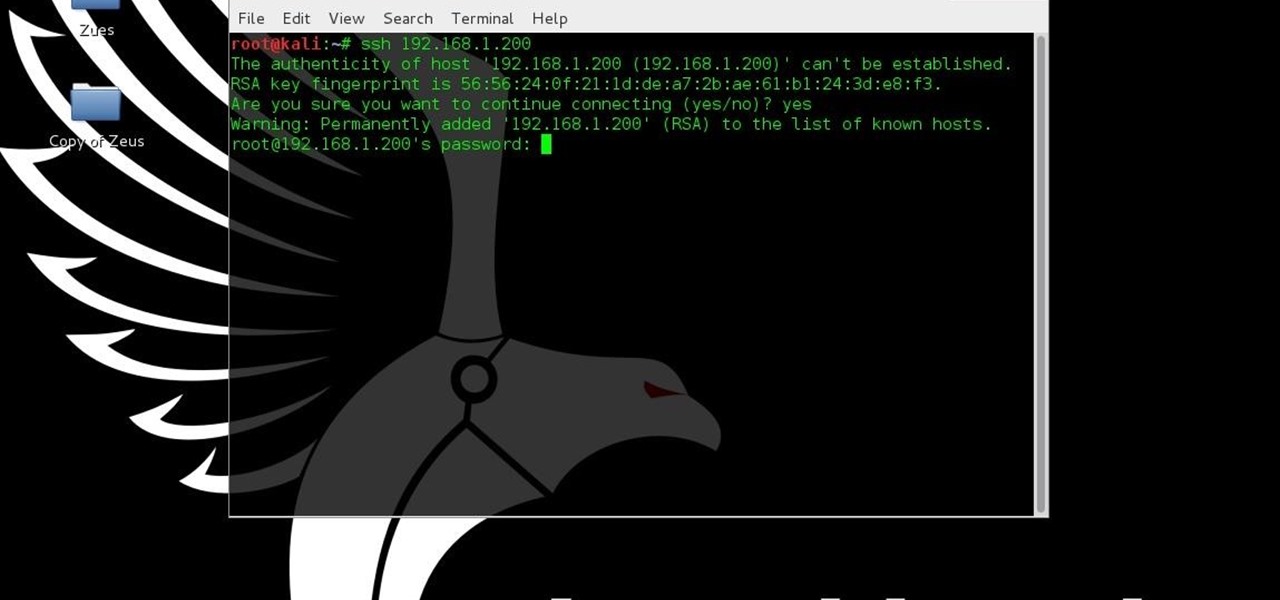
This tutorial is for people who want to try different types of hacks in an environment that is the same for everyone so it will help people to ask questions and learn. This series assumes you know how to run a VM and network them together. This series also assumes that the services running on the Metasploitable machine are needed to be running.