Bring a little joy and festivity to this holiday season, check out this do-it-yourself video to see how to make a festive holiday wreath, perfect for creating that festive atmosphere around your house during Christmas. At home on your front door or in a hallway, this cheerful Christmas wreath decoration is a cinch to make and sure to liven the Christmas spirit.

Learn how to do dumbbell 21 curls. Presented by Real Jock Gay Fitness Health & Life. Benefits

Keep your stargazing sights and new experiences logged in a journal. Watch Amateur Astronomy for Beginners - The Astronomical Journal.

Have you always wanted to spread your mark on urban society, but were a bit of a scaredy-cat? Well now you have the chance of convincing anyone and everyone you're the next great graffiti artist by creating graffiti in Photoshop. If anyone asks just say the local council came and cleaned it off and it's a good thing you took a picture of your art, isn't it?
Just a few days after a senior US counter-terrorism expert warned that US drone strikes were turning Yemen into the “Arabian equivalent of Waziristan”, US drone strikes yesterday aped the tactic of ‘follow up’ strikes used by the US in Pakistan.

In each day of our life, we see inflammation. We see it during sore throats and abscess formations in our bodies, and even slight tooth pain is a form of inflammation. Sometimes it's good when it fights to protect us from invading organisms, but sometimes it becomes bad when it occurs in inappropriate ways, like acne.
Do you'll know a program software to detect unmask caller's for cellphones for abroad network's carriers, as i often travel abroad to Hong Kong ,Japan and Malaysia and i went switch to those networks via changing the States sim card to the local domestic sim card i often received unmasked/private number's callers calling myself but i have not way of finding out who is it?
Do you know a program software to detect unmask caller's for cellphones for abroad network's carriers, as i often travel abroad to Hong Kong ,Japan and Malaysia and i went switch to those networks via changing the States sim card to the local domestic sim card i often received unmasked/private number's callers calling myself but i have not way of finding out who is it?

Contrary to popular belief, you don't need a gallery space or expensive art education to share your art with the rest of the world. Take a cue from today's innovative artists who share their creative experiments directly out on the streets and in public spaces for the everyday pedestrian in unique and quirky ways. And no, you don't have to be a skilled graffiti tagger, either. Just some yarn, random knick-knacks, photos, and Post-it notes as well as other basic office supplies.

Hello World! Welcome to the place wholly devoted to the local surf of Southern California. I am like many people a transplant from the East Coast. I started surfing when I moved here for college 8 years ago.

This video is regarding air conditioner services. Leaks are a major cause of problems. Water and air can leak into the system. Water damage, rust and refrigerant leaking all make the unti ineffiecient. You should evaluate the unit regularly and also run it periodically to keep the system from working properly.The manual should provide a good amount of information that will help you ensure you are not doing anything to damage the system of repair it incorrectly. Service your vehicle's air cond...

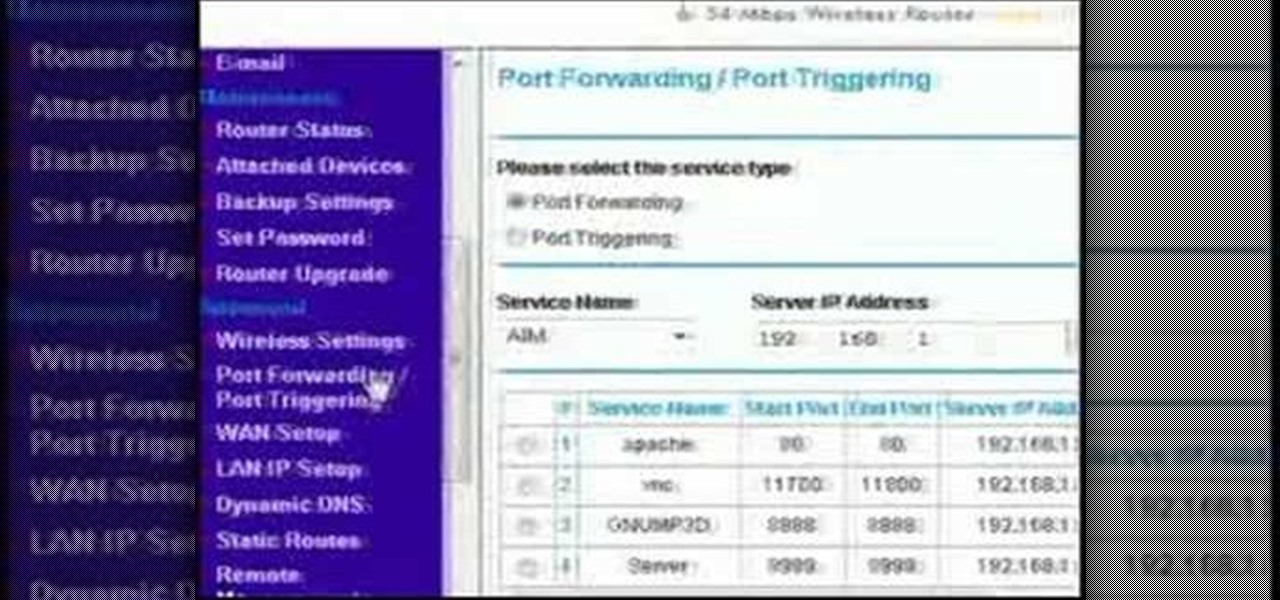
This video discusses how to bypass your router to access your server. In the search window type in CMD to open up a command prompt. Then type in ipconfig to bring up the ip configuration. You want to look for the ip address for the default gateway and the one for your computer. They should both start with 192.168. Once you find them open up internet explorer and type in the ip address for your default gateway and it should then prompt you for a user name and password. Log in and look for a po...

Your IP address is what identifies your personal computer while you are online. You may want to change your IP address for privacy, to bypass website settings, to download, or for various other reasons. This tutorial will take you through the steps you need to start surfing more anonymously.

The World Health Organization has declared the new coronavirus a pandemic, and the Centers for Disease Control and Prevention recommends video visits with a healthcare professional to reduce the risk of being exposed to the coronavirus that causes COVID-19. If you are experiencing mild flu-like symptoms, virtual doctor visits may also prevent you from endangering others.

Privilege escalation is one of the essential skills a hacker can have and often separates the newbies from the pros. With a continually changing landscape and a plethora of exploits out there, it can be a problematic aspect of any attack. Luckily, some tools can help expedite the process. Linux Exploit Suggester is just one of many to help you get root.

Compromised uTorrent clients can be abused to download a malicious torrent file. The malicious file is designed to embed a persistent backdoor and execute when Windows 10 reboots, granting the attacker remote access to the operating system at will.

While SSH is a powerful tool for controlling a computer remotely, not all applications can be run over the command line. Some apps (like Firefox) and hacking tools (like Airgeddon) require opening multiple X windows to function, which can be accomplished by taking advantage of built-in graphical X forwarding for SSH.

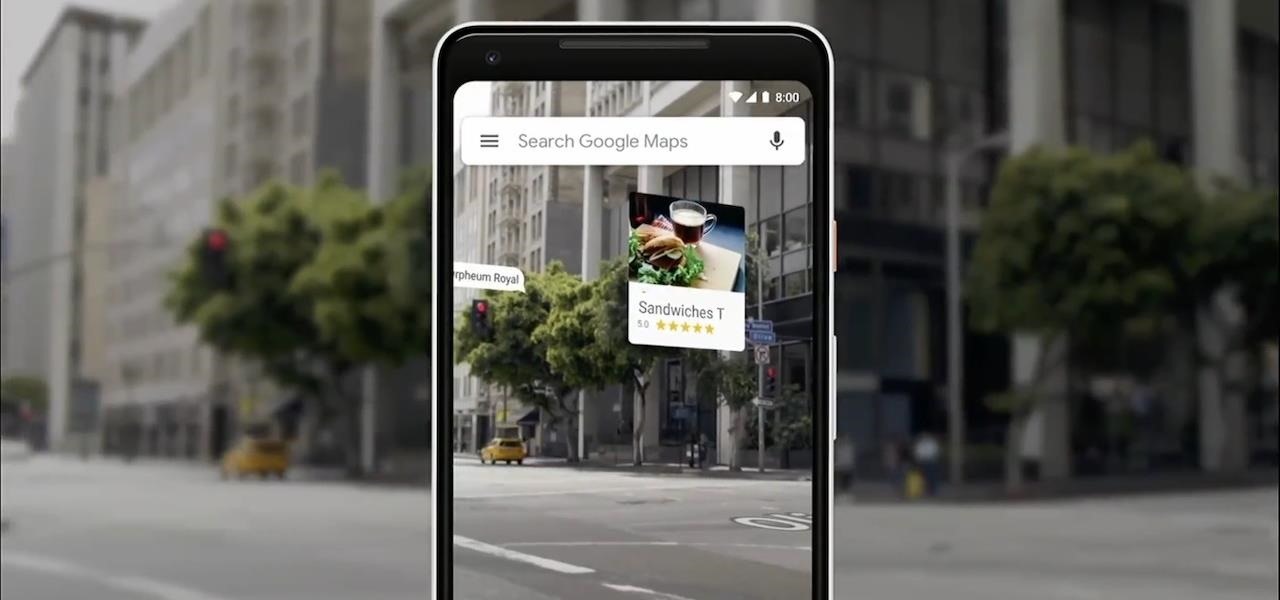
The augmented reality walking navigation mode for Google Maps appears to be closer to an upcoming release for the general public.

AMC Theatres was never a fan of MoviePass and even predicted its unsustainability. After the struggling MoviePass turned off diehard fans with too many new restrictions to combat its cash problems, AMC stepped in to save the day with its AMC Stubs A-List subscription for cheaper movie tickets.

Let's face it, iPhones are expensive. With the latest iPhone XS Max reaching as high as $1,449, our wallets could all use a little support. That's where Black Friday comes in, supplying us with deals and discounts on iPhones of all kinds. If you're looking for a new iPhone this holiday season without having to break the bank, you've come to the right place.

Hundreds of Windows 10, macOS, and Linux vulnerabilities are disclosed every single week, many of which elude mainstream attention. Most users aren't even aware that newly found exploits and vulnerabilities exist, nor that CVEs can be located by anyone in just a few clicks from a selection of websites online.

When OnePlus announced their partnership with T-Mobile and the deal the magenta carrier is set to offer, mouths dropped. But as usual, this deal comes with some caveats. The bulk of these will hurt the folks who love to root, something a large portion of the OnePlus community enjoys doing.

With just one line of Ruby code embedded into a fake PDF, a hacker can remotely control any Mac computer from anywhere in the world. Creating the command is the easy part, but getting the target to open the code is where a hacker will need to get creative.

For those of us who love to multitask, picture-in-picture mode is a godsend. The feature, introduced in Android 8.0 Oreo, lets you enjoy videos in a floating window overlaid on top of another app. However, while the OS does have native support, only a select number of apps support the feature.

Hackers rely on good data to be able to pull off an attack, and reconnaissance is the stage of the hack in which they must learn as much as they can to devise a plan of action. Technical details are a critical component of this picture, and with OSINT tools like Maltego, a single domain name is everything you need to fingerprint the tech details of an organization from IP address to AS number.

Kali Linux is established as the go-to operating system for penetration testing, but in its default configuration, it's less than ideal for regular desktop use. While in many scenarios, a live boot or virtual environment can resolve these issues, in some situations, a full installation is better. A few simple changes can be made to a Kali Linux desktop to make it safer to use in this environment.

Hashes containing login passwords are transmitted between Windows computers on local Wi-Fi networks. By intercepting and decrypting these hashes using Responder and John the Ripper, respectively, we can learn a target's login credentials which can be later used to gain physical access to their computer.

Apple has tools built into iOS to help parents monitor the iPhone habits of their children. However, those same tools can be used by everyday iPhone owners to both hide apps they don't care about, as well as restrict features they don't need or that infringe on privacy. Whether you fit into one category or the other, all iPhone users can benefit from the "Restrictions" feature.

The internet is constantly under siege by bots searching for vulnerabilities to attack and exploit. While conventional wisdom is to prevent these attacks, there are ways to deliberately lure hackers into a trap in order to spy on them, study their behavior, and capture samples of malware. In this tutorial, we'll be creating a Cowrie honeypot, an alluring target to attract and trap hackers.

Configuring onion services for the first time can be tricky. A surprising number of system administrators make seemingly trivial mistakes that ultimately lead to catastrophic cases of de-anonymizing supposedly anonymous sites on the dark web. OnionScan is a tool designed to identify common misconfigurations in onion services and aid us in understanding how to fix them.

Threats to your privacy and security are everywhere, so protecting your data should be the highest priority for anyone with a smartphone. However, one threat many people overlook is the company who supplies the operating system your Android phone runs — Google.

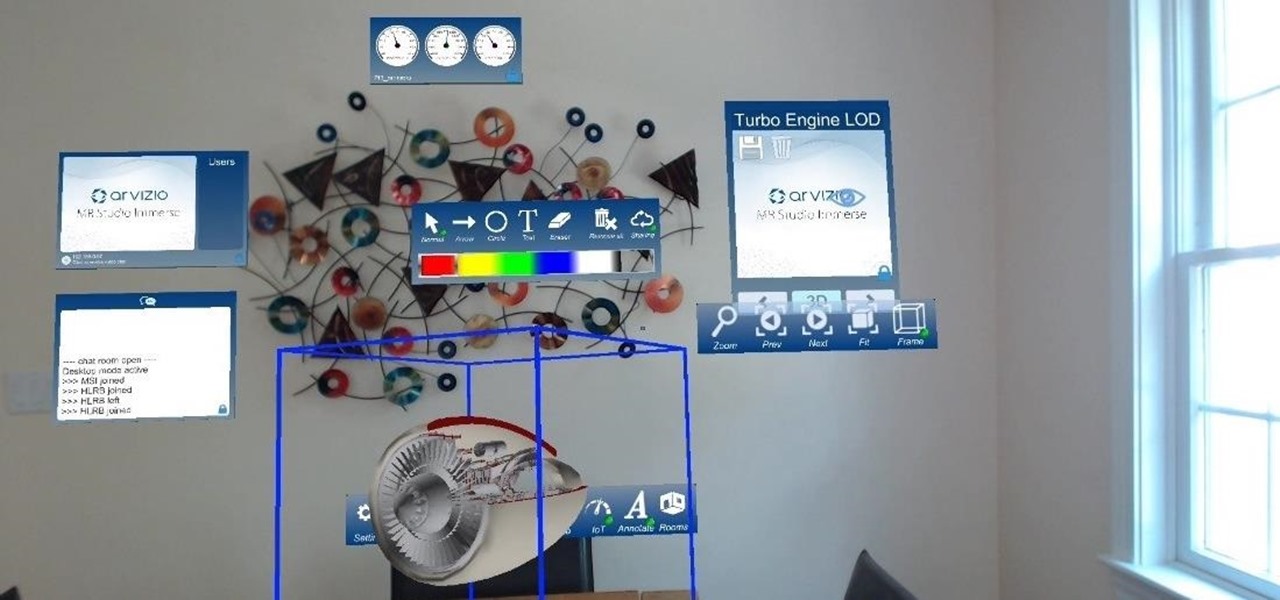
HoloLens developer Arvizio has expanded its collaboration suite of tools for enterprises with a device that can stream and record mixed reality experiences in high-definition for local and remote audiences.

The leading platforms enabling augmented reality technology lead our headlines in Market Reality this week.

Download a popular, legit app from the Google Play Store. Decompile it. Add malicious code. Repackage the app. Distribute the now trojan-ized app through third-party Android app sites. This is how advertising malware Ewind, what Palo Alto Networks calls "adware in applications' clothing," infects Android users.

Uber resumed its pilot program for driverless cars after one of its autonomous vehicles crashed in Tempe, Arizona last weekend.

The HoloLens is a natural medium for 3D data visualization, which offers a far more ideal approach over 2D screens to managing multiple resources simultaneously and grasping the bigger picture. We've already seen how management is using holograms to oversee cities, firefighters, and the military, and now training for sports teams is being addressed with VAR Football.

Watching the NCAA Men's Division I Basketball Tournament without cable used to be easy. As long as you had an internet connection, CBS and Turner (TBS, TNT, and TruTV), which co-broadcast March Madness, let you watch all 67 games online free of charge.

Hello ladies and gentlemen, PySec here coming at you with another informative(hopefully) article for you all. In the last tutorial, we finally finished our discussion about IP Addressing and I intentionally didn't mention a really important concept with which IP Addressing wouldn't be feasible without it. What I'm talking about is how our network device gets the IP Address in order to communicate with other devices on the network/Internet. There are many different ways for that to be accompli...

This Is for the Script Kiddies: This tutorial is about a script written for the How to Conduct a Simple Man-in-the-Middle Attack written by the one and only OTW.