Microsoft has invested years and countless man-hours in an effort to get their cloud storage service on par with competitors like Dropbox and Google Drive, who have long resided at the top of this market. Their hard work has definitely paid off, as OneDrive (formerly SkyDrive) has finally reached a point in its development where it can stand toe to toe with any comparable service in almost any measurable regard.

The telecommunications industry has come a long way since Ma Bell opened the first telephone exchange in the late 1800s. With the advent of fiber optics and wireless broadband technology, we no longer have a need for a dedicated phone connection, as today's data networks can carry much more than a simple voice conversation.

Finger limes are one of those foods that bring out the little kid in even the most staid grown-up. I dare you not to squeal when you cut one open, squeeze, and see all that bubbly goodness emerge.

Welcome back, my novice hackers! Reconnaissance is one of the most important preparatory steps to hacking. As I have emphasized many times before here on Null Byte, you must know the operating system, the ports, the services, the applications, and sometimes even the language of the target to be effective. If you haven't taken the time to gather this info, then you are likely wasting your time.

With popular remote desktop app LogMeIn recently ending its free service, lots of Android users have begun looking for alternatives. There are some good ones out there like TeamViewer and Microsoft Remote Desktop, but today, Google released an app that makes a pretty good contender.

For the most part, transferring files from your computer to your Nexus 7 (and vice versa) is a simple process. Just hook up your tablet to your computer with the USB cable and transfer. However, most of the time you'll need additional software on your computer to do this, and then, of course, you need the USB cable.

Former professional athlete and fitness expert takes you through a full body fitness workout!

Learn How to draw Katy Perry with the best drawing tutorial online. For the original tutorial with full control over the speed and steps please visit: how to draw.

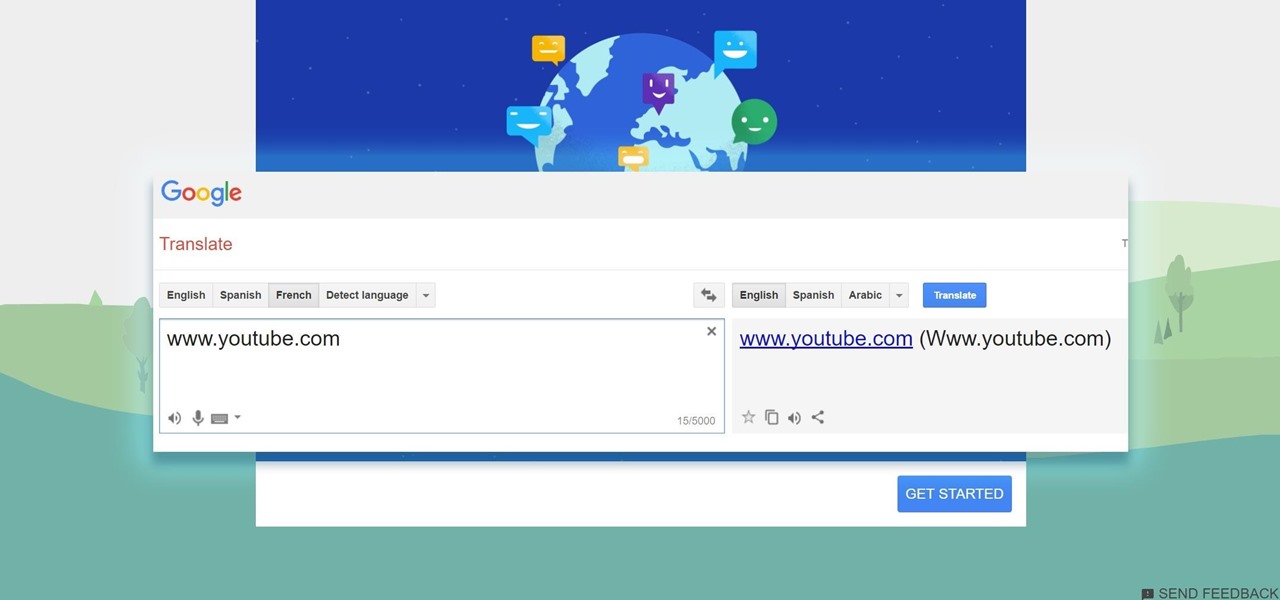
Need to break out of the restrictions your school or workplace have on internet browsing? Maybe you want to waste some time on YouTube, check out some gaming action on Twitch, or simply just browse Facebook or Twitter.

Let's face it, there is nothing more badass than killing zombies in a mall with a little girl's tricycle wearing the full plate mail of a medieval knight. This video will show you how to set that up in Dead Rising 2 by getting all of the four pieces of the knight armor, which will together half all the damage you receive. Well, it shows you an awesome demo of the scene I described above, but to get the pieces simply do the following:

In this video we learn how to tie a necktie in a Full Windsor knot. First, take four inches on the skinny side and bring the long end over it. Then, bring the tie up back underneath and pull it through. Drop this down to the right hand side and then bring the long end back up underneath the other side. Bring the tie across the front of the knot towards your neck and pull it through the back of the tie. Next, bring the tie across the front of the knot and create a cross section. Bring it back ...

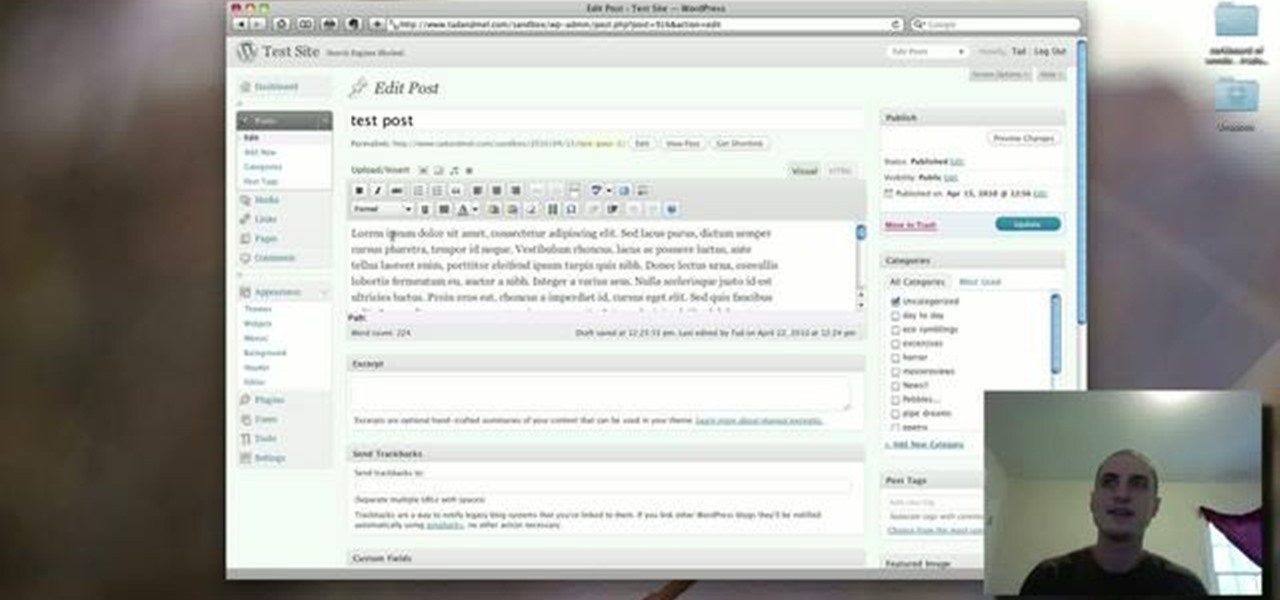
In this clip, learn how to use the Format Dropdown Menu, Underline, Align Full and color adjustment buttons in the WordPress editor. Every version of WordPress brings with it new features, new functions and new ways of doing things. Fortunately, the very same technology that allows an open-source blog publishing application like WordPress to exist in the first place also makes it easy for its users to share information about the abovesaid things through videos like this one. Take a look.

In this video, we learn how to draw a full body Donald Duck. First, start by drawing circles for the eyes and body. The body circle should be larger and more round than the head. After this, start drawing lines to connect these two circles and make the neck and body with a t-shirt on. After this, draw the tail on him and then start to draw the beak. Next, add in legs to the body and then add in the eyes. Use a darker pencil to outline the body, then make lines for the hair on the head and on ...

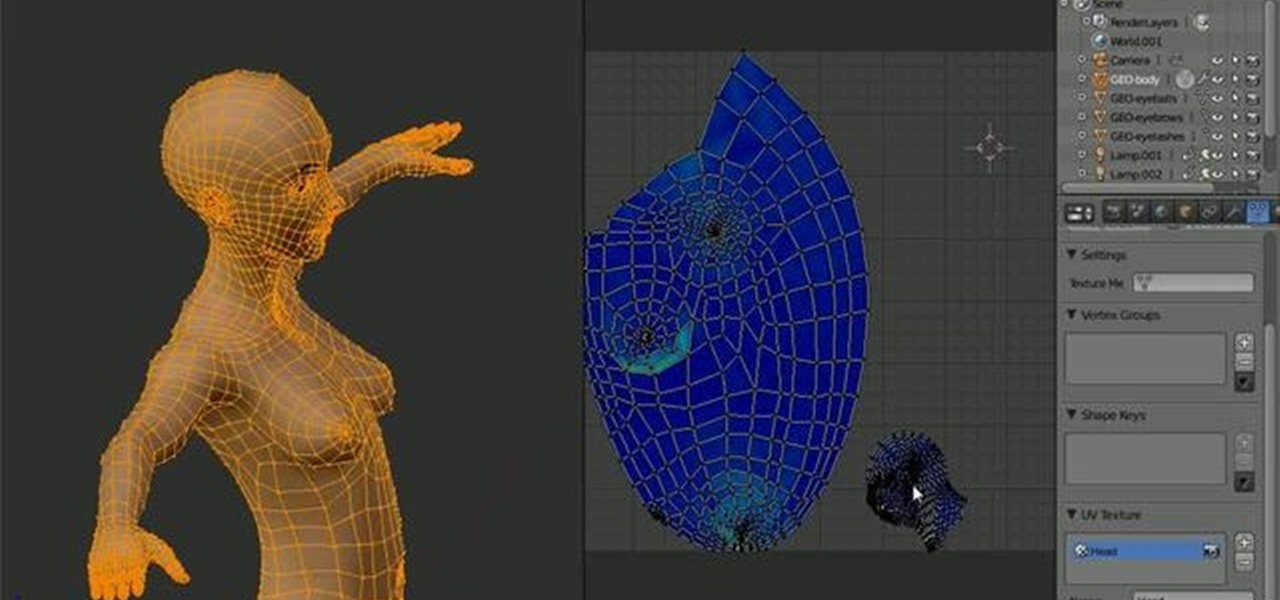
In this Blender 2.5 video tutorial, you'll see how to UV unwrap a full, stylized female character. The tutorial covers creating seams, unwrapping, pinning and techniques to reduce stretching. Whether you're new to the Blender Foundation's popular open-source 3D computer graphics application or are a seasoned digital artist merely on the lookout for new tips and tricks, you're sure to be well served by this free video software tutorial from the folks at CG Cookie. For more information, includi...

Flip open any major women's glossy - or just look at the covers - and you'll see that Victoria's Secret hair (i.e. full, voluminous waves that land somewhere between full-on curls and pin-straight hair) is the most common hairstyle used.

Want to program your own Java games and applications but don't know beans about object-oriented programming? Never you fear. This free video tutorial from TheNewBoston will have you coding your own Java apps in no time flat. Specifically, this lesson discusses how to add a exit full screen mode feature to your applets when writing code in the Java programming language. For more information, including detailed, step-by-step instructions, watch this helpful programmer's guide.

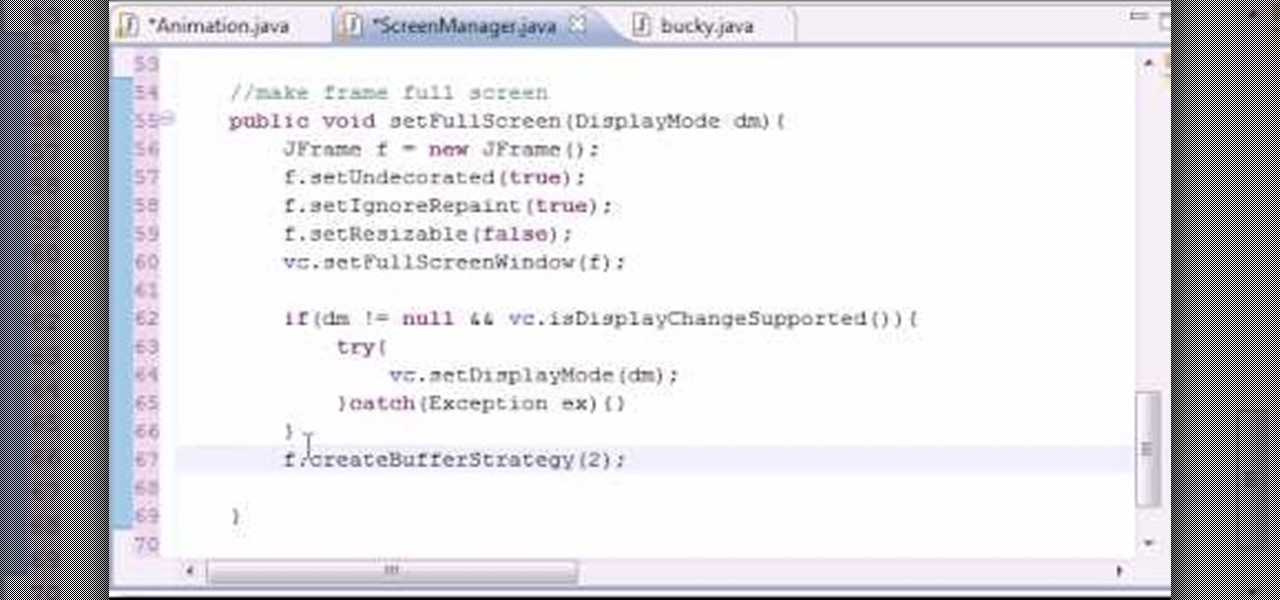
Want to program your own Java games and applications but don't know beans about object-oriented programming? Never you fear. This free video tutorial from TheNewBoston will have you coding your own Java apps in no time flat. Specifically, this lesson discusses how to to create a full-screen frame when writing code in the Java programming language. For more information, including detailed, step-by-step instructions, watch this helpful programmer's guide.

In this video tutorial, viewers learn how to do a standing full (360 back-flip). Before attempting this trick, it is highly recommended that users have mastered a back-flip. Make sure that you can see he ground in mid-air. Bring your feet together and bend the arms back. Bend your knees and push up with your arms raised up. Then leap up high and twist you body in mid-air. Users may also start twisting the body as they leave the ground. This video will benefit those viewers who are interested ...

Tom Skowronski teaches us how to shoot a good video. Look before shooting so you have a more controlled movement. Hold camera steady at all times. Move the subject in front of the camera and turn the camera mans back to the sun to illuminate the subject. . Give nose room for a more professional look. Have a full frame and no dead space to have a natural looking video. Cut off at head to have a full frame. Following Tom Showronski's video-making advice can lead to a professional-looking video....

No matter what you think of Slipknot's music, you gotta admit they have a cool, horror movie look. This video will walk you through how to make your own Slipknot full head masks. You'll be surprised how simple the process is.

Full-Text search allows you to save large portions of text – even Microsoft Word documents, or other file formats – into your database and perform complex queries based on this textual data while expecting great performance. This lesson demonstrates how to set up Full-Text search paying particular attention to the nuances of setting it up within SQL Server Express. Enable full-text search in an SQL database.

A network Tarpit, sometimes know by the German word Teergrube, is a service or set of hosts that deliberately try to slow malicious network connections down to a crawl. The idea is to put up unused hosts or services on the network that respond to an attacker, but do things to waste their time and greatly slow their scanning (or spreading in the case of Worms). To follow along with this video tutorial, you'll need a package called LaBrea by Tom Liston and an unused IP address to tarpit. Set up...

Golf king Rickard Strongert explains how to avoid hitting fat shots and avoid carving divots the size of hedgehogs out of your local golf course. Stop hitting fat shots.

If you find yourself alone and bored with a spoon and fork then this is worth taking a look at. Learn how to float utensils above a glass using only fire and your imagination. This trick would work great for parties and bars alike. Float cutlery items and become a local magical legend. Perform the floating cutlery trick.

Many people all around the world have been using Korean Anycall Galaxy S (SHW-m110s), because the price is reasonable and easy to used. But after they buy this phone they always saw two clocks in the front screen while the phone locked, one is Local clock and the second is Seoul clock. The most of the user always want to remove it but they can’t do it, now I’ll show you how to remove it step by step. Step 1: Go to Settings Step 2: Wireless and Network Step 3: Mobile Networks Step 4: T Roaming...

Looking for the best way to to pay or transfer money for your overseas property can be difficult. Should I make a money transfer with my bank or a broker? And many other questions that we ask ourselves.

Some of you might be using Tor to host hidden services, and some of you might not even know what hidden services are. If the latter's you, do not miss this article. Why? Because you can host your websites and services on the I2P darknet. It's safe and secure—it's anonymous.

Here's a delicious Byte of information for you. A proof of concept program on Linux was coded to exploit a known bug in how the Linux Kernel (versions 2.6.39+) handles permissions for the

In this how to video, you will learn how to draw a full moon. First, draw a large circle. Now fill the circle in with an orange color. Add shading with a darker shade of orange to create texture. Next, fill in the back of the moon with a black color. Make sure no white is showing. Next, a silhouette in front of the moon will be created. This is done by creating tree shapes in the bottom half of the moon in a black color. Fill in the outlines with black. Once this is done, your full moon image...

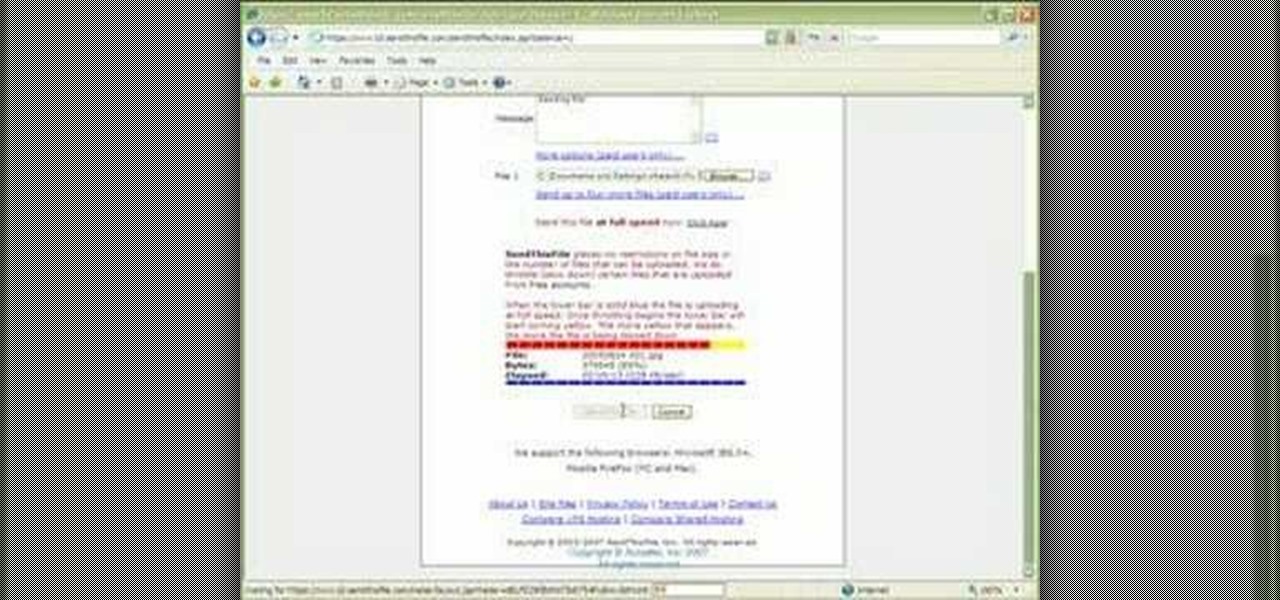
1. Type in WWW.sendthisfile.com in the web toolbar and press enter 2. Click on Register found on the top right side

This video shows you how to control your computer from your iPod touch. 1. Go to UVNC. Click on Installation. This will take you to download options. Download the latest stable version. 2. Install Hamachi, which helps you find your computer's IP address. Click on Download Here link, fill in the registration information, and click submit. 3. Install a VNC listener on your iPod so it can connect to your desktop. Jailbreak your iPod, and open the installer. Click All Programs; scroll down until ...

Saving money during this tough economic period is more important than ever, especially when it comes to servicing your vehicle. So in this 2 part video tutorial, you'll find out one way you can keep your wallet fat, by learning how to change the oil to your Vespa scooter.

You need four persons to play doubles. One person shall be on the forehand side while the other person shall be on the backhand side. Same thing for applies for the opposite team. You need to be in your side of the court. Either you should be on the right or the left side of your court. However you have the option to move or switch sides at any time. When you are doing the service then your partner must stand in the service box with his back towards the back wall. The opposite team must stand...

Learn how to deal with tough and abusive customers and how to enact good customer service with expert retail sales management advice in this free online customer service video series.

No operating system is stricken with as many vulnerabilities as Windows, and it's often a race to release the latest patches to fix things. From an attacker's point of view, knowing which patches are present on a Windows machine can make or break successful exploitation. Today, we will be covering three methods of patch enumeration, using Metasploit, WMIC, and Windows Exploit Suggester.

Before attacking any website, a hacker or penetration tester will first compile a list of target surfaces. After they've used some good recon and found the right places to point their scope at, they'll use a web server scanning tool such as Nikto for hunting down vulnerabilities that could be potential attack vectors.

Popping a shell is often the main goal of a hacker, and it can be exciting when executed properly, but sometimes they do have their limitations. Metasploit's Meterpreter probably needs no introduction, but this powerful, dynamic payload can offer a leg up over normal shells. To prove it, we'll show how to take a normal command shell and elevate it to a Meterpreter session.

With the number of web applications out there today, it comes as no surprise that there are just as many vulnerabilities waiting for hackers to discover. Finding those vulnerabilities can be a difficult task, but there are plenty of tools available to make the process easier. While it won't help find any zero-days, web scanners such as Uniscan will detect common vulnerabilities.

If you've ever been on the receiving end of a threatening phone call, you'll immediately know the value in being able to record phone conversations on your iPhone. Beyond that extreme example, however, recording calls is still an extremely useful feature to have for important conversations like business meetings and verbal agreements, and it's totally doable with a third-party app.

The gig economy is thriving, and if you aren't already making money with your phone, you could be missing out on easy residual income. Some people just want extra cash, and some even manage to completely ditch the 9–5, enabling them to work at their own pace and set their own hours.