Full-size pickups are more difficult than cars when or smaller trucks when it comes to repairs. Even something as simple as replacing the brake pads can become daunting. But if you're changing the brake pads on your Ford F-250 truck, this video will give you some much needed help.

When you're examining a patient's chest, you start out by simply looking at them— by inspection. It will be hard to count the respirations visually on a healthy person's chest because it moves so little, but in a patient with respiratory distress, the chest might be overactive and strain may show in the neck muscles. Eve Bargmann, M.D., will also teach doctors about palpation, percussion, and auscultation of the chest and back.

In this video from Livestrong we learn how to do a barbell full squat to increase leg strength. Find a squat rack at a gym and rack your bar a little bit below shoulder. In a split stance, come up underneath the bar and rest it on the back of your shoulders. Lift off, core tight, and step back away. Feet shoulder width apart, chest up, head up. In a sitting motion, come back down and then back up. Drive through the heels, abs tight. Down and up. Remember to keep chest and head up always and s...

Check out this informative video tutorial from Apple on how to use full-screen view in Pages '09. iWork '09, the office productivity suite from Apple, is the easiest way to create documents, spreadsheets, and presentations. Writing and page layouts are easy in Pages. Numbers gives you simple ways to make sense of your data. You'll captivate your audience with new and sophisticated features in Keynote.

To properly set a table for an informal four course dinner, keep in mind that a soup course, a salad course, an entree and a desert will be served. First, add the service plate or charger to the table. Place it directly in front of the guest two inches from the table. It will serve as the under plate before the entree arrives. Use exactly the amount of silverware needed to accommodate the meal. For this meal, you will need a soup spoon, a salad fork, a salad knife, a dinner fork, a dinner kni...

Learn how to do dumbbell regular 21 curls to preacher curls. Presented by Real Jock Gay Fitness Health & Life.

How would you like to be able to watch all of the movies and television shows available on the Netflix watch instantly service on your HD2 Android phone? Check out this video to learn how to download the Netflix app.

Today is the day before Thanksgiving. It's also the BIGGEST travel day in North America. Everyone is taking flights home to their family and friends for a nice Thanksgiving dinner. But this holiday will be one to remember thanks to the TSA.

To achieve full synchronization in Assassin's Creed: Brotherhood, you will have to execute missions exactly how Ezio did. At the beginning of every mission, you will be given a restraint, and if you successfully work around that restraint, you will be that much closer to the perfect assassin.

Check out this basic back-to-school look that's also great for daily work and church services. It's a neutral makeup look with very little shimmer. It only takes about 5 minutes to create these beautiful eyes! Watch and learn how to apply these eyeshadows and cosmetics.

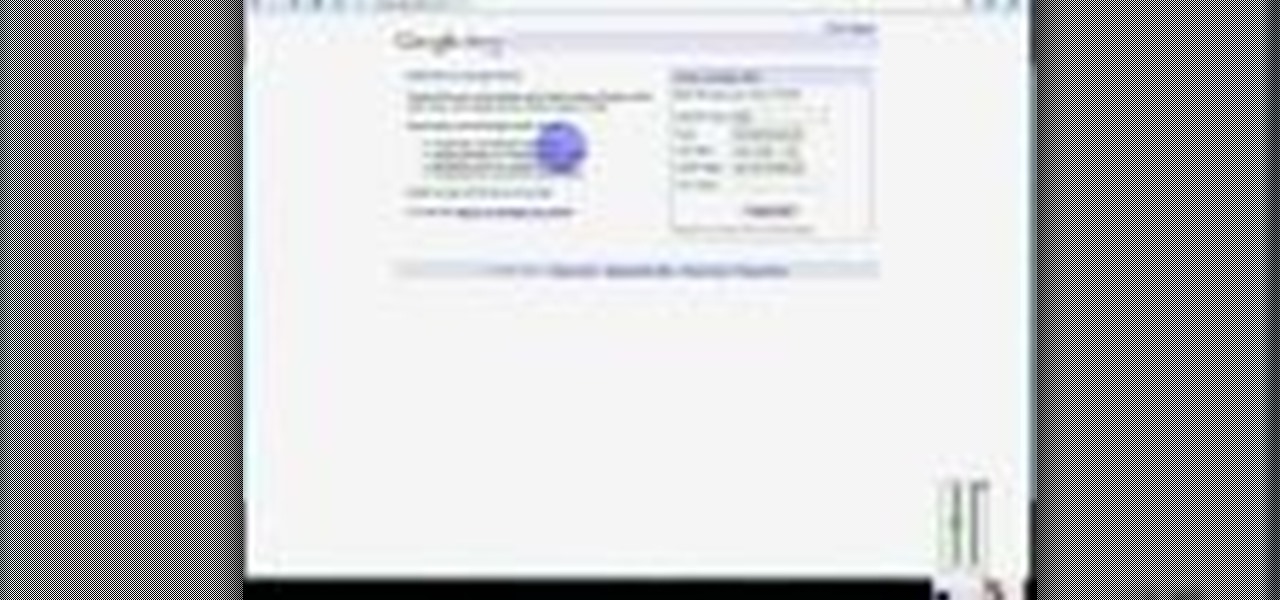
Want to receive daily, weekly or monthly updates on a subject of your choice? With Google Alerts, it's easy! So easy, in fact, that this home computing how-to from the folks at Easily can present a complete (and somewhat talky) overview of the process in just under five minutes' time. For the specifics, and to get started setting up and using Google Alerts yourself, just watch this handy how-to.

Maybe it's just us, but this city reminds us a lot of the dreamscape Parisian city from Cristopher Nolan's mind heist movie "Inception," aside from the whole city folding back over itself thing and whatnot.

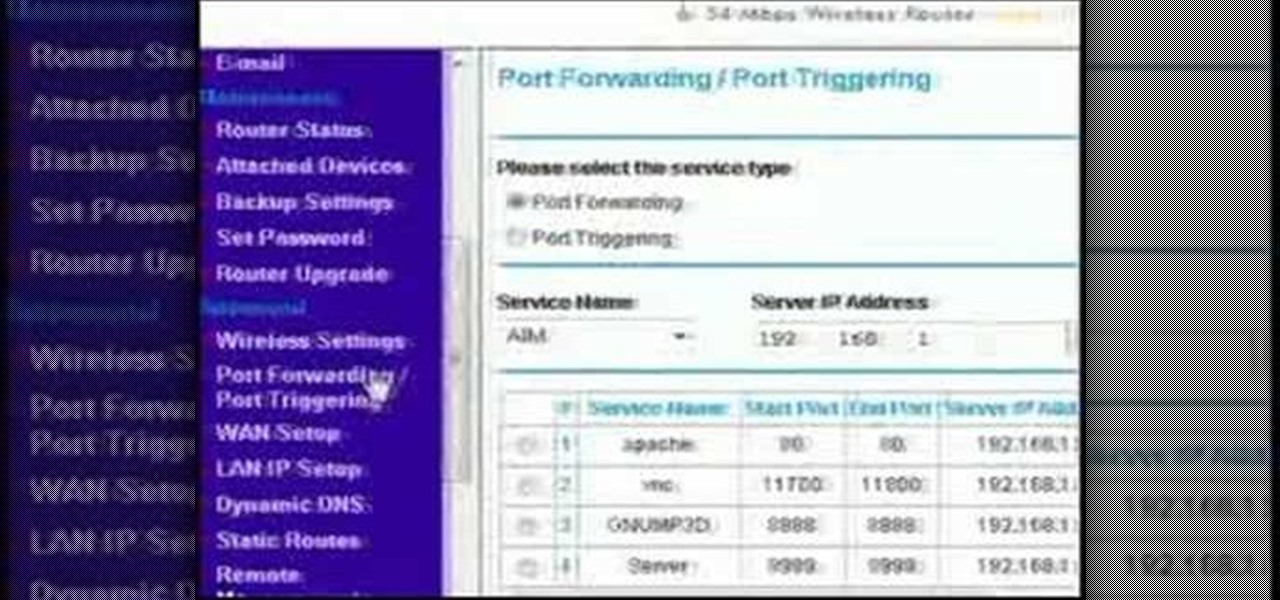
This video discusses how to bypass your router to access your server. In the search window type in CMD to open up a command prompt. Then type in ipconfig to bring up the ip configuration. You want to look for the ip address for the default gateway and the one for your computer. They should both start with 192.168. Once you find them open up internet explorer and type in the ip address for your default gateway and it should then prompt you for a user name and password. Log in and look for a po...

This tutorial will show you a super simple way to get free ringtones for your iPhone. This method will let you bypass iTunes's expensive ringtone service and create your own - anytime, from any song and for free!

In this how to video, you will learn how to draw a full moon. First, draw a large circle. Now fill the circle in with an orange color. Add shading with a darker shade of orange to create texture. Next, fill in the back of the moon with a black color. Make sure no white is showing. Next, a silhouette in front of the moon will be created. This is done by creating tree shapes in the bottom half of the moon in a black color. Fill in the outlines with black. Once this is done, your full moon image...

Your IP address is what identifies your personal computer while you are online. You may want to change your IP address for privacy, to bypass website settings, to download, or for various other reasons. This tutorial will take you through the steps you need to start surfing more anonymously.

This is an Apple iPhone video tutorial that will show you how to unlock an Apple iPhone 2G or 3G for use with another mobile phone service provider other that AT&T. If you are using a Macintosh computer, you can unlock both the 2G and the 3G phones. If you're using a PC, then you can only unlock the 3G iPhone.

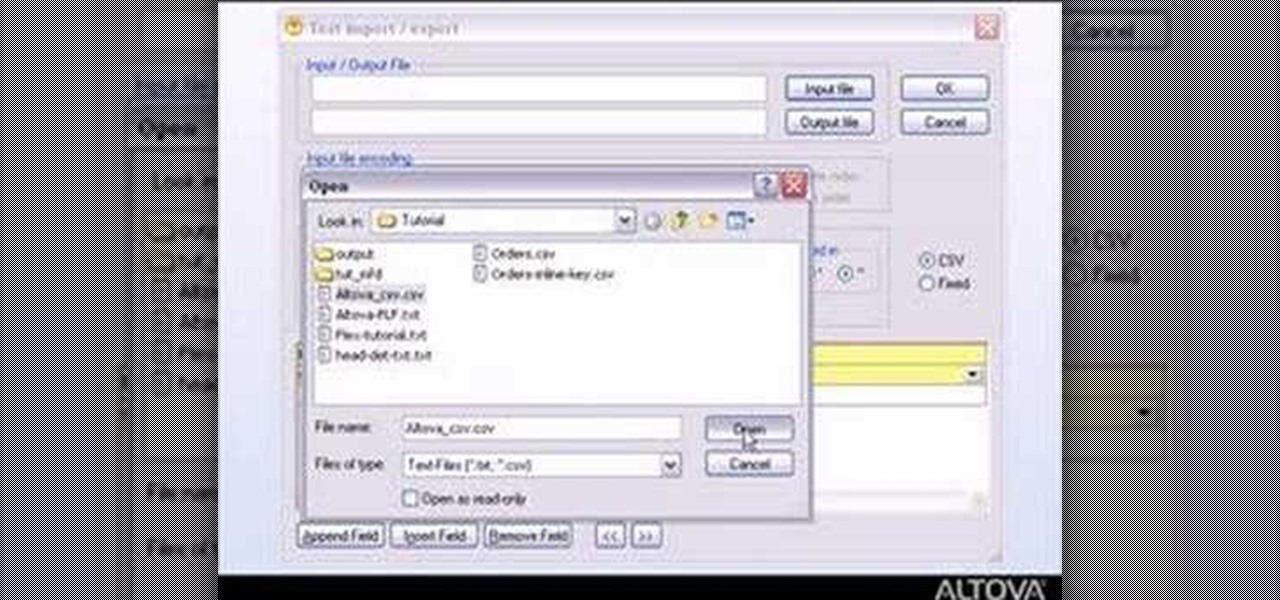
MapForce supports flat files as the source and/or target of any mapping involving XML, database, EDI, web services or other flat file data. In this how-to, you'll find instructions for mapping data from arbitrary text files (such as log files, CSV, fixed-width, and other legacy data sources) to databases and XML files.

The Prada cell phone (the LG KE850) is a unique, sophisticated and elegant mobile phone with the first complete advanced touch interface.

This tutorial teaches you how to get vibrato on the harmonica. This video also teaches you a few notes on getting a full acoustic tone. With the tips from this how to video you can get a rich tone on your harp.

Basil is full of nutrition and flavor. It can be a powerful part of a healthy diet. Basil is full of flavor and reduces the need for salt.

Watch this software video tutorial to learn how to control full-screen playback with keyboard commands in VLC Media Player. The tips in this how-to video will help you easily use VLC Media Player shortcuts to make full-screen playback more convenient.

Watch this how-to video to learn how to get 30 days of Xbox Live Gold for free just by pretending you don't want it. Xbox Live Gold is normally a subscription service, but you can get 30 days of it for free by following the tips in this how-to video.

In this how to video you can learn to create a punk, goth, emo red Avril Lavigne inspired eyeshadow look. This makeup tutorial uses the following products:

An installer shows some tips to help remove your trialer hub so it can be serviced and then reinstall it so your wheel can be remounted.

Learn how to develop great game habits on the basketball court with the help of this full court pressure defense drill.

Perform this advanced soccer ball handling move (Full Sole Rollover) by rolling completely over the ball before turning. This makes a great ball touch drill.

Just some suggestions and roughly the way I handle calls. There is more than one way to do this and every call is different. Enjoy!

How to do a full nelson escape using Jiu Jitsu.

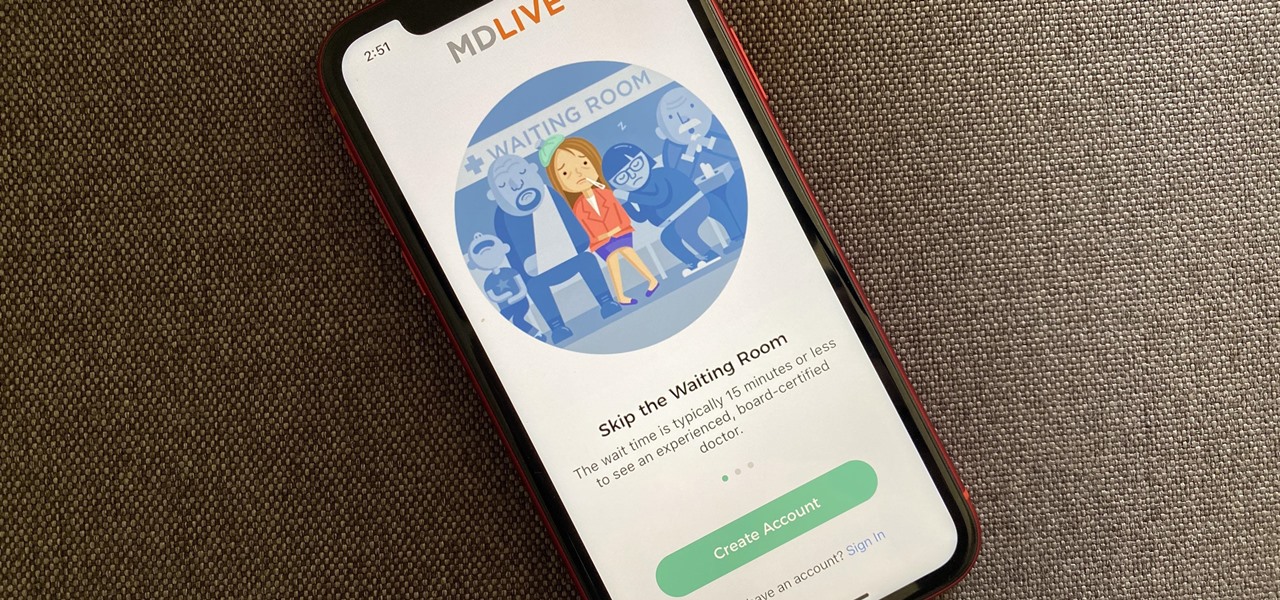
The World Health Organization has declared the new coronavirus a pandemic, and the Centers for Disease Control and Prevention recommends video visits with a healthcare professional to reduce the risk of being exposed to the coronavirus that causes COVID-19. If you are experiencing mild flu-like symptoms, virtual doctor visits may also prevent you from endangering others.

We've all seen the login pages that allow you to log in to third-party accounts using your credentials from Facebook, Google, or Twitter. It saves you the trouble of creating another account and remembering more passwords — but it can also become a privacy and security issue, which is why Apple created the "Sign in with Apple" feature for iOS 13.

There are a number of reasons you'd want to delete your Skype account. You may have decided to move away from the app in favor of another service like WhatsApp or FaceTime, or perhaps you want to erase your account due to an online hack. Regardless of why you might want to delete your Skype account, doing so isn't quite as straightforward as it appears.

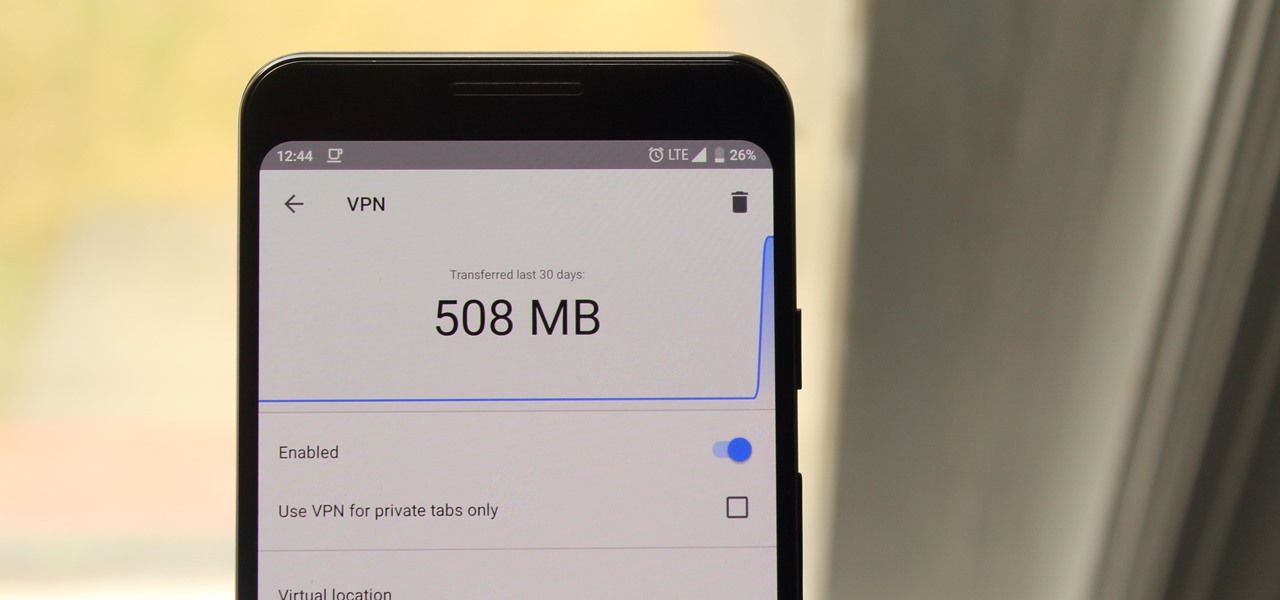
Browsing the web can be dangerous. With all of the various threats out there, it isn't enough to just avoid bad links and visit only HTTPS websites. You need to take advantage of the tools available to you so you don't end up the victim of some scam. Fortunately, Opera is making this a bit easier.

AMC Theatres was never a fan of MoviePass and even predicted its unsustainability. After the struggling MoviePass turned off diehard fans with too many new restrictions to combat its cash problems, AMC stepped in to save the day with its AMC Stubs A-List subscription for cheaper movie tickets.

When OnePlus announced their partnership with T-Mobile and the deal the magenta carrier is set to offer, mouths dropped. But as usual, this deal comes with some caveats. The bulk of these will hurt the folks who love to root, something a large portion of the OnePlus community enjoys doing.

A new augmented reality cloud platform from German startup Visualix is working to give enterprises the capability to scan their own warehouses, factories, and stores and create maps for augmented reality navigation.

Thanks to recent reports, we now know third-party apps have a lot more access to our Gmail than we may have initially thought. In fact, these third-party apps have the ability to read our emails, not because these companies are necessarily shady, but because we agreed to it. Luckily, there's a way to view which apps have this access, as well as a way to boot those apps from your Gmail entirely.

Hackers rely on good data to be able to pull off an attack, and reconnaissance is the stage of the hack in which they must learn as much as they can to devise a plan of action. Technical details are a critical component of this picture, and with OSINT tools like Maltego, a single domain name is everything you need to fingerprint the tech details of an organization from IP address to AS number.

Kali Linux is established as the go-to operating system for penetration testing, but in its default configuration, it's less than ideal for regular desktop use. While in many scenarios, a live boot or virtual environment can resolve these issues, in some situations, a full installation is better. A few simple changes can be made to a Kali Linux desktop to make it safer to use in this environment.

The cosmetics industry faced a rude awakening on Friday as beauty behemoth L'Oréal gobbled up ModiFace, one of the leading providers of augmented reality technology to the cosmetics industry (price details for the acquisition were not disclosed).