In our society, multitasking is an obsession. Whether it's driving while using your phone (DON'T DO IT) or drinking a cup of coffee while typing up some work, we multitask at every turn of the day. People that work all day in front of a computer are especially prone to multitasking, and that's why XDA-Developers member Floyd1973 has developed a way to control any Android phone while connected via USB to a Windows or Linux PC. Android Remote Phone Tools

Among its many new features, Android P returns the spirit of lock screen widgets to users by presenting the current temperature and weather conditions underneath the clock. It isn't flashy, but it's a fun and useful addition that, unfortunately, does not always work. If your lock screen weather isn't showing up, you might want to try these steps to fix it.

Intense exercise can cause problems with our digestive tract. It even has a name — "Exercise-induced Gastrointestinal Syndrome." Simply put, strenuous exercise can damage the gut and let the bacteria that reside there potentially pass into the bloodstream.
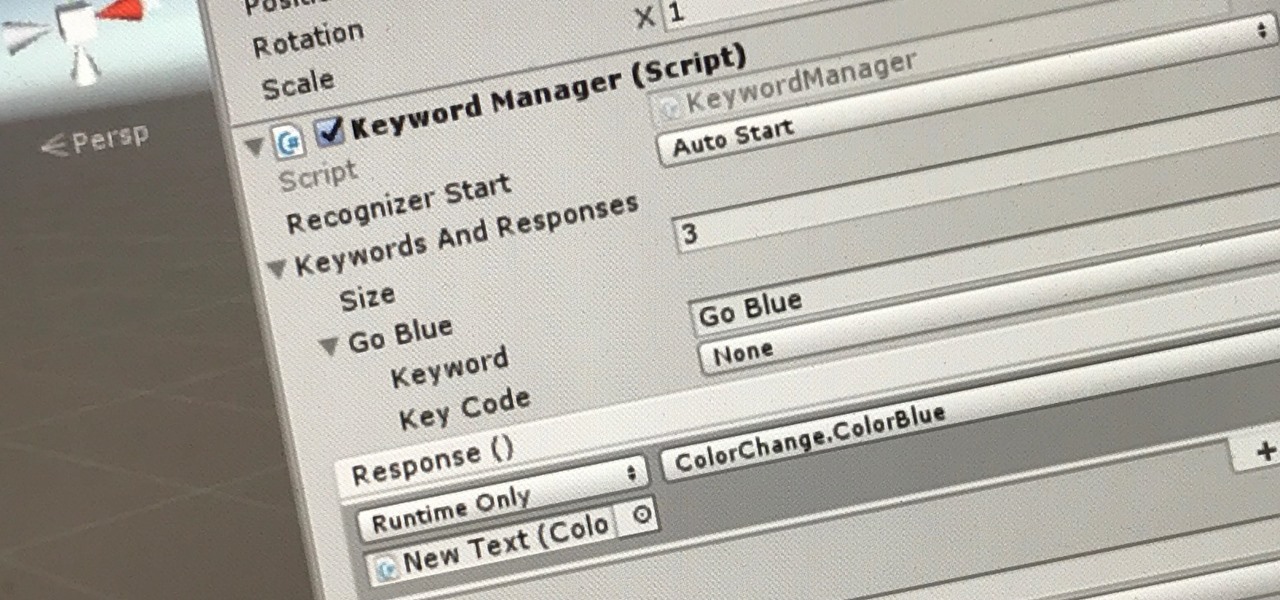
The HoloToolkit offers a great many, simple ways to add what seems like extremely complex features of the HoloLens, but it can be a bit tricky if you're new to Windows Holographic. So this will be the first in an ongoing series designed to help new developers understand what exactly we can do with the HoloLens, and we'll start with voice commands.

How is it goin', fellow 1337 haXX0rZ! dtm here with another article, this time, we'll be looking at infecting PE files, executables in particular for this write-up. Obviously some prerequisite knowledge will be needed since this isn't really newbie-friendly. If you are still a beginner, fear not, it might still be interesting to read! Hopefully!

Welcome to a tutorial on XOR encryption. We'll be looking at what XOR is and how we can use it to encrypt or decrypt data.

In this article, we will build a parallel password cracker using the techniques explained in the previous part. As SHA-512 is the digest function that Kali (and most modern Linux distributions) use to store our passwords, we will make a SHA-512 password cracker.

Welcome back, my budding hackers! When we are looking for ways to hack a system, we need a specific exploit to take advantage of a certain vulnerability in the operating system, service, or application. Although I have shown you multiple ways to exploit systems here in Null Byte, there are still many more exploits available that I have not yet shown you.

One of the best things about the Samsung Galaxy S3 is the ability to modify the device in countless ways, as with any other Android device.

With the Wigle WiFi app running on an Android phone, a hacker can discover and map any nearby network, including those created by printers and other insecure devices. The default tools to analyze the resulting data can fall short of what a hacker needs, but by importing wardriving data into Jupyter Notebook, we can map all Wi-Fi devices we encounter and slice through the data with ease.

Using a strong password is critical to the security of your online accounts. However, according to Dashlane, US users hold an average of 130 different accounts. Memorizing strong passwords for that many accounts is impractical. Fortunately, password managers solve the problem.

Many popular IoT devices have terrible security. For instance, a hacker who's on the same Wi-Fi network as a Sonos speaker can assume direct control over the device's behavior. If an IoT device doesn't secure the messages used to control it over a network, it's easy for somebody to write a few Python scripts to make it do whatever they want.

Being able to write your own hacking tools is what separates the script kiddies from the legendary hackers. While this can take many forms, one of the most coveted skills in hacking is the ability to dig through the binary files of a program and identify vulnerabilities at the lowest level. This is referred to as binary exploitation, and today we're going to check out a tool known as Protostar.

An attacker with shell access to a Linux server can manipulate, or perhaps even ruin, anything they have access to. While many more subtle attacks could provide significant value to a hacker, most attacks also leave traces. These traces, of course, can also be manipulated and avoided through methods such as shell scripting.

Black Mirror, Netflix's technology-horror anthology, never fails to provide thought-provoking entertainment centered around emerging and futuristic technologies, and the third season's second episode, "Playtest," delves deep into the worlds of mixed, augmented, and virtual reality. While designed to leave you haunted by the end, offering a more "evil" narrative than we'll likely see in our actual future, the episode explores possibilities that aren't as far off as one might think.

In this tutorial, we learn how to use height change in tango. This will combine many elements of tango to change height deliberately for function and style. You do not want to change your weight and height without knowing it, because it can change how you dance and make it look completely different. Pay attention to your body and how your feet are placed on the ground. If your body weight is shifted too much to one foot it can change how you are dancing and the height of your overall self. Us...

In this how-to video, you will learn how to embed a social or fund raising widget on to your Facebook page. Look for static fbml on the Facebook search function. Click on it and add to page. Next, press add static fbml. Now you are finished. Go to edit page and click edit on the application. Now you can embed whichever code you need to paste into your Facebook page. Do not worry about what the code does, as you do not need to know it in order for it to work. Save the changes and go back to th...

Leeann of Hierchiss explains how to turn a TV into an oscilloscope. Turn the TV on and make sure it works. First, unplug the power. Take the back off the television. Cut the four picture wires that attach to the circuit board. Strip the ends of the wires. Tape the remaining wires off to prevent short circuiting. Clamp the red and yellow wires and attach to a 1/4 inch jack which feeds into a tape player. Repeat the same process for the green and blue wires. Plug in the TV to make sure the conn...

Have some files you don’t want anyone to see? Or maybe it’s just been a while since you’ve emptied your trash bin. The trash bin function is not a permanent delete but you can erase files off your Mac with this tutorial.

In this video you'll learn how to make an easy and delicious home made cheesecake topped with some fresh kiwi slices. Easy and quick to eat for you and the entire family. This is a perfect desert to make for the next family function for everyone to enjoy. It's also to cook for those of you on a budget.

This innovative handset makes user convenience its priority. Created with the aim of overcoming the limitations of existing mobile phones, every function is available through a flexible layout of navigation keys. Fixed keypads are a thing of the past with the LG KF600 Venus cell phone.

Like all appliances, the oven has a tendency to get dirty inside. Unfortunately, unlike most appliances, the oven is extremely difficult to clean out. Many ovens have a clean selection that will burn off all the excess items in there, but even those left over ashes can sometimes be difficult to wipe away. If your oven does not have the clean function, the method most people use is to clean it out with an oven cleaner. It will most likely consist of spraying the cleaner on all dirty parts of t...

Here is a three part video series which explains the function and parts of constructed stilts, and how to turn them into werewolf stilts by adding fur and padding for your comfort! Make sure to check out the mask - Make a furry werewolf mask!

Hashes are commonly used to store sensitive information like credentials to avoid storing them in plaintext. With tools like Hashcat, it's possible to crack these hashes, but only if we know the algorithm used to generate the hash. Using a tool called hash-identifier, we can easily fingerprint any hashes to discover the right Hashcat mode to use to retrieve a password.

Web 2.0 technology has provided a convenient way to post videos online, keep up with old friends on social media, and even bank from the comfort of your web browser. But when applications are poorly designed or incorrectly configured, certain flaws can be exploited. One such flaw, known as CSRF, allows an attacker to use a legitimate user's session to execute unauthorized requests to the server.

For the second time in a row, Apple pushed out a new iOS 12 developer beta on a Monday, and for the first time this round, they've done it only one week after the last one. While the August 6 release of iOS 12 developer beta 6 doesn't contain a wealth of updates, there are still a few things you'll want to know about.

One of the most critical bugs to come out in the last five years was Shellshock, a vulnerability which allows attackers to execute arbitrary code via the Unix Bash shell remotely. This vulnerability has been around for a while now, but due to the ubiquity of Unix machines connected to the web, Shellshock is still a very real threat, especially for unpatched systems.

One of the primary factors that separates an augmented reality device from a standard heads-up display such as Google Glass is dimensional depth perception. This can be created by either RGB cameras, infrared depth cameras, or both, depending on the level of accuracy you're aiming for.

Over the years, the internet has become a dangerous place. As its popularity has increased, it has attracted more hackers looking to make a quick buck. However, as our dependency on the web grows, it becomes increasingly difficult to sever all ties. This means we have to protect one of our weakest points, the password.

M — Facebook's AI-powered assistant unveiled to the public in April — is now better than ever. The latest update to M now allows it to provide three more suggestions: a function to save content to view later, birthday wishes, and call initiation.

Most people are familiar with the decline of honeybee colonies around the world. Among other threats, Colony Collapse Disorder (CCD) is eroding the capability of honeybees to maintain their hives and provide their services to human farmers.

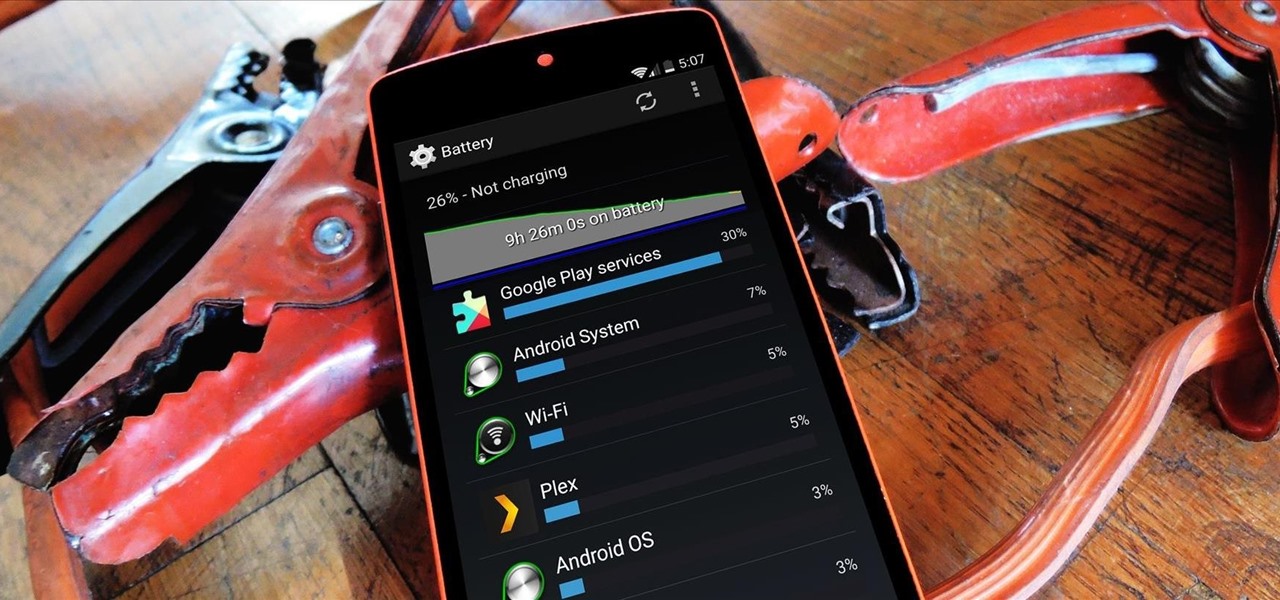
No matter how far technology advances, battery life continues to be an issue. Powerful new hardware is introduced each year, but smartphone batteries only get a few extra milliamp-hours to compensate.

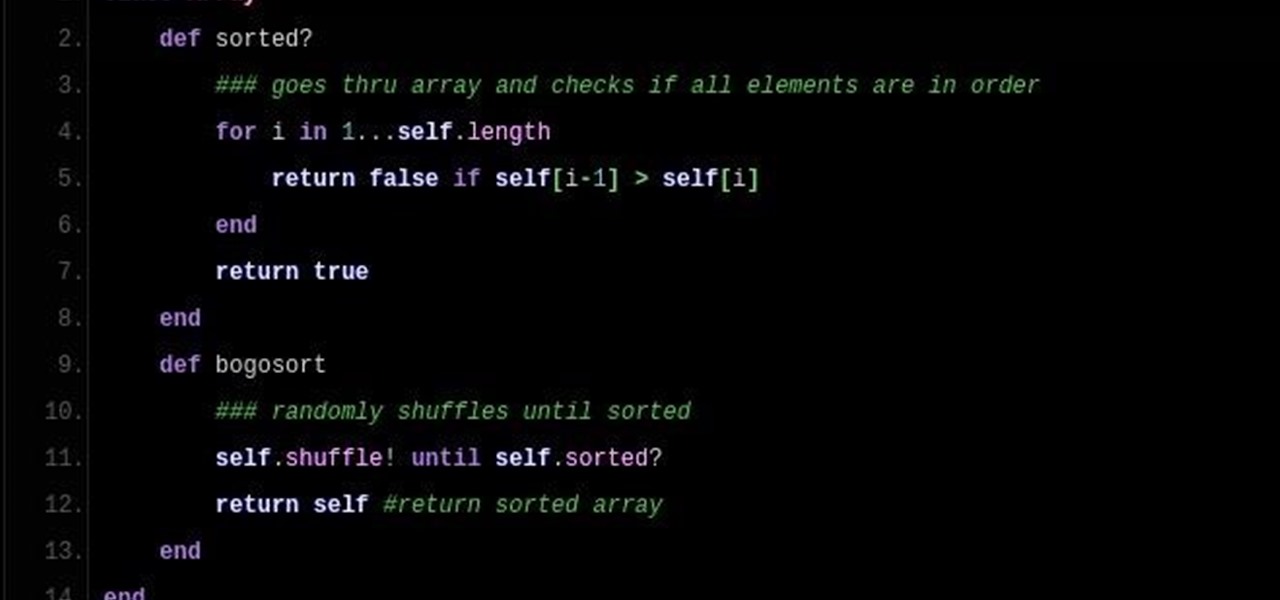
So DTM insisted I write up a little article on Bogo Sort. What Is Bogo Sort?

Hello aspiring hackers, It's been a while since I wrote a tutorial, so I figured I might just share one of the tools that I have created to help the community grow.

What's up, peeps? In this quick tutorial, we will be looking at structs, a special kind of data type.

In general, smartphones and cars don't mix—but this is mainly because you have to take your eyes off the road to poke around on your handheld gadget. In reality, the only difference between your smartphone and your car's FHWA-approved infotainment system is that the latter is mounted in a fixed position and has an oversized interface that makes it easy to use without looking away from the road.

The world's most commonly-used desktop operating system is getting a huge makeover in the form of Windows 10. While there are many sweeping changes in this new version, some of the smaller tweaks may prove to be the most useful.

Do you remember the last time we used BeEF? Well, now we get to use it again, but this time with MITMf! We are going to auto-inject the hooking script into every webpage the victim visits!

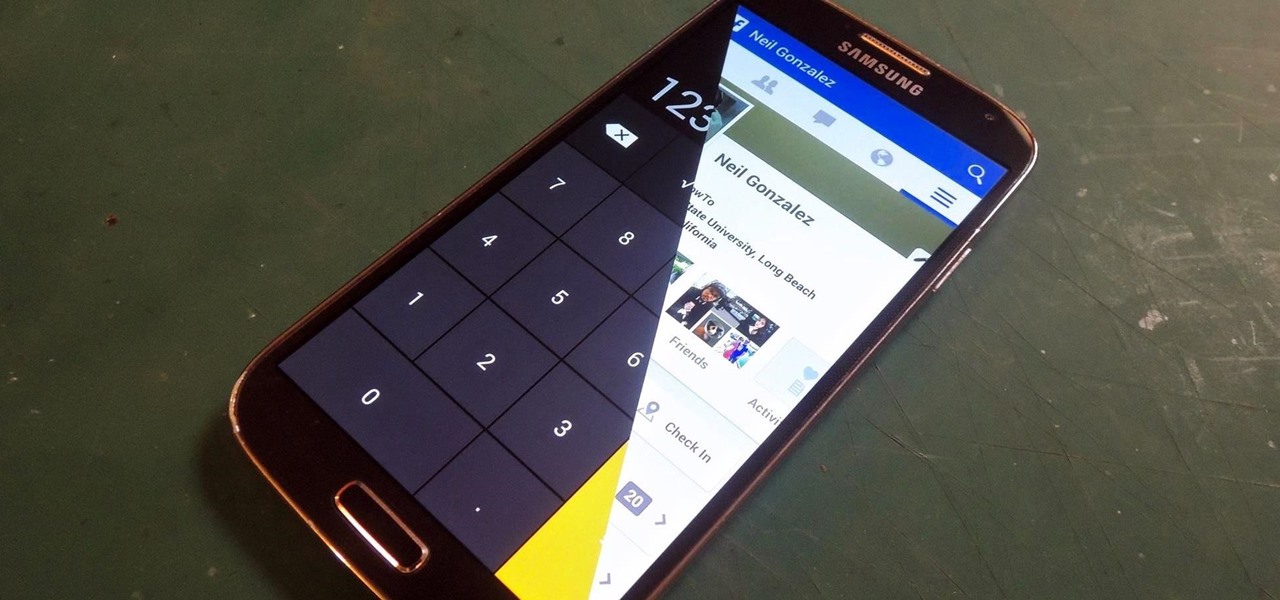
Trust can be a touchy subject in general, and is often required when sharing personal information—especially so when handing our phones over to others. You may not have a ton of secret or nefarious information on your device, but that doesn't mean you want your mom or snoopy coworker having easy access to your messages or Facebook app.

An app can request a wakelock to prevent your Android device from entering sleep mode so that it can sync data in the background. This obviously drains your battery, because instead of running in low-power sleep mode, your processor is fully activated while it performs its tasks.