
How To: Make Your Remote Screenshot Captor(Python)
Hi I am a new member of null byte(although I am reading this website from the beginning) and this is going to be my first post.


Hi I am a new member of null byte(although I am reading this website from the beginning) and this is going to be my first post.

Welcome back everyone. I apologize for the lack of training articles, but I've been rater busy lately. I've recently picked up a second job and my college courses are now back in session, so I'm a bit strapped for time.
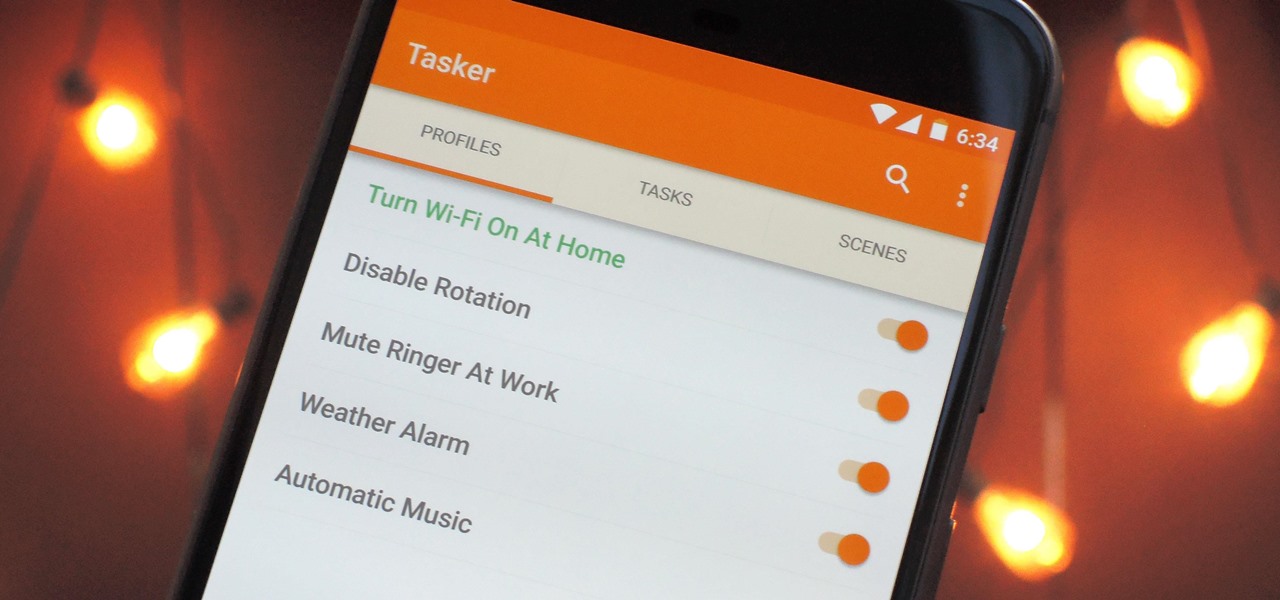
When it comes to automation apps on Android, Tasker is still the king of the hill. For a price of $2.99 on the Google Play Store, it's a great buy for any would-be tinkerer that would like to get into automating actions on their Android device. Then, when you consider that there's a free 7-day trial version available, there's almost no reason that you shouldn't at least test the waters with Tasker.

For SQL injection, the next step after performing reconnaissance and gathering information about a database is launching an attack. But something seems off .. in the real world, it's usually not quite as simple as passing in a few fragments of SQL code to an input field and seeing all that glorious data displayed right in the browser. This is when more advanced techniques are needed.

German groups ZF Friedrichshafen AG and HELLA are collaborating to add to their autonomous portfolios with camera and radar development.
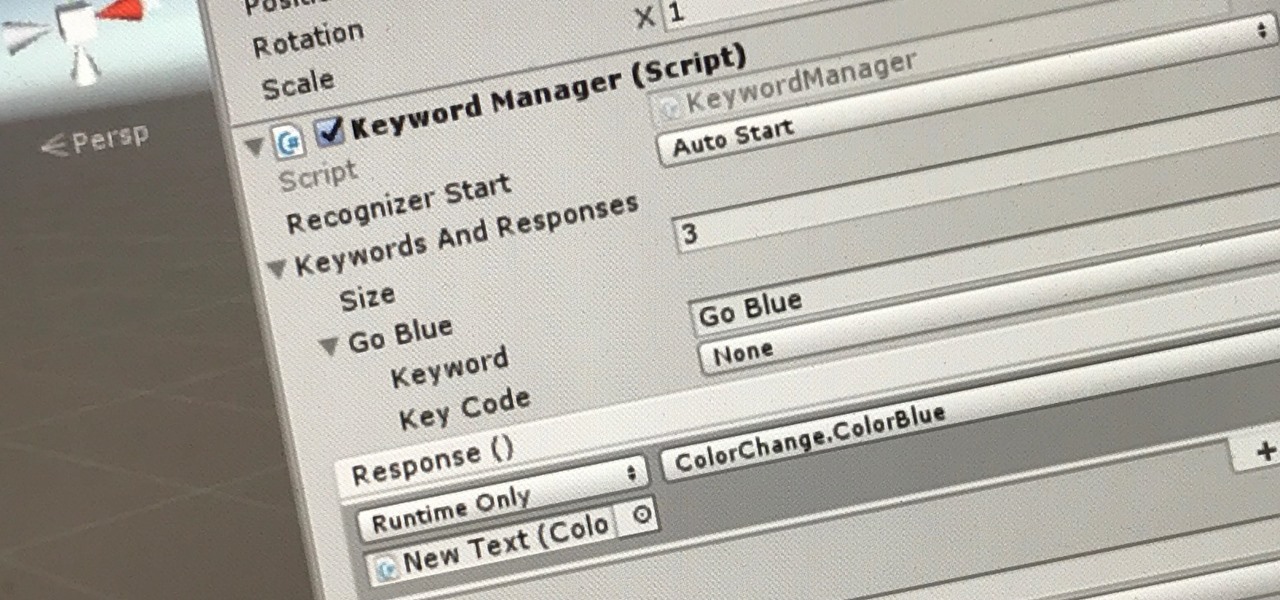
The HoloToolkit offers a great many, simple ways to add what seems like extremely complex features of the HoloLens, but it can be a bit tricky if you're new to Windows Holographic. So this will be the first in an ongoing series designed to help new developers understand what exactly we can do with the HoloLens, and we'll start with voice commands.

The Moto X and Moto Z have a set of features that let you launch common shortcuts by shaking your phone in one direction or another. For instance, there's a chop gesture that turns on the LED flashlight, and a wrist-twist gesture that instantly opens the camera app.

Hey readers! This tutorial will be the entry point for the introduction of buffer overflows. Something like requesting user input is a very common place for vulnerabilities to pop up and we will definitely have fun while trying to make programs crash. But for now, let's start with how we can get input from a user.

What Is IPython? IPython is a richly featured replacement for the standard python interpreter. It offers a wider range of functionality, that the standard

Lock screen apps are a dime a dozen, but every now and then one pops up that defies expectations. We've already covered some good ones for the Samsung Galaxy S4, including Picture Password Lockscreen (which gives you secret unlock gestures), SlideLock (which improves notifications), and TimePIN (which gives you a more clever PIN).
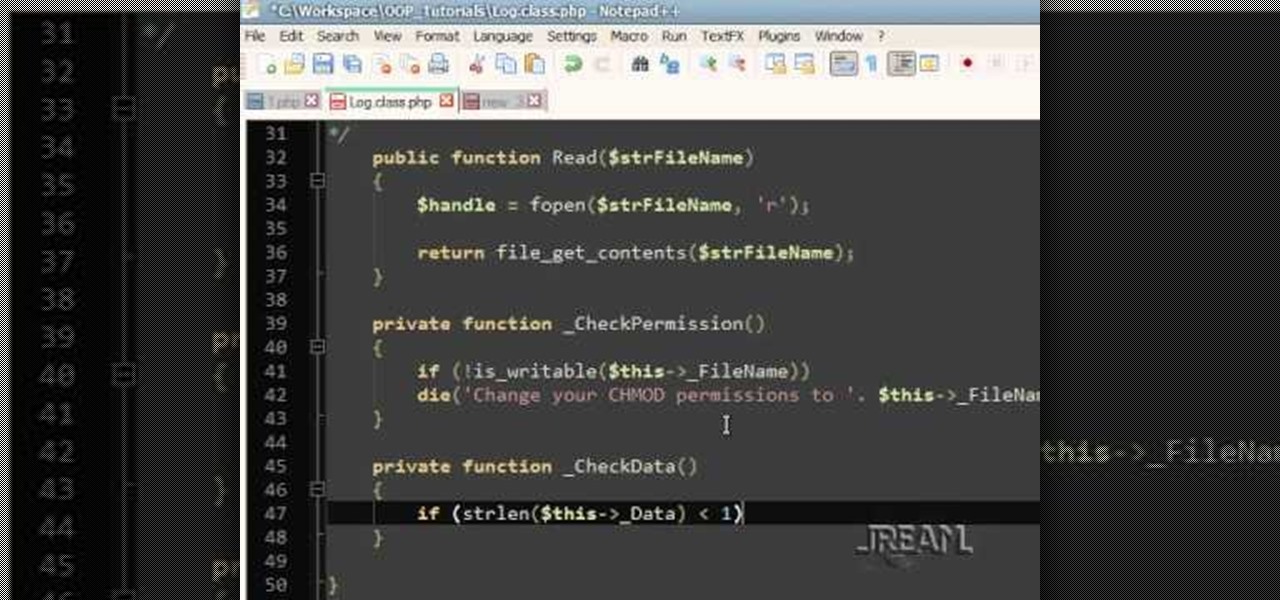
In this tutorial, learn to setup private properties(variables) and private methods(functions) with your PHP OOP programming. This tutorial will have the file logger run through some private methods. Check it out and open the door to the world of PHP programming.
In this clip, you'll learn how to get navigate and use the basic features and functions of the Symantec Altiris Client Management Suite. It's easy! So easy, in fact, that this helpful how-to can present a complete overview of the app in just over three minutes. For more information, including detailed, step-by-step instructions, take a look.

This tutorial shows you how a stylus pen and graphics tablet (such as the Wacom tablet) can be used to interface with the various features and functions of Mudbox 2009. Use your pen and tablet to create 3-D imagery and models in Mudbox 2009!

It is possible to convert your Excel spreadsheets into a PDF file by using your PC's Print Manager and Save As functions. This video shows you a step by step to create a password-protected PDF version of your Excel file.

Need some help figuring out how to use the Talking Tom Cat app on your Apple iPhone? This video tutorial presents an overview of the app's essential functions and features. For more information, including detailed, step-by-step instructions, and to get started using Talking Tom Cat on your own Apple iPhone 3G, 3GS, 4 or iPod Touch, take a look.

Learn how to utilize the empty expansion slots to add new functions and features to a Windows or Linux PC. This brief video tutorial from the folks at Butterscotch will teach you everything you need to know. For more information, including detailed, step-by-step instructions, and to get started understanding and using hardware expansion slots yourself, take a look.
In this clip, you'll learn how to create Navi'i-style eyes (with special attention paid to the irises and pupils) with Adobe Photoshop CS5. Whether you're new to Adobe's popular raster graphics editor or a seasoned designer looking to better acquaint yourself with the new features and functions of the latest iteration of the application, you're sure to benefit from this free software tutorial. For more information, watch this video guide.

Want to create a photo effect reminiscent of the film 300 in Adobe Photoshop? This clip will walk you through the process. Whether you're new to Adobe's popular raster graphics editor or a seasoned designer looking to better acquaint yourself with the new features and functions of the latest iteration of the application, you're sure to benefit from this free software tutorial. For more information, watch this video guide.

In this clip, you'll learn how to create a simple image overlay effect for title text and headers in Adobe Photoshop CS4 or CS5. Whether you're new to Adobe's popular raster graphics editor or a seasoned designer looking to better acquaint yourself with the new features and functions of the latest iteration of the application, you're sure to benefit from this free software tutorial. For more information, watch this video guide.

Masking and keying are two of the more basic and important functions of Adobe After Effects. This video will teach you how to use them quickly and easily, using a little Counter Strike video as an example. There is no narration, but the material is simple enough that you should still be able to follow along.

Droid Wizard gives a basic tuturial of sending a text message on the Motorola Droid. The video shows how to access the text message functions on the Multi-touch.

This video tutorial takes a look at the cut, copy and paste functions and how to use them on a Windows PC. If you don't know how to use the cut, copy and paste tools, you'd be well served to take a look. Get started using cut, copy & paste with this how-to!

This video card making tutorial shows how to make a name placard, great for social functions. Also demonstrated are how to use a Cuttlebug embossing machine and how to replicate the stamp kissing technique. Watch this instructional video and learn how to make a name card placard.

A cow's tail might be in the way of a variety of veterinary procedures or other practical functions. In order to get the tail out of the way, the cow's tail may be tied. Learn how to tie a cow's tail for surgical or any purpose without hurting the cow or damaging the bones by watching this video veterinary tutorial.

Sandblasting has a bunch of functions. It can be used to soften rough surfaces, roughen soft surfaces, take off unwanted surfaces, or shape a surface. If you're curious about the process and wish to try it yourself, you can check out this video to learn how to sandblast glass with experts at the Corning Museum of Glass.

Learn how to use the iStore (the iTunes WiFi music store) functions on the new iPod touch.

You may be surprised to learn that your vegetable peeler can serve many functions - this video will show you.

Cells in Numbers '08 are the same as in Excel. Basically, they are where you store your data. This tutorial will show you how to use the different functions of cells.

Pages '08 actually functions as more than a word processor because it has a page layout mode that helps make brochures, posters, flyers and other projects that need layouts.

Whether your palate runs to domestic or imported, a piece of cheese can be a real treat for the senses. Its smell, taste, and texture are all parts of its appeal. A big part of what makes that savory wonderfulness comes from the microbes in and on the cheese. Thanks to a team of researchers dedicated to studying those microbes, we have a better understanding of their importance to cheese and us.

The Cloud Security Alliance (CSA), a leading IT trade association, has published its first report on risks and recommendations for connected-vehicle security, ahead of when driverless cars are about to see volume production in the near future.

If you read my article on the OSI model, you got a good overview on communications from that model's perspective, but how does that relate to TCP/IP? We're going to take it a step further, getting into the idea behind the two address concept. How does an IP address and a MAC address work together? If you want to hijack sessions and all sorts of lulz like that, you need to understand these concepts. Let's get into it, mates!

Today's post is a small go-to guide for beginner programmers in Null Byte. With many of our community members picking up programming from our Community Bytes, it only makes sense to lay out a one-stop guide for your reference. Hopefully this guide will help you make an educated and thoughtful choice on what programming languages you want to learn, and how you want to learn said languages.

Step 1: What Exploit Development Is and Why Should I Be Interested on About This Topic
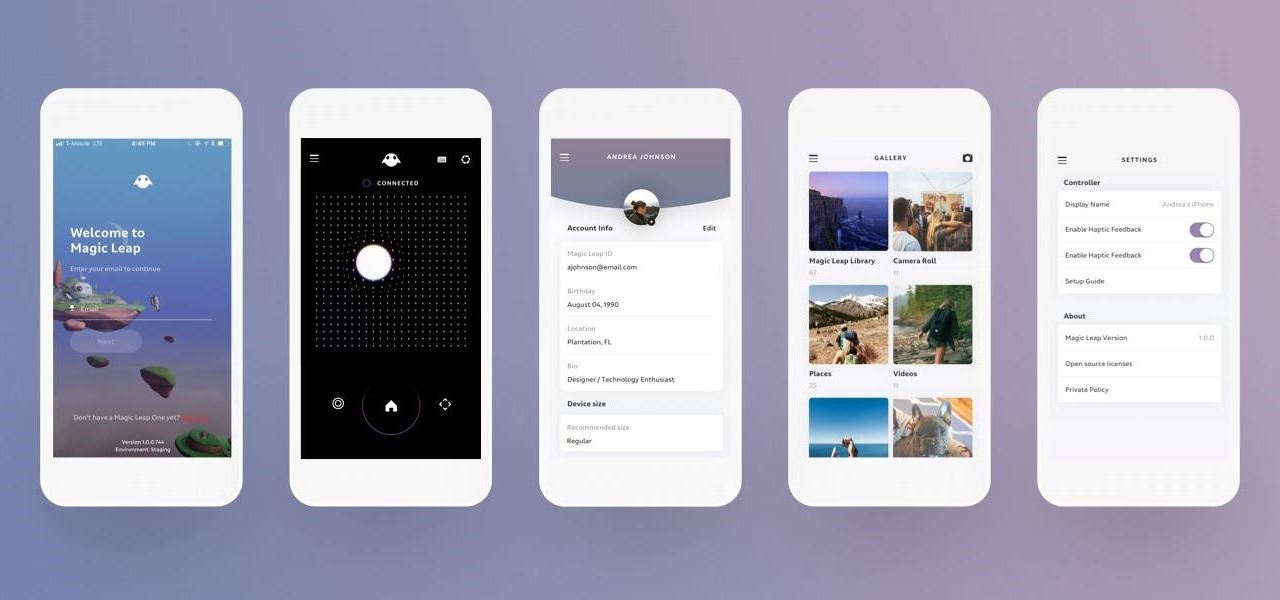
Among a treasure trove of new developer information on the Lumin OS that Magic Leap recently published on its Creator Portal appears to be the official confirmation of the Magic Leap Mobile Companion App.

Koadic allows hackers to monitor and control exploited Windows systems remotely. The tool facilitates remote access to Windows devices via the Windows Script Host, working with practically every version of Windows. Koadic is capable of sitting entirely in memory to evade detection and is able to cryptographically secure its own web command-and-control communications.

The rumors have been confirmed by Samsung themselves: Samsung has developed a virtual assistant of their own, named Bixby.

Welcome to the final tutorial of the series on standard C. This article will cover the linked list abstract data type (ADT). There will be a lot of abstraction to try to deliver the understanding in the most basic way for easiest interpretation of what they are and how they work, then we will get into the guts of it and learn the technical code underneath. For those who have yet to grasp the concept of pointers, it's advisable that you do that first before approaching this. Having learned thi...
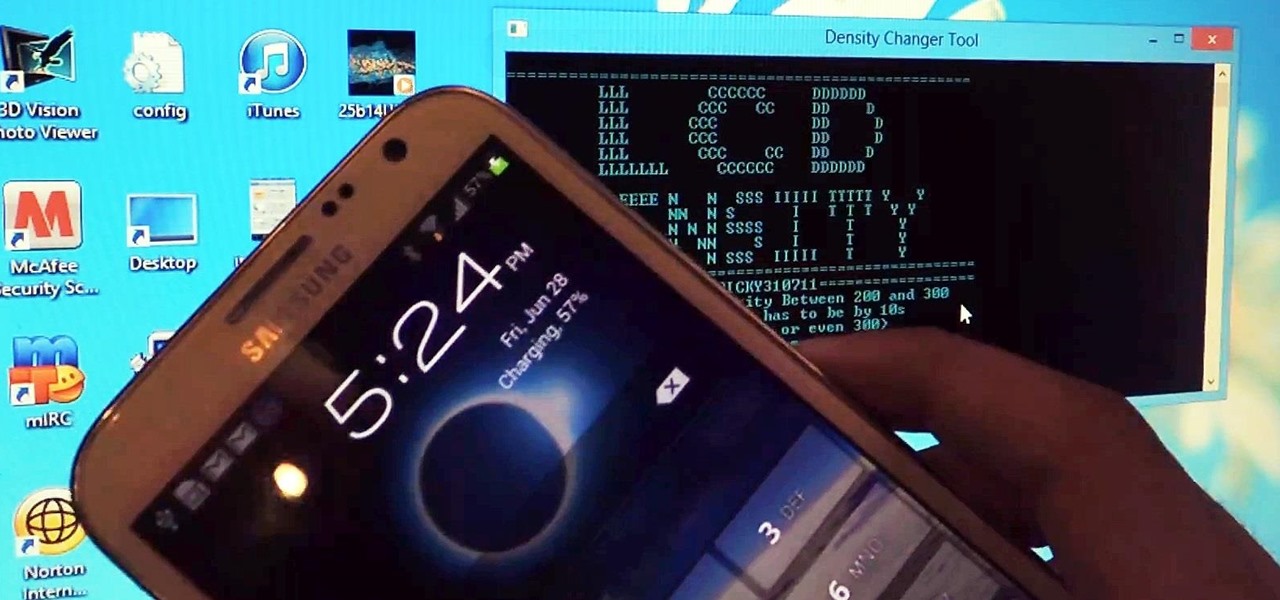
There are a ton of cool features available on your Samsung Galaxy Note 2, but if you're a softModder, you can make your phone do just about anything.

IFTTT (short for If This, Then That) is an amazing piece of software that automagically links actions on your phone with online services and real-world objects. For example, an applet could read: "if you come home, then turn on Wi-Fi." IFTTT goes further than just using simple smartphone functions, though — thanks to applets, it's fully configurable with a ton of smartphone apps.