
News: New Ultra-Realistic Android Scares the Crap Out of Everybody
Holy… Lord, help us all—this isn't CG, it's for real. Meet Geminoid DK, the latest spawn from Osaka University Professor Hiroshi Ishiguro's legion of ultra-realistic Androids.


Holy… Lord, help us all—this isn't CG, it's for real. Meet Geminoid DK, the latest spawn from Osaka University Professor Hiroshi Ishiguro's legion of ultra-realistic Androids.

Inception may not be the lead contender for the 68th Golden Globe Awards, honoring the best movies and television from 2010, but Christopher Nolan's film still collected four nominations— Best Motion Picture, Best Director, Best Screenplay and Best Original Score.

This Japanese expression has two basic meanings. The literal meaning is to break one’s bone(s), as when falling from a height. The figurative meaning is “to try harder.” That is, to try so hard that one’s bones break.

Google has caught a lot of flack for various privacy infringements over time. Google Buzz was the latest uproar, when lack of proper prior testing allowed the tool to expose a slew of information users did not necessarily want shared, resulting in massive complaints. A Harvard student even went so far as to file a lawsuit (read more).

This collection of instructional videos from BaseballRox with Max Luckhurst will help you develop your outfield mechanics with cutoffs and relays in the sport of baseball. These baseball videos are aimed to help young players and coaches improve their performance on the field. See how to practice outfielder's cutoffs and relays in baseball.
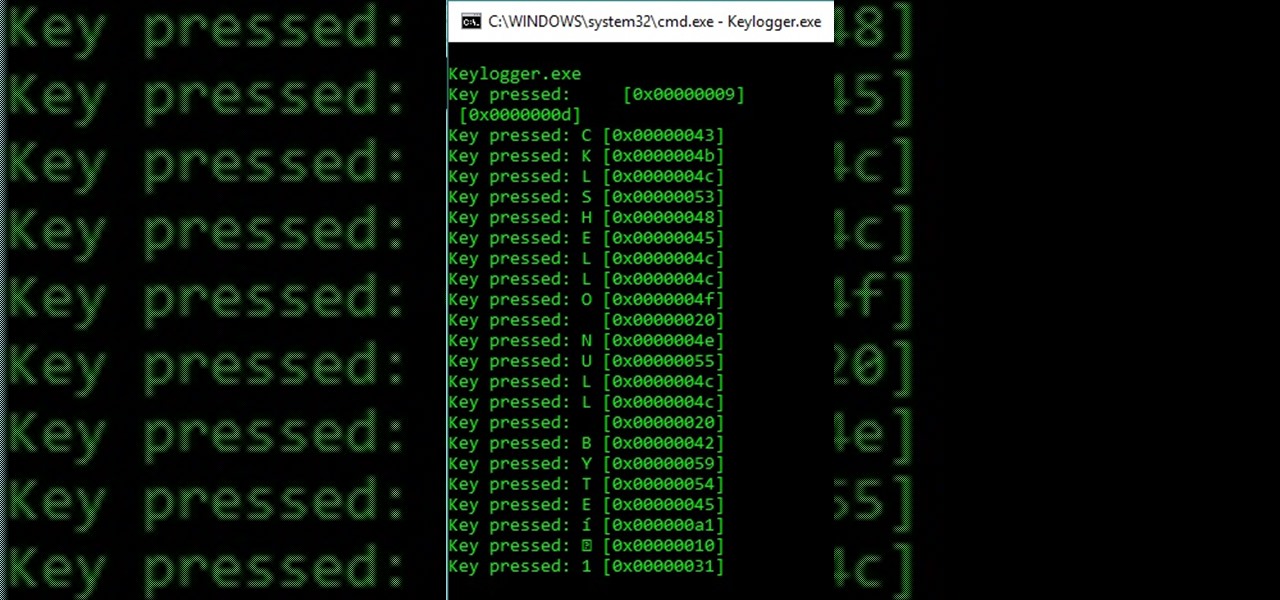
Yo yo yo, what's goin' on my devilish fiends? Have you come here to learn how to make a keylogger for malicious intent? You sly fox! But in all seriousness, this article will cover quite a simple method for creating the most basic of Windows keyloggers. You're in for a surprise! Let's dive right in!

Artist Marshall Astor has made a fully functional Rubik's Cube out of bronze. What? No differentiated, colored sides? How do you play? Apparently there's reasoning behind it. Astor gets deep:

Following in the footsteps of great historical figures is a great way to learn about them. Michael Wood famously did so in the 1980's for his PBS documentary and book In The Footsteps of Alexander The Great. This March, UK-based marketing director Chris Worth completed a similar endeavor—not by tracing the path of a real-life emperor or explorer, but a humble video game character. One known simply as "The Courier".

It's tough to figure out what a mummy would have looked like when he was alive; soft tissue of a human body decays, even in ice. But, Dutch brothers Adrie and Alfons Kennis took the challenge. Using techniques that belong to both science and art, they managed to reconstruct the face and body of Otzi the Iceman, a mummy who was found in the Italian Alps in 1991.

The classic Super Mario Bros is perhaps the most beloved video game on Earth. Almost daily, homages to Mario pop up on the web over and over and over again. Everybody loves the charming 2D world of Mario. But what would Mario look like in 3D… and moreover, what would Super Mario feel like as a First Person Shooter game?

This is the first of two Video's introducing you to your fingers from a Hand Analysis perspective. The Fingers mainly govern the mind and thinking. Somewhere in the vast fabric of time somebody discovered that the length and inclination of each particular finger can bring out certain personality traits. I still find it amazing and satisfying to see somebody with a longer than average 'little finger'(Mercury-communication), that sticks out that can't stop talking and buzzing around all excited...

Remember the firestorm SCRABBLE Trickster caused nine months ago? SCRABBLE enthusiasts across the world were outraged when Mattel created a game that would allow proper nouns to be acceptable words of play. Essentially, it was a dumbed down, youth-friendly version of the classic game they've all come to love. Luckily, it was just a spinoff game—not a replacement. The same can't be said of the new edition of Collins Official SCRABBLE Words.

I took a class in the fall entitled Writing for Television at Bentley University in Boston. Much of what I learned has helped me through my first year of creative writing. One of the keys to writing television that we learned in the class was that a television show follows the traditional three act structure that any story follows, except for the fact that in a television episode, many questions are allowed to go unanswered.

According to Wikipedia, to be called "the Stradivari" of any field is to be deemed the finest there is...

US can legally kill Americans in terror groups You read it right. The US can now target Americans who are supposedly part of terrorist groups. Here's my analysis of Attorney General Eric Holder points (keep in mind though, these are point's brought up by MSNBC, original article here):

Search engine optimization (SEO) is now one of the most important topics for website owners to understand. Anyone that depends on their website to bring them business needs to know the ins and outs of SEO in order to maximize their website’s potential. And if you want your website to have a high Google rank then SEO is essential.

Mobile devices can do just about anything these days, thanks to third-party developers. iPhones and Android devices have been known to do some pretty wild things. Need a dupe key made? Scan and order one with your iPhone. Want to know if you're hotter than Justin Bieber? Compare your facial features. Are you a policeman who needs to ID a suspect? Scan their fingerprints and irides. Want to control your Canon DSLR remotely? Use your Android phone.

Could the world really be coming to an end tomorrow? Presuming you believe the biblical prediction from 89-year-old Harold Camping, May 21st, 2011 is undeniably Judgment Day. If you have confidence in that prophecy, you're probably not even reading this because you're too busy either A) preparing for the Rapture or B) sitting in your backyard bunker hoping to outwit annihilationism.

Understandably, the tragedy in Japan has substantially risen the level of worldwide radiation-related hysteria. So much so, as an alternative to stampeding health food stores for iodine tablets, crafty individuals and organizations are hacking together personal radiation detectors. Rather than relying on the government, the creation and modification of handheld Geiger counters provides a self-sufficient solution to today's questions regarding radiation. Profiled below, three admirable organiz...

And Dumbfounded Most Watching Game 1 of 2010 World Cup I just finished watching the Mexico - South Africa 2010 World Cup opener and boy was it a good one. The finish of a tie, wasn't totally cool to me, until I realized what I missed.
Hello again ! This is the second part to Fingers from a Hand Analysis perspective.Where as the first Video just covers basic introductions to the Fingers, this part two Video takes things a little bit further and examines ......Finger Shape ;- Length suggesting mental speed, Methodical or Speedy thinker ?Finger Width ;- Suggesting which level a persons interests may lay, Mental or Practical realms ?Finger Prints ;- Amazingly interesting area to explore , Fingerprints do not change.. They star...

Antivirus programs usually aim to prevent malicious software from crashing your system, not ARE malicious software that crashes your system. Except, that was the case with AVG Anti-Virus yesterday when they released a software update that rendered 64-Bit Windows 7 systems useless. It affected both free and paid AVG owners.

Note: The article assumes that the reader has a fundamental understanding of at least one other programming language and Perl. This is intended serve as a quick reference for Perl's input/output of data to databases.

In the first part of this series, we learned about darknets, as well as how they came about. But these patches of forgotten Internet are not the oasis of free information you might think. Despite being hidden—or just harder to come across—these networks are no more safe then anywhere else on the 'clear' Internet. The nature of networking and routing means your location is always known in server logs. It only takes one phone call to your ISP with your IP address to obtain both your physical ad...

When it comes to social engineering, Null Byte is here to show you how it's done. Social engineering is the key fundamental to unlocking tons of possibilities and opportunities in your everyday life. So, what is social engineering? Social engineering can be called many things. It's taking nothing and turning it into something. It's taking the bad and making it good. Above everything else, it's the art of manipulating the world and people around you—coercing that salesman into giving you a low...

FOXBORO, Mass. - The New England Patriots Alumni Club (NEPAC), announced that more than a dozen former Patriots players are gearing up to host a "Football for You" youth clinic in Worcester on Saturday, May 29 from 12:30-5:00 p.m.

Cryptography is a quintessential part of computer security in the modern world. Whenever you buy something on eBay or log into Facebook, that data is encrypted before it's sent to the server in order to prevent third parties from eavesdropping and stealing your sensitive information.

I recently posted a link to what seemed to be a very useful guide on Lifehacker for creating a TOR button in Chrome. However, when I tried it myself, it did not work. Also, it lacked a warning on the limits of Tor, which I think are important. Therefore, I decided to create an updated and more comprehensive tutorial.

Shortening URLs has become a necessity in this age of Twitter and limited-character status updates. It not only allows us to cram more words into our oh-so-important Twitter statuses, but it also helps us with a few other things.

Having an SSH or Secure SHell to tunnel your traffic through is something we have talked about many times at Null Byte. As we know, it allows us to securely route and encrypt our traffic through a remote server, effectively anonymizing us and protecting our traffic from all forms of analysis—simultaneously. We have gone over how to make a home SSH tunnel. However, the question has come up, "How can I get an SSH tunnel to somewhere other than my computer?" This would be useful in a situation w...

Image via Tiger Mom Says.

Dactyloscopy isn’t going anywhere. Forensic science has much relied on fingerprinting as a means of identification, largely because of the massive amount of fingerprints stored in the FBI’s biometric database (IAFIS), which houses over 150,000 million prints. And thanks to the departure of messy ink-stained fingertips, biometric analysis isn’t just for solving crimes anymore.

As 2009 comes to a close, the Telegraph presents a compilation of this past year's wackiest inventions. As always, here at WonderHowTo, we are inspired and impressed by ingenuity. The contraptions below range from utter silliness (engagement ring bra) to downright amazing (see-through concrete). Check it out.

What is a Data Structure?

Professionally and academically speaking, I am a computer scientist, but I also enjoy lock picking as a hobby, so I thought I would share what knowledge I have with this. Before we start doing anything, first we need to understand the fundamentals of how locks work and then acquire and familiarize ourselves with basic lock-picking tools.

Yesterday, Mojang announced their next video game project 0x10c, and the response has been tremendous. Discussions have covered everything from the math mystery over the game's name, to creating projects that interpret the assembly instruction code the in-game computers use (more on that later), to the debate over why a monthly fee would be required to play online in the "multiverse". To answer that last one, Mojang wants to run everyone's virtual computers in their cloud, even if the user is...

In this article, I'll show you how to build a coil gun. A coil gun is a device that fires magnetic projectiles at high velocities, using electricity. Coil guns require no explosive propellant, therefor can be fired an infinite amount of time, providing that there is ammunition and available electricity.

Welcome to Minecraft World! Check out our advanced tutorials and come play on our free server. Sometimes it's easy to get overwhelmed with the sheer scale or complexity of a build or group project on your favorite server. Too much stress from any creative endeavour can lead to mistakes, discouragement, or fighting among a community. What better way to relieve stress and entertain the troops than some old fashioned competition?

Carol Baldwin-Moody of Wilmington Trust describes the challenges that are present in her line of work as senior vice president and chief risk officer. There is a strong legal backing to every major issue in today’s society. Baldwin-Moody has come across several scenarios that aren’t covered by the dated constitutional law in effect today. In past years, a risk officer was thought to be a management concept that would be useful, but not worth the investment. Lately, a risk officer career has b...

This words will help you identify terms that are brought up in reviews. You can also use them when writing your own review to be a bit more descriptive.